Endpoint Security client help
Use the Ivanti Endpoint Security application to monitor and manage Endpoint Security activity on your computer. To open the Endpoint Security application, double-click its icon in the Windows taskbar notification area.
Endpoint Security includes the following components:
- Application control: Monitors software activity and prevents malicious software from executing.
- Whitelist: Prevents programs that aren't on an approved list from executing.
- Firewall: Protects you from unauthorized network connections.
- Device control: Monitors and restricts attached device access. Restrictions can be placed on wireless connections, USB thumb drives, and so on.
Depending on how your Ivanti administrator configured Endpoint Security, some components may be disabled.
If you're authorized by a Ivanti Administrator with Endpoint Security rights, you can also use the Endpoint Security application to enable/disable and customize Endpoint Security component configurations. If your administrator hasn't authorized you, you can still use the application to view Endpoint Security settings and information. Non-administrators can also request access to a restricted operation by providing an administrator an unique authentication code that's in the Restricted operation password dialog box.
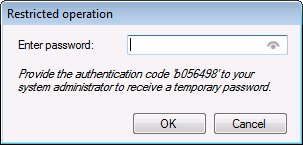
For information on using restricted operations, see the Ivanti® Endpoint Manager online help.
Using Endpoint Security
Use Endpoint Security to do the following:
- View Protection status for Endpoint Security components (home view)
- View program activity (reports view, Program activity)
- View startup applications (reports view, Startup applications)
- View the Ivanti trusted file list (reports view, Trusted file list)
- View the detailed Endpoint Security activity log for your computer (reports view, Detailed activity)
- Installing an authorized program
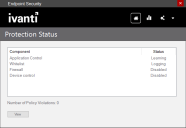
Viewing protection status for Endpoint Security components
The Endpoint Security home button shows the current protection status for Endpoint Security components. The status refreshes automatically when changed and can be one of the following:
- Blocking: Security violations are blocked and reported.
- Disabled: Component isn't active
- Learning: Security violations are allowed and learned
- Logging: Security violations are allowed but reported
Clicking the View button opens the detailed Endpoint Security activity log, where you can see policy violations and other activity.
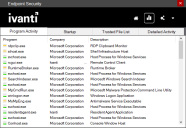
Viewing program activity
The Program activity report tab shows currently running programs, the program name, the company that made it, and a description of the file if it's available. The colored icon next to each program indicates the process permissions:
- Red: The program has no Endpoint Security permissions or restrictions configured and so it runs without restrictions.
- Yellow: The program has some Endpoint Security permission restrictions. See its permissions details for more information.
- Green: The program has all Endpoint Security permissions and runs without restrictions.
Right-clicking a program allows you to do the following:
- Cick Details to see Endpoint Security settings affecting that program. Users with Endpoint Security administration rights can modify program permissions and add or modify trusted file list programs. Changes here only affect the selected process. For example, if there are two notepad.exe processes, modifying the permissions for one won't affect the other. If you make changes and don't select Add to local trusted file list, your changes are temporary and only last until the selected program ends.
- Click Terminate to forcefully end a program (Endpoint Security administrator-only). To prevent data loss, only do this for programs that are unresponsive and when there's no other way to end them.
- Click Notify to toggle the notification status. When enabled (the default), Endpoint Security violations involving that program will trigger a popup in the Windows notification area on the taskbar. If you don't want to see these popups for a program, disable this option. When disabled, violations will still be logged.
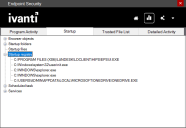
Viewing startup applications
The Startup report tab shows a tree view that categorizes startup objects by type. This list is refreshed in real-time. The categories include:
- Browser objects: Internet Explorer/ActiveX plugins
- Startup folders: Windows startup folders
- Startup files: INI files
- Startup registry: Various registry location allowing program execution
- Scheduled task: Entries in c:\windows\tasks
- Services: Entries in HKLM\SYSTEM\CurrentControlSet\Services
If you right-click an item you can view the items details. The Date field shows when the startup item was added. Dates are only available for startup Items added after Endpoint Security was installed.
If your Ivanti administrator allows, you can also enable/disable startup items.
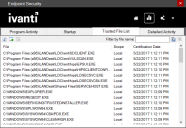
Viewing the Ivanti trusted file list
The Trusted file list report tab shows files on the trusted file list that your administrator has configured. Files on this list are trusted and can bypass application control restrictions. This list refreshes in real-time. Ivanti administrators can add entries to the core server's trusted file list. Other modifications to the core server's trusted file list must be made from the Endpoint Security for Endpoint Manager console. All other changes you make here are local to your computer.
Viewing the detailed Endpoint Security activity log for your computer
The Detailed activity report shows Endpoint Security log events and security violations.
Right-clicking an event allows you to do the following:
- Notify violations: When unchecked, Endpoint Security won’t display notification when the process raises a violation (the process will still be blocked as expected)
- Learn globally: Add the required permissions to the core’s trusted file list, so the process won’t be alerted next time (password required)
- Learn locally: Add the required permissions to the local trusted file list, so the process won’t be alerted next time (password required)
- Request exception: Send a request to the administrator asking that this file to be added to the core’s trusted file list.
Installing an authorized program
Users with Endpoint Security administration rights can use Endpoint Security to install an authorized program. Opening the settings menu and clicking Install authorized program opens a file browser where you can select the program's installer executable. Installing a program this way does the following:
- The selected program won’t be blocked
- Its child processes won’t be blocked
- Executable files created by this program or child processes will be allowed to execute and can be added to the system startup