Provisioning template action types
The table below displays the action types and where they fit into sections by default. You can add any action type to any section, but note that some actions inherently fit in certain sequences in provisioning, and if an action is executed outside its intended sequence, unintended consequences may occur.
| Action name | System migration | Pre-OS installation | OS installation | Post-OS Installation | System configuration |
|---|---|---|---|---|---|
|
BitLocker |
X |
|
|
|
X |
| Capture image | X | ||||
| Capture profile | X | ||||
| Change agent settings | X | X | |||
| Compare variable | X | X | X | X | X |
| Configure agent | X | ||||
| Configure target OS | X | ||||
| Control service | X | ||||
| Copy file | X | X | X | X | X |
| Create directory | X | X | X | X | X |
| Customize mapped software | X | X | X | X | X |
| Delete file | X | X | X | X | X |
| Deploy image | X | ||||
| Deploy profile | X | ||||
| Device name prompter | X | X | X | X | X |
| Distribute software | X | ||||
| Download file | X | X | X | X | X |
| Download from preferred server | X | X | X | X | X |
| Execute file | X | X | X | X | X |
| Hardware-independent imaging | X | X | |||
| Inject script | X | X | X | X | X |
| Install mapped software | X | ||||
| Install service | X | ||||
| Join domain | X | ||||
| Launch template | X | X | X | X | X |
| Map/Unmap drive | X | X | X | X | X |
| Map/Unmap drive to preferred server | X | X | X | X | X |
| Partition | X | X | X | ||
| Patch system | X | ||||
| Reboot/Shutdown | X | X | X | X | X |
| Replace text | X | X | X | X | X |
| Scripted install | X | ||||
| Uninstall service | X | ||||
| Unzip file | X | X | X | X | X |
| Update registry | X | ||||
| Wait | X | X | X | X | X |
| Windows refresh | X | X |
macOS action types
The table below shows actions you can use with macOS devices.
| Action name | System migration | Pre-OS installation | OS installation | Post-OS Installation | System configuration |
|---|---|---|---|---|---|
| Capture image | X | ||||
| Capture profile | X | ||||
| Change agent settings | X | X | |||
| Compare variable | X | X | X | X | X |
| Configure agent | X | ||||
| Configure target OS | X | ||||
| Copy file | X | X | X | X | X |
| Create directory | X | X | X | X | X |
| Customize mapped software | X | X | X | X | X |
| Delete file | X | X | X | X | X |
| Deploy image | X | ||||
| Deploy profile | X | ||||
| Device name prompter | X | X | X | X | X |
| Distribute software | X | ||||
| Download file | X | X | X | X | X |
| Execute file | X | X | X | X | X |
| Hardware Independent Imaging | X | X | |||
| Inject script | X | X | X | X | X |
| Join domain | X | ||||
| Launch template | X | X | X | X | X |
| Map/Unmap drive | X | X | X | X | X |
| Map/Unmap drive to preferred server | X | X | X | X | |
| Mount ISO | X | X | X | X | X |
| Partition | X | X | X | ||
| Reboot/Shutdown | X | X | X | X | X |
| Replace text | X | X | X | X | X |
| Scripted install | X | ||||
| Unzip file | X | X | X | X | X |
| Wait | X | X | X | X | X |
For more information on configuration details, see BitLocker Config.
The Capture image action lets you capture an image at the time of OS installation, through the use of the imaging tool you specify.
For the Capture image and Deploy image tasks in Provisioning templates, one of the image type options is “Ivanti ImageW V2”. This option is no longer supported for new customers. Existing customers with a pre-Endpoint Manager 2024 core can copy the following files from their old core (or old installation media) to continue using this functionality:
- \Program Files\LANDesk\ManagementSuite\ldlogon\provisioning\windows\imagew.exe
- \Program Files\LANDesk\ManagementSuite\ldlogon\provisioning\windows\imagew_x64.exe
For Windows devices, if the tool or the contents to be captured in an image are located on a share, you must place the Map drive action prior to the Capture image action in order to authenticate to the share.
•Select the image type: Select the type of image you want to capture. If you select Symantec or Other, you will also need to provide a path to the application used for imaging.
•Specify the UNC path to the image file: Enter a UNC path to the image that is captured, including the image file name. Configure your preferred server with valid credentials to the share for the image file path. This option is used only when you select Symantec or Other as the image type.
•Specify the UNC path to the imaging tool: Enter a UNC path and file name for the imaging application. This option is used when you select Symantec or Other as the image type.
•Command-line parameters: Enter any command-line parameters that will customize the way the image is captured.
•Validate: Click this button to generate a default command line for the imaging tool and path you specified. You can add other command-line parameters after you click Validate, but if you have already entered any custom parameters they will be removed when you click Validate.
Use this action to capture a macOS image from a target device. The capture image action uses preferred server credentials to authenticate to the shares. This is set in the Content replication / Preferred servers tool. A macOS server has to be set as a preferred server for this to work. The User name and Password fields in the core server’s preferred server properties are used to access the shares. The options available for this action include:
•Specify the path to save the image file, including the name of the image file: To enter the location to capture and store the image file. Either smb://Server/SharePoint/ImageFile.dmg OR afp://Server/SharePoint/ImageFile.dmg format can be entered into this field. If left blank, the current boot image is used by default.
•Mac image: Captures the Mac image.
•Windows image: Captures the Windows Bootcamp image.
•Validate: Click this button to populate the Command-line parameters field with the data provided in the other fields.
This action runs the user migration assistant to capture one or more profiles. To use this action, you need to know where the user migration assistant command XML file is located on the core server and where saved profiles are to be stored.
You can use unique identifiers to name profiles when they are saved, or you can specify a full filename for the profile.
To use the user migration assistant, managed devices must have the standard Ivanti agent, which includes the inventory scanner, local scheduler, and software distribution agents. Profile migration uses the software distribution agent to distribute files.
- Select user migration assistant command XML file: Specify the location of the user migration assistant command file, which is an XML file saved on the core server (typically in the ldmain share, in the ldlogon\uma\commandxml folder). You can specify the path and filename in UNC or HTTP format. Click Browse to locate the command file you want to use. If you want to edit an existing command file or create a new one, click Edit. Select a file and click Edit, or click New to create a new one.
- UNC path for saved profiles: Specify where to save the profile files. Type a UNC path or click Browse and select a path. Profiles can be saved on any available server/share, including on the core server. Profiles are saved with a .sma extension.
- Specify full filename instead of using variables: Select this check box if you don't want to name the profile using the unique identifiers.
- File name unique identifiers: Select any combination of the computer name, MAC address, and serial number to create the filename of each profile. (For example, if you select Serial number and the serial number of the machine is 123A567B, the profile name will be saved as "123A567B.sma.") These profile file names are only used to make the file names more readable. They aren't used by automatic naming to associate profiles between computers.
Use this action to capture a profile on a target device. The capture profile action uses preferred server credentials to authenticate to the shares. This is set in the Content replication / Preferred servers tool. A macOS server has to be set as a preferred server for this to work. The User name and Password fields in the core server’s preferred server properties are used to access the shares.
When saving profiles, you can specify a full filename, or you can use unique identifiers to create the file name to store the profile.
The Mac version of capture profile captures these items:
- Core certificate
- Device name
- How network adapter interfaces are configured
- LDMS configuration
The fields that can be selected in this action are a follows:
- Path for saved profile: Where to store the profile when it is captured. The format can be smb://server/sharepoint or afp://server/sharepoint.
- Specify full filename instead of using variables: Select this if you want to disable the filename unique identifiers options. Selecting this will require the filename to be specified in the Path for saved profile field.
- File name unique identifiers: Select any combination of the Computer name, MAC address, and Serial number to create the filename of each profile.
The change agent settings action lets you select specific Ivanti agent settings for agent components. Agent settings only affect agent components that are installed on the device. Applying an agent setting to an agent component that isn't installed won't install that component or have any effect.
The default agent setting option is to Keep agent's current settings. Use the Edit button to modify an existing agent setting and the Configure button to manage all settings for a component.
Evaluates the variable at the client and returns success or fail based on the comparison. There is no case-sensitivity with string comparisons. This is useful for controlling the branching flow of If/Else conditions. For more information on conditions, see Provisioning template conditionals.
The variables you can compare depend on what is available from the device inventory and the template. BNF database query syntax is also supported. Note that new devices may have no or limited inventory data available.
The configure agent action lets you select an agent configuration to install on the provisioned device. This action should be the first thing done after the reboot that follows the OS install actions. Configurations are added to the drop-down list as you create them in Agent configuration. This action can only be completed as part of a template that includes either the Scripted install or Deploy image actions, or if the client machine has already been configured with an agent.
- Configuration name: The name of the configuration. Select a configuration from the list of valid agent configurations.
- Reboot if required: Select this check box to allow the device to reboot after agent configuration, if a reboot is required.
When you install a new service pack, the agent configuration database IDs change. This means that the templates referencing those configurations become outdated. As a result, any provisioning history referencing those configurations will be unable to display the name of the configuration it once referenced, and any template referencing the old configurations will need to be updated before it will run correctly. The configuration name is not displayed in the History page, and if you try to re-schedule this template, it will fail on the Agent Configuration action because of this problem. To fix it, you must clone the template, open the cloned template, open the Agent Configuration action, and assign the configuration you want to use. Then the task will run successfully.
The configure agent action lets you select an agent configuration to install on the provisioned device. This action should be the first thing done after the reboot that follows the OS install actions. Configurations are added to the drop-down list as you create them in Agent configuration.
The configure agent action uses preferred server credentials to authenticate to the shares. This is set in the Content replication / Preferred servers tool. A macOS server has to be set as a preferred server for this to work. The User name and Password fields in the core server’s preferred server properties are used to access the shares.
- Configuration name: Select which agent configuration to deploy in the action.
- Reboot if required: Will set a reboot to occur after the agent is installed.
This action inserts the provisioning agent (ldprovision) into an image so that the agent can be installed after reboot. It is required for continued provisioning after the new OS starts. For this action to work, the following conditions must be met:
- The Windows system drive must be mounted.
- The Windows file system must be either sysprepped or have an agent on the machine
- Insert unique ID: To use the existing device ID, select this check box and enter the device ID in the box.
This action should be performed as the last action in the post-OS installation section because it includes a reboot operation.
The Control service action starts, stops, or restarts a specified service. The target OS must be Windows for this action.
- Service name: The display name of the service.
- Service control action: The action to execute on the service. Can be Stop, Start, or Restart.
The Copy file action copies files to specific locations on the target device. Both the source and destination can be located on a share. If this is so, you must include a Map drive action prior to the Copy file action. The Copy file action can be recursive, meaning that all files/folders below the source path can be copied, maintaining their original structure. Wildcard characters are supported (such as *.exe or ld*.*).
- Source path and file name: The server/share path and file name location of the file to be copied. If you want to copy all files and folders below the source path, no file name is necessary.
- Destination path and file name: The server/share path and file name location to copy the file to.
- Copy subdirectories: Copies all subfolders and files below the source.
The Create directory action creates a directory in the specified location and can create the parent directory, if needed.
- Path of the directory: Type the path to the directory to be created.
- Create parent directory if needed: Select this check box to create the parent directory.
This action allows the technician at the device being provisioned to select and install software that was marked "customizable" in the Product to package mappings dialog box. You can access this dialog box from the OS Provisioning toolbar by clicking Tools > Product to package mapping.
When using this action, generally add it near the template beginning. Once it's added, you can configure a timeout for how long the customize mapped software prompt will appear on the device. The default is 300 seconds. If a technician isn't there to customize mapped software, the action will eventually time out and whatever customizable software that was installed on the source device will be installed on the new device.
The template must include the Install mapped software action for the changes made here to take effect.
The Delete file action removes files in specific locations on the target server. The path can be located on a share. If this is so, you must include a Map drive action prior to the Delete file action. The Delete file action can be recursive, meaning that all files/folders below the source path can be deleted. Wildcard characters are supported (such as *.exe or ld*.*).
- Path and file name: Enter the full path and name of the file to be deleted.
- Delete subdirectories: Deletes all subfolders and files below the source.
This action deploys the selected image to the target server through the use of the imaging tool you specify. If the tool or the image to be deployed are located on a share, you must place the Map drive action prior to the Deploy image action in order to authenticate to the share.
You must manually reboot after deploying an image.
For the Capture image and Deploy image tasks in Provisioning templates, one of the image type options is “Ivanti ImageW V2”. This option is no longer supported for new customers. Existing customers with a pre-Endpoint Manager 2024 core can copy the following files from their old core (or old installation media) to continue using this functionality:
- \Program Files\LANDesk\ManagementSuite\ldlogon\provisioning\windows\imagew.exe
- \Program Files\LANDesk\ManagementSuite\ldlogon\provisioning\windows\imagew_x64.exe
- Select the image type: Select the type of image you want to deploy. If you select Symantec or Other, you will also need to provide a path to the application used for imaging.
- Specify the UNC path to the image file: Enter a UNC path to the image that is deployed, including the image file name. Configure your preferred server with valid credentials to the share for the image file path. This option is used when you select either Ivanti ImageW or ImageX as the image type.
- Specify the mapped drive path to the image file: Enter a path to the image , including a drive letter and the image file name. This option is used when you select Symantec or Other as the image type.
- Specify the mapped drive path to the imaging tool: Enter a mapped drive path and file name for the imaging application. This option is used when you select Symantec or Other as the image type.
- Command-line parameters: Enter any command-line parameters that will customize the way the image is deployed.
- Validate: Click this button to generate a default command line for the imaging tool and path you specified. You can add other command-line parameters after you click Validate, but if you have already entered any custom parameters they will be removed when you click Validate.
Use this action to deploy an image from a target device. This action uses preferred server credentials to authenticate to the shares. This is set in the Content replication / Preferred servers tool. A macOS server has to be set as a preferred server for this to work. The User name and Password fields in the core server’s preferred server properties are used to access the shares.
The options available for this action include:
- Specify the path to save the image file, including the name of the image file: This is to define the smb://Server/Share/ImageFile.dmg or afp://Server/Share/ImageFile.dmg to capture the image.
- Mac Image: Select this for Mac images.
- Validate: Click to populate the Command-line parameters field with the data provided in the other fields.
This action runs the user migration assistant to deploy one or more profiles that have been captured and saved. To use this action, you need to know where saved profiles have been stored.
To use the user migration assistant, managed devices must have the standard Ivanti agent, which includes the inventory scanner, local scheduler, and software distribution agents. Profile migration uses the software distribution agent to distribute files.
- UNC path where the profile was previously saved: Specify where the profile files are saved. Type a UNC path or click Browse and select a path. Profiles can be saved on any available server/share, including on the core server. Profiles are saved with a .sma extension.
- Specify full filename instead of using variables: Select this check box if you don't want to name the profile using the unique identifiers.
- File name unique identifiers: Select any combination of the computer name, MAC address, and serial number to create the filename of each profile. (For example, if you select Serial number and the serial number of the machine is 123A567B, the profile name will be saved as "123A567B.sma.")
Use this action to prompt for keyboard input to name the device running the OS Provisioning Template. This is optional because without it, the name is assigned from the following two steps:
- Variable: Create an “ldHostname” variable to replace text in the unattend script.
- Unattend script: Places the “ldHostname” variable into the “ComputerName” field of the script.
These two steps assign the Hostname on the device is provisioned.
If instead, you want to allow someone to input the name, inject the Device Name Prompter action as the first step in the Pre-OS installation section. This will allow the user to start the OS Provisioning template, get the prompt right-away in the process, then leave to do something else. The name will be in memory, and will be used rather than what is in the variable “ldHostname” inserted into the “ComputerName” of the unattend script.
- Timeout (seconds): This sets the amount of time to allow the user at the device to input a name for the device. If the name and typed and the “Enter” key is pressed, the timeout continues without further waiting. If the name is not input before the time elapses, the action defers to the variable “ldHostname” in the “ComputerName” field of the unattend script.
This action distributes a software distribution package to the target. You can choose from any distribution package that you have saved in the Distribution packages tool. This action can only be completed after the agent configuration action, or after agents have been installed on the device.
- Software distribution package: Select the package you want to distribute.
The Download file action downloads the selected file using an anonymous user (anonymous HTTP login) to a destination you specify. If the files to be downloaded or the destination are located on a share, you must place the Map drive action prior to the Download file action in order to authenticate to the share.
If you have multiple servers, you'll want to use a preferred server.
- Source path and file name: The current server/share path and name of the file to be downloaded. Downloading files from a UNC path is not supported. If you want to download a file from a UNC path, you should use the Map drive action to map to the UNC path, then use the Copy file action.
- Destination path and file name: The location the file is to be downloaded to.
- Use proxy server: Enables the proxy server option to download a file. By default, this option is disabled. If you enable a proxy server, you must fill in the address and port fields below.
- Address: Identifies the IP address of your proxy server.
- Port: Identifies the port number of your proxy server.
- Requires login: Allows you to enter a username and password if the proxy server is credentialed instead of a transparent proxy server.
- User name: Enter a valid user name with authentication credentials to the proxy server.
- Use a variable for the password: Select this check box to use a variable for the password. This variable is set in Template variables under Sensitive data type. Enter the variable name in the Password box enclosed in percent signs (%variablename%). For more information, see Define a template variable.
- Password: Enter the user's password. Confirm the password in the Confirm password box.
Should an error occur, such as the file not downloading to the device, right-click the task and navigate to Provisioning history > Download file. This shows any errors encountered during the file transfer.
This action uses content replication to download data from a preferred server to the target device. The download can be a single file or the contents of a folder (including subfolders) on the source server. To use this action, you must have configured at least one preferred server using the Content replication tool. The choice of which preferred server is used depends on the settings you made when you set up preferred servers in the Content replication tool.
- Source: Specify the path to the file or folder you want to download. This path must exist on all shares that are used for preferred server downloads.
- Download directory: Select this check box to download the entire folder specified in the Source box. If this is cleared, only the file you specify will be downloaded.
- Destination: Specify the path on the target device to which you want to copy the file or folder.
- Preferred download locations: The three check boxes let you specify which download sources you want to use. They are listed in the order of priority: if all three boxes are selected, a peer download is attempted first, followed by a preferred server, and finally a source download.
- Attempt peer: Select this check box to first attempt a peer download. The replicator will first check local peers for source files that it is replicating. If the replicator can't find the files on a peer, it will then attempt to get the file from a preferred server or the source server. This option can reduce the traffic load on preferred and source servers.
- Attempt preferred server: Select this check box to download from a preferred server. If the replicator can't find the file on a preferred server, it will then attempt to get the file from the source server.
- Allow source: Select this check box to download from the file source. This is recommended only as a secondary option if a peer download or preferred server download can't be completed.
- Bandwidth used from core or preferred server: Adjusts the priority of this specific task over other network traffic. The higher the percentage slider is set, the greater the amount of bandwidth being used by this task over any other traffic. WAN connections are usually slower, so it is most often recommended to set this slider at a lower percentage.
- Bandwidth used peer-to-peer: Adjusts the priority of this specific task over other network traffic. The higher the percentage slider is set, the greater the amount of bandwidth being used by this task over any other traffic. LAN connections are usually faster than WAN connections, so it is most often recommended to set this slider at a higher percentage than that of the WAN.
The Execute file action executes the selected file on the targeted server, along with any command-line parameters or return codes you specify.
- Target path and file name: The location of the file you want to execute.
- Command-line parameters: Enter any command-line parameters that customize the way the file is executed.
- Working directory: The program will be executed with reference to this directory. Any supporting files of the program should reside in this directory. Command-line parameters start from this reference point.
- Expected return value: The value expected to be returned by the application upon execution. Can be Any, equals (=), less than (<), greater than (>), or Between. If the value is to be anything other than Any, enter the values to be expected in the boxes provided.
- Insert: Opens the Environment variable dialog box, where you can add an environment variable and its value.
- Name: Type the name of the environment variable of the file. Use double percent signs to specify environment variables (for example, %%windir%%\system32\calc.exe).
- Value: Enter the value of the variable.
- Modify: Modify the selected variable.
- Remove: Delete the selected variable.
- Capture command output: When this check box is selected, output from the executable is written to a log file. Clear the check box to avoid capturing the output.
The Hardware-independent imaging action includes the hardware-independent imaging tool (hiiclient.exe) in the provisioning process. Hardware-independent imaging (HII) lets you create a single repository of device drivers that can be injected into provisioning templates or deployment scripts. A base image is installed on the device, and the HII tool then injects drivers that are specific to the device model.
This action is only included in the System configuration or the Post-OS installation section for templates based on the Windows preboot environment. After the OS is installed, but before the device reboots, the HII tool detects the device model and retrieves drivers for that model. The drivers are installed onto the device and their information is included in the registry. After a reboot, when the OS starts it configures the drivers.
You can also use HII to associate SWD packages with drivers. This works well with drivers that are only in an executable (.EXE) format.
- Using UNC to download driver files: select this check box to specify that only UNC is used to access the HII repository.
If you use this action, include a Reboot action after it in the Post-OS installation section.
This action injects a script into the target OS file system. For example, you can inject sysprep.inf into the Deploy image action or unattend.txt into a Scripted install action. The scripts that you can select are those in the Install scripts list (accessed from the Install scripts button on the Provisioning toolbar) that can be applied to the current template.
Injecting a script copies the file to the local machine and also replaces any variables within the file. This action is useful when you want to replace variables in any text file, such as a Windows Sysprep answer file.
- Script name: The name of the script.
- Target file name: The location of the script you want to inject.
This action installs software detected on a target device which is monitored in the Software License Monitoring tool
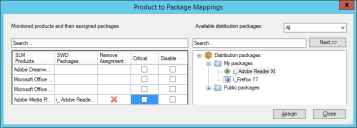
Use this action to install software using the rapid software deployment feature as configured in the Product to Package Mapping tool, which can be launched by clicking the Product to Package Mapping icon  on the OS provisioning toolbar.
on the OS provisioning toolbar.
In the Product to Package Mappings tool, you can assign SLM Products to distribution packages. This assignment sets which software will be installed on the newly provisioned device. The ability to make these assignments enables upgrading an older version of software to a newer version, as part of an OS Provisioning task.
- SLM Products: Populates with all software applications in the SLM tool's Monitored section.
- SWD Packages: Shows all distribution packages that are created and available to be installed.
- Remove Assignment: Allows removing the assignment so the software will NOT be deployed as part of the Install Mapped Software action.
- Critical: Selecting this checkbox is analogous to selecting the Stop processing the template if this action fails checkbox for a template action. When selected, if the particular software fails to install, the action fails and will NOT continue to install other software associated as a part of the Install Mapped Software action. When unchecked, even if the particular software package fails to install, the task will continue to install other distribution packages assigned to SLM products. (All software which is attempted to be installed by the action is logged in the OS Provisioning Template History.)
- Disable: Selecting this checkbox means that although a product may be assigned, it will NOT be installed as a part of the Install Mapped Software action. The use case scenario for selecting this is for testing purposes. While testing, do not install the software which has the Disable box selected, while you test other software as a part of this action, then, after all testing is complete, you can clear the Disable box and have the action install all assigned software.
The target OS must be Windows for this action.
- Display name: The name you want to display to represent the service.
- Service name: The name of the service.
- Service description: A description of the service
- Target path and file name: The location of the service you want to install.
- Command-line parameters: Enter any command-line parameters that will customize the way the service is installed.
- Service startup type: Can be Manual, Automatic, or Disabled.
- Interactive service: Select this option to display on the desktop any user interface that can be used by the logged-in user when the service is started. This includes any message boxes the service may invoke during the installation process. If this check box is not selected, the template runs without user interaction, assuming the default selections of any service messages. If the service displays any messages during startup, it may cause the template to pause until the message dialog box is closed.
Use this action to have the device join a domain or workgroup. For domains, you will also need to provide credentials for an account that has rights to add devices to domains. Mac devices cannot join workgroups, so this option will not be available.
•Select operation type: Can be Join domain or Join workgroup.
•Name: Name of the domain or workgroup the device should join.
•OU: The organizational unit associated with the domain.
•Username: Type the username required to authenticate to the domain. This can be entered in one of two formats: [email protected] or domain\user.
•Use a variable for the password: Select this check box to use a variable for the password. This variable is set in Template variables under Sensitive data type. Enter the variable name in the Password box enclosed in percent signs (%variablename%). For more information, see Define a template variable.
•Password: Enter the corresponding password to the username above and confirm.
The supplied parameters are built into the configuration profile using these domain credentials and then encrypted. Once sent to the device, it tries to join the domain. If a failure is encountered, it is added to the error log in addition to returning an error from the join domain action.
Use this action to launch another template as the next action, by clicking Select New Template. This action will start a new template targeting the device matched in the Machine Mappings tool. If no device is matched, the device will target itself, allowing templates to be chained.
The use case for this is when a user has a device that is being replaced with a new device. The OS Provisioning template can capture a profile and other information from the original device, and then the Launch Template action can deploy the desired operating system and the profile (captured from the original device) onto the new device, as well as continue installing desired software on the new device.
For more information on machine mapping, see About the Machine Mapping tool.
Use this action to map or unmap (disconnect) a drive on Windows devices. Note that some systems do not accept drive mappings below drive H.
- Map/Unmap a drive: Select whether this action is to map or unmap (disconnect) a drive.
- UNC path: Enter the server and share you want to map to.
- Resource path to disconnect: When disconnecting a resource, specify the path to be disconnected.
- Drive letter/Mount point: Enter the drive letter you to map the path to. If you chose to unmap a drive, type the name of the drive you want to disconnect.
- User name: Enter the name of the user credential to log on to the drive.
- Use variable for the password: Select this check box to use a variable for the password. This variable is set in Template variables under Sensitive data type. Enter the variable name in the Password box enclosed in percent signs (%variablename%). For more information, see Define a template variable.
- Password: Enter the corresponding password to the username above. Confirm the password in the Confirm password box.
This action maps a drive on the target device to a path on a preferred server (or the source server). The drive mapping stays in effect until the drive is explicitly unmapped (disconnected), so you should include an Unmap action in a template after an action that downloads data from a preferred server. To use this action, you must have configured at least one preferred server using the Content replication tool. The choice of which preferred server is used depends on the settings you made when you set up preferred servers in the Content replication tool.
- Drive letter: Enter the drive letter you want to map the path to. If you chose to unmap a drive, type the name of the drive you want to disconnect.
- Unmap drive: Select this check box if the action is to unmap a drive. The action will simply unmap (disconnect) the drive you specified in Drive letter.
- Path: Enter the path to the drive in UNC format (\\sharename\path). This path must exist on the source server and all shares that are used for preferred server downloads.
- Attempt preferred server: Select this check box to first attempt to map the drive to the nearest preferred server that contains the specified folder structure. If no preferred server is found with the folder structure, an attempt will then be made to map the drive to the path on the source server.
- Require preferred server: Select this check box to map the drive to the nearest preferred server that contains the specified folder structure. If no preferred server is found with the folder structure, the task fails (rather than map to the source server).
- Don't allow preferred server: Select this check box to map the drive to the path on the source server, without mapping to a preferred server.
Use this action to mount an ISO image.
- Image name and path: Enter the \\server\share\file.iso information.
- Mount point: Enter the desired mount point.
The Partition action lets you complete a variety of actions relating to partitions on the target server. Select partition actions from the Action type list.
The actions are listed below.
NOTE: The boot environment and target OS must be set prior to executing this action.
Create partition: Create a partition on the specified disk.
- Disk: Type the disk ID. On Windows, it is the disk number.
- Partition type: Select the partition type. This can be Primary, Extended, or Logical.
- Size: The size of the partition to be created, in MB.
- Offset: A number (in 8-bit byte format) indicating how far into the disk you want to create the partition.
- Start: The start position of the partition (cylinder number).
- End: The end position of the partition (cylinder number).
Remove partition: Delete a partition on the specified disk.
- Remove from disk: Type the disk ID. On Windows, it is the disk number.
- Partition ID: The partition number to be removed.
Remove all partitions: Delete all partitions on the disk.
- Remove from disk: Type the disk ID. On Windows, it is the disk number.
Format partition: Create a file system structure on a partition.
- Logical disk drive letter: The drive letter of the partition to be formatted (Windows).
- File system: For Windows, the file systems are FAT, FAT32, and NTFS.
- Quick format: Select this check box to perform a quick format on the partition.
Mount partition: Mount a partition.
- Disk: The disk number to be mounted (Windows).
- Partition ID: The partition number to be mounted (Windows).
- Logical disk drive letter to create: The drive letter of the partition to be mounted (Windows).
Unmount partition: Unmount a partition.
- Disk: The disk number to be unmounted.
- Partition ID: For Windows, the partition number to be unmounted.
- Logical disk drive letter to remove: The drive letter of the partition to be unmounted (Windows).
Make bootable: Make a partition bootable.
- Disk: The disk number to be made bootable. For Windows, this is the disk number.
- Partition ID: The partition number to be made bootable.
- Bootable: Select the check box to make the partition bootable.
- Windows 7/Windows 2008 R2 with a separate system partition: Select this check box to create a separate OS partition.
- OS partition ID: The partition number for the separate OS partition.
Expand partition: Expands the last partition on the drive. Free space must be available.
- Disk: The disk number to be mounted.
- Partition ID: For Windows, the partition number to be mounted.
- Size: The new size of the partition in MB (Windows). If you leave this blank, the partition will be expanded to fill the disk.
- Start: The start position of the partition (cylinder number).
- End: The end position of the partition (cylinder number).
The Partition action lets you complete a variety of actions relating to partitions on the target server.
When specifying a partition size, you can state these as MB or a percentage of the disk. Be sure the amount of disk space exists. This action will overwrite anything that currently exists. If you do not specify a size on a partition, (this can only be left empty on the last partition) the remainder of the disk will be assigned the last partition.
The action types available are listed below:
Create partition: Create a partition on the specified disk.
•Disk ID: Type the disk ID or disk node identifier to partition.
•Partitions: Establishes multiple partitions to be created as part of the pre-OS installation. With each partition, you can specify a Name, partition Size, and File System.
Remove all partitions: Remove all partitions on the device from the specified disk ID or disk node identifier.
Format partition: Create a file system structure on a partition.
•Format Boot Volume:
•Partition: Specify the partition to format. The value here should match the partition's assigned name.
•File system: Select the desired drive format. The most common formats include MS-DOS FAT32 and HFS+.
Mount partition: Mount the partition to a directory mount point.
•Mount Boot Volume: Specify whether the directory mount point is a boot volume or disk.
•Partition: The partition to mount, specified by name or disk ID. If Mount Boot Volume is selected, this field cannot be used.
•File path to mount: The disk location to mount the partition or volume.
Unmount partition: Unmount a partition to make it inaccessible to Finder. It will still remain visible from the command line or Disk Utility app.
•Unmount Boot Volume: Specify whether the directory mount point is a boot volume or disk.
•Mount point to unmount: The partition or volume to unmount.
Resize partition: Alter the size of a specific partition.
•Disk: The disk ID or disk node identifier.
•Partition ID: The partition name.
•Size in MB: Set the new partition size in MB. If the size is smaller than what currently exists, it will reduce in size. You can also set negative values, which is interpreted as the size by which to shrink the partition.
Set CoreStorage: Control the use of CoreStorage, a volume manager that allows for independence between logical volumes and physical storage.
•Enable or Disable CoreStorage: Select an option to decide whether this partition is managed by CoreStorage.
•Target Boot Volume
•Partition: The partition name.
Create an OS X Fusion Drive: Combine a hard disk drive with a solid-state drive into a single CoreStorage managed logical volume with the space of both drives combined. The partitions specified here are merged into a single managed space.
•Partition 1: The partition of the first drive.
•Partition 2: The partition of the second drive.
•Name for resulting volume: The new volume name.
•File System: Select the desired drive format. These systems differ from standard file systems and are specific to Fusion Drives.
Delete an OS X Fusion Drive: Remove an existing Fusion Drive from Mac devices.
•Target boot drive
•Fusion Drive Identifier: The name of the Fusion Drive. This is the same value as you set for Name for resulting volume when first creating a Fusion Drive.
The Patch system action scans the target device for vulnerabilities and remediates them. This action can only run after a Configuration action that installs the Software updates agent is run.
- Scan only: Scans the machine for vulnerabilities.
- Scan and remediate vulnerability: Scans the machine for vulnerabilities, and fixes (where possible) the vulnerability.
- Scan and remediate group: Scans the machine for vulnerabilities and fixes the vulnerabilities included in the group.
- Vulnerability ID: A valid vulnerability ID from Patch Manager. If the ID is not valid, the action will fail.
- Group ID: A valid group ID from Patch Manager. If the ID is not valid, the action will fail. You can click the Group ID list button to select a vulnerability group that you have created.
The core vulnerability definitions should be updated prior to executing this action. All patches to be remediated must be downloaded on the core before executing either remediation option in this action.
Reboot or shut down the server. A reboot must immediately follow the OS install action. Upon reboot, the provisioning agent restarts the template to continue the progression of provisioning tasks. Use the Reboot action to move from System migration section to OS sections or OS sections to System configuration section. Multiple reboots are supported.
•Reboot: Shut down the server and restart it.
•Shut down: Shut down the server at the end of the provisioning task and leave it powered down (off). You must make sure that this action is the last action in the template, or additional actions will not be completed.
•Boot to managed WinPE (virtual boot): Boot the client machine into a managed WinPE environment. Actions will be executed as instructed by the core server. This option is for use when there is no PXE server in the network for provisioning.
•Confirmation message timeout: Specify the number of seconds that a confirmation message is displayed before it times out.
•Reboot: Shut down the server and restart it.
•Shut down: Shut down the server at the end of the provisioning task and leave it powered down (off). You must make sure that this action is the last action in the template, or additional actions will not be completed.
•NetBoot: Shut down the device and restart it using a network disk drive.
•Confirmation message timeout: Specify the number of seconds that a confirmation message is displayed before it times out.
•Partition/Server: Specifies the partition to use when booting. You can specify a partition or network location depending on the action selected. If this field is left blank, the device will boot to the original partition used.
Replace text in an existing file.
- Source path and filename: The path and filename of the file to have text replaced.
- Find what: The existing text that is to be replaced.
- Replace with: The text that is to take the place of the existing text.
- Replace first occurrence, Replace all occurrences: Replace the new text either the first time it is encountered or every time it is encountered.
Install an operating system through the use of custom scripts. There can only be one action that installs an OS.
Windows
- UNC path to installation source: This is a path where the executable file is found within the installation source. This must have been mounted within the Pre-OS Install section (Map drive action).
- Domain and user name: Enter a domain and user name to log on to the device on which the executable file resides.
- Use variable for the password: Select this check box to use a variable for the password. This variable is set in Template variables under Sensitive data type. Enter the variable name in the Password box enclosed in percent signs (%variablename%). For more information, see Define a template variable.
- Password: Enter the password to log on to the device. Confirm the password in the Confirm password box.
- Additional parameters passed to setup: Parameters to be passed to the install file when it is executed. For Winnt32, the Provisioning handler automatically fills in the unattend (/unattend) and the source arguments (/s). These are generated from the path that was given in the Winnt32 path, and from the script that has been selected.
- Installation script: The unattend file used when installing the operating system.
- Force reboot: Select this check box to require a reboot after the OS has been installed.
Uninstall a service on the target device.
- Service name: The name of the service to be uninstalled.
Unzip the contents of a package to a predetermined location. This action can restore original structure.
- Source path and file name: The path and file name of the package to be unzipped.
- Target path: The location where the package is to be unzipped. If this is an existing directory/folder, any duplicate filenames will be overwritten.
- Create target directory if it doesn't already exist: If the target does not exist, select this check box to create it automatically.
This action adds or removes keys or values to the registry, or imports a registry (.reg) file. Editing the registry incorrectly may damage your system, potentially rendering it inoperable. Before making changes to the registry, you should back up any valued data on your computer.
Select an operation from the Registry operation list.
- Delete key: Remove a registry key's expected folder and path.
- Delete value: Remove the expected value of the key.
- Create key: Create a folder on the left side of the Registry Editor.
- Import file: Import a registry file.
- Set value: Create a value. The data entered is interpreted as a value determined by the Type list.
- Key: Enter the key to create or delete.
- Value: Enter the value to create or delete.
- Datum: Enter data to be saved in a value.
- Type: Select a data type. This can be String Value, Expanded string value, Binary Value, DWord Value, or Multi-String Value.
- Import file contents: Type a description of the registry file to be imported.
- Import data from registry file: Type the full path to the registry file, or click Browse to find it, then click Import file.
Pause the template execution for a specified time or until a required file has been created.
- Time: Pause the template execution for a period of time.
- Number of seconds to wait: Type the number of seconds for which to pause the template.
- File: Pause the template execution until a file has been created.
- Wait for file to exist: Pause the action until the specified path and file exists. This is useful when an action requires an application to install a file. When the file is created, the next action in the template is executed.
- Maximum number of seconds to wait: Type the number of seconds to wait for the file to be created. If the time passes and the file isn't created, the template continues with the next action.
Act upon a target device with a Windows 8 or later OS. These options call the Windows actions for Update and recovery.
- Reset: If you want to recycle your PC or start over completely, you can reset it to its factory settings. Select this option to remove everything and reinstall Windows. This will use the .wim file included in a default image without reformatting the drive.
- Fully clean the drive: Select this checkbox to format the drive prior to overwriting the drive with the .wim file.
- Use default local WIM: Select this checkbox to use the .wim file included in the default OS.
- UNC path including WIM filename to use: Type the UNC path and file name of the .wim file to use. The Use default local WIM checkbox must be cleared to enable this option.
- Refresh: Select to refresh the target PC without affecting the user profile items, such as My Documents, My Music, My Pictures, and so on. This uses a .wim file to overwrite the drive without affecting the user profile items.
- Use default local WIM: Select this checkbox to use the .WIM file included in the default OS.
- UNC path including WIM filename to use: Type the UNC path and file name of the WIM file to use. The Use default local WIM checkbox must be cleared to enable this option.
- Create and assign local WIM: Select to refresh the image with the .wim file included in the default OS.
- UNC path including WIM filename to use: Type the UNC path and file name of the .wim file to use and replace as the local .wim file for future use.
- Assign specified image as local WIM: Select to refresh the image with the .wim file designated in the UNC path including WIM filename to use field.
- UNC path including WIM filename to use: Type the path and file name of the .wim to use to refresh the image.