Component interaction
This section provides an overview of how the various components in an Ivanti Access deployment interact with each other. The following table describes how various components interact with Ivanti Access.
|
Component |
Ivanti Access |
Ivanti Access + Standalone Sentry |
||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
Ivanti Access administrative portal |
All Access related configurations , monitoring, reporting are done in the Ivanti Access administrative portal. |
All Access related configurations , monitoring, reporting are done in the Ivanti Access administrative portal. |
||||||||||||
|
UEM |
Managed apps which use Ivanti Tunnel, the Ivanti Tunnel app, and configurations are pushed from UEM. Ivanti Access gets device posture information from UEM. |
Managed apps which use Ivanti Tunnel, the Ivanti Tunnel app, and configurations are pushed from UEM. |
||||||||||||
|
Ivanti Tunnel |
Ivanti Tunnel establishes trust with Ivanti Access. Only authentication traffic to Ivanti Access goes through Ivanti Tunnel. To trigger Ivanti Tunnel, apply the Ivanti Tunnel VPN configuration to the managed apps and AppConnect apps. |
Ivanti Tunnel establishes trust with Ivanti Access. Only authentication traffic to Ivanti Access goes through Ivanti Tunnel. To trigger Ivanti Tunnel, apply the Ivanti Tunnel VPN configuration to the managed apps and AppConnect apps. |
||||||||||||
|
Standalone Sentry |
Not applicable.
|
Ivanti Access gets device posture information from Standalone Sentry. Standalone Sentry:
•Captures information on which users, devices, and apps authenticate to enterprise cloud service. This information is reported in the Ivanti Access administrative portal. Standalone Sentry Communicates with the Ivanti Access administrative portal on port 443. Standalone Sentry syncs up with Ivanti Access at 15-minute intervals. To force update the configuration changes to Standalone Sentry, use the following CLI command in CONFIG mode: |
UEM compliance actions and policies
Policies configured in a UEM define the checks on device posture and compliance actions if the device in non compliant. Access does the following if devices are out of compliance:
- Ivanti Access blocks connection to cloud service if devices are non compliant (violate an UEM policy) and also have a blocking action set up against the corresponding policy. If there is a non blocking action (such as email, monitor, notify) for a policy violation, Ivanti Access does not take any action.
- For Ivanti EPMM, Ivanti Access quarantines connection to cloud service if the devices are non compliant (violate an UEM policy) and also have a quarantine action set up against the corresponding policy.
However, for Ivanti Neurons for MDM, Ivanti Access does not take any action against a corresponding quarantine policy.
In addition, you can configure Ivanti Access to revoke a session token if a device is non compliant. For more information on device compliance for session revocation, see About session revocation.
Device posture information on Compliant and Non-compliant modes
-
Ivanti Access will have device posture information within 5 minutes to perform compliance actions after device moves from Non-Compliant to Compliant in Ivanti Neurons for MDM.
-
Ivanti Access will have device posture information within 25 minutes to perform compliance actions after device moves from Compliant to Non-Compliant in Ivanti Neurons for MDM.
When a device goes out of compliance, Access blocks the data path. This blocked status of the device can be viewed on Ivanti Neurons for MDM under Devices > Overview.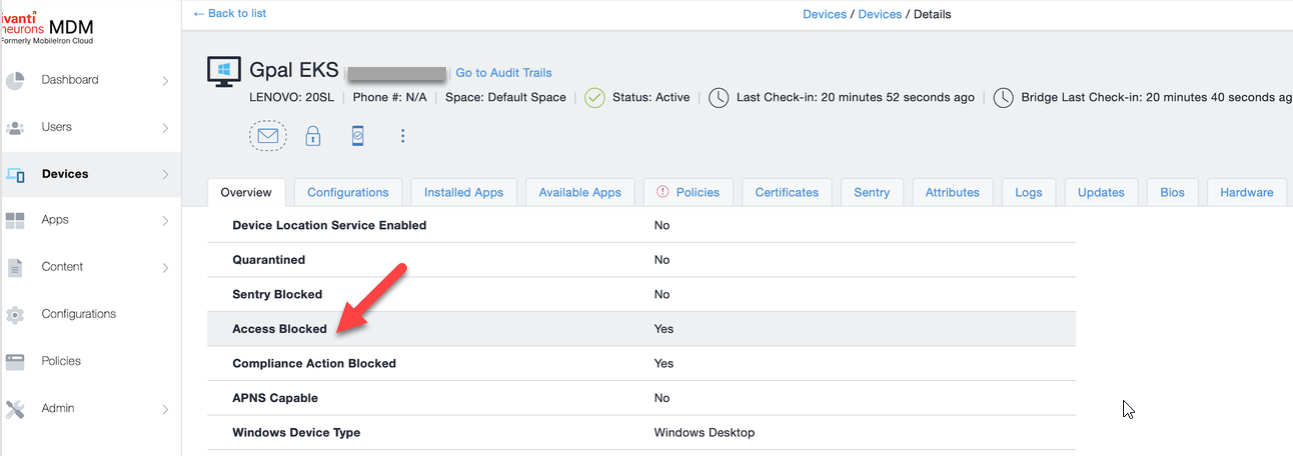
For more information on UEM compliance actions and policies, see the respective Ivanti EPMM or Ivanti Neurons for MDM guides.