App whitelist
Administrators can configure an app whitelist to control if links in an AppConnect app can be opened in non-AppConnect apps. The combination of apps and domains configured in the whitelist determine:
- which links can be opened in non-AppConnect apps.
- the non-AppConnect apps presented to the Android device user in which to open the link.
Configuring the whitelist allows device users to choose a non-AppConnect app, such as WebEx or GoToMeeting, to open from a link in an AppConnect app such as Email+.
The whitelist is ignored if the Web option in the AppConnect Global policy is enabled. If the Web option is enabled, device users can open a link in any non-AppConnect browser on the device.
The value in the whitelist is a combination of the application ID and domain and defines which domains can be opened and the app in which to open the domain. When device users click on a link in an AppConnect app such as Email+, the device user can choose from the following apps:
- All AppConnect apps installed on the device that can open the link.
- If a whitelist is configured, non-AppConnect apps on the device that can open the link.
The non-AppConnect apps that are presented depends on whether the domain in the link is configured in the whitelist and if the application ID for a non-AppConnect app is configured in the whiltelist.
Key-value pair for the app whitelist
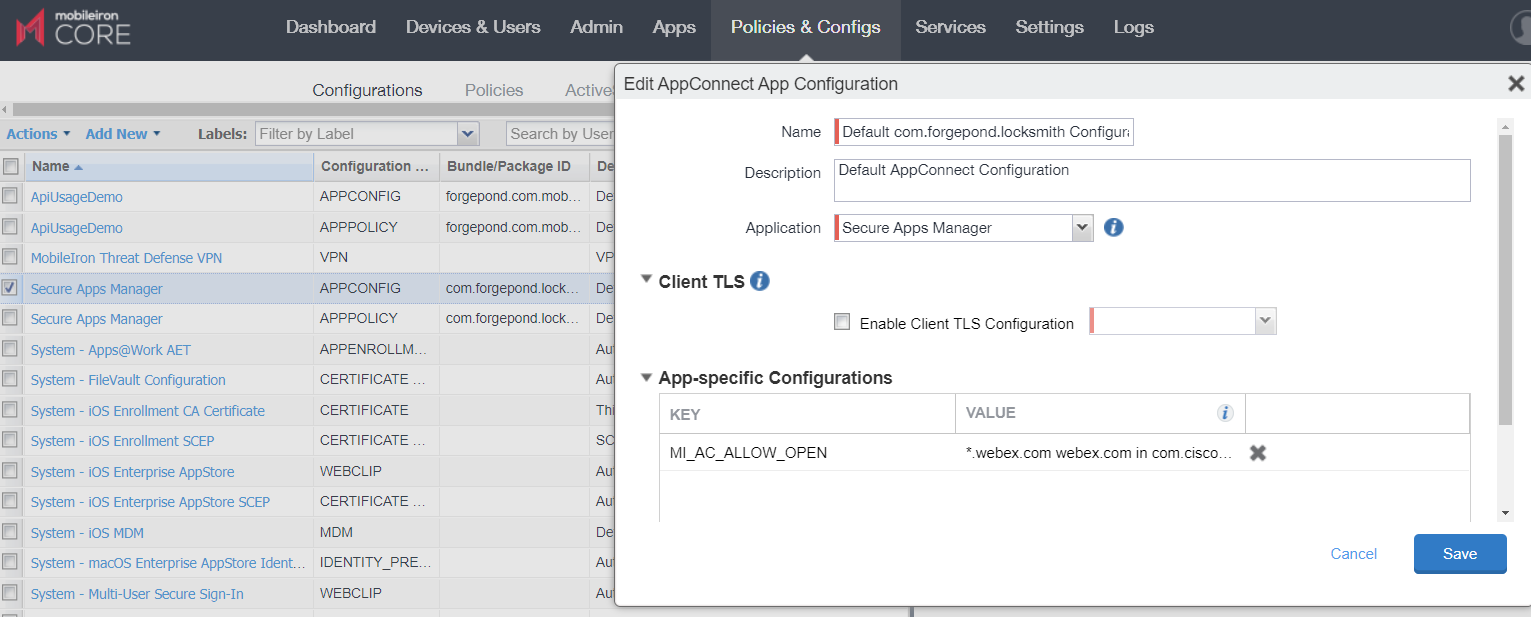
You create the app whitelist by adding a key-value pair in the AppConnect app configuration for Secure Apps Manager. To configure the whitelist, add the following key: MI_AC_ALLOW_OPEN. The value is a matching rule in any of the following formats:
-
domain: Specifies the domain that can be opened in non-AppConnect apps. The domain can include the wildcard character *.
Example :
- Wildcard domain: *.webex.com : Any URL whose host ends with webex.com can be opened in any compatible non-AppConnect app.
-
Multiple domains: *.webex.com webex.com: Any URL whose host ends with webex.com and WebEx links can be opened in a compatible non-AppConnect app.
-
domain in applicationID: Specifies the non-AppConnect app in which the domain can be opened.
Example :
- Wildcard domain in an application ID: *webex.com in com.cisco.webex.meetings: Any URL whose host ends with webex.com can be opened in the WebEx app.
- Multiple domains in an application ID: *.webex.com webex.com in com.cisco.webex.meetings: Any URL whose host ends with webex.com and WebEx links can be opened in the WebEx app.
-
in applicationID: Specifies the non-AppConnect app in which any link can be opened.
Example :
- Application ID: in com.cisco.webex.meetings: Any URL can be opened in the WebEx app.
The following describes the characteristics of the matching rules:
- The value can configure multiple rules.
- Each rule is separated by a semi colon.
- Each rule can have several domain patterns followed by an optional keyword in.
- The application IDs are listed after the in keyword.
- If an application ID is not configured, device users see all non-AppConnect apps on the device that can open the link.
- If the rule contains only an application ID, the app is available for selection for any compatible link.
App whitelist examples
The following table provides examples of the value for various scenarios.
|
Example scenario |
Value |
|---|---|
|
Allow WebEx links to open in the native WebEx app |
*.webex.com webex.com in com.cisco.webex.meetings |
|
Allow WebEx links to open in any non-AppConnect browser and in the WebEx app |
*.webex.com webex.com |
|
Allow any compatible links to open in the native WebEx app |
in com.cisco.webex.meetings |
|
Allow WebEx links to open in the native WebEx app and GoToMeeting links to open in Chrome |
*.webex.com webex.com in com.cisco.webex.meetings ; www.gotomeeting.com in com.android.chrome |
How the app whitelist is evaluated
The whitelist is evaluated each time a user opens a link from an AppConnect app. When users open a link in an AppConnect app:
- The request is redirected to Secure Apps Manager.
- The Secure Apps Manager checks whether the Web option in the Global AppConnect policy is enabled.
- If the Web option is enabled, users can open the link in a non-AppConnect browser and the whitelist is ignored.
- If the Web option is not enabled, Secure Apps Manager checks the MI_AC_ALLOW_OPEN key value.
- The Secure Apps Manager builds a list of external apps that are able to view the link.
-
The Secure Apps Manager filters out the non-AppConnect apps that are not in the whitelist.
If an application ID is not configured, Secure Apps Manager does not filter out any non-AppConnect app.
- The device user can select from the AppConnect apps and non-AppConnect apps in the whitelist that can open the link.
Whitelist apps are available for selection to device users only if the domain pattern in the link matches exactly with the domain pattern configured in the key-value pair.
Configuring an app whitelist
You configure the app whitelist in the AppConnect app configuration for Secure Apps Manager.
Procedure
- In the MobileIron Core Admin Portal, go to Policies & Configs > Configurations.
- Select the AppConnect app configuration for the Secure Apps Manager.
- Click Edit.
-
In the App-specific Configurations section, click Add+.
Figure 1. Add key-value pair to App-specific configuration
- Add the key MI_AC_ALLOW_OPEN.
- Enter a value for the key.
- Click Save.
For information about the formats supported for the value, see App whitelist