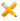Setting up app control
You can set up app control to enhance visibility into the apps being installed on managed devices and enforce corporate app policy.
App control is achieved through a collaboration between the app control rules, Security policy, and alerts:
- The app control rules define which apps you want to control.
- The security policy specifies which devices the rules are applied to and the actions to associate with a rule violation.
- The alert determines the information that is sent as the result of rule violation, and the recipients of the information.
Setting up app control involves completing the following tasks, in this order:
- Configure alerts for when a device violates the app control rules in its security policy.
- Define app control rules.
- Editing the default privacy policy.
- Apply the app control rules to a security policy that is applied to the target devices.
This order of tasks is strongly recommended to ensure that alerts are generated if devices are already in violation when they receive the corresponding policy from Ivanti EPMM. Otherwise, these devices will not generate an alert until one of the following actions occurs:
- administrator changes the security policy
- administrator edits the app control rule
- device updates app inventory
- device updates device details.
Ivanti EPMM does not support app control rules for MAM-only iOS and Android devices.
About app control alerts
To create an alert, you configure a Policy Violation Event in Logs > Event Settings.
The security policy specifies whether violating devices should just trigger an alert or also be blocked from ActiveSync access and AppConnect apps. However, if the associated Policy Violation Event is not yet defined, no alert is generated.
IMPORTANT: To ensure that the alert is generated in a timely fashion for devices that are already in violation when the policy is created, you should create the event first.
App control rule types
By creating app control rules, you define lists of apps that are Required, Allowed, or Disallowed on designated devices. These types are defined as follows:
Table 1. App Control Rule Types
|
Rule Type |
Purpose |
When Policy Violation Occurs |
|
Required
|
(For iOS, macOS, and Android only) Specify apps that must be installed. Required rules take precedence over Disallowed rules in case of a conflict. |
The absence of a required app is a policy violation. |
|
Allowed |
Specify a small set of apps that are allowed to be installed. |
The presence of an app not on the Allowed list is a policy violation. |
|
Disallowed |
Specify a set of apps that are forbidden. |
The presence of a disallowed app is a policy violation. |
You may want to use the rules as described in these examples:
- Required rules (iOS, macOS, and Android only) example: since MDM-enabled iOS devices report inventory even if the Ivanti Mobile@Work has been uninstalled, you can create a Required rule to ensure that if the device user removes Ivanti Mobile@Work, the appropriate response is triggered.
- Allowed rules example: create a set of Allowed rules for use by temporary employees to ensure that they are not installing any personal apps on a corporate device.
- Disallowed rules example: create a set of Disallowed rules to help lower exposure to apps with known security issues. Note that Required rules take precedence over Disallowed rules in the case of a conflict.
App control rules applied in security policies
The following figure shows app control rules applied in the Access Control section of a security policy. In this case, the selected compliance actions are applied if the disallowed apps are detected on a device to which the security policy is applied.
Figure 1. Access Control section in a New Security Policy
Setting up App Control
Complete the App Control set up using the following steps in the following order:
Step 1: Configure App Control alerts
Step 2: Define App Control rules
Step 3: Edit the privacy policy
Step 4: Apply the app control rule to a security policy
Each part of the setup is detailed next.
Step 1: Configure App Control alerts
To enable app control alerts:
- In the Ivanti EPMM Admin Portal, go to Logs > Event Settings.
- Select Add New > Policy Violations Event.
- Enter a name for the event.
- In the Security Policy Triggers section, look for the App Control - All Platforms heading.
-
Confirm that the app control alerts you want to generate have been selected. The following table summarizes these alerts:
Item
Description
Disallowed app found
Generate an alert if a disallowed app is found on a designated device.
App found that is not in Allowed Apps list
Generate an alert if an app is found that is not on the Allowed Apps list for the designated device.
Required app not found
Generate an alert if a required app is not found on a designated device.
- Disable any other triggers that you do not want to enable.
- Click Save.
Step 2: Define App Control rules
Procedure
- In the Ivanti EPMM Admin Portal, go to Apps > App Control.
- Click Add.
- Enter a name for this rule.
The name cannot be changed once the app control rule is saved.
- For the Type option, select the type of rule you want to define:
- Required: (iOS, macOS, and Android only) This rule specifies criteria for apps that MUST be installed. WP8.1 devices ignore this option.
- Allowed: This rule specifies criteria for apps that MAY be installed, exclusive of all other apps.
- Disallowed: This rule specifies criteria for apps that MUST NOT be installed.
- Under Rule Entries, provide one or more entries to identify the apps you want to control. Fill out each entry using the guideline that follow:
- For App, select one of the values listed below to indicate if you are providing a partial or exact match with the app name or identifier, or if you’re providing a MS Store GUID.
If you selected Required, then you must select Identifier Equals or Name Equals. Required is not supported for Windows.
|
Operator Value |
Use for: |
App Identifier/ Name field must have: |
|
Identifier Contains |
iOS, macOS, and Android |
At least a partial match with the app identifier |
|
Identifier Equals |
iOS, macOS, and Android |
An exact match with the app identifier. |
|
MS Store GUID Equals |
Windows Phone 8.1 and Windows 10 Desktop |
An exact match with the application’s MS Store GUID |
|
Publisher/PFN Equals |
Windows 10 Desktop |
Dynamic lookup of the Publisher Product Family Name (PFN) from the Windows Store Search window. See App Control for Windows 10 Desktop devices |
|
EXE/Win32 Equals |
Windows 10 Desktop |
See Identifying the GUID for a Windows Phone app for details. |
|
Name Contains |
iOS, macOS, and Android |
At least a partial match with the app name |
|
Name Equals |
iOS, macOS, and Android |
An exact match with the app name. |
- In the App Identifier / Name field, you can use the application name, unique application identifier, or MS Store GUID as follows:
- App name: For iOS, macOS, or Android, type in the official app name you want to match. Do not enter wildcards. If you don’t know the official name, enter text that you will be able to identify with this app. Once a managed device has installed the app once, the Installed Appspage will display the app’s official name. You can then change this field to match.
- App identifier: For iOS and macOS you can enter the app’s unique bundle ID, or for Android its package name. Using the unique app identifier instead of the app name helps to ensure that a security policy doesn’t unexpectedly block access to important apps when or if an app developer changes the name of an app.
- For WP8.1 enter the MS Store GUID of the app. (See also: Identifying the GUID for a Windows Phone app.)
- In the Device Platform list, select the platform to which you want to apply this entry.
- In the optional Comment field, you can enter a note about the purpose of the entry.
- To add another rule entry, click the + icon.
-
Click Save.
When editing the App Control Rules dialog box, upon clicking Save, you will be asked to confirm your changes.
- This app control rule is now defined.
- To put this app control rule into use, select it in the Access Control section of the appropriate Security Policy dialog, as described next.
Step 3: Edit the privacy policy
App Control does not function unless the administrator changes the default privacy policy setting of "App Catalog Apps" to "All Apps."
- In the Ivanti EPMM Admin Portal, go to Policies & Configs > Policies.
-
Select Default Privacy Policy and then select Edit.
The The Modify Privacy Policy dialog box opens.
- In the Apps field, select All Apps.
- Click Save.
Step 4: Apply the app control rule to a security policy
Procedure
- In the Ivanti EPMM Admin Portal, go to Policies & Configs > Policies.
- Select the security policy you want to work with.
- In the Policy Details pane, click Edit. The Modify Security Policy dialog box opens.
- Scroll down to the Access Control section.
- Under For All Platforms, select the check box when a device violates following App Control rules:”. The field activates.
- In the drop-down list, select the action you want to perform if the app control rule is violated. You can select from:
- Block Email, AppConnect apps, and Send Alert: This option prevents the device from accessing email via ActiveSync and generates a policy violation alert, if configured. This option also unauthorizes AppConnect apps, and blocks app tunnels.
- Send Alert: This option generates a policy violation alert if you have configured the alert in Logs > Event Settings page.
- Any custom compliance actions you have created, which will appear in this list.
- Under Rule Type: Required, select the rules you want to apply, if any, and click the arrow button to move them from the Available list to the Enabled list.
The list of items that appear in the Available column are the App Control Rules you defined in the previous setup step.
- To apply allowed-type or disallowed-type rules, select either Rule Type: Allowed or Rule Type: Disallowed. You may not select both in the same security policy.
- Select the allowed-type or disallowed-type rules you want to apply and click the arrow button to move them from the Available list to the Enabled list.
- Click Save.
- Apply the security policy to a label that is also applied to the target devices. Click Actions > Apply to Label.
The app control rules are now defined and applied to the devices through the security policy.
Editing app control rules
To edit an app control rule, click the edit icon next to the rule in the Apps > App Control page. Note that you cannot change the type of an app control rule if that rule has been applied to a security policy. To delete it, remove it from the security policy first.
Viewing app control status
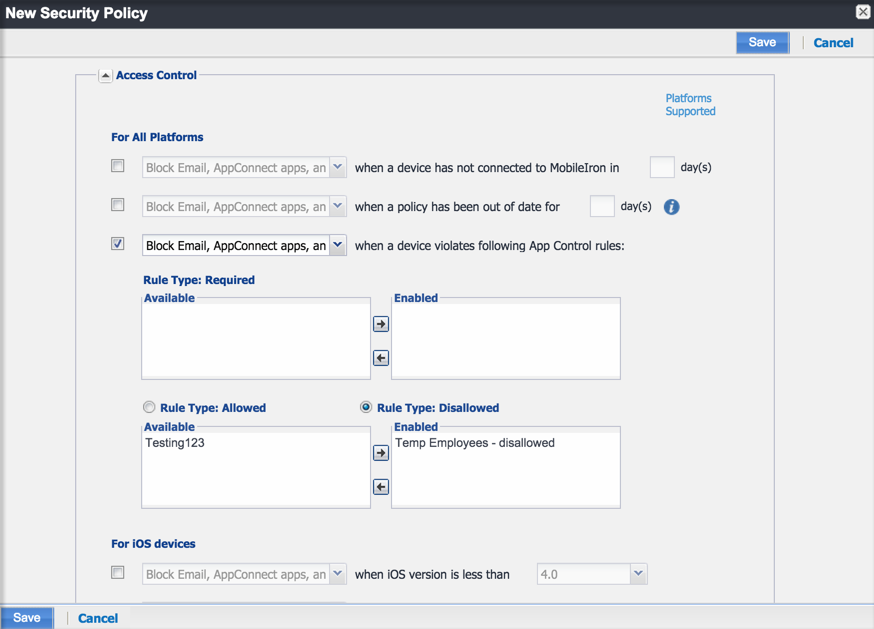
In addition to the alerts you can configure, Ivanti EPMM displays app control status for devices in the Devices & Users > Devices page. Select the entry for a device in violation to see details in the Device Details pane.
Click the caret next to the device entry to open the device details pane. Click Compliance to see the app control status information.
Figure 2. Viewing App Control Compliance Status
The following table shows the icons that indicate app control violations:
|
Icon |
Description |
|
|
|
|
|
|
|
|
|
|
|
App Control for Windows 10 Desktop devices
This feature is for Windows 10 Desktop only.
AppLocker allows administrators to block specific apps from being downloaded or executed. You can block apps by using one of the following two approaches:
- Excluding apps (blacklist) - specifying apps to block.
- Including apps (whitelist) - Identifying allowed apps and excluding all other apps not on the list and all systems not defined by the administrator.
Use the dynamic lookup feature to include Publisher/PFN (Product Family Name) from the Microsoft store to include or exclude apps to security policies.
Creating a rule to block apps from Windows 10 desktop devices
This section covers how to create an app control rule excluding specified apps using dynamic lookup. This procedure describes:
- Using dynamic lookup to create a rule (called Blacklist) that excludes specified apps.
- Applying the Blacklist rule to a security policy.
Procedure
- In the Ivanti EPMM Admin Portal, go to Apps > App Control > Add. The Add App Control Rule dialog box opens.
- Enter Blacklist in the Name field as the name of the rule.
- Select Disallowed for the Type option.
- Select Publisher/PFN Equals from the App drop-down.
Leave the App Identifier/Name blank. - Select Windows from the Device Platform drop-down.
The Windows icon appears next to the Comment field when you select Windows as the platform.
- Click the Windows icon to open the Windows Store Search dialog box.
- Click the Windows option.
- Locate the app and click the Select button to automatically insert the PFN into the App Identifier/Name field.
- (Optional) Click the green plus (+) sign to add more apps to the rule, as necessary.
-
Click Save.
When editing the App Control Rules dialog box, upon clicking Save, you will be asked to confirm your changes.
Applying a rule to block apps from Windows 10 desktop devices
When you block an app that is in use and installed from the Microsoft Store, the app will continue to run until users close it. When users open a blocked app, Windows displays a message informing users that the app has been blocked by their system administrator. Ivanti EPMM sends instructions to the OS to block the specified app(s).
When users try to install a blocked app, they will see a message that the app has been blocked due to company policy.
Procedure
- In the Ivanti EPMM Admin Portal, go to Policies & Configs > Policies.
- Select Default Security Policy and click Edit.
- Scroll to the For Windows Devices section in the Access Control group.
- Click the box next to Application Restrictions and select Blacklist from the drop-down.
- Click Save.
Identifying the GUID for a Windows Phone app
The GUID is a unique number that identifies the app in the Microsoft ecosystem. In the Windows Phone Store, select the app. The URL for the app includes the GUID. The GUID is the alpha numerical section at the end of the URL.
Example:
http://www.windowsphone.com/en-us/store/app/netflix/c3a509cd-61d6-df11-a844-00237de2db9e
In the example, the GUID is c3a509cd-61d6-df11-a844-00237de2db9e.