Certificates overview
Ivanti EPMM is capable of distributing and managing certificates. Certificates are mainly used for the following purposes:
- Establishing secure communications
- Encrypting payloads
- Authenticating users and devices
Certificates establish user identity while eliminating the need for users to enter user names and passwords on their mobile devices. Certificates streamline authentication to key enterprise resources, such as email, Wi-Fi, and VPN. Some applications require the use of certificates for authentication.
Ivanti recommends to allow HTTPS traffic on port 8443 from the corporate network, limited to Ivanti applications only. This service is intended for EPMM server management and must have strictly controlled access.
The following diagram compares a certificate to a passport:
Figure 1. Comparing certificates to a passport

The certificate includes information that identifies the following information:
- The issuing certificate authority
- Acceptable uses for the certificate
- Information that enables the certificate to be validated.
This solution provides the flexibility to use Ivanti EPMM as a local certificate authority, an intermediate certificate authority, or as a proxy for a trusted certificate authority.
Types of certificates
Ivanti EPMM uses the following types of certificates:
|
Certificate type |
Description |
|
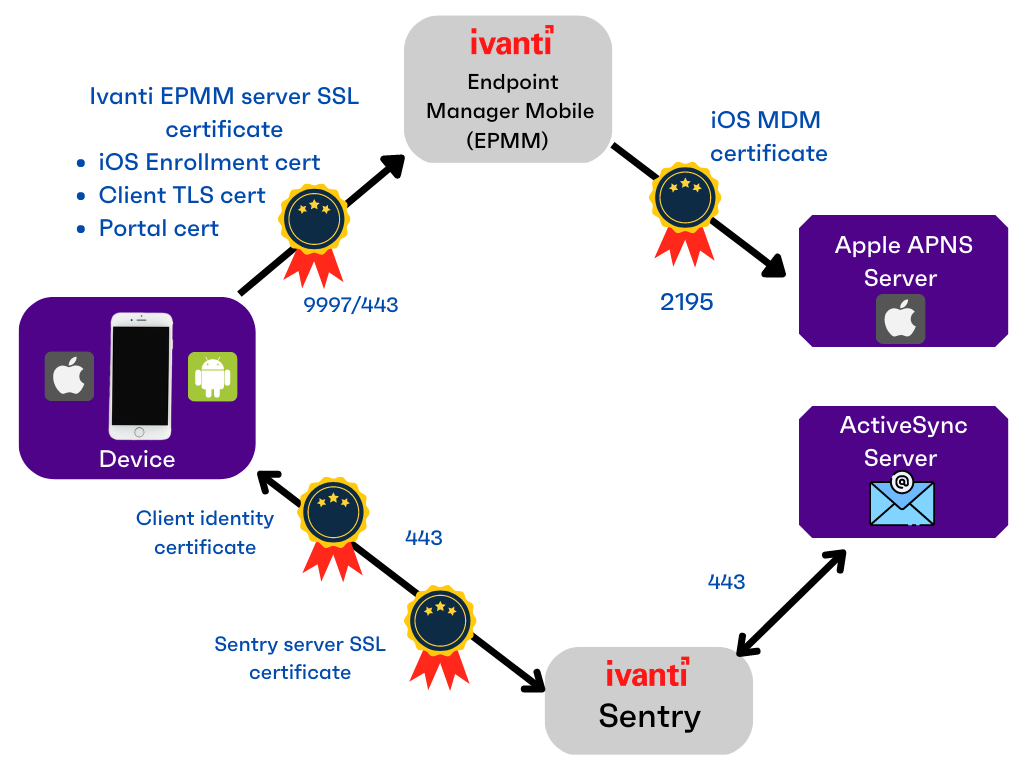
Portal HTTPS |
The identify certificate and its certificate chain, including the private key, that identifies Ivanti EPMM, allowing a client (such as a browser or app) to trust Ivanti EPMM. Typically, this certificate is the same certificate as the Client TLS and iOS Enrollment certificates. Ivanti EPMM sends this certificate to the client as part of the TLS handshake over port 443 or 8443 when the client initiates a request to Ivanti EPMM. This certificate must be a publicly trusted certificate from a well-known Certificate Authority if you are using mutual authentication. “Certificates you configure on the System Manager” in the Ivanti EPMM System Manager Guide. |
|
Client TLS |
The identify certificate and its certificate chain, including the private key, that identifies Ivanti EPMM, allowing Ivanti Mobile@Work for iOS and Android to trust Ivanti EPMM. Typically, this certificate is the same certificate as the Portal HTTPS and iOS Enrollment certificates. Ivanti EPMM sends this certificate to Ivanti Mobile@Work for iOS or Android as part of the TLS handshake over port 9997 when Ivanti Mobile@Work initiates a request to Ivanti EPMM. “Certificates you configure on the System Manager” in the Ivanti EPMM System Manager Guide. |
|
Ivanti EPMM server SSL |
Can be either self-signed or third-party certificates. By default, Ivanti EPMM generates self-signed certificates. You can use trusted certificates from third-party certificate providers such as Verisign, Thawte, or Go Daddy. Kerberos and Entrust certificates are also supported. |
|
Sentry server SSL |
Identifies the Sentry to the client and secures communication, over port 443, between devices and the Sentry. |
|
TLS trust certificate chain for mobile management (formerly known as the iOS MDM certificate) |
Allows iOS mobile devices to trust requests from Ivanti EPMM. Validates profile authenticity for iOS. Enables the MDM feature set for iOS devices. Uses port 2195 to communicate with Apple APNS. |
|
iOS Enrollment |
The identify certificate and its certificate chain, including the private key, that identifies Ivanti EPMM. Ivanti EPMM uses this identity certificate to sign the Apple MDM configurations that it sends to iOS and macOS devices. Typically, this certificate is the same certificate as the Client TLS and Portal HTTPS certificates.
|
|
Client identity |
Verifies the identity of users and devices and can be distributed through Certificate Enrollment. |
The following diagram illustrates where each certificate type is used in the Ivanti EPMM architecture:
Figure 2. Certificate types in the Ivanti EPMM architecture