Custom compliance policies
Ivanti EPMM provides security policies for 10 static definitions to mark a device as non-compliant. These policies have limited customization options, but are a quick and easy way to begin to set up compliance policy rules. The Compliance Policies feature allows administrators to define their own criteria for marking devices non-compliant. They can combine dozens of device and user fields to create non-compliant matching criteria.
Compliance policy rules use the Advanced Search filter criteria to define non-compliant devices. Each compliance policy rule has a filter criteria and an associated compliance action object. Access compliance policies by selecting Policies & Configs > Compliance Policies from the Admin Portal.
Ivanti EPMM uses custom device and user attributes to set up compliance policy rule conditions. These settings, listed under Devices & Users > Devices > Advanced Search > User Fields > LDAP > User Account Control in the Admin Portal, are:
- Account Disabled
- Locked Out
- Password Expired
Compliance policies are enforced by Ivanti EPMM during device check-in.
The work flow to set up and use compliance policies is:
- Assigning compliance roles
- Managing compliance policy rules
- Managing compliance policy groups
- Device search fields for compliance rules
Assigning compliance roles
The following describes how to assign compliance roles.
Procedure
- Log into the Admin Portal.
- Go to Admin > Admins.
- Select a user then select Actions > Edit Roles.
- Select an Admin Space.
-
Scroll down the window to the Compliance Policy Management section.
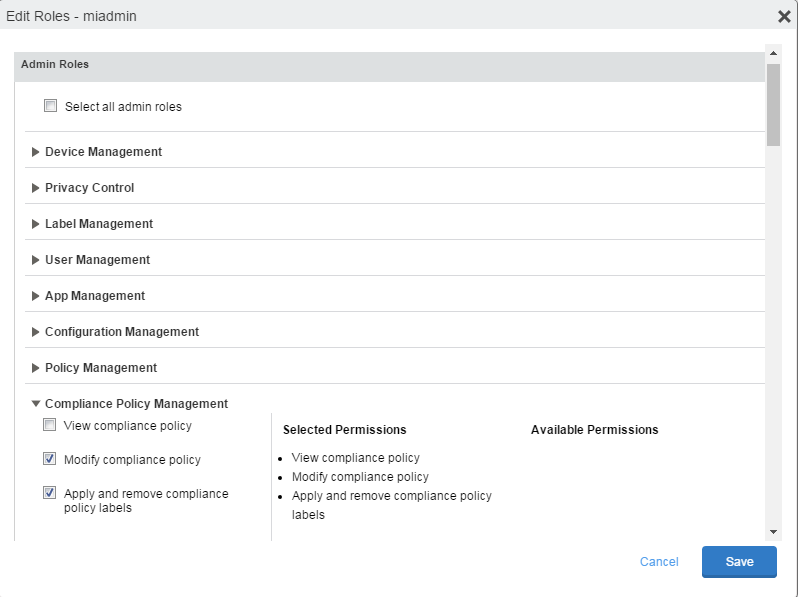
- Select one or more of the roles:
- View compliance policy: Allows the selected user to view rules, groups, lists, and configuration.
- Modify compliance policy: Allows the selected user to create, edit, and delete rules and groups.
- Apply and remove compliance policy labels: Allows the selected user to add or remove groups from labels.
- Scroll to the Settings and Services Management section.
- Select View settings and services.
- Select Save.
Managing compliance policy rules
Compliance policy rules are the building blocks in compliance policy groups used to manage device compliance. Administrators create compliance policy groups, add compliance policy rules to the groups, apply the groups to labels pushed to devices. Administrators can create a group with no rules or add compliance policy rules while creating the compliance policy group, if rules have already been created. They can also modify the group, including the name, description, and selected rules. This section describes:
- Creating compliance policy rules
- Substitution variables for compliance policy rules
- Viewing and modifying compliance policy rules
- Deleting compliance policy rules
- Searching for compliance policy rules
Creating compliance policy rules
A single rule can be in multiple compliance policy groups.
Procedure
- Go to the Admin Portal.
- Select Policies & Configs > Compliance Policies.
- Select Compliance Policy Rule tab and then select Add+.
- Add a unique name in the Rule Name field.
- Select the Status to Enabled or Disable.
- Enter a description of the rule if desired.
-
Build a Condition using Advance Search to define non-compliance. For a list of definitions / values of the items to search on, see Advanced searching .
It is recommended to have one Condition set to include when Ivanti Mobile@Work last checked in within the last 30 days. See the TIP below.
- In the Compliance Actions field, select from the drop-down to use on devices matching the condition.
- If you don't want the search results to include retired devices, select the Exclude retired devices from search results check box.
- Select Save.
TIP - We recommend that you create a Compliance Policy rule with one condition set to include when Ivanti Mobile@Work last checked in with Ivanti Endpoint Manager Mobile. This is helpful if you need assurance that Ivanti Mobile@Work is running on devices (for example, for use in Mobile Threat Defense).
Procedure
- Go to the Admin Portal.
- Select Policies & Configs > Compliance Policies.
- Select Compliance Policy Rule tab and then select Add+.
- Enter ClientLastCheckIn in the Rule Name field.
- Enter Condition > All.
-
Go to Field and type in "Client Last Check-In" or select Common Fields > Client Last Check-In.
The regular expression is listed below; green check mark indicates regular expression is accepted.
- Select within the last in the Value field; enter 30 days in the remaining two fields.
-
Keep the default setting of Exclude retired devices from search results.
- In the Compliance Actions field, select Send Alert from the drop-down.
-
Select Save.
Substitution variables for compliance policy rules
The following table lists the substitution variables for compliance policy rules.
|
Category |
Substitution variable |
|
Compliance policy rule customized message |
The substitution variables are available for use in compliance policy rules for all devices. To use in a compliance action message, copy/paste the variable into the Message field.
|
Viewing and modifying compliance policy rules
You can view or modify a compliance policy rule. Viewing a rule requires the View role and modifying a rule requires the Modify role.
You can modify a rule without removing it from an assigned group. For instance, you can change its status from Enabled to Disabled to troubleshoot it. When you modify a rule, the change is applied to all the groups that use the rule.
Procedure
- Go to the Admin Portal.
- Select Policies & Configs > Compliance Policies > Compliance Policy Rule.
- Select the name of the rule you want to modify and select Edit.
- Modify details, as necessary, including disabling the rule.
- Select Save.
Deleting compliance policy rules
Procedure
- Go to the Admin Portal.
- Select Policies & Configs > Compliance Policies > Compliance Policy Rule.
- Select the name of one or more rules to delete.
- Select Actions > Delete.
Searching for compliance policy rules
Procedure
- Go to the Admin Portal.
- Select Policies & Configs > Compliance Policies > Compliance Policy Rule.
- Enter a name in the search field.
- Use one of the following filters:
- All
- Enabled
- Disabled
- Select Search.
Managing compliance policy groups
Compliance policy groups are applied to devices to manage device compliance. Administrators create compliance policy groups, add compliance policy rules to the groups, apply the group's rules to devices matching the label criteria.
Administrators can create a group with no rules or add compliance policy rules while creating the compliance policy group, if rules have already been created. They can also modify the group, including the name, description, and selected rules. This section describes:
- Creating compliance policy groups
- Modifying compliance policy groups
- Adding compliance policy rules to a group
- Applying compliance policy groups to labels
- Removing compliance policy groups from labels
- Deleting compliance policy groups
- Searching for compliance policy groups
Creating compliance policy groups
You can create a group without adding rules, which can be added later. One rule can be member of multiple groups.The following provides the steps to add one or more compliance policy rules to a compliance policy group.
Procedure
- Go to the Admin Portal.
- Select Policies & Configs > Compliance Policies.
- Select Compliance Policy Group tab.
- Select Add+. The Add Compliance Policy Group page displays.
- Enter a unique name in the Group Name field.
- Select Enabled in the Status field.
- Move one or more rules from Available Rules to the Selected Rules list.
- Select Save.
Modifying compliance policy groups
The following provides the steps to modify compliance policy groups.
Procedure
- Go to the Admin Portal.
- Select Policies & Configs > Compliance Policies > Compliance Policy Group.
- Select the name of the group you want to modify.
- Modify details, as necessary, including the name, description, or to enable or disable the group.
- Select Save in the Details section.
- Select Edit in the Rules section.
- Modify rules, as necessary, by adding or removing rules.
- Select Save in the Rules section.
Adding compliance policy rules to a group
One rule can be a member of multiple groups. This procedure requires that you have already created one or more rule. See Creating compliance policy rules for details.
Procedure
- Go to the Admin Portal.
- Select Policies & Configs > Compliance Policies > Compliance Policy Group.
- Double-select the name of the group to which you want to add one or more rules.
- Go to the Rules section and select Edit.
- Move one or more rules from the Available Rules list to the Selected Rules list.
- Select Save in the Rules section.
Applying compliance policy groups to labels
Once a group (and its underlying rules) is assigned to devices, status of the devices are evaluated based on the conditions in the rules for compliance. Compliance Policy rules are evaluated against each device in the following ways:
- During device check-in
- Periodically, during the compliance policy check interval. This is set at Policies & Configs > Compliance Actions > Preferences.
- When a manual Check Compliance is initiated by the administrator. This can be set at Policies & Configs > Compliance Actions > Check Compliance or on the Devices page under Actions.
Procedure
- Go to the Admin Portal.
- Select Policies & Configs > Compliance Policies > Compliance Policy Group.
- Select the name of the compliance policy group you want to apply to label.
- Select Actions > Apply to Labels.
- Select one or more of the labels.
- Select Apply.
Removing compliance policy groups from labels
Once a group (and its underlying rules) is assigned to devices, status of the devices are evaluated based on the conditions in the rules for compliance. The following describes the steps to apply a compliance policy groups to one or more labels.
Procedure
- Go to the Admin Portal.
- Select Policies & Configs > Compliance Policies > Compliance Policy Group.
- Select the name of the compliance policy group you want to remove from a label.
- Select Actions > Remove from Labels.
- De-select one or more of the labels.
- Select Apply.
After the next device check in, these changes will apply.
Deleting compliance policy groups
The following provides the steps to delete one or more compliance policy groups.
Procedure
- Go to the Admin Portal.
- Select Policies & Configs > Compliance Policies > Compliance Policy Group.
- Select the name of one or more groups to delete.
- Select Actions > Delete.
Searching for compliance policy groups
The following provides the steps to search for compliance policy group.
Procedure
- Go to the Admin Portal.
- Select Policies & Configs > Compliance Policies > Compliance Policy Group.
- Enter a name in the search field.
- Use one of the following filters:
- All
- Enabled
- Disabled
- Select Search.
Device search fields for compliance rules
This section includes the compliance action objects the compliance policy rules use for device search fields. In addition to the fields listed in the below table, any Custom Device Attributes or Custom User Attributes that were added in Settings > System Settings > Users & Devices > Custom Attributes will also be available for searching.
The following table lists the available objects, including:
- Common fields
- Custom fields
- Android devices
- iOS devices
- Windows devices
- User fields (including LDAP fields)
|
Category |
Compliance policy objects |
|
Common |
The following search fields are available for use in compliance rules for all devices: |
|
Android |
The following search fields are available for use in compliance rules for all Android devices: |
|
iOS |
The following search fields are available for use in compliance rules for all iOS devices: |
|
Windows |
The following search fields are available for use in compliance rules for all Windows devices: |
|
User |
The following search fields are available for use in compliance rules user-related fields, including LDAP: |
Independent, customized messages and email subject for each compliance action tier
In previous releases, only one customized message could be sent for all Compliance Action tiers supported in Compliance Policies > Compliance Policy Rule. Starting in this release, administrators have the ability to create and send independent, customized messages and email subject lines for each of the now 20 possible Compliance Action tiers.
Compliance actions are categorized as:
-
V1, which are compliance actions that existed in Ivanti EPMM before Version 11.8.0.0.
-
V2, which are compliance actions that are created starting in Ivanti EPMM 11.8.0.0.
The following table compares compliance actions between V1 (pre-version 11.8.0.0) and V2 (Version 11.8.0.0+):
|
Compliance actions Version 1 |
Compliance actions Version 2 |
|
Uses even center for alert-related settings. |
Actions cannot use the event center configuration. Instead, all the settings related to alerts, message languages, and so on, are available in the action page in the Settings tab. |
| Compliance action messages are configured at rule level. Only one message can be configured for all tiers in an action |
Compliance action messages can be configured in each tier. |
|
Uses only single alert messages across all tiers in the action. |
Administrators can configure alert messages and subjects in multiple languages selected in the action settings. The system default language is mandatory and cannot be ignored or removed. Once an administrator selects languages, they must enter the subject and message for all the selected languages. When the system dispatches messages to the devices, it picks the language specified in the device locale. If the device-specific locale is not configured in the action page, the system default language (for example, English) is used. For example, if an administrator configures messages in French and English, but the device locale (German), has not been configured, the subject and messages use the system default language (English) in alerts. |
|
Uses event center. |
Administrators can configure different messages for each tier in multiple languages and configure the alert severity levels and alert frequency settings for each tier in an action. Alert recipients and message languages can be configured at an action level in the compliance action page > Settings tab. |
|
Existing behavior is unchanged. |
For V2 actions, the maximum length of the message = 800 chars, including substitution variables. The maximum length of the subject = 150 chars, including substitution variables. |
|
After upgrading to Ivanti EPMM 11.8.0.0, existing V1 actions can be used. New V2 actions can also be used. New actions can only be created as V2 actions. Administrators can upgrade/migrate V1 actions to V2 actions. When they edit V1 actions, they can apply V2 action features to V1 actions and upgrade/migrate the V1 action to a V2 action using the Upgrade to New Compliance Action checkbox in the Edit Compliance Action page. This upgrade is non-reversible, that is, the upgraded/migrated V1 cannot be reverted if it has been successfully migrated to V2. |
After upgrading/migrating to Ivanti EPMM 11.8.0.0, new actions can only be created as V2 actions. |
|
Supports templates in the event center. |
Templates Administrators can insert the following variables (that are exposed in the Insert Variable section) in the subject and message content:
|
|
Supports templates in the event center. |
Templates Administrators can insert the following variables (that are exposed in the Insert Variable section) in the subject and message content:
|
|
Existing behavior is unchanged. |
Alert frequency time has granularity to hours and days. For example, administrators can send up to 5 alerts in 5 hours, or 10 alerts in 2 days. Two days duration = 24 * 2 = 48 hours. Delay of the next tier should be greater than or equal to the Sendupto value of the current tier in the V2 action. |
|
|
After upgrading to Ivanti EPMM 11.8.0.0+, a default system-generated event of type Compliance Rule Violation Event is generated in the EventSettings page. This event cannot be edited or deleted. |
|
|
When a compliance policy rule violation occurs, the system uses tier-specific alert preferences. Security policies continue to use the alert preferences from the event center. |