Outgoing SSL configuration
For Ivanti Neurons for MDM, cipher suites and protocols configuration is done in the Sentry profile on Ivanti Neurons for MDM.
The Outgoing SSL Configuration page Allows administrators the flexibility to configure Standalone Sentry to use cipher suites and protocols to match the security and system needs of your enterprise.
Use the Outgoing SSL Configuration page to configure ciphers and protocols for outgoing traffic from Ivanti Standalone Sentry to backend resources. You can do the following:
- Enable Strict TLS settings for Standalone Sentry SSL connections to backend resources.
- Enable SNI.
- View the Available and Selected protocols and cipher suites.
- Set up custom protocol and cipher suite configuration.
The default ciphers and protocols are colored blue.
Enable Strict TLS
You can enable strict TLS for outgoing traffic from Ivanti Standalone Sentry to backend resources. Strict TLS is not enabled by default. When you enable strict TLS, the Java Trust Store is enabled by default. You can also use the custom trust store option to upload additional certificates that Ivanti Standalone Sentry should use.
Server hostname verification with strict TLS
If strict TLS is enabled, Ivanti Standalone Sentry provides an additional layer of security by also verifying the server hostname. Server hostname verification is automatically enabled if Enable Server TLS is checked.
Impacts of server hostname verification
If the server’s hostname does not match the hostname in the server’s certificate, connection to the server will fail. The following connection error will be seen in Ivanti Standalone Sentry logs and in System Manager > Monitoring:
"Got exception during device-to-server processing, Sentry reporting error to client:server name mismatch, certificate issued to: [s01-trvlr-001]"
Workaround: If there is a mismatch in the server hostname and hostname in the server’s certificate, upload a new certificate that contains the correct hostname to the server, or disable strict TLS.
TLS settings for Ivanti Standalone Sentry in Ivanti EPMM
To enable strict TLS for outgoing traffic from Standalone Sentry, you should have also checked Enable Server TLS under ActiveSync Configuration or TLS Enabled under AppTunnel Configuration. These settings are configured in Services > Sentry in the Ivanti EPMM Admin Portal.
If none of the service use TLS, the Outgoing SSL Configuration settings do not persist even if a change is made in the GUI.
SNI
Server Name Indication (SNI) is an extension to TLS. SNI allows multiple hostnames to be served over HTTPS from one IP address. By default, SNI is disabled on Ivanti Standalone Sentry for outgoing connections.
SNI allows a load balancer to direct incoming traffic to the correct backend server based on the hostname provided by the client, in this case, Ivanti Standalone Sentry. Some backend server may require that SNI is enabled in the client.
Your Active Directory Federation Services (ADFS) may require SNI for all client communications.
If SNI is enabled for Outgoing SSL connections, in some cases health check may fail if the backend server does not also support SNI. The workaround is to disable health check for the impacted server.
Cipher suites and protocols
Ivanti Standalone Sentry includes a set of cipher suites and protocols. A default set of cipher suites and protocols is available in the Selected column. You can customize the Selected list of ciphers and protocols to match the security and system needs for your enterprise.
The available and default set of cipher suites and protocols may be updated in a release. Some cipher suites and protocols may be added, while others may be removed. Cipher suites and protocols may be removed if the platform no longer supports these cipher suites and protocols.
If you are set up to use the default cipher suites and protocols, these will be updated to the latest defaults when you upgrade to a new version of Ivanti Standalone Sentry. If you are set up to use a custom list of Selected cipher suites and protocols, the custom list is preserved when you upgrade your Ivanti Standalone Sentry. However, any cipher suites or protocols that were removed will also be removed from the Selected and Available columns. New cipher suites and protocols will be added to the Available column.
Making changes to the selected list of cipher suites may impact the performance and security of traffic through Ivanti Standalone Sentry. Therefore, before making any changes to the Selected cipher suites, Ivanti recommends that you understand both the performance and security impact of the changes.
Supported protocols
- TLSv1.2 (Selected by default)
- TLSv1.1
- TSLv1
- SSLv2Hello
- SSLv2Hello is a pseudo-protocol that allows Java to initiate the handshake with an SSLv2 'hello message.' This does not cause the use of the SSLv2 protocol, which is not supported by Java. SSLv2Hello requires that TLSv1 protocol is also selected.
- SSLv2Hello is required by some load balancers and SSL off loaders for proper functioning. If your environment does not need it, it is recommended to remove this from the protocol list for improved security.
Enabling strict TLS
You can enable strict TLS and other trust settings for traffic from Ivanti Standalone Sentry to backend resources.
Procedure
-
In the Ivanti Standalone Sentry System Manager, go to Settings > Services > Sentry > Outgoing SSL Configuration.
-
In the Strict TLS Settings section, check Enable Strict TLS.
Additional options are now available.
Table 21. Enable Strict TLS options Item
Description
Enable Default Java Trust Store
Selected by default if strict TLS is enabled.
Certificates and Certificates Authorities in the Java Trust Store are used to trust the SSL connection to the backend resource.
Allow and Log untrusted servers
Select to allow Ivanti Standalone Sentry to connect to a backend resource that does not use a trusted certificate in Java or custom trust store.
Enable Custom Trust Store
Select to upload certificates to the Ivanti Standalone Sentry trust store. Ivanti Standalone Sentry will use the certificates in the custom store to trust backend resources.
Generally used if backend resources use self-signed certificates.
-
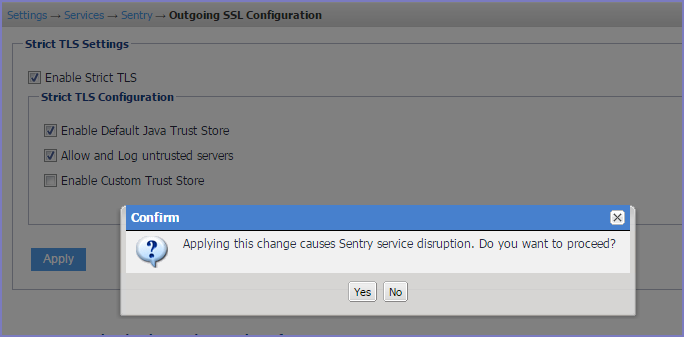
Click Apply.
Confirm TLS setting change.
Figure 1. Confirm TLS settings change
-
Click Yes.
The new TLS settings are applied and Ivanti Standalone Sentry restarts. It may take up to one minute for Ivanti Standalone Sentry to restart. Traffic will be disrupted till Ivanti Standalone Sentry is up and running again.
- Click OK.
Enabling Server Name Indication (SNI)
You can enable SNI for Standalone Sentry outgoing connections.
Procedure
- In Ivanti Standalone Sentry System Manager, go to Settings > Services > Sentry > Outgoing SSL Configuration.
- Click the Enable SNI check box.
- Click Apply.
Creating a custom cipher configuration
You can customize the protocols and cipher suites the Ivanti Standalone Sentry will use.
Procedure
-
In Ivanti Standalone Sentry System Manager, go to Settings > Services > Sentry > Outgoing SSL Configuration.
Ciphers and protocols are configured in the Sentry to Backend Ciphers and Protocols Configuration section.
The Use Default Cipher Suites and Protocols (recommended) option is selected by default.
-
Select Use Custom Configuration.
-
Click on Proceed to continue.
-
Select the protocols and cipher suites to move from the Available to Selected column or vice-versa as necessary.
The default cipher suites and protocols are colored blue.
-
Click Apply to apply the changes.
When Use Default Cipher Suites and Protocols (recommended) is selected, the cipher suites and protocols can be moved between the Available and Selected columns. However, the configuration is not changed. You must also select the Use Custom Configuration option to make changes to the default configuration.
Switching back to default configuration
You can revert your settings to default configuration if you do not wish to use the custom configuration.
Procedure
-
In Ivanti Standalone Sentry System Manager, go to Settings > Services > Sentry > Outgoing SSL Configuration.
-
In the Sentry to Backend Ciphers and Protocols Configuration section, select Use Default Cipher Suites and Protocols (recommended).
-
Click Apply to apply the changes.
The cipher suites and protocols are reset to the default settings.
Clicking on Reset to Default resets the Available and Selected columns to default settings. However, the default settings will not be applied. To apply the default settings, you must select Use Default Cipher Suites and Protocols (recommended), and then click Apply.