Key Distribution Center (KDC) discovery through DNS
With Kerberos authentication, Ivanti Standalone Sentry determines which Key Distribution Center (KDC) to communicate with to obtain a ticket for a user account. If the user is located in the same realm as Standalone Sentry, the configured KDC is used. If the user is not located in the same realm, by default, Ivanti Standalone Sentry attempts to locate a KDC through DNS discovery.
KDC discovery through DNS can be triggered by one of the following:
•The user's realm is different from that of Standalone Sentry.
•Even if the user's realm is the same as Standalone Sentry, the letter case in the realms do not match exactly.
•Sometimes, the KDC that is configured cannot be resolved.
The following provide additional information about KDC discovery:
| • | KDC discovery in a cross-realm Kerberos environment. |
•Disabling Key Distribution Center (KDC) discovery through DNS.
•Configuring additional Kerberos realms.
KDC discovery in a cross-realm Kerberos environment
In a cross-realm environment, discovery through DNS could be slow and even fail. This may result in failure to get a ticket. DNS discovery may be slow or fail due to the following reasons:
•The response may contain a very large list of all KDCs known to that DNS server. Going through a large set of records may take a long time.
•The topology of customer's network and access rules and firewall configuration may block or slow access to KDC servers, and Ivanti Standalone Sentry may eventually give up. Thus, failing to acquire a ticket.
To better manage the ticketing process in a cross-realm Kerberos environment, you can do the following:
•Disable KDC discovery through DNS.
•Configure additional realms, other than the Ivanti Standalone Sentry realm, and the associated KDC servers.
•If KDC discovery is disabled, you must configure additional Kerberos realms and the associated KDC servers.
•If KDC discovery is disabled, Standalone Sentry will fail to obtain a ticket in the following cases:
| - | the KDC server for a user’s realm is not configured in Standalone Sentry settings |
| - | the KDC servers for that realm are not accessible |
•If KDC discovery through DNS is enabled and if you have also configured additional KDC servers, Standalone Sentry will first check the configured KDC servers before doing KDC discovery through DNS.
In a cross-realm Kerberos environment, configuring Kerberos realms and the associated KDC servers:
•reduces the time required to get a ticket
•decreases the risk of failure to get a ticket
Disabling Key Distribution Center (KDC) discovery through DNS
Disabling KDC discovery through DNS allows you to better manage the ticketing process in a cross-realm Kerberos environment.
Procedure
| 1. | In the Ivanti EPMM Admin Portal, go to Services > Sentry. |
| 2. | Click on the Edit icon for the Sentry record that you will edit. |
| 3. | Scroll down to the Kerberos Authentication Configuration section. |
Figure 1. Disabling KDC discovery through DNS
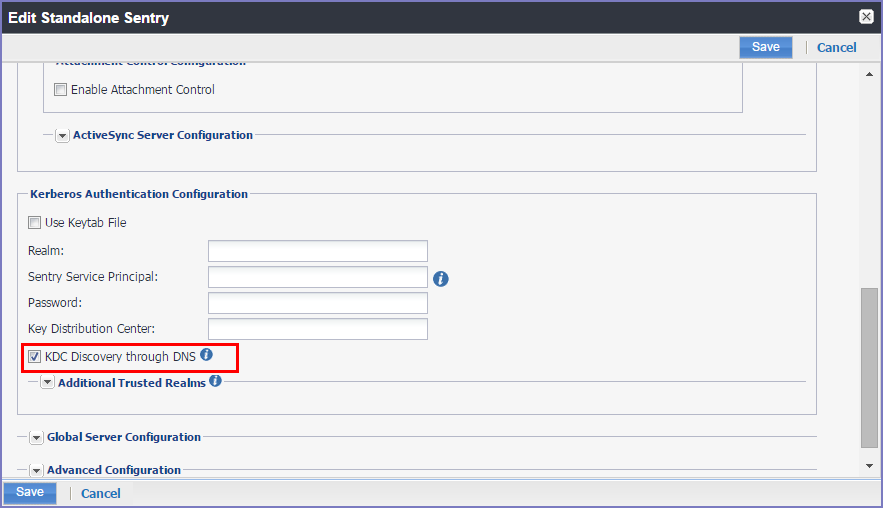
| 4. | De-select the KDC Discovery through DNS option. |
| 5. | Click Save to save the changes. |
KDC discovery in a cross-realm Kerberos environment.
Configuring additional Kerberos realms
You configure additional realms, other than the Standalone Sentry realm, and the associated KDC servers to better manage the ticketing process in a cross-realm Kerberos environment.
Procedure
| 1. | In the Ivanti EPMM Admin Portal, go to Services > Sentry. |
| 2. | Click on the Edit icon for the Sentry record that you will edit. |
| 3. | Scroll down to the Kerberos Authentication Configuration section. |
| 4. | Expand the Additional Trusted Realms section. |
Figure 2. Additional trusted realms
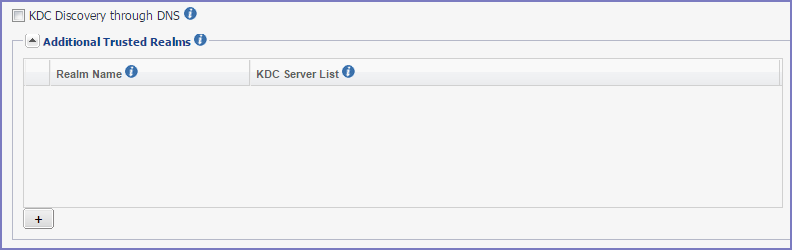
| 5. | Click + to add new Kerberos realm. |
|
Item |
Description |
|
Realm Name |
Enter a Kerberos realm name. Realm names are not case sensitive. |
|
KDC Server List |
Enter the associated KDC servers. You can enter domain name or IP address. Each domain name or IP address must be separated by a semicolon. If a port is not specified, the default port 88 is used. |
| 6. | Click Save to save the changes. |