Change firewall rules
This section describes the configuration settings relating to the firewall.
| NOTE: | For configuration settings relating to the Deployment components, see Internal Corporate Network Rules for firewall rules required for the internal corporate network. See External / Internal rules for which ports to open and also see Additional firewall rules. |
Windows device support requirements
Autodiscovery allows Windows devices to seamlessly register with MobileIron. The following set up is required for using autodiscovery with Windows devices:
-
Create DNS A record to point to MobileIron Core
-
Obtain a TLS/SSL SAN certificate from a trusted Certificate Authority (CA)
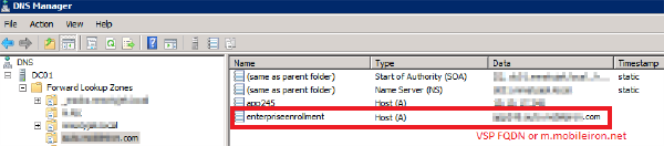
Create DNS A record
Create a DNS A record that refers DNS requests for enterpriseenrollment.YourCompanyDomainName.com to the MobileIron Core IP address.
| NOTE: | YourCompanyDomainName must match the domain of the email addresses used for registering with MobileIron. |
Figure 1. Enterprise enrollment
Obtain a TLS/SSL SAN certificate
For Windows devices, a Subject Alternative Name (SAN) TLS/SSL certificate from a trusted Certificate Authority (CA), such as Verisign or GoDaddy, is required. If you use a self-signed (localCA) certificate, device enrollment will fail.
-
The TLS/SSL certificate provides trusted and secured connection without certificate warnings.
-
A SAN certificate, also known as a multi-domain certificate or a unified communication certificate, is valid for two or more hosts. The SAN certificate must cover the MobileIron Core hostname and enterprise enrollment.YourCompany-Domain name.com.
Connecting to the Windows Store
You can set up recommended apps that device users can download from the Apps@Work app.
For Windows devices, your firewall must allow connections to the following hosts:
-
https://www.windowsphone.com (Port 443)
-
http://marketplaceedgeservice.windowsphone.com (Port 80)
-
http://cdn.marketplaceimages.windowsphone.com (Port 80)
AppConfig Community Repository outbound firewall port setting
Core requires outbound firewall access on TCP port 443 to https://appconfig.cdn.mobileiron.com/com.example.OneTouchConfiguration/current/appconfig.xml for the Managed App Configuration UI to render properly.
Additional outbound access links:
-
https://api.appthority.com/applications/bulk_query (Appthority)
-
https://api.mqcdn.com/sdk/mapquest-js/v1.0.0/mapquest.css (for the find my phone mapping and etc options)
-
pki-ws.symauth.com (SymantecManagedPKI)
-
https://onestore.microsoft.com (Business Store Portal (BSP))
-
https://bspmts.mp.microsoft.com/V1 (Business Store Portal (BSP))
-
https://mobility.threatpulse.com:9443 (BlueCoat)
-
https://login.microsoftonline.com/{tenant_id}/oauth2/authorize (Microsoft Graph)
-
https://eu-api.samsungknox.com (Samsung E-FOTA)
-
https://has.spserv.microsoft.com/HealthAttestation/ValidateHealthCertificate/v1 (Windows device attestation)
-
https://webapi.teamviewer.com/api/v1/ (Android Help@Work)
-
https://system.globalsign.com/cr/ws/GasOrderService (GlobalSign)
-
https://appconfig.cdn.mobileiron.com (iOS Managed AppConfig community)
-
https://graph.windows.net/%s/devices/deviceId_%s?api-version=1.6 (Azure active directory)