Known issues
For known issues found in previous releases, see the "Known issues" sections in the release notes for those releases, available in MobileIron Core Product Documentation.
This release includes the following known issues:
- VSP-62373: For Apple-licensed apps that will be used by both User Enrolled devices and Device Enrolled devices, the license type should be set to Device-based licenses. Devices enrolled with DEP or Device Enrollment where the Apple-licensed app is set to user-based licenses will show the app as "Free" instead of "Prepaid" and the app will fail to install. User enrolled devices will always have the Apple-licensed app assigned as a user-based license regardless of this setting.
-
VSP-62367: When an MTD anti-phishing configuration with Content Blocker enabled is created and pushed to an iOS device running Mobile@Work prior to release 12.3.0, the user receives a prompt to enable the Content Blocker. If Content Blocker is enabled on the device but is later disabled, the user does not receive another prompt to enable it.
Workaround: Upgrade to Mobile@Work release 12.3.0.
-
VSP-62314: When Content Blocker is disabled for a device, the updated status for that device on the Core > Devices > Devices & Users page should be "N/A" and not "Active." The device displays "N/A" when the anti-phishing policy is removed from the device.
-
VSP-62263: There is an issue when pushing the Security Policy for macOS version 10.13 or later to devices with "Enabling Enforce Password Rule at Next Login" enabled. Any modification of the security policy will require users to change their password when it is pushed to their device.
-
VSP-62256: In a few cases, MobileIron Access-enabled Tunnel profiles are not displayed or synced on Access. Please contact the MobileIron support team to determine if any of the Android Enterprise configuration IDs match the missing Tunnel profile ID. If yes, delete and recreate the Tunnel configuration on Core.
-
VSP-62233: When an Apple Device Enrollment client is installed as a Sideloaded App, and the client is Authenticator Only enabled, two device entries are created—one as an Apple Device Enrollment device, and another as an Authenticator Only client device.
-
VSP-62216: If transport layer security (TLS) is enabled for the MobileIron Connector, the root certification must be uploaded to Core. Without this certification, Core will display an error message.
-
VSP-62209: Core does not display or allow the re-upload of certificates in .pfx and .p12 formats that are uploaded using LDAP certificate-based authentication.
-
VSP-62183: The System Manager's certificate-based authentication does not make a Certificate Revocation List (CRL) check after a CRL download request fails.
Workaround: Restart the Tomcat2 (System Manager) service, so it will attempt to download the CRL again.
-
VSP-62182: The MobileIron System Manager allows certificate-based authentication when a Certificate Revocation List (CRL) is not accessible. There is currently no option to configure allowing or blocking certificates when a CRL is not accessible.
-
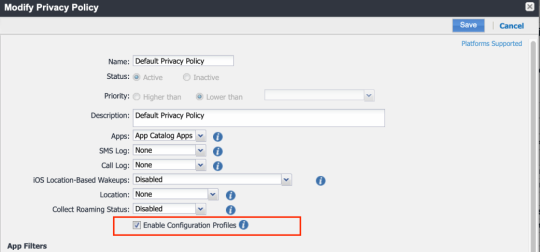
VSP-62007: For threat detection and mitigation to work for devices in mobile application management (MAM)-only mode, you must click Enable Configuration Profiles in the Policies & Configs > Policies > Privacy Policy menu.
-
VSP-62004: Android device registrations fail on Core servers with both FIPS mode and SafetyNet enabled. The only workaround is to disable SafetyNet attestation.
-
VSP-61962: MobileIron Access Session Revocation Service (SRS) will fail to revoke Office 365 session tokens if the LDAP user principal configured in MobileIron Core contains uppercase letters.
Workaround: Change the LDAP user principal to lowercase letters.
-
VSP-61699: The MTD sinkhole VPN and the MTD anti-phishing VPN are not removed from the device when the MTD License is inactivated.
-
VSP-61552: When Samsung Knox devices are enabled on the same Core server as AppConnect, the devices are erroneously deployed as Authenticator Only devices.
-
VSP-61539: If a supervised device is enabled for Authenticator Only mode, the device registers as Authenticator Only. It will register as supervised once Core updates.
-
VSP-60688: There is an issue with Apps@Work and AppConnect, where if the Certificate Expiry duration is shorter than the Renew duration, they become inaccessible.
Workaround: Ensure that the Certificate Expiry duration is greater than the Renew duration.