Certificate Mgmt
Use the Security > Certificate Mgmt menu items to fulfill certificate requirements your organization may have for the MobileIron appliance or the TLS client. With these options, you can:
- Generate a self-signed certificate
- Generate a CSR for a certificate authority
- Upload required certificates
| NOTE: | When you update a certificate, you are prompted to confirm that you want to proceed because the HTTP service needs to be restarted, resulting in service disruption. |
This section includes the following topics:
- Certificates you configure in the System Manager
- Generate a self-signed certificate
- Certificate signing request (CSR) requirements
- Generate a certificate signing request (CSR)
- Upload client certificate (CSR) window
- Uploading certificates
- Viewing certificates
Certificates you configure in the System Manager
You configure the following certificates on the System Manager at Security > Certificate Mgmt:
|
Certificate |
|
|||
|
Portal HTTPS Port 443 and 8443 |
|
|||
|
Client TLS Port 9997 |
|
|||
|
iOS Enrollment |
|
Generate a self-signed certificate
You can generate a self-signed certificate for:
- the MobileIron iOS Mobility Management Best Practices
- the MobileIron Sentry configurations
- The Portal HTTPS certificate, the Client TLS certificate, or the iOS Enrollment certificate.
Procedure
- Log into System Manager.
- Go to Security > Certificate Mgmt.
- Select Manage Certificate in either the Portal HTTPS row, the Client TLS row, or the iOS Enrollment row.
- Select Certificate Options > Generate Self-Signed Certificate.
-
Click one of the following self-signed certificate options:
- Generate Self Signed RSA Certificate
- Generate Self Signed ECDSA Certificate
Certificates you configure in the System Manager
Certificate signing request (CSR) requirements
The following table summarizes the requirements and related information for each component of a MobileIron deployment.
|
Component |
Requirements |
|
Appliance |
Private key file Certificate file Root CA certificate file Without password |
|
Standalone Sentry |
Private key file Certificate file Root CA certificate file Without password |
|
Client |
Private key file Certificate file Root CA certificate file Without password |
Generate a certificate signing request (CSR)
Procedure
- Log into System Manager.
- Go to Security > Certificate Mgmt.
- Select Manage Certificate in either the Portal HTTPS row, the Client TLS row, or the iOS Enrollment row.
- Select Certificate Options > Generate CSR.
-
Fill in the form, as necessary.
Refer to Upload client certificate (CSR) window table for details.
-
Click Generate.
The system displays a message similar to the following message.
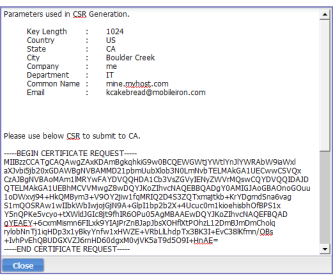
- Open a text file in a text editor or application.
- Copy the content between BEGIN CERTIFICATE REQUEST and END CERTIFICATE REQUEST and paste it into the text file.
- Open a second text file.
- Copy the content between BEGIN RSA PRIVATE KEY and END RSA PRIVATE KEY and paste it into the second text file.
- Click Close.
- Submit the text file you created in step 8.
Certificates you configure in the System Manager
Upload client certificate (CSR) window
The following table summarizes fields and descriptions in the Upload client certificate window:
|
Fields |
Description |
|
Common Name |
Enter the server host name. |
|
|
Enter the email address of the contact person in your organization who should receive the resulting certificate. |
|
Company |
Enter the name of the company requesting the certificate. |
|
Department |
Enter the department requesting the certificate. |
|
City |
Enter the city in which the company is located. |
|
State |
Enter the state in which the company is located. |
|
Country |
Enter the two-character abbreviation for the country in which the company is located. |
|
Key Length |
Select 2048 or 3072 to specify the length of each key in the pair. Longer keys provide stronger security, but may impact performance. |
Uploading certificates
You can upload a certificate after you receive the CA certificate from the certifying authority.
Procedure
- Log into System Manager.
- Go to Security > Certificate Mgmt.
- Select Manage Certificate in either the Portal HTTPS row, the Client TLS row, or the iOS Enrollment row.
- Select Certificate Options > Upload Certificate.
-
Select a certificate based on the following information:
Fields
Description
Key file
The file created in Step in Generate a certificate signing request (CSR)
Server certificate
The CA certificate file you received from the certifying authority.
CA certificate
A generic CA certificate file.
- Click Upload Certificate.
Certificates you configure in the System Manager
Viewing certificates
Use the Security > Certificate Mgmt menu items to view both Portal HTTPS or Client-TLS certificates.
Procedure
- Log into System Manager.
- Go to Security > Certificate Mgmt.
- Select View Certificate in either the Portal HTTPS row, the Client TLS row, or the iOS Enrollment row.