New features and enhancements summary
This section provides summaries of new features and enhancements available in this release of MobileIron
- General features and enhancements
- Android and Android enterprise features and enhancements
- iOS and macOS features and enhancements
- iOS and macOS features and enhancements
- MobileIron Threat Defense features
For new features and enhancements provided in previous releases, see the release notes for those releases, available in MobileIron Core Product Documentation. MobileIron Support credentials are required to access the site.
General features and enhancements
This release includes the following new features and enhancements that are common to all platforms.
-
Microsoft Intune Device Compliance Support added: MobileIron Core now supports Microsoft Intune device compliance. Organizations can update the device compliance status in the Microsoft Azure Active Directory (AAD.) Using conditional access from AAD, if the device is non-compliant, administrators can block the device from accessing apps. By connecting Core to Microsoft Azure, administrators will be able to use the device compliance status of MobileIron's managed devices for conditional access to Microsoft 365 apps. In Core, administrators will see the following changes:
-
The System Settings page has a new menu item in the left navigational pane > Microsoft Azure > Device Compliance for iOS & Android. There are new fields to assist with the reporting of device compliance status to Microsoft Azure.
-
Administrators can direct device users to a specific Enrollment URL and Remediation URL. If a URL is not provided, a default URL is automatically provided by Core.
-
Once the setup is completed, Core is connected to Microsoft Azure.
-
A Partner Device Compliance policy (under Policies) needs to be created and applied to the device group that reports the device compliance to Azure.
-
In Devices & Users > Devices > Advanced Search drop down > Common Fields section, five new fields have been added:
-
Azure Client Status Code
-
Azure Device Compliance Report Status
-
Azure Device Compliance Report Time
-
Azure Device Compliance Status
-
Azure Device Identifier
-
-
The ability to de-provision the Azure account has been added.
-
All activity of adding, editing, and deactivating an account are recorded in the Logs.
For more information, see "Azure Tenant" and "Advanced searching" in the MobileIron Core Device Management Guide for Android and Android enterprise Devices or in the MobileIron Core Device Management Guide for iOS and macOS Devices.
-
Enhancements to the self-service user portal (SSP)
-
Default language selection now includes self-service user portal pages: From Core 11.0.0.0 through the most recently released version as supported by MobileIron, when you change the Core default language in the Settings > General > Language page, your selection also changes all the self-service user portal (SSP) pages, as well. This is an enhancement to previous releases, when not all SSP pages displayed in the selected language. For more information, see the Language Support section of the MobileIron Core Device Management Guide for your operating system.
NOTE: The portal will, by default, attempt to detect the default language of the end user device and display the correct language. Otherwise, the portal displays the selected default language. To have all client devices view the SSP in the same language, regardless of the user device language, make sure the DETECT USER LANGUAGE option is OFF. This will force all users to the default language selection. -
Option to "Trust" or "Untrust" mac and iOS devices in self-service user portal: Mobile@Work users can temporarily elevate or downgrade the trust level of their device, depending upon the surrounding conditions. The following new options are available from the self-service user portal (SSP) Devices page:
-
Untrust: Select this option to temporarily remove confidential information and applications from the device. When the device is trusted (the default), the user will see the Untrust option. Use this option before entering a location where device security may be at higher than normal risk, such as in airports.
-
Trust: When the device is untrusted, the user will see the Trust option. Use this option when no unusual device security risks exist.
For more information, see the section "Trust and Untrust options" in the "Self-service User Portal" chapter of the MobileIron Core Device Management Guide for iOS and macOS Devices.
-
-
Improved auto-detect of device type and browser during registration: MobileIron has improved the auto-detection of devices and browsers as part of MobileIron client registration. Core uses this information to provide appropriate guidance to users registering their devices.
-
Customize iOS self-service user portal "Request Registration PIN" message: You can now customize and set defaults in the "Request Registration PIN" page of the iOS self-service user portal. For more information, see "Customizing the request registration PIN page" in the MobileIron Core Device Management Guide for iOS and macOS Devices.
-
Self-service portal enhancements for ADA Section 508: The self-service user portal (SSP) user interface in Core 11.0.0.0 through the latest release as supported by MobileIron has been enhanced to enable screen readers to render text and image content as intended. This is to increase compliance with the Americans with Disabilities Act (ADA) Section 508.
-
API support for self-service user portal: This release provides several public APIs that you can use to provide self-service portal functionality from within your user interface. See the MobileIron Core v2 API Guide for complete details.
-
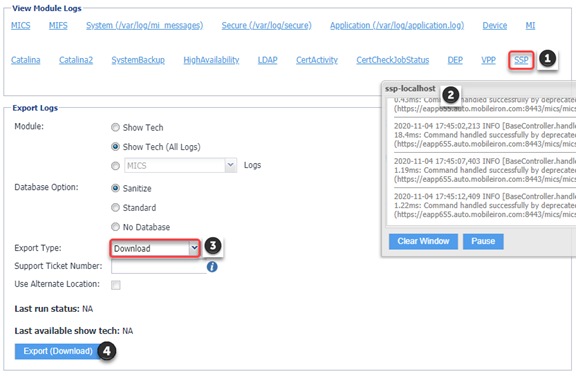
SSP-related log files now available: With this release, you can view and download self-service user portal (SSP)-related log files from the System Manager > Troubleshooting > View Module Logs page.
Figure 1. Viewing and downloading SSP log files
-
To view the SSP-related logs, click the new SSP link in the View Module Logs section. A scrolling window opens, displaying the log files.
-
To download the SSP-related logs, enter your criteria in the Export Logs section. Select Download as the Export type (HTTP and SFTP are not supported at this time). Click Export.
For more information about log files, see "Working with logs" section of the MobileIron Core System Manager Guide.
-
-
Set Time Zone: The administrator can now set the time zone for one or more devices from within the Device Details page using the Actions > Set Time Zone option. The time zone device action is also displayed in the Device Details page of a device. This feature is applicable to iOS 14.0 and tvOS 14.0 through the latest version as supported by MobileIron. For more information, see "Setting the time zone of a device" in the MobileIron Core Device Management Guide for your operating system.
-
Send email when using the Wipe or Cancel Wipe command on a device: Administrators now have the ability to customize or suppress emails that are automatically generated when a Wipe command or Cancel Wipe command is sent. The Send notification of wipe to registered user field is useful for users that have multiple devices. The email notification helps prevent confusion to device users who may think Core is wiping their current, active device. For more information, see "Wipe" or "Cancel Wipe" in the MobileIron Core Device Management Guide for your operating system.
Additional enhancements
-
System Manager Self Diagnosis disabled after upgrade: The System Manager feature Self Diagnosis (System Manager >Maintenance > Self-Diagnosis) is no longer supported, and has been removed with this release.
-
Sentry configuration updated to support OAuth redirect: In MobileIron Core > Services > Sentry, under Server Authentication, whenever ActiveSync is enabled, the following options are available:
-
Basic Auth only
-
OAuth Auth only
-
Basic Auth and OAuth
This feature is supported on MobileIron Sentry, targeted to release in December 2020. For more information about configuring OAuth on MobileIron Sentry, see "Device and Server Authentication" in the MobileIron Sentry Guide for MobileIron Core.
-
-
Support for VMWare ESXi 6.7 and ESXi 7.0 hypervisor software: Core and Connector ISO can be deployed on VMWare ESXi 6.7 and ESXi 7.0 hypervisor software from Core 11.0.0.0 through the most recently released version as supported by MobileIron. For more information see "Virtual Core requirements" in the On-Premise Installation Guide for MobileIron Core and Enterprise Connector 11.0.0.0.
-
Help Desk telephone numbers now accept up to 24 digits: In the Settings > System Settings > General > Helpdesk > Contact(s) field, the length of a valid telephone number has been expanded from 15 digits to 25 characters total:
-
24 digits for numbers beginning with the + symbol.
-
22 digits for numbers without the + symbol.
For more information, see "Configuring help desk contact information" in the MobileIron Core Device Management Guide for your operating system.
-
-
Support to enable/disable FIDO (Fast IDentity Online) authentication: The new user interface for Zero Sign-on can be enabled from MobileIron Core > Policies and Configs > Policies > SaaS. Use the toggle button to enable or disable the interface. This feature is supported on Access 44, targeted to release in December 2020.
-
View 100+ Win32 apps on Windows 10 devices: For Windows 10 devices with more than 100 Win32 apps, the App inventory is updated in the database. You can view this inventory in the Device Details > Apps page. For more information, see "Privacy policies" in Getting Started with MobileIron Core and "Installed Apps Device Details page" in the MobileIron Core Apps@Work Guide.
-
New options to restrict Device Registration: New options for device registration are provided that allow administrators to restrict which devices can register with MobileIron Core. The restrictions are based on the enrollment type and the options are available on the Admin Portal in Settings > Users & Devices > Device Registration. For more information, see "Restricting device registration by enrollment type" in the Getting Started with MobileIron Core.
Android and Android enterprise features and enhancements
This release includes the following new features and enhancements that are specific to the Android and Android enterprise platforms.
-
Existing Tunnel configurations support MTD anti-phishing: For devices that already have Tunnel for Android configured, you can continue to use the existing Tunnel configuration for anti-phishing support with MTD. Anti-phishing support with Tunnel and MTD is supported with Tunnel 4.6.0 for Android. For more information see MobileIron Tunnel for Android Guide for Administrators.
-
New field added to Privacy policies: In the Privacy policy, a new field has been added - Prompt User to Enable Location Services if Wi-Fi/MTD configuration is pushed (Android enterprise.) Administrators have the ability to prompt device users to enable the device's location setting. This setting is useful if the device user resides in a country that has GDPR requirements. During the registration process, the device user is prompted to enable the location setting. If the device user does not grant permission, the configuration will fail. For more information, see "Enabling Android enterprise" in the MobileIron Core Device Management Guide for Android and Android enterprise Devices. See also "Privacy Policies" in the Getting Started with MobileIron Core.
-
Support for closed network / AOSP deployment: There are situations where the onboarding, registration and management of devices is limited and requires a different approach. Examples of these kinds of situations are:
-
In an environment that does not have connectivity to Google mobile services (GMS) due to restrictions in the organization or due to a closed network.
-
In countries where Google mobile services are not available.
-
Where devices that do not have Google mobile services but vendors have enabled Android Enterprise AOSP (Android Open Source Project.)
With the 11.0.0.0 release, MobileIron Core now supports a new mode of deployment:
-
Integrated deployment (GMS/Non-GMS) - the entire Core instance serves devices in full Android enterprise mode (for example, Samsung devices) and also devices that do not have GMS (for example, AR/VR devices.)
This feature applies to Android 6 devices through the latest version as supported by MobileIron. For more information, see "Setting up Core with a closed network / AOSP deployment" in the MobileIron Core Device Management Guide for Android and Android enterprise Devices.
-
-
Support for app restrictions with in-house applications for Android non-GMS devices: For devices registered to Core in a non-GMS mode, administrators can apply in-house app restrictions to these devices. Administrators can also distribute those apps and its configurations as in-house applications directly to Mobile@Work clients without using Google mobile services. For more information, see "App restrictions with in-house applications for Android" in the MobileIron Core Apps@Work Guide.
-
New warning banner added to Privacy Policy: For Android devices, in the default Privacy Policy, administrators can add a warning banner that displays upon device reboot. This is helpful for companies that require all approved mobile operating systems, such as Android 9.0, to be managed according to a security baseline / guidance. Device users will see the warning banner upon device reboot and will have to acknowledge it before continuing use of the device. For more information, see "Privacy Policies" in Getting Started with MobileIron Core.
-
Limit Android device registration by Allowed or Blocked devices: You can create Allowed or Blocked device registration lists from the Settings > System Settings > Users & Devices > Device Registration > Restrictions for Android > Allow/Blocked devices list. When you click either Create a list of Allowed devices or Create a list of Blocked devices, a device table opens, where you can enter specific device information that will, when matched, either allow the requesting device to register or block it. Blocked devices receive a pop-up message: "Unable to complete registration (Invalid Manufacturer). Please contact your administrator."
For more information, see "Registering Android devices" in the MobileIron Core Device Management Guide for Android and Android enterprise Devices.
-
Common Criteria and alphanumeric device passcode: An alphanumeric device password is no longer a requirement for Common Criteria mode for Android devices. The following settings are required to enable the Common Criteria mode:
-
Device Encryption is enabled
-
SD Card Encryption is enabled
-
Password history is disabled
-
Max password failed attempts is greater than 0
For information about these settings, see Security policies in Getting Started with MobileIron Core.
-
iOS and macOS features and enhancements
This release includes the following new features and enhancements that are specific to the iOS and macOS platforms.
-
Field name changed in Google Account configuration for iOS devices: Previously, a field titled "Google User's Full Name," was added to the Google Account Configuration dialog box. This field name has been changed to "Google Account Name." When an email is sent from this Google account, the name entered here displays who the email is from. Upgrading from previous releases will fill in the name as per the configuration. This field used to be a required field, and it is now an optional field for adding or updating an iOS Google Account Configuration. For more information, see "Google Account" in the MobileIron Core Device Management Guide for iOS and macOS Devices.
-
Three new restrictions for iOS: The following fields have been added to iOS restrictions in the iOS / tvOS > Restrictions configuration page.
-
Allow Personalized Advertising (iOS 14.1 through the latest version as supported by MobileIron)
-
Allow NFC (iOS 14.2 through the latest version as supported by MobileIron)
-
Force Dictation Processing Only on Device (iOS 14.3 through the latest version as supported by MobileIron)
For more information, see "iOS and tvOS restrictions settings" in the MobileIron Core Device Management Guide for iOS and macOS Devices.
-
-
New Skip option for Device Enrollment Profiles: A new option has been added to allow devices to Skip the App Store pane during the registration of an Automated Device enrollment device. For more information, see "Creating Apple Device Enrollment profiles" in the MobileIron Core Device Management Guide for iOS and macOS Devices.
-
New workflow to install management profile for macOS 11.0 and above: During iReg device registration, when the device users begin registering their devices with macOS 11.0 and later versions as supported by MobileIron Core, users are prompted with a message that the management profile has been downloaded. To install the profile, device users need to install the downloaded profile, go to System Preferences > Profiles, and then click Install. For more information, see "In-app Registration" in the MobileIron Core Device Management Guide for iOS and macOS Devices.
-
Notification preview type: In the App Notifications Configuration, select a Preview Type to display in the device notification message previews. Select Never to prevent apps from displaying message previews in Notifications. Applicable to iOS 14.0 through the latest version as supported by MobileIron. For more information, see "Configuring notification settings" in the MobileIron Core Device Management Guide for iOS and macOS Devices.
-
New field in App Catalog - Prevent user from removing and offloading app: Administrators can now prevent device users from removing a selected managed app (for example, Mobile@Work) and prevent the OS from offloading unused apps. When the device user tries to uninstall the app, a pop-up will state: "Uninstall Not Allowed - It is not possible to uninstall this app at this time." Administrators also have the option to allow device users to remove and uninstall the selected app. Applicable to iOS 14.0 through the latest version as supported by MobileIron. For more information, see "Using the wizard to import iOS apps from the Apple App Store" and "Using the wizard to add an in-house iOS or macOS app to the App Catalog" in the MobileIron Core Apps@Work Guide.
-
Extensible Single Sign-On: MobileIron Core enables Extensible Single Sign-On with the following configurations: Extensible Single Sign-On and Extensible Single Sign-On Kerberos. The implementation requires an app extension, such as Microsoft Authenticator, from the identity provider. With an Extensible Single Sign-On implementation, device users need to only authenticate once when accessing enterprise resources. Device users are not prompted to authenticate for subsequent log in. A single sign-on configuration using Extensible Single Sign-On does not require a Tunnel or Sentry deployment. For more information, see "Extensible Single Sign-On" and "Extensible Single Sign-On Kerberos" in the MobileIron Core Device Management Guide for iOS and macOS Devices.
MobileIron Threat Defense features
MobileIron Threat Defense protects managed devices from mobile threats and vulnerabilities affecting device, network, and applications. For information on MobileIron Threat Defense-related features, as applicable for the current release, see the MobileIron Threat Defense Solution Guide for Core, available on the MobileIron Threat Defense for Core Documentation Home Page at MobileIron Community.
| NOTE: | Each version of the MobileIron Threat Defense Solution guide contains all MobileIron Threat Defense features that are currently fully tested and available for use on both server and client environments. Because of the gap between server and client releases, MobileIron releases new versions of the MobileIron Threat Defense guide as the features become fully available. |