Creating an MTD anti-phishing protection configuration
You can create an MTD anti-phishing configuration for managed Android devices and optionally, iOS devices. The configuration applies URL Handler for Android devices, and on-device VPN and Content Blocker are options for iOS devices.
Procedure
-
Log in to MobileIron Core admin portal.
-
Go to Policy & Configs > Policies.
-
Click Add New > MTD Anti-Phishing. The Add MTD Anti-Phishing Policy page opens.
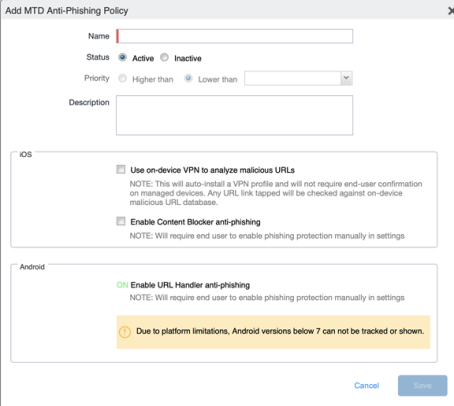
-
In the Add MTD Anti-Phishing Policy dialog box, enter a name for the policy.
-
For status select Active. This is the default setting.
-
Specify a priority for this policy, relative to the other custom policies of the same type. Select Higher than or Lower than, then select an existing policy from the drop-down list. This priority determines which policy is applied if more than one policy is available.
NOTE: Only one active policy can be applied to a device. -
(Optional) Enter a description.
- In the iOS section, select from the following policy options:
- Use on-device VPN to analyze malicious URLs - This option auto-installs a VPN profile to managed clients without requiring end-user confirmation. Tapped links are checked against an on-device database of malicious URLs.
- Enable Content Blocker anti-phishing - The end user must enable this feature. When enabled, all network traffic is blocked when a phishing threat is detected. Once cleared, network traffic is again allowed.
- In the Android section, URL Handler is enabled by default, and requires the end user to enable the feature.
-
Click Save.
-
Apply a label to the policy. See Creating MTD labels in Core for Android and iOS devices.
-
Create a compliance policy rule to ensure that device users enable MobileIron Phishing Protection. See Creating compliance policy rules and groups. Give the policy the following settings:
- Condition: MTD Anti-Phishing status / Equals / Not Enabled
-
Regular Expression: "common.mtd_anti_phishing_status"="CLIENT_NOT_ENABLED"
This expression makes the devices go out of compliance, and it triggers a compliance action that forces device users to enable MobileIron phishing protection.
-
Force device check in.