Advanced phishing protection for iOS devices
From Core 10.7.0.0 through the most recently released version as supported by MobileIron, you can enable Threat Management Console advanced phishing protection to MTD-enabled iOS devices without any client user action. This tool provides full coverage against risky URLs through an automatically enabled, on-device VPN.
Procedure
- Log into Threat Management Console.
- Click the Policy tab.
-
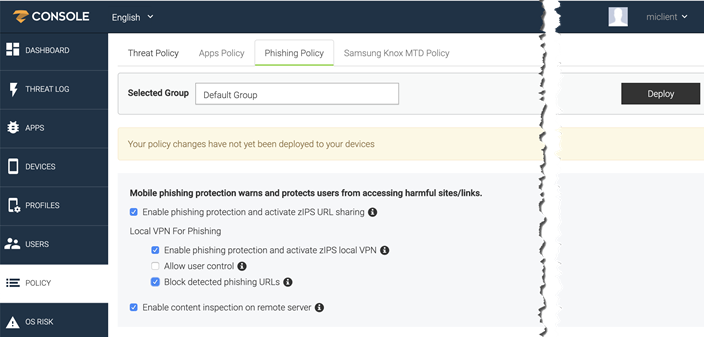
From the Policy page, click Phishing Policy. The phishing policy configuration page displays.
-
In the Selected Group field, select from the groups you created in Creating compliance policy rules and groups.
-
Select from the following options:
-
Enable phishing protection and activate zIPS URL sharing - Enabled by default. Check this option to enable phishing protection.
- Local VPN for Phishing
- Enable phishing protection and activate zIPS local VPN - Enabled by default. Check this option to enable a local phishing VPN.
- Allow user control - Disabled by default. This option cannot be enabled.
-
Block detected phishing URLs - Enabled by default. Check this option to block phishing URLs when they are detected on a device.
NOTE: Do not disable Phishing Policy option "Block detected phishing URLs." If disabled, users will see a non-working notification.
-
Enable content inspection on remote server - Enabled by default. This option allows the Threat Management Console to access a much larger database of blacklisted sites than the sites available on the device, providing multi-level protection.
-
- Click Deploy to distribute the phishing protection policy to the selected device group.