MTD features, issues, and enhancements in Core 11.0.0.0
Each version of the MobileIron Threat Defense Solution guide contains all MTD features that are currently fully tested and available for use on both server and client environments. Because of the gap between server and client releases, MobileIron releases new versions of the MTD guide as the features become fully available.
The following features and enhancements are a part of the MobileIron Threat Defense Solution for Core 11.0.0.0.
General MTD features, issues, and enhancements
The following MTD general features, issues, and enhancements are available in this release:
Customized local threat notification text for Mobile@Work devices
You can customize local threat notification text for
New MobileIron Tunnel configuration deploys automatically when needed
From
Existing Tunnel configurations support MTD anti-phishing
For devices that already have Tunnel for Android configured, you can continue to use the existing Tunnel configuration for anti-phishing support with MTD. Anti-phishing support with Tunnel and MTD is supported with Tunnel 4.6.0 for Android.
Tunnel for anti-phishing unnecessary with MobileIron Access
When configuring the MobileIron Tunnel app, if you have selected "Enable MobileIron Access," you should not enable "Use Tunnel for Anti-phishing only." When both options are selected, Core displays an error message.
"Available OS Updates" work correctly for macOS and iOS devices
There was an issue where, when iOS or macOS devices performed a twice-a-day scan for operating system (OS) updates, the information was not captured, and the Device Details > Available OS Updates field displayed "Unavailable." This issue has been fixed. From Core 11.0.0.0 through the latest release as supported by MobileIron, iOS devices running OS 9 or higher, and macOS devices running OS 10.11 or higher can receive the results of the OS update scan and display the correct status information in the "Available OS Updates" field.
MTD supported in custom spaces
MobileIron Threat Defense for Core 11.0.0.0 can be enabled within custom spaces. The "Use Tunnel for Anti-phishing only" check box is disabled for custom spaces.
Successful sign in to Microsoft Azure may stop responding in Safari browser
The Microsoft Azure consent page (the place where you sign in to Azure) might stop responding when accessed from the Safari browser, leaving the incorrect impression that consent was not successful. This is a Microsoft known issue. Workaround: Close the page and return to MobileIron Core. To avoid the issue, use the Chrome browser for accessing Azure.
Users can disconnect MobileIron anti-phishing VPN by connecting to a different VPN provider
Users who launch a device-level VPN app, such as PulseSecure or GlobalProtect from their device will disconnect the MobileIron anti-phishing VPN, which disables the anti-phishing solution on the device. The device user must navigate back to Settings > VPN settings and re-select MobileIron anti-phishing VPN to re-enable MTD anti-phishing protection.
MTD features, issues, and enhancements for iOS devices
The following MTD features, issues, and enhancements are available for iOS devices in this release:
New network permission prompt wording for iOS clients
The message prompting iOS users to allow MobileIron access to their devices has changed. The message originates from Apple, and it cannot be circumvented at this time.
-
New message: This will identify devices on your WiFi network in order to protect your data from cyber threats.
-
Old message: Local Network Usage information is required for MobileIron Threat Defense.
Help with MTD activation on Apple devices
MobileIron provides new tools for activating MTD on Apple Automated Device Enrollment (DEP) or International Roaming Expert Group (IREG) enrolled clients. See the knowledge-based article Allow MTD-activation of devices using M@W client when app has been suspended or killed for information.
MTD features, issues, and enhancements for Android devices
The following MTD features, issues, and enhancements are available for Android and Android Enterprise devices in this release:
Advanced multi-level phishing protection using the MobileIron Tunnel app
From Core 11.0.0.0 through the most recently released version as supported by MobileIron, several new advanced anti-phishing protection options are available for MTD-enabled Android devices without client user action:
-
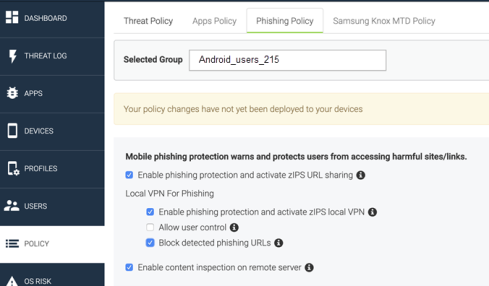
Threat Management Console Phishing – This server-initiated VPN configuration enables advanced anti-phishing support, and includes options to block detected phishing URLs and to enable content inspection on a remote server. The configuration provides coverage against risky URLs, and can be applied with or without the MTD VPN and URL Handler options. For more information, see Advanced phishing protection for managed devices.
Figure 1. Threat Management Console Phishing options
-
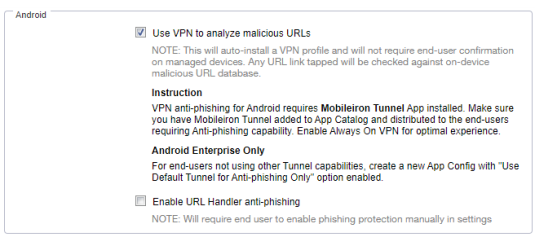
MTD VPN anti-phishing policy – The Android Anti-phishing Protection Configuration > Use VPN to analyze malicious URLs option checks potentially malicious links against an on-device database of malicious URLs. When a user taps on a potentially risky URL, they see a notification with a warning of the potential danger. Once Threat Management Console VPN is enabled, the MTD anti-phishing policy can be applied alone or in conjunction with URL Handler. See Using a remote database to validate URLs.
Figure 2. MTD anti-phishing options
-
VPN anti-phishing for Android requires the Mobilelron Tunnel app, which can be downloaded to your App Catalog and distributed to Android end-users who require anti-phishing capability. Enable Always On VPN for optimal experience. See Android anti-phishing using MobileIron Tunnel app.
| NOTE: | The anti-phishing VPN for Android solution requires MobileIron Tunnel 4.6.0. |
Customize end-user local threat alert notifications
You can customize local threat notification text for Mobile@Work devices through the Threat Management Console. The feature is enabled by default from the Core Local Actions policy. When enabled, the default notification text for end users changes from MTD defaults to the Threat Management Console defaults, which administrators can customize in any of the supported languages. For more information, see Customizing local threat notification text.
Android support for Zimperium SDK v4.14.3
MTD for Core 11 supports the 4.14.3 Zimperium SDK, which contains a fix for an issue regarding the incorrect detection of a rogue access point.
MobileIron Tunnel upgrade needed to support anti-phishing
When a VPN anti-phishing configuration is pushed to Android devices, older versions of the MobileIron Tunnel app display an error message.
Workaround: To enabled anti-phishing capabilities, upgrade the MobileIron Tunnel app to version 4.6.0 through the latest version as supported by MobileIron.
Disabling risky Wi-Fi blocked for Android Enterprise devices running Android 10.0 and higher
A Samsung limitation prevents devices running MobileIron Go in Android enterprise mode from disabling risky Wi-Fi connections on Android version 10.0 through the most recently released version as supported by MobileIron. Until a patch is released, if disabling risky Wi-Fi with an alert has been enabled in Local Actions, the user will see an erroneous alert that the Wi-Fi has been disabled.
Older versions of Mobile@Work enable URL Handler anti-phishing by default
Android devices running older versions of Mobile@Work software have URL Handler anti-phishing enabled by default, even when no anti-phishing options are selected. Workaround: Upgrade to Mobile@Work 11.0.0.0 for Android.
Registering Oculus Quest 2 on Android 10.0 devices
Oculus Quest 2 devices running Android 10.0 operating system cannot complete registration if an MTD anti-phishing configuration is on the device. Workaround: Remove the anti-phishing configuration.
Wi-Fi not disabled for Oculus Quest 2 on Android 10.0 devices
On Oculus Quest 2 devices running Android 10.0 operating system, the MTD local action to "Disable WiFi" does not disable the Wi-Fi, although it displays a notification that Wi-Fi has been disabled.
MTD Local Actions policy not supported on devices with custom XML configurations
MTD Local Actions are not supported on Android devices still using custom XML configurations. The behavior is expected, as custom XML configurations are being retired for this reason.