Configuring the Threat Management Console Mobile Threat Response Policy
The Threat Response Matrix (TRM) defines the actions that Threat Management Console takes upon detecting an event. Among the options are:
- Enable or disable detection of a specific threat classification
- Alert the admin
- Change the severity of a threat
- Set MDM actions and mitigation actions
Before you begin
- If you are setting up Server-initiated mitigation and compliance be sure you have completed the procedures listed in Creating compliance policy rules and groups
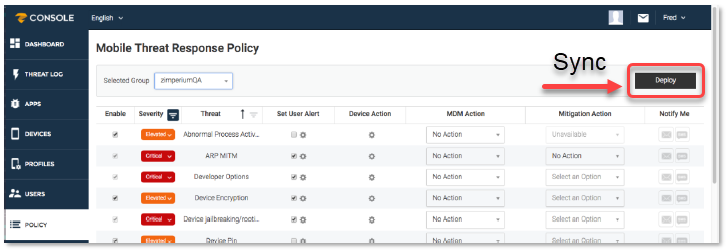
After you modify these options, click Deploy to send, or sync the new TRM to currently activated devices. When integrated and synced with MobileIron Core, each label used for integration is created as a group with its own TRM policy. See the sample TRM policy.
Figure 1. Example Threat Response Matrix
|
Name |
Description |
|---|---|
| Enable |
The Threat Management Console administrator has the option of disabling certain threat detections and, therefore, the collection of associated forensics. |
| Severity |
The administrator has the option of changing the threat severity levels. This is useful for different business cases. The options are "Critical," "Elevated," "Low," and "Normal. |
| Threat |
The threats listed in the Threat column represent the classes of threats that MobileIron Threat Defense detects. Threat classes are recognized by MTD, which is able to determine when a malicious event is happening. |
| Set User Alerts |
Administrators cannot manage MTD alerts through Threat Management Console. In order to implement and localize MTD alerts, please use Local Actions policy in |
| Set Device Action |
Administrators can deploy device actions for Android and iOS devices on Threat Management Console. See Set device action. |
| MDM action |
Administrators can enable server-enforced mobile device management (MDM) action items on the Threat Management Console policies page. After deploying / syncing with MobileIron Core, when a threat is detected, Threat Management Console instructs Core to move the device to the chosen label in the Threat Response Policy / Matrix. The workflow assigned to that label determines the action that Core takes on the device. The communication from Threat Management Console to Core is performed securely through a MobileIron API call. See MDM action. |
| Mitigation action |
When a threat that was detected by Threat Management Console has been remediated and is no longer posing a threat to the device, you can define specific actions that can be taken. For example, when a device is determined to be under a Man-in-the-Middle attack, it can be prevented from accessing various corporate resources. When the device is moved to a clean network, you can automatically allow the device to access those resources again. See Mitigation action. |
| Notifications |
You can set up an email or SMS notification process for each specific threat. SMS notifications require the administrator’s telephone information to be set up in the User page of a given administrator. Each email or SMS contains an Event summary and a link to the actual event that can be viewed in a browser after login. See Notifications. |