Configuring MobileIron Tunnel in MobileIron Core
MobileIron Tunnel creates a secure connection between the managed device and Access for authenticating users accessing enterprise cloud resources.
Before you begin
|
•
|
Ensure that you have registered Access with MobileIron Core. |
|
•
|
Ensure that you have added MobileIron Tunnel to MobileIron Core. |
For information on how to add MobileIron Tunnel to MobileIron Core, see the relevant section in the MobileIron Tunnel Guide for Administrators for the device OS.
Procedure
|
1.
|
In MobileIron Core, go to Polices & Configs > Configurations. |
Figure 1. add mobileiron tunnel vpn setting
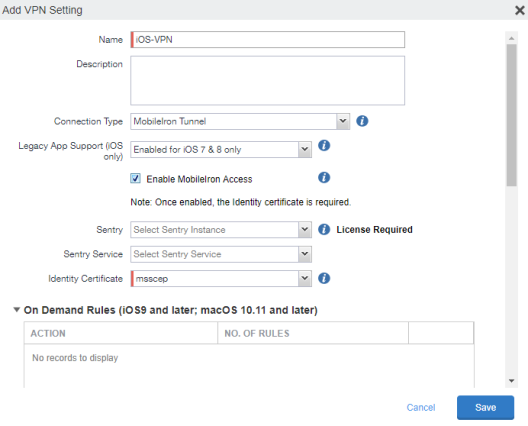
|
3.
|
For Connect Type, select the MobileIron Tunnel or MobileIron Tunnel (Android). |
Create a separate Tunnel configuration for each OS type.
|
4.
|
Enter a name for the configuration. |
|
5.
|
Select the check box for Enable MobileIron Access. |
|
6.
|
For Identity Certificate, select the Certificate Enrollment configuration you created earlier to establish trust between Tunnel and Access. |
Note The Following:
|
•
|
The Enable MobileIron Access setting is also available in the AppConnect App Configuration and Web@Work configuration. The setting allows these apps to direct authentication traffic to Access. The setting is available only if Services > Access is configured in the MobileIron Core Admin Portal. Otherwise, the setting is grayed out. |
|
•
|
Federated traffic from Docs@Work through Access is only supported with Tunnel. However, using Tunnel to CIFs services will fail. Federated traffic through AppTunnel and an Access (without Standalone Sentry) deployment is not supported for Docs@Work. Selecting Enable MobileIron Access in the Docs@Work configuration does not have an impact. |
|
•
|
Google Apps (GApps) require Chrome to direct authentication traffic through Access. |
Next steps
Configure Access in MobileIron Core. See Configuring MobileIron Core in Access.
