Delegated IdP overview
In most cases Access is deployed as a proxy between the service provider (SP) and the identity provider (IdP). In such a deployment, all federated SP traffic goes through Access. In some cases, you may want to retain the existing SP-IdP federated setup, but deploy Access to federate a sub set of the traffic, such as traffic from mobile devices. In such cases, Access can be deployed as a delegated IdP rather than as a proxy to the IdP. If Access is deployed as a delegated IdP, the original IdP is seen as an SP by Access.
Figure 1. Access as the IdP proxy
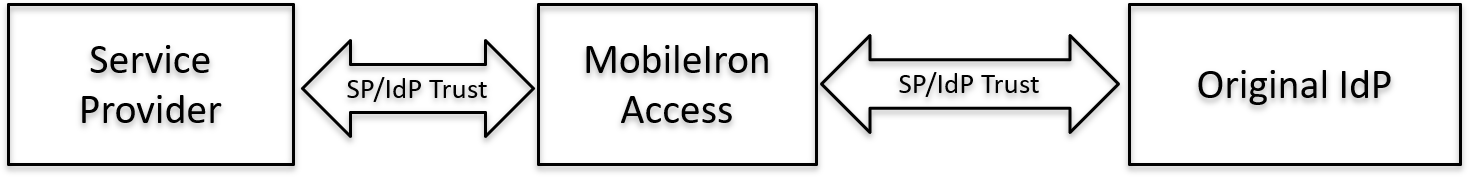
Figure 2. Access as the delegated IdP
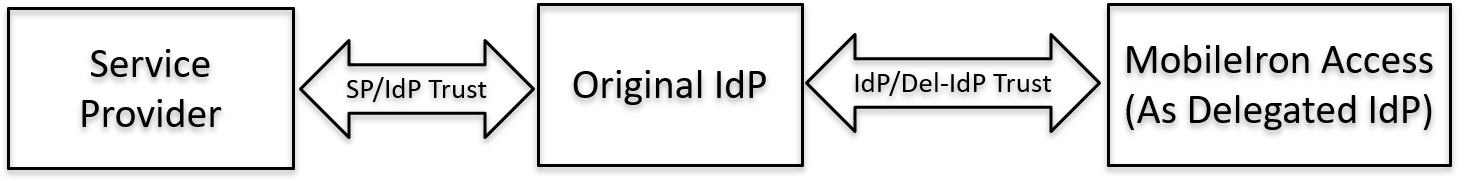
Access can be deployed as the delegated IdP only for the following IdPs:
- Idaptive
- Microsoft ADFS
- Okta
- PingFederate
In an Access configured as a delegated IdP:
- To authenticate managed devices, configure certificate single sign-on (SSO) in the UEM.
- To authenticate unmanaged devices, you have the option to enable Unmanaged Device Authentication in Access. If authentication for unmanaged devices is enabled, the unmanaged device is redirected to the original IdP for forms-based authentication.