About Authenticator Only with Ivanti Access
In an Authenticator Only deployment, employees register their device with a unified endpoint management (UEM) platform in Authenticator Only mode. A device that is registered with in Authenticator Only mode is not managed. This means that mobile device management policies and configurations such as mobile threat defense, password requirements, Wi-Fi, VPN are not applied to the device. However, the Authenticator Only device checks in with the UEM periodically and registers the posture of the device. If the Authenticator Only device is in compliance, users can continue to use it as their identity and authentication factor.
The following provides additional information about Authenticator Only with Ivanti Access:
- Required components for Authenticator Only
- Use cases for Authenticator Only
- Authentication flow for Authenticator Only
- Device actions and policies for Authenticator Only
- Android enterprise and Authenticator Only
Required components for Authenticator Only
Deploying Authenticator Only requires that the following components are set up:
- Ivanti Access deployment with a Unified Endpoint Management (UEM) platform. The UEM platforms are:
- Ivanti Neurons for MDM
- Ivanti EPMM
- UEM client. The UEM clients are:
- Go for Ivanti Neurons for MDM
- Mobile@Work for Ivanti EPMM.
See the Release notes for Ivanti Neurons for MDM or Ivanti EPMM for supported client versions.
Use cases for Authenticator Only
The following describes the authentication use case enabled with Authenticator Only devices:
- Password less access from unmanaged devices: Users accessing an enterprise cloud service provider (SP) from an unmanaged device are presented with a QR code. Scanning the QR code with their Authenticator Only device authenticates the user and allows access from the unmanaged device. Users scan the QR code using the client and the native camera on the Authenticator Only device. Users do not need to enter their username and password. Users have the following additional options for subsequent log in:
Enable push notifications. If enabled, a push notification is sent to the managed device on subsequent log in from the unmanaged device.
Alternately, users can use the client on their managed device to generate a one-time passcode (OTP). OTP allows users to access cloud services from the unmanaged device even when the client does not have access to the Internet.
The following table describes the passwordless features with Authenticator Only devices:
|
UEM |
Client |
Feature supported |
|---|---|---|
|
Ivanti Neurons for MDM |
Go for iOS |
QR code, push notifications, OTP |
|
Go for Android and Android enterprise |
QR code, push notifications, OTP |
|
| Ivanti EPMM |
Mobile@Work for iOS |
QR code, push notifications, OTP |
|
Mobile@Work for Android and Android enterprise |
QR code, push notifications, OTP |
Authentication flow for Authenticator Only
The following describes the authentication flow from an Authenticator Only device using passwordless authentication.
Figure 1. Authenticator Only authentication flow
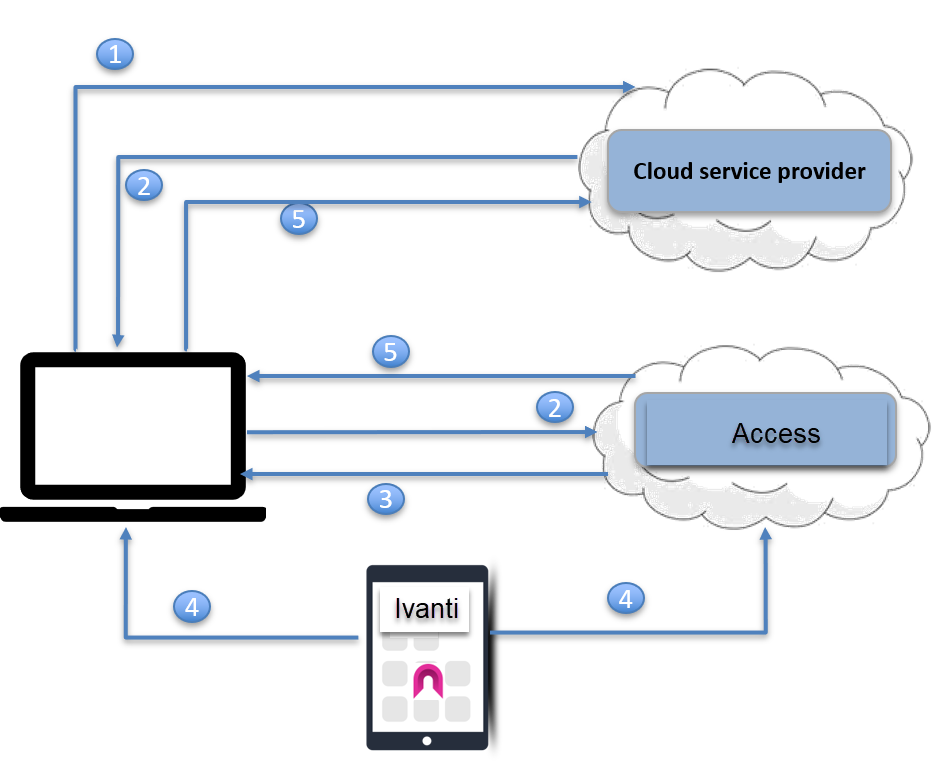
| 1. | User requests access to a cloud service from an unmanaged device, such as a desktop. |
| 2. | The cloud service redirects user to the configured identity provider (IdP)to authenticate. Since Ivanti Access is the configured IdP, the request is redirected to Ivanti Access. |
| 3. | Ivanti Access generates and presents a QR code to the user. |
| 4. | The user scans the QR code with the mobile device in Authenticator Only mode to approve the login. |
| 5. | Access generates a new SAML response to redirect to the original SP. The original SP obtains the user identity from the SAML response and presents the personalized screen to the user. |
Device actions and policies for Authenticator Only
A device in Authenticator Only mode is not managed by UEM. Device and app management policies and features are not available on a device in Authenticator Only mode. To view the device's security posture, the following devices actions and policies are available and applied to Authenticator Only devices.
- Administrator actions (Ivanti Neurons for MDM)
- Administrator actions ( Ivanti EPMM)
- Device user actions
- Compliance polices and actions (Ivanti Nerons for MDM)
- Polices and actions (Ivanti EPMM)
Administrator actions (Ivanti Neurons for MDM)
Administrators can take the following actions on Authenticator Only devices on Ivanti Neurons for MDM:
- Retire: The Retire action removes the SaaS configuration (Ivanti Nerons for MDM) or policy (Ivanti EPMM) from the device and retires the device.
- Add to Group: Select or change the device group.
- Assign Custom Attributes
- Remove Custom Attributes
- Assign to user
- Force Check-in
- Set Ownership
Administrator actions ( Ivanti EPMM)
Administrators can take the following actions on Authenticator Only devices on Ivanti EPMM:
- Retire: The Retire action removes the SaaS policy from the device and retires the device.
- Apply to Label
- Remove from Label
- Set Custom Attributes: Set or clear custom attributes.
Device user actions
The following lists the actions device users can take on the User portal:
- Retire Device
- Send invitation
Compliance polices and actions (Ivanti Nerons for MDM)
The following compliance policy is applied to Authenticator Only devices on Ivanti Nerons for MDM:
- Compromised Devices policy: Go checks in with the Ivanti Nerons for MDM and reports if the device is compromised. The device status is displayed in the listing for the device in Device > Device on Ivanti Nerons for MDM. The following compliance actions are applied on Authenticator Only devices:
Retire: Removes the SaaS configuration from the device and retires the device.
Quarantine: Uninstalls the SaaS only configuration and associated certificates.
Polices and actions (Ivanti EPMM)
The following policies and compliance actions are applied to Authenticator Only devices on Ivanti EPMM:
- Security policy: The default policy is applied.
- Sync policy: The default policy is applied.
- Privacy policy: The default policy applied.
-
Compliance actions:
- Quarantine: The SaaS policy is removed.
See "Managing Compliance" in the Ivanti EPMM Device Management Guide
Android enterprise and Authenticator Only
If the UEM supports both Work Profile for device management (MDM), as well as Authenticator Only, the Work Profile policies and configurations take priority.
Therefore, Ivanti recommends creating separate user groups for Android enterprise and for Authenticator Only. Do the following:
- Apply the Authenticator Only devices to the Authenticator Only user group.
- Do not apply Android enterprise devices, polices, and configurations, to the Authenticator Only user group. The Android enterprise configurations are:
- Android enterprise: Work Profile (Android for Work)
- Android enterprise: Work Managed Device (Android for Work)
- Android enterprise: Managed Device with Work Profile