About multi-factor authentication with Authenticator
For multi-factor authentication, there can be only one primary device. The managed device on which the Authenticator app is installed is the primary device. All approval notifications are sent to the primary device. If multiple managed devices have Authenticator installed, the latest managed device on which Authenticator is activated is considered the primary device. If enabled, users also have the option to generate one-time passcode (OTP).
- Required components for multi-factor authentication with Authenticator
- Use cases for multi-factor authentication with Authenticator
- One-time passcode (OTP) with Authenticator
- Multi-factor authentication flow
- One-time passcode workflow
- Authenticator app features
Required components for multi-factor authentication with Authenticator
Deploying multi-factor authentication with Ivanti Access requires that the following components are set up:
- Ivanti Access deployment
- Ivanti Tunnel
- Authenticator app on a managed mobile device.
The managed device can be either an iOS, Android, or Android enterprise device.
See the Ivanti Access Release Notes for supported versions.
Use cases for multi-factor authentication with Authenticator
- Authenticator provides two-factor authentication to enterprise cloud services. Users accessing an enterprise cloud service confirm their identity by:
- Providing their user credentials, typically the name and password, to the identity provider.
- Accepting the Authenticator notification on their managed device.
- In addition, administrators can configure conditional rules to define when multi-factor authentication with the Authenticator app is triggered. Example: Create a User Info Rule to trigger multi-factor authentication for only a certain set of users or groups, a Network Rule to trigger multi-factor authentication if the user is outside the enterprise IP range.
One-time passcode (OTP) with Authenticator
Device users have the option of generating a one-time passcode (OTP) in Authenticator, which they can use instead of using push notification. OTP provides users another option to control access to enterprise cloud services from another managed device. It also provides an option to control access to enterprise cloud services even when Authenticator does not have access to the Internet.
The OTP for multi-factor authentication is displayed when the application is launched.
Multi-factor authentication flow
The following describes the authentication flow with multi-factor authentication.
Figure 1. Multi-factor authentication flow
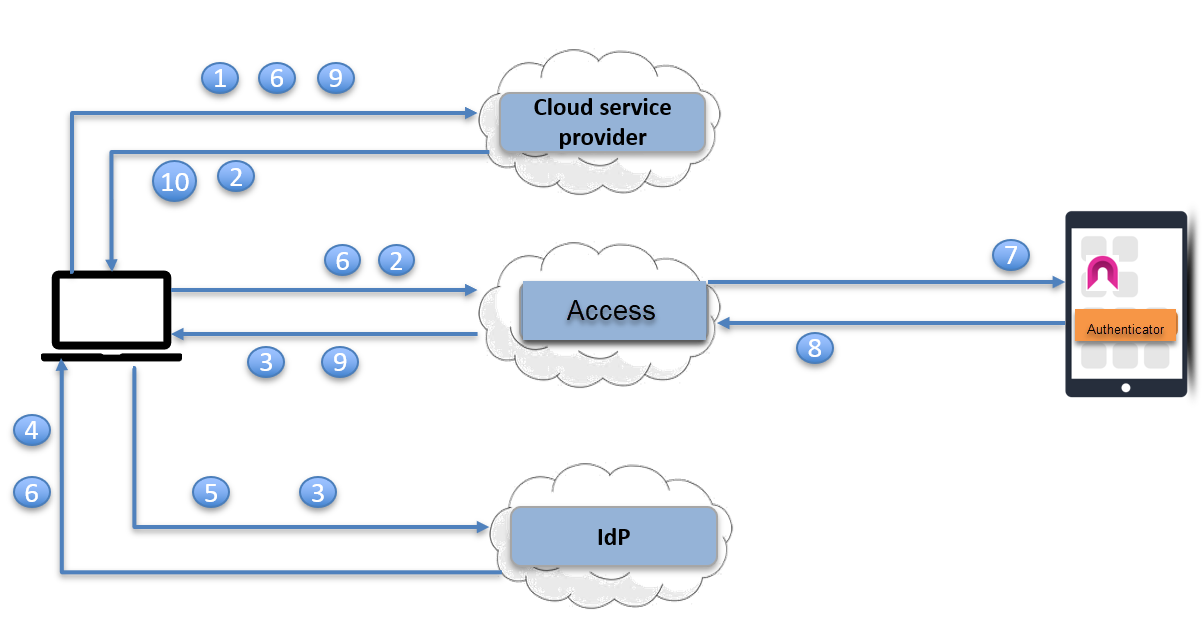
| 1. | User requests access to a cloud service. |
| 2. | The cloud service redirects user to the configured identity provider (IdP)to authenticate. Since Ivanti Access is the configured IdP, the request is redirected to Ivanti Access. |
| 3. | Ivanti Access redirects the request to the original IdP. |
| 4. | The original IdP challenges the user for a user name and password. |
| 5. | The user enters the user name and password and posts to the IdP. |
| 6. | The IdP verifies the user identity, generates a SAML Response containing the user identity and sends it to the configured service provider (SP) via a redirect. Since Ivanti Access is the configured SP in the IdP, Ivanti Access receives the redirect. |
| 7. | Ivanti Access obtains the user identity from the SAML response, and sends a push notification to the managed device registered to receive authentication push notifications for that user. |
If one-time passcode (OTP) is enabled, users have the option to generate an OTP in Authenticator. See One-time passcode workflow
| 8. | The user receives the push notification and launches the Authenticator to respond. If the user approves the transaction, the Authenticator authenticates to Ivanti Access using Ivanti Tunnel. |
| 9. | If Ivanti Access verifies the user identity received from Authenticator to be the same as the user identity received in the SAML response, Ivanti Access generates a new SAML response to redirect to the original SP |
| 10. | The original SP obtains the user identity from the SAML response and presents the personalized screen to the user. |
One-time passcode workflow
The Authenticator app automatically generates and displays a one-time passcode (OTP) when device users launch the app. A progress value indicates for how long the OTP is valid.
The following describes the OTP workflow when users access a cloud service provider (SP) from a browser or an unmanaged app or device:
- Users are redirected to an interaction page to enter their credentials. They have the option to click on the Enter one-time password link to enter the OTP obtained from Authenticator.
- Ivanti Access validates the OTP entered by the user against the OTP generated by Ivanti Access for the activated device for that user. A match completes the second-factor authentication of the user.
- Ivanti Access verifies and retrieves the user identity from the activated device and generates a new SAML response to redirect to the original SP.
- The original SP obtains the user identity from the SAML response and presents the personalized screen to the user.
Authenticator app features
The Authenticator app provides the following features:
- The Authenticator app is easy to activate or deactivate on users' managed devices.
- Device users can either allow or block access to requests. They may want to deny access if an unknown user attempts to access an enterprise cloud service.
- If a request is not allowed or blocked within 5 minutes, the request expires and the authentication attempt from the device is blocked.
- Device users have the option to generate a one-time passcode (OTP) instead of using push notifications.
- If the managed device is locked, a notification is presented. Users unlock the device to view the request in Authenticator.
- Authenticator provides information about the service being accessed and device information and location.
- Administrators can add their company branding to the Authenticator app.