Configuring Mobile App Single Sign-on (SSO)
In an Ivanti Access deployment, single sign-on (SSO) allows users access to enterprise cloud services from the apps on their mobile devices without having to enter passwords. Single sign-on is available only for managed apps, including the Safari browser, on managed devices using Ivanti Tunnel. Access identifies the user based on the certificate used to establish the VPN tunnel. Based on the information provided in the certificate, Ivanti Access generates a federation response to the service provider (SP) without redirecting the user to the original identity provider (IdP). Access determines the contents of the federation response based on the Native Mobile Application Single Sign-On (SSO) configuration in Ivanti Access, which includes the user identifying information that the SP expects.
The user identifying information that the SP expects is typically available in the enterprise LDAP directory. The UEM SCEP that Ivanti Tunnel uses captures the user information from LDAP and makes the information available in the Ivanti Tunnel certificate. The Native Mobile Application Single Sign-On (SSO) configuration uses the information from the Ivanti Tunnel certificate in the federation response to the SP.
This feature is also referred to as certificate-based single sign-on.
Before you begin
-
Ensure that the user identifying information that the service provider (SP) expects is available in the Ivanti Tunnel certificate.
The following are examples of user identifying information:
- Email address
- Immutable ID
-
Configure the subject alternative names in the SCEP setting for the Ivanti Tunnel certificate in the UEM.
Example: If you are using the email address and immutable ID as the user identifying information, configure the following in the subject alternative name:
Type
Value
RFC 822 Name
$EMAIL$
NT Principal Name
(Required only for Office 365, holds the unique immuatble ID)$USER_CUSTOM1$
- SCEP obtains users information from LDAP. Therefore, ensure that the LDAP settings in UEM fetch the appropriate attributes from LDAP. If you are using email and immutable ID as the user identifying information, ensure that the following values are available in LDAP settings in UEM:
- Email: userPrincipalName
- Custom 1: ObjectGUID
- For more information, see Configuring Ivanti EPMM for SSO certificates, Configuring Ivanti Neurons for MDM for SSO certificates, and Customizing certificates for single sign-on in Ivanti Access.
- To make it easier to configure mobile application single sign-on, upload a sample Ivanti Tunnel certificate and assign user friendly names to each field in the certificate. For more information, see User Certificates.
Procedure
- In Ivanti Access, go to Profile > Federated Pairs.
- Click +Add New Pair or edit an existing pair.
-
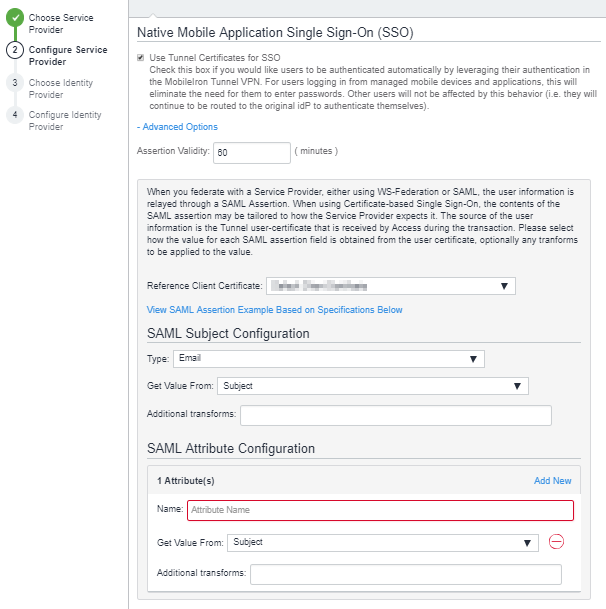
In the service provider (SP) configuration page, scroll down to the Native Mobile Application single Sign-On (SSO) section.
Figure 1. Application single sign-on advanced options
- Select Use Ivanti Tunnel Certificates for SSO.
- Expand Advanced Options.
- From the Reference Client Certificate drop-down list, select the sample Ivanti Tunnel certificate.
- In the SAML Subject Configuration section, for Type, select
- Unspecified for SAML
- the type the service provider expects for WS-Fed.
- For Get Value From, select the certificate field from which to get the value.
You created the user-friendly names when you added the sample Ivanti Tunnel certificate to Access in the User Certificates tab. - (Optional) For Additional Transforms: Enter the required transforms if the SP expects values that are derived from the value provided in the certificate.
- (Optional) SAML Attribute Configuration. The SAML attribute configuration populates the Attribute and value section of the federation response from Access. Configure this if the SP expects such attributes. Click New to add each new attribute.
- (Optional) For Encryption Algorithms, select the data encryption algorithm and the key transport algorithm.
The encyrption options are available only if Encrypt SAML assertions is enabled. - (Optional) Click the View SAML Assertion Example Based on Specifications Below link to verify that the SAML assertion contains the required user-identifying information.
•For information about configuring the assertion fields in a federation response, see Customizing certificates for single sign-on in Ivanti Access.
•For information about encrypting SAML assertions, see Encrypting SAML assertions