Split Tunneling
In an Ivanti Access deployment, all authentication traffic for the federated pairs configured in Access goes through Access using Tunnel VPN. Depending on the type of Ivanti Access deployment, all other traffic through Tunnel VPN goes directly to the destination server or through Standalone Sentry. Split tunneling allows you to control which traffic goes through Standalone Sentry to on-premise enterprise resources and which traffic goes directly to the destination.
For example, you may need to configure split tunneling if your deployment uses Ivanti Tunnel VPN:
• to authenticate to a service provider (SP), such as Salesforce, via Access.
•to access an internal SharePoint server such as sharepoint.mycompany.com via Standalone Sentry.
In the example, federated authentication traffic to Salesforce goes through Access, traffic to the SharePoint server goes through Standalone Sentry, and data traffic to Salesforce goes directly to the destination.
Split tunneling is supported for both Ivanti Access and Ivanti Access + Standalone Sentry deployments.
The following topics provide additional information about split tunneling:
- Split tunneling in an Ivanti Access + Standalone Sentry deployment
- Split tunneling in an Ivanti Access deployment
- Split tunneling for Android
- Split tunneling for iOS and macOS
- Overview of steps for configuring split tunneling in Ivanti Access
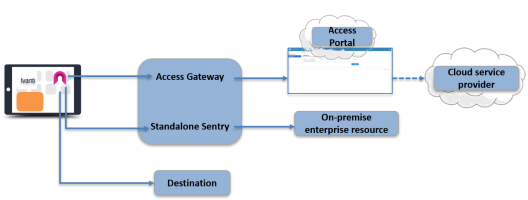
Split tunneling in an Ivanti Access + Standalone Sentry deployment
In an Ivanti Access + Standalone Sentry deployment, all authentication traffic for the federated pairs configured in Access goes to Ivanti Access. All other Ivanti Tunnel VPN traffic goes through Standalone Sentry. Split tunneling allows you to specify how the traffic that is not federated through Ivanti Access is handled. You can specify whether the traffic goes through Standalone Sentry or directly to the destination.
Split Tunneling is disabled if all the Sentry profiles from VPN are removed from all the registered EMMs.
Figure 1. Split tunneling in an Ivanti Access + Standalone Sentry deployment
Split tunneling in an Ivanti Access deployment
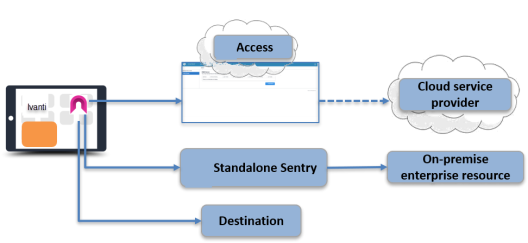
In an Ivanti Access deployment, by default, all authentication traffic for the federated pairs configured in Access goes to Access. All other traffic goes directly to the destination. However, you may require that some traffic go through Standalone Sentry to access on-premise enterprise resources. In such cases, you configure split tunneling to do the following:
•Authentication traffic for federated pairs configured in Ivanti Access goes through Access.
•Traffic to on-premise enterprise resources goes through Standalone Sentry.
•All other traffic goes directly to destination.
Figure 2. Default split tunneling in an Access (without Standalone Sentry) deployment
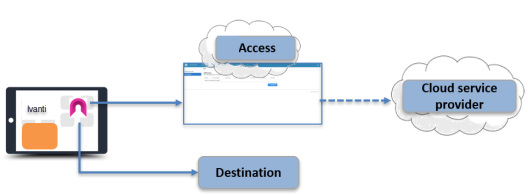
Figure 3. Split tunneling Access (without Standalone Sentry) and Standalone Sentry
Split tunneling for Android
For Android apps, split tunneling is configured in the Ivanti Tunnel VPN configuration for Android or in the Ivanti Tunnel for Android enterprise configuration. Split tunneling using Ivanti Tunnel for Android native and Android enterprise is handled in the Tunnel configuration for those devices. See the Ivanti Tunnel for Android Guide for information about setting up split domains and routes lists.
In an Ivanti Access deployment, tunneling to both enterprise cloud services and to on-premise enterprise resources is not supported with Ivanti Tunnel for Samsung Knox Workspace.
Split tunneling for iOS and macOS
For iOS apps and macOS, split tunneling is configured in Ivanti Access in Profile > Split Tunneling. The split tunneling configuration in Ivanti Access is only applicable to Ivanti Tunnel for iOS and macOS.
Overview of steps for configuring split tunneling in Ivanti Access
The following is an oveview of steps for configuring split tunneling in Ivanti Access: