Device-initiated (local) compliance for iOS jailbreak detection
MobileIron Core checks a device for compliance with its security policy each time the device checks in. checks all devices for compliance at regular intervals to detect out-of-compliance devices that have not checked in. When a device is out of compliance, initiates the specified compliance actions.
When an iOS device is jailbroken (compromised), some compliance actions can be device-initiated. Device-initiated compliance (local compliance) for jailbreak detection means:
- The Ivanti client detects the violation.
- The Ivanti client performs one or more of the following: alerts the user, blocks AppConnect apps, or retires AppConnect apps (blocks access to the apps and wipes their data).
These actions do not depend on connectivity to . However, also continues to enforce compliance actions when the device is connected.
Therefore, device-initiated compliance (local compliance) for jailbreak detection means that you can protect corporate data on devices even when the devices are off-line.
Typically, you configure a compliance action for jailbroken devices that occurs locally on the device, such as making AppConnect apps unauthorized or retired.
Compliance actions for device-initiated jailbreak detection
When Mobile@Work detects that the device is jailbroken, it can take one of the following actions:
- Alert the device user with a banner or notification.
-
Block AppConnect apps.
The device user becomes unauthorized to use AppConnect apps.
-
Retire AppConnect apps.
The device user becomes unauthorized to use AppConnect apps and the apps’ secure data is deleted.
Configuring device-initiated compliance for jailbreak detection
The following is an overview of the steps for creating a device-initiated compliance for jailbreak detection.
Creating a compliance action
Create a compliance action in the MobileIron Core Admin Portal.
Procedure
- Go to Policies & Configs > Compliance Actions.
-
Click Add+.
Figure 1. Compliance actions
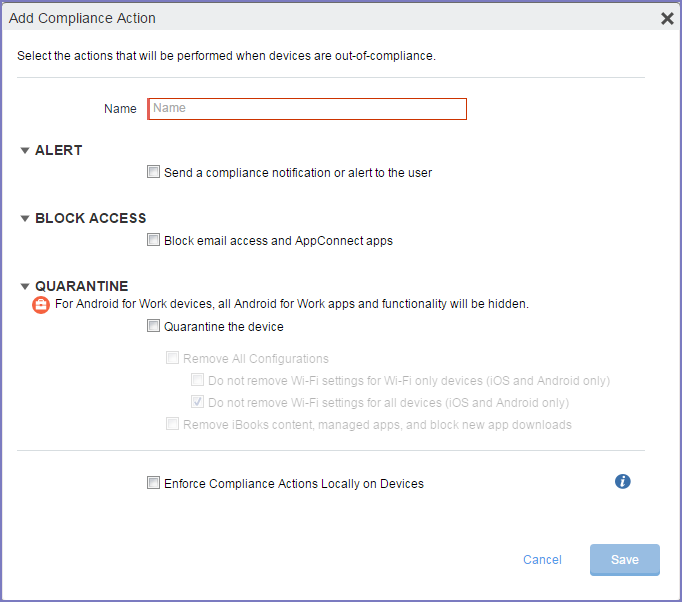
- Enter a name for the compliance action.
- Select Send a compliance notification or alert to the user if you want the device user to receive a notification.
-
Select Block email access and AppConnect apps if you want the device user to become unauthorized to use AppConnect apps when the device becomes non-compliant.
If the device is on-line, this selection also restricts access to email via ActiveSync if you are using a Standalone Sentry for email access. It also blocks AppTunnel tunnels that AppConnect apps and iOS managed apps use.
-
Select Quarantine the device if you want to retire AppConnect apps (blocks access to the apps and wipes their data) when the device becomes non-compliant.
If the device is on-line, this selection also blocks AppTunnel tunnels that AppConnect apps and iOS managed apps use.
-
Select Enforce compliance actions locally on devices.
The compliance actions are enforced locally on the device only if the security violation is that the device is jailbroken. Compliance actions for other security violations require interaction with MobileIron Core.
- Click Save.
“Compliance actions policy violations” in the Core Device Management Guide for iOS and macOS Devices.
Specifying the compliance action in the security policy
Specify a compliance action in the security policy.
Procedure
- Go to Policies & Configs > Policies.
- Select a security policy.
- Click Edit.
- In the section Access Control, in For iOS devices, select When a compromised iOS device is detected.
- In the drop-down, select the compliance action that you created.
- Click Save.