AppConnect for iOS overview
MobileIron AppConnect for iOS provides a software development kit (SDK) for securing and managing enterprise applications on mobile devices. These secure enterprise apps are called AppConnect apps or secure apps.
You can develop an AppConnect app for apps written using:
- Objective-C, by using the AppConnect for iOS Objective-C APIs.
- Swift, by using the Swift interfaces that correspond to the AppConnect for iOS Objective-C APIs. These Swift interfaces are automatically generated by Xcode when you add the AppConnect framework into your Xcode project.
- the Xamarin development platform, using Xamarin C# bindings of the AppConnect for iOS Objective-C APIs.
- Cordova (or Phonegap), by using the AppConnect for iOS Cordova Plugin, described in the MobileIron AppConnect for iOS Cordova Plugin Developers Guide.
Note The Following:
-
If your AppConnect app is to be distributed from the Apple App Store, due to Apple App Store requirements, your app is required to work as a regular app in addition to working as an AppConnect app.
-
If your app uses an older version of the AppConnect for iOS SDK, MobileIron recommends that you always rebuild your app with the current version of the SDK. Using the current version ensures the app contains all new features, improvements, and resolved issues.
-
An Apple Developer Enterprise Program account is required to distribute in-house apps. See Apple Developer Enterprise Program.
Where to get the AppConnect for iOS SDK
The AppConnect for iOS SDK ZIP flle is available at help.mobileiron.com in the Software tab.
Check for the latest updates to this document and other developer resources on: https://developer.mobileiron.com.
The SDK is also available at https://support.mobileiron.com/support/CDL.html.
Documentation is also available at https://support.mobileiron.com/docs/appconnect/.
Legal notices are also available on https://support.mobileiron.com/copyrights/ACe.
Secure app features
Secure enterprise apps that are built using the SDK can:
-
Receive app-specific configuration information from the MobileIron server.
This capability means that device users do not have to manually enter configuration details that the app requires. By automating this process for the device users, each user has a better experience when installing and setting up apps. Also, the enterprise has fewer support calls, and the app is secured from misuse due to configuration. This feature is also useful for apps which do not want to allow the device users to provide certain configuration settings for security reasons.
-
Tunnel network connections to servers behind an enterprise’s firewall.
This capability means that device users do not have to separately set up VPN access on their devices to use the app.
-
Authenticate an app user to an enterprise service.
This capability means that AppConnect app users do not have to enter login credentials to access enterprise resources.
-
Handle data loss prevention.
The MobileIron server administrator decides whether an app can copy content to the iOS pasteboard, use the document interaction feature), receive documents from other apps (Open From) use drag and drop, or print. The AppConnect library enforces the pasteboard, Open In, Open From and drag and drop policies. The app enforces the print policy.
-
Control custom keyboard use by your app.
The MobileIron server administrator can choose whether an app can use custom keyboards, and the AppConnect library enforces the choice. If the administrator does not configure this choice, your app can choose to reject custom keyboard use.
-
Blur the app’s screens when the app is not in the foreground.
This blurring occurs if you specify a particular key in your Info.plist. The AppConnect library then enforces this behavior, which can be overridden by the MobileIron server administrator.
-
Protect the app’s data independent of device level encryption.
You can protect your app’s data using APIs provided by the AppConnect for iOS SDK. This secure file
I/O capability means that data encryption for your app is not dependent on the device having a device passcode. Note that the AppConnect library and the MobileIron client app protect AppConnect-related data, such as configurations and certificates, without any special actions by the app. The secure file I/O APIs also allow you to share encrypted data among AppConnect apps. -
Obtain derived keys for custom encryption.
If your app uses custom cryptography, you can get derived encryption keys from the AppConnect library. This feature is useful for legacy apps that cannot easily convert to using the SDK’s secure file I/O APIs. Because the keys are derived, accidental leaks have limited damage, and the keys are not weakened by brute force attacks.
-
Secure sensitive data like encryption keys and passwords
The AppConnect for iOS SDK provides APIs for heightened security of especially sensitive data. These APIs use Apple hardware capabilities (Apple’s Secure Enclave) to reduce the sensitive data’s attack surface, because the data is never stored in plain-text in memory.
-
Log messages to the device’s console and files.
By using APIs provided by the AppConnect for iOS SDK, your app can log messages of different severity levels to the device’s console. The MobileIron server administrator decides the severity levels that are written to the console, and whether the logs are also written to files.
-
Provide AppTunnel diagnostics.
By using APIs provided by the AppConnect for iOS SDK, your app can log or display diagnostic data about your app’s AppTunnel configuration and usage.
-
Be FIPS compliant.
-
Deliver derived credentials to the MobileIron client app.
This capability is only for apps that obtain derived credentials from a derived credential provider and deliver the credentials to the MobileIron client app. Very few apps implement this capability. How to implement this capability is described in Derived Credential Handling.
AppConnect for iOS SDK advantages
With the AppConnect for iOS SDK:
-
You can focus on application logic.
The SDK handles low-level, complex work such as authentication to access AppConnect apps, certificate authentication to enterprise resources, tunneling, AppConnect passcode handling, data encryption, and getting app-specific settings and configuration from the MobileIron server.
-
You use a set of simple APIs to develop a secure enterprise app.
-
The app does not have to interact directly with web service interfaces to get the information it needs to behave as a secure enterprise app. Using the APIs, the app gets notified of any changes that the administrator makes on the MobileIron server to controls and configuration.
-
You can create one app, with one code base, that can behave as a secure app or a regular app. This behavior is required for secure apps that are distributed from the Apple App Store.
-
For more information, see Developing Third-party Dual-mode Apps.
64-bit and 32-bit app support
Using the AppConnect for iOS SDK, you can build an app as a 64-bit app or as a 32-bit app.
MobileIron AppConnect components
The apps that you build with this SDK work with the following MobileIron components:
|
MobileIron component |
Description |
|
MobileIron Core |
The MobileIron on-premise server which provides security and management for an enterprise’s devices, and for the apps and data on those devices. An administrator configures the security and management features using a web portal. |
|
MobileIron Connected Cloud |
The MobileIron cloud offering that has the same functionality as MobileIron Core. |
|
MobileIron Cloud |
The MobileIron cloud offering that provides similar functionality as MobileIron Core. However, it does not support all the AppConnect features that MobileIron Core supports. |
|
Standalone Sentry |
The MobileIron server which provides secure network traffic tunneling from your app to enterprise servers. |
|
The Mobile@Work for IOS app |
A MobileIron client app that runs on an iOS device. It interacts with MobileIron Core or Connected Cloud to get current security and management information for the device. It interacts with the AppConnect library to communicate necessary information to your app. |
|
The MobileIron Go app |
A MobileIron client app that runs on an iOS device. It interacts with MobileIron Cloud to get current security and management information for the device. It interacts with the AppConnect library to communicate necessary information to your app. |
|
The MobileIron AppStation app |
A MobileIron client app that runs on an iOS device. It interacts with MobileIron Cloud. It can be used on the device instead of MobileIron Go when the MobileIron Cloud tenant supports Mobile Apps Management (MAM) but not Mobile Device Management (MDM). It interacts with the AppConnect library to communicate necessary information to your app. |
|
The AppConnect library |
The MobileIron library that your app uses to get AppConnect information. The AppConnect library is part of the AppConnect framework that your app includes. It provides your app management and security capabilities, and facilitates communication between your app and the MobileIron client app. |
Note The Following:
- MobileIron Core, MobileIron Connected Cloud, and MobileIron Cloud are each also referred to as a MobileIron server.
- Mobile@Work, MobileIron Go, and MobileIron AppStation are each also referred to as a MobileIron client app.
| IMPORTANT: | Some AppConnect features depend on the version of MobileIron Core, MobileIron Cloud, Standalone Sentry, and the MobileIron client app. |
Using a secure app
A device user can use a secure enterprise app only if:
-
The device user has been authenticated through the MobileIron server.
The user must use the MobileIron client app to register the device with the MobileIron server. Registration authenticates the device user.
-
The server administrator has authorized the device user to use the app.
-
The device user has entered a secure apps passcode or Touch ID/Face ID.
The server administrator configures whether a secure apps passcode, also called the AppConnect passcode, is required, and configures its complexity rules. The administrator also configures whether using Touch ID/Face ID, if available on the device, is allowed instead of the AppConnect passcode.
The AppConnect passcode is not the same as the passcode used to unlock the device.
App responsibilities
Your app is responsible for:
- enforcing the authorization settings
- handling the data loss prevention settings
- using the app-specific configuration
- ensuring the app’s data is protected by using the AppConnect secure file I/O APIs
- logging messages at the appropriate log level to protect sensitive data
- logging or displaying AppTunnel diagnostic information (optional)
- preserving and restoring the app’s state when control switches from the app to the MobileIron client app and back
MobileIron client app and AppConnect library responsibilities
The MobileIron client app and the AppConnect library are responsible for:
- authenticating the user to the MobileIron server
- authenticating to enterprise services using certificates
- tunneling network connections
- AppConnect passcode and Touch ID / Face ID handling
- protecting AppConnect-related data, such as configurations and certificates
- managing the encryption key for the AppConnect secure file I/O
- controlling when sensitive log messages are written
AppConnect for iOS SDK variants
Due to Apple deprecating the UIWebView class, the AppConnect for iOS SDK is available in two variants. One with UIWebView support and another without the support for UIWebView. The AppConnect SDK without UIWebView support is available to use for apps that are submitted to the App Store.
AppConnect for iOS SDK contents
The AppConnect for iOS SDK is available as a ZIP file called AppConnectiOSSDK_V<version>_<build>.zip, where:
- <version> is the version number of the SDK.
- <build> is the build number of the SDK.
The ZIP file contains the following:
-
AppConnect.framework, which you include in your app’s set of frameworks.
The AppConnect.framework includes the AppConnect library and header files.
-
AppConnectExtension.framework, which you include in an extension of an AppConnect app to share files with a host app. AppConnectExtension.framework includes the AppConnect extension library and header files.
-
A Documentation folder, which contains,
-
this document
Check for updates to this document as described in Where to get the AppConnect for iOS SDK.
-
- A plugins folder, which contains,
the cordova folder, which contains the Cordova plugin, sample apps, the install_ac_cordova_plugin.sh script, and documentation
the xamarin folder, which contains the Xamarin C# bindings, sample apps, and C# API documentation.
-
the script post_embed_actions.sh
See Add AppConnect files and settings to your Xcode project.
-
Notices.pdf, which contains SDK copyright information, software, and licenses.
-
README_license.pdf, which contains the SDK license agreement.
-
A Samples folder, which contains these sample apps:
-
HelloAppConnect, which demonstrates how an app uses the AppConnect framework. It displays its authorization status, its app configuration, and its data loss prevention policies.
The sample includes both an Objective-C and a Swift version of the app.
-
DualMode example, which demonstrates the behavior of a dual-mode app.
-
SwiftFileSharing app, a Swift app demonstrating AppConnect API usage, including sharing secure files from an extension.
-
-
The SDK_without_UIWebView folder which contains the iOS SDK variant that does not support UIWebView. The folder includes the following:
-
AppConnect.framework, which you include in your app’s set of frameworks.
The AppConnect.framework includes the AppConnect library and header files.
-
AppConnectExtension.framework, which you include in an extension of an AppConnect app to share files with a host app.
AppConnectExtension.framework includes the AppConnect extension library and header files.
- A plugins folder, which contains:
the cordova folder, which contains the Cordova plugin, sample aspps, the install_ac_cordova_plugin.sh script, and documentation
the xamarin folder, which contains the Xamarin C# bindings, sample apps, and C# API documentation.
-
Header files in AppConnect.framework
The following header files are included in the AppConnect.framework:
|
Header file |
Description and related topics |
|
ACCompatibility.h |
Header file for compatibility of AppConnect constants with Swift. |
|
ACDerivedCredential.h |
Described in Derived credential header files. |
|
ACDerivedCredentialService.h |
Described in Derived credential header files. |
|
ACError.h |
Defines the error domain and error codes used by the SDK’s POSIX-style APIs, and Objective-C secure file subclasses and categories. |
|
ACFileHandle.h |
Defines a NSFileHandle subclass for secure file I/O. |
|
ACFileHandle.h+ACSharedSecureFile.h
|
Defines a category for sharing secure files with another AppConnect app. |
|
ACSecureFile.h |
|
|
ACSensitiveData.h
|
Defines the classes for using heightened security for sensitive data such as encryption keys. |
|
ACTypes.h
|
Defines AppConnect typedef enumerations used in AppConnectInterface.h. |
|
ACUnwrappedFile.h
|
Defines the class for a host app to use to unwrap a secure file shared by an extension. |
|
ACWrappedAppKey.h
|
Defines the class for a provider app to use to create an encryption key for encrypting shared files in its extension. |
|
ACWrappedFileReadHandle.h
|
Defines the class for a host app to use to get the file handle of an extension’s shared, wrapped file. |
|
AppConnect.h |
Umbrella header file for the AppConnect.framework, importing all the header files in the framework. |
|
AppConnect+Networking.h |
Defines the following APIs:
|
|
AppConnectInterface.h |
|
|
AppConnectUIApplication.h |
Defines the UIApplication subclass that the AppConnect library uses. An app imports this header file only if it uses a subclass of UIApplication. |
|
NSArray+ACSecureFile.h |
Defines NSArray category interfaces for secure file I/O. |
|
NSData+ACSecureFile.h |
Defines NSData category interfaces for secure file I/O. |
|
NSData+ACSharedSecureFile.h |
Defines NSData category interfaces for secure file I/O when sharing data among AppConnect apps. |
|
NSDictionary+ACSecureFile.h |
Defines NSDictionary category interfaces for secure file |
|
NSFileManager+ACSecureFile.h |
Defines NSFileManager category interfaces for secure file I/O. |
|
NSKeyedArchiver+ACSecureFile.h |
Defines NSKeyedArchiver category interfaces for secure file |
|
NSKeyedUnarchiver+ACSecureFile.h |
Defines NSKeyedUnarchiver category interfaces for secure file operations. |
|
NSMutableArray+ACSecureFile.h |
Defines NSMutableArray category interfaces for secure file I/O. |
|
NSMutableDictionary+ACSecureFile.h |
Defines NSMutableDictionary category interfaces for secure file I/O. |
Header files in AppConnectExtension.framework
The following header files are included in the AppConnectExtension.framework:
|
Header file |
Description and related topics |
|
ACWrappedFile.h |
Defines the ACWrappedFile class used by extensions to share secure files. |
|
AppConnectExtension.h |
Umbrella header file for the AppConnectExtension.framework, importing all the header files in the framework. |
|
AppConnectExtensionInterface.h |
Defines AppConnectExtensionInterface class and AppConnectExtensionInterfaceProtocol. |
AppConnect for iOS architecture
Your app, using the AppConnect library, interacts with the MobileIron client app. The MobileIron client app is either Mobile@Work for iOS, MobileIron Go for iOS, or MobileIron AppStation for iOS. Mobile@Work interacts with Core and MobileIron Go interacts with MobileIron Cloud. AppStation is used in certain use cases instead of MobileIron Go to interact with MobileIron Cloud when a MobileIron Cloud tenant is set up for Mobile Apps Management (MAM) but not Mobile Device Management (MDM). The AppConnect library also interacts with Standalone Sentry for AppTunnel support.
The following diagram illustrates the interactions between an AppConnect app, the AppConnect library, the MobileIron server, the MobileIron client, and the Standalone Sentry. The diagram uses MobileIron Core for the server and Mobile@Work for the client.
Figure 1. AppConnect app interaction
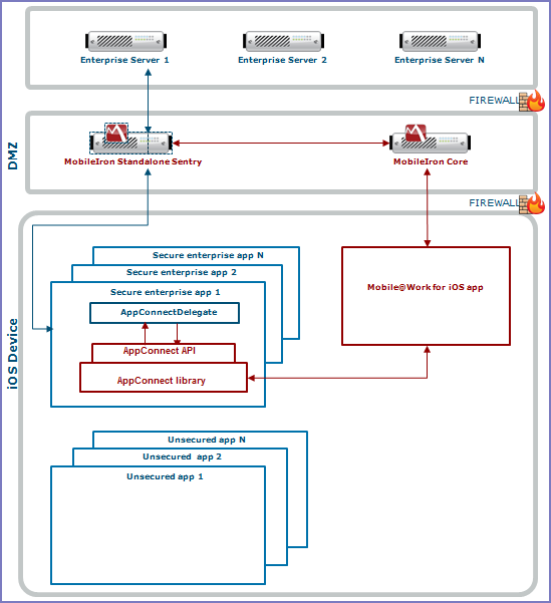
Note The Following:
- Each secure enterprise app communicates with an AppConnect singleton object, which contains the AppConnect library.
- The AppConnect library communicates with the MobileIron client app.
- The app uses the AppConnect API to get management and security-related information, such as whether the server administrator has authorized the app to run on the device.
- Each secure enterprise app creates an object that implements the AppConnectDelegate protocol. This object receives notifications from the AppConnect library. These notifications tell the app about changes to management and security-related information.
- The MobileIron client app communicates with the MobileIron server to get management and security-related information.
The MobileIron server provides security and management for an enterprise’s devices, and for the apps and data on those devices. An administrator configures the security and management features using a web portal. - The AppConnect object interacts with a Standalone Sentry if it is tunneling network connections to an enterprise server behind the firewall.
The MobileIron client app and AppConnect apps
The MobileIron client app supports AppConnect apps, including the following tasks:
-
It communicates with the MobileIron server to get management and security-related information and passes the information to the AppConnect apps.
The MobileIron client app periodically does an app checkin with the MobileIron server to get this information. The administrator configures the app checkin interval on the MobileIron server. It is the maximum time between app checkins while an AppConnect app is running.
-
It enforces the AppConnect passcode or Touch ID/Face ID.
The MobileIron client app prompts the device user to create an AppConnect passcode or Touch ID/Face ID when first launching any AppConnect app. The administrator configures an auto-lock timeout on the MobileIron server. After this period of inactivity, the MobileIron client app prompts the device user to reenter his AppConnect passcode or Touch ID/Face ID.
When you run your AppConnect app, the MobileIron client app sometimes automatically launches to support app checkin and the AppConnect passcode or Touch ID/Face ID. Understanding the MobileIron client app expected behavior can help you when you test your AppConnect app.
App checkin and the MobileIron client app
On each app checkin, the MobileIron client app gets AppConnect policy updates for all the AppConnect apps that have already run on the device. These updates include changes to data loss prevention policies, password settings, app configurations, and AppTunnel settings.
For example, for Mobile@Work, these updates are due to changes on MobileIron Core to:
- the AppConnect global policy for the device.
- AppConnect container policies for each of the AppConnect apps that have run on the device.
- AppConnect app configurations for each of the AppConnect apps that have run on the device.
- the current authorization status for each of the AppConnect apps that have run on the device.
The MobileIron client app does an app checkin in the following situations:
-
The device user launches an AppConnect app for the first time.
In this situation, the MobileIron client app finds out about the app for the first time, and adds it to the set of AppConnect apps for which it gets updates.
-
The app checkin interval expires while an AppConnect app is running.
-
The app checkin interval expired while no AppConnect apps were running and then the device user launches an AppConnect app.
In each of these situations, the MobileIron client app launches, and the device user sees the MobileIron client app momentarily. Once the MobileIron client app has completed the app checkin, the device user automatically returns to the AppConnect app.
The auto-lock timeout and the MobileIron client app
The MobileIron client app launches to prompt the device user for the AppConnect passcode or Touch ID/Face ID in the following situations:
- The auto-lock (inactivity) timeout expires while the device is running an AppConnect app and the AppConnect passcode, or Touch ID/Face ID, is the login mechanism.
If the device user is interacting with the app, the auto-lock timeout does not expire. This case occurs only when the device user has not touched the device for the duration of the timeout interval.
- The device user used the MobileIron client app to log out of AppConnect apps, and then launches an AppConnect app.
- The server administrator has changed the complexity rules of the AppConnect passcode, and an app checkin occurs.
In each of these situations, the MobileIron client app launches, and presents the device user with a screen for entering his AppConnect passcode or Touch ID/Face ID. After the device user enters the passcode or Touch ID/Face ID, the device user automatically returns to the AppConnect app.