AppTunnel with TCP tunneling
AppTunnel can tunnel TCP traffic between an app and a server behind the company’s firewall, securing the data-in-motion. A Standalone Sentry is necessary to support AppTunnel with TCP tunneling. Also, support for AppTunnel with TCP tunneling requires wrapping the app with the Generation 2 wrapper.
UDP tunneling is not supported.
Inform the server administrator that your app requires AppTunnel with TCP tunneling,including information about the enterprise server that it accesses. The administrator requires this information to correctly configure AppTunnel with TCP tunneling for your app on the Ivanti server. Once configured, the AppConnect wrapper, the Secure Apps Manager, and the client app, manage TCP tunneling. No additional app development is necessary.
When to use AppTunnel with HTTP/S tunneling versus TCP tunneling
AppTunnel with TCP tunneling, rather than AppTunnel with HTTP/S tunneling, is required to secure data-in-motion for:
- Java apps that use C or C++ code to access an enterprise server
- Java apps that use APIs outside of the specific set of HTTP/S APIs that AppTunnel with TCP tunneling supports.
You can also use AppTunnel with TCP tunneling with Java apps that do use the HTTP/S APIs that AppTunnel with HTTP/S tunneling supports. However, AppTunnel with TCP tunneling is not necessary for such apps, since AppTunnel with HTTP/S tunneling is supported.
-
Xamarin apps that use APIs other than ModernHTTPClient.
-
Hybrid web apps, including Cordova apps
These apps use Android WebView and WebKit technologies to access and display web content. Because WebView does not use one of the HTTP/S APIs that AppTunnel with HTTP/S tunneling supports, AppTunnel with TCP tunneling is required.
-
React Native apps
Because React Native apps do not use one of the HTTP/S APIs that AppTunnel with HTTP/S tunneling supports, AppTunnel with TCP tunneling is required.
AppTunnel with TCP tunneling does not support Kerberos authentication to the enterprise server. It supports only pass through authentication. With pass through authentication, the Standalone Sentry passes the authentication credentials, such as the user ID and password (basic authentication) or NTLM, to the enterprise server. Therefore, apps that must use AppTunnel with TCP tunneling, such as hybrid apps, cannot use Kerberos authentication to the enterprise server. However, these apps can use Certificate authentication with AppTunnel with TCP tunneling.
The following table shows whether to use AppTunnel with HTTP/S tunneling or TCP tunneling with an Android secure app depending on the code that is making the network connection. It also shows which generation of the wrapper you can use.
|
Code type |
AppTunnel with HTTP/S tunneling |
AppTunnel with TCP tunneling |
|
Java code using supported HTTP/S APIs |
Supported with: •Generation 1 wrapper •Generation 2 wrapper |
Supported with Generation 2 wrapper |
|
Java code using unsupported HTTP/S APIs |
Not supported |
Supported with Generation 2 wrapper |
|
Xamarin apps using supported HTTP/S APIs |
Supported with Generation 2 wrapper |
Supported with Generation 2 wrapper |
|
Xamarin apps using unsupported HTTP/S APIs |
Not supported |
Supported with Generation 2 wrapper |
|
C or C++ code |
Not supported |
Supported with Generation 2 wrapper |
|
Hybrid web app, including Cordova |
Not supported |
Supported with Generation 2 wrapper |
|
React Native app |
Not supported |
Supported with Generation 2 wrapper |
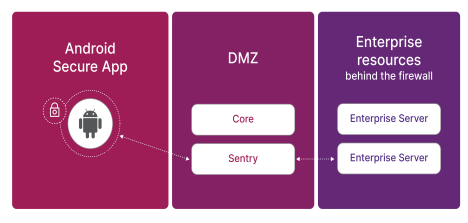
SSL between the device and Sentry
When an app uses AppTunnel with TCP tunneling, the traffic between the device and the Standalone Sentry is secured using an Secure Sockets Layer (SSL) session, as shown in the following diagram.
AppTunnel with TCP tunneling