Compliance actions policy violations
You can assign compliance actions for security policy violations and for compliance policy violations. When you configure access control in either type of policy, you can select default compliance actions that are provided with MobileIron Core. You can also select custom compliance actions that you create.
Figure 1. Compliance actions policy violations
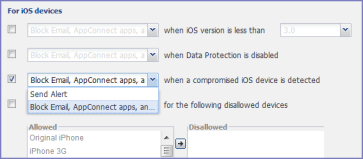
| NOTE: | To create the custom compliance actions, see Custom compliance actions. |
Default compliance actions
The following table describes the default compliance actions:
|
Default compliance action |
Description |
|||||||||||||||
|
Send Alert |
Sends alert that you configured for the policy violation. To configure the alert, see Policy violations event settings. |
|||||||||||||||
|
Block Email, AppConnect Apps And Send Alert |
AppConnect apps become unauthorized when the next device checkin occurs. When the device user tries to launch an AppConnect app, the Secure Apps Manager displays a small pop-up message with the reason the app is unauthorized.
|
|||||||||||||||
|
Customized compliance actions |
These actions can contain 4 tiers of actions. Tiers 2-4 are only used in compliance policies; they are not used by legacy security policies. Security policies only perform the action defined in tier 1. |
Custom compliance actions
You can customize the compliance actions that you want to take for the settings on the Compliance Actions page under Policies & Configs. After you create your customized compliance actions, the actions you created appear in a drop-down list in the Access Control section of your security policies.
Custom compliance actions enable you to specify combinations of the following actions:
- Send alert
- Block email access and AppConnect apps (includes blocking app tunnels)
- Quarantine: block email access, block app tunnels, block AppConnect apps, and wipe AppConnect app data
- Remove configurations (i.e., profiles)
- Specify exceptions for Wi-Fi-only devices
Once you create a set of these actions, you can select that set from the drop downs in the Access Control section of security policies.
Creating a compliance action
With custom compliance actions, you can create actions to better manage access control. With tiered compliance actions, you can customize them to include up to 4 levels of action to better manage compliance actions.
Procedure
- Log into the Admin Portal.
- Go to Policies & Configs > Compliance Actions.
- Click Add+ to open the Add Compliance Action dialog box.
- Select the appropriate fields as described in the Add Compliance Action table.
| NOTE: | If you have selected Show for the Custom ROM Related Functions in Settings > System Settings > Android > Android Custom ROM, then the wipe action is available. To enable wipe, first read and select the caution statement. You can then select Wipe the device. The wipe option applies to Android devices only. |
- If you want to add another set of actions, click the plus (+) button and select the fields, as necessary, to complete the second compliance action.
- If you want to add another set of actions, click the plus (+) button and select the fields, as necessary, to complete the third compliance action.
- Click Save to add the new compliance action for access control and compliance actions.
- You can select them by going to:
- Policies & Configs > Policies > policy > Edit > Access Control section (1 tier only).
- Policies & Configs > Compliance Policies > Add+ > Compliance Policy Rule > Compliance Actions drop-down (1-4 tiers).
Add Compliance Action table
The following table describes the Add Compliance Actions options:
Table 2. Add Compliance Action fields
|
Item |
Description |
||||||||||||
|
Name |
Enter an identifier for this set of compliance actions. Consider specifying the resulting action so that the action will be apparent when you are editing a security policy. |
||||||||||||
|
Enforce Compliance Actions Locally on Devices |
|
||||||||||||
|
ALERT: Send a compliance notification or alert to the user |
Select if you want to trigger a message indicating that the violation has occurred. Core sends alerts to users, administrators, or both. To configure the alert, see Policy violations event settings. |
||||||||||||
|
BLOCK ACCESS: Block email access and AppConnect apps |
AppConnect apps become unauthorized when the next app checkin occurs. When launched, an AppConnect app displays a message and exits. Some iOS AppConnect apps that have portions that involve only unsecured functionality can allow the user to use only those portions. AppConnect apps become unauthorized when the next device check in occurs. When the device user tries to launch an AppConnect app, the Secure Apps Manager displays a small pop-up message with the reason the app is unauthorized. This action impacts AppConnect apps, as well as third-party AppConnect for Android apps. |
||||||||||||
|
QUARANTINE: (Select this check box to display the other Quarantine options.) |
AppConnect apps become unauthorized and their data is wiped when the next device checkin occurs. When the device user tries to launch an AppConnect app, the Secure Apps Manager displays a small pop-up message with the reason the app is unauthorized. This action impacts AppConnect apps, as well as third-party AppConnect for Android apps.
|
||||||||||||
|
QUARANTINE: |
Select to remove the following configurations:
However, because of Android limitations, this action does not remove any certificates used in Certificate Enrollment, Certificate, and Wi-Fi configurations. These certificates are installed into the device’s credential storage. Only the device user can remove them by using the Clear Credential Storage command in the Android Settings app on the device. Certificates used in Exchange and VPN configurations are removed because these certificates are stored in the respective apps. Also, certificates installed in a Samsung Knox device’s credential store are removed.
|
||||||||||||
|
QUARANTINE: |
|
||||||||||||
|
QUARANTINE: |
|
||||||||||||
|
QUARANTINE: |
Select this option to remove Managed Apps from the device and block access to Apps@Work when the device is not compliant. (Applicable only for Android enterprise apps and only if the "Quarantine app when device is quarantined" check box in the App Catalog is selected.)
|
||||||||||||
|
Retire: |
Select to trigger a local retire action on an Android enterprise device. See the "Retiring an Android enterprise device" section in the Managing the Android enterprise device life cycle topic for the specific actions that are taken. This selection protects work profile data from data leakage by retiring the work profile on a personal device or performing a factory reset on a managed device. These actions are performed only locally on the device by Mobile@Work. Also, the Retire action is only visible when you select the Enforce Compliance Actions Locally on Devices check box and it is only available in tier 1. WARNING: This action cannot be reversed. |
When the compliance action takes effect
When you first apply a security policy, several factors affect the amount of time required to communicate the changes to targeted devices:
- sync interval
- time the device last checked in
- battery level
- number of changes already queued
- whether Enforce Compliance Actions Locally on Devices is selected.
Once the change reaches the device, MobileIron Core checks the device for compliance. If the device is out of compliance, then the action is performed.