Enabling SafetyNet attestation on Android devices
In the Core Admin Portal, you can enable Google SafetyNet attestation on Android devices to verify the integrity of the devices' software and hardware. This action provides Core with the devices' SafetyNet attestation status. With this status, you can:
•Take actions on untrusted devices.
•Deliver policies, configurations, and apps to only trusted devices.
•Assess whether the Mobile@Work app running on a device is valid, or if it is a malicious app pretending to be Mobile@Work.
This feature attests, or verifies, various information about the device. Specifically, this feature:
•certifies the manufacturer and model of devices
•provides information about Mobile@Work
•certifies the device is intact and has not been tampered with
•verifies that the Google Play version installed on the device supports SafetyNet
SafetyNet attestation works with any Android deployment, including work profiles, managed devices, and managed devices with work profiles. It also works when the device is in device admin mode.
If SafetyNet is enabled on the security policy of the device, Core initiates a SafetyNet attestation check when:
•the device has been rebooted or
• the last SafetyNet check was performed more than 24 hours ago.
Safety attestation requires that the device is running Mobile@Work 10.1 for Androidor supported newer versions.
SafetyNet attestation flow
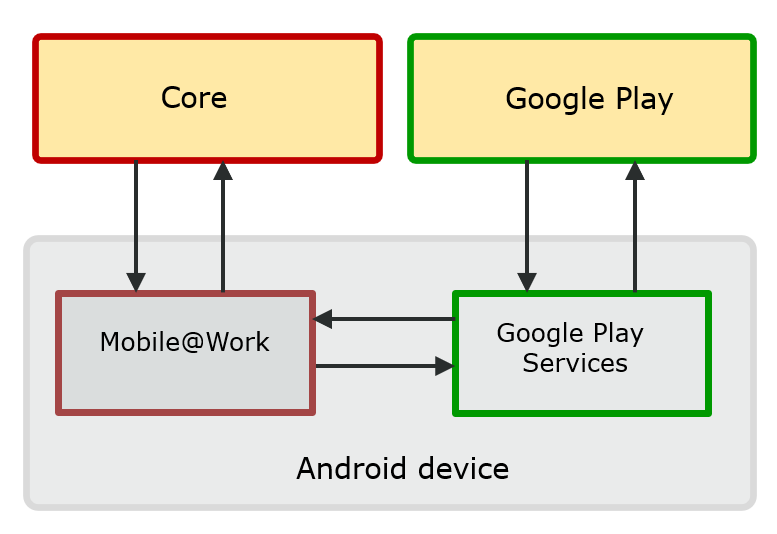
When Core initiates a SafetyNet attestation check for a device, it sends a request to Mobile@Work. Mobile@Work requests Google Play Services to do the check, and Google Play Services communicates with Google Play. Google Play Services returns the results to Mobile@Work, which returns the results to Core. The following figure illustrates this flow.
Figure 1. SafetyNet attestation flow
Setting SafetyNet attestation
To configure Core to initiate SafetyNet attestation for devices, do the following.
Procedure
| 1. | Log into the Admin Portal. |
| 2. | Go to Policies & Configs > Policies. |
| 3. | Select a security policy and click Edit. |
Alternatively, create a new security policy by clicking Add New > Security.
| 4. | Scroll down to the Android section. |
| 5. | Select “Require Google SafetyNet Attestation”. |
| 6. | Click Save. |
"Security policies" in Getting Started with Core
Basic integrity check and CTS profile verification
SafetyNet attestation provides two checks for the device:
•the basic integrity check
Verifies that the device has not been tampered with.
•the Google Compatibility Test Suite (CTS) profile verification.
Verifies that the device meets the requirements of a device that has passed Android compatibility testing.
SafetyNet attestation information in device details
In the Admin Portal, in the Device Details of a device at Devices & Users > Devices, you can view the following fields about SafetyNet attestation. You can also use these fields in Advanced Search, including creating labels.
Table 1. SafetyNet attestation information
|
Status on Device |
Description |
|
SafetyNet Enabled |
Indicates whether the security policy applied to the device has SafetyNet enabled. |
|
SafetyNet Exception |
Indicates an exception occurred while running SafetyNet attestation on the device. |
|
SafetyNet Timestamp |
The date and time when Core last received a SafetyNet attestation response from the device. |
|
SafetyNet Status |
The results of the last SafetyNet attestation, described in the next table. |
The following table explains the values of the SafetyNet Status field in a device's Device Details.
Table 2. SafetyNet status values
|
Core Status |
Description |
|
Compatible |
Core received a successful response, indicating a positive response to both the basic integrity test and the CTS profile verification. |
|
Basic |
Core received a successful response to the basic integrity check, but received a failed response to the CTS profile verification. |
|
Fail |
Core received a response, but received failed responses to basic integrity and CTS profile. This status indicates that a device is uncertified. |
|
Unsupported |
This status occurs when either: •Mobile@Work determines that SafetyNet attestation is not supported on the device. •The device is running a version of Mobile@Work for Android prior to Mobile@Work 10.1. |
|
Unknown |
Either Mobile@Work timed out waiting for results, or Core did not receive results in the acceptable time interval. Examples of legitimate reasons for an Unknown state are when a user is in airplane mode or has lost network connectivity. Therefore, be cautious about the actions you assign to devices that display this status. |
|
Tampered Client |
Core received a response that Mobile@Work is not valid, indicating the device has been tampered with. |
|
Error |
Either an exception occurred when calling SafetyNet or there was some other error. |