Custom SSL
This VPN connection type is supported on iOS devices. It is not supported on macOS, Android, and Windows devices.
The Custom SSL connection type is for SSL VPN solutions that have a third-party app in the App Store. Use the following guidelines to configure a Custom SSL VPN.
Within these selections, you may make settings for:
iOS VPN profiles and password caching
To facilitate iOS deployments, Ivanti EPMM offers the option of caching a user’s VPN password. This option is turned off by default. Cached passwords are encrypted, stored on the appliance, and used only for authentication. Note that the password must match the LDAP password in order for this feature to be of use.
Proxy - None (default)
Use the following guidelines to configure a Custom SSL VPN connection without a proxy.
|
Item |
Description |
|
Name |
Enter a short phrase that identifies this VPN setting. |
|
Description |
Provide a description that clarifies the purpose of these settings. |
|
Channel |
For macOS only. Select one of the following distribution options: •Device channel - the configuration is effective for all users on a device. This is the typical option. •User channel - the configuration is effective only for the currently registered user on a device. |
|
Connection Type |
Select Custom SSL (iOS and macOS only). |
|
Server |
Enter the IP address, hostname, or URL for the VPN server. |
|
Proxy |
None is the default setting. To configure a Manual or Automatic proxy, go to Proxy - Manual or Proxy - Automatic. |
|
Username |
Specify the user name to use (required.) The default value is $USERID$. Use this field to specify an alternate format, such as: $USERID$, $EMAIL$, $SAM_ACCOUNT_NAME$, $USER_CUSTOM1$, $USER_CUSTOM2$, $USER_CUSTOM3$, $USER_CUSTOM4$, $CUSTOM_DEVICE_Attributename$, $CUSTOM_USER_Attributename$, $NULL$ You can use combinations such as the following:
Enter $NULL$ if you want the field presented to the user to be blank. Users will need to fill in the relevant username. Some enterprises have a strong preference concerning which identifier is exposed. |
|
User Authentication |
Select the user authentication to use:
|
|
Password |
Specify the password to use (required.) The default value is $PASSWORD$. Include at least one of the following variables: $USERID$, $EMAIL$, $PASSWORD$, $USER_CUSTOM1$, $USER_CUSTOM2$, $USER_CUSTOM3$, $USER_CUSTOM4$, $CUSTOM_DEVICE_Attributename$, $CUSTOM_USER_Attributename$, $NULL$ You can use combinations such as $EMAIL$:$PASSWORD$ Enter $NULL$ if you want the field presented to the user to be blank. Users will need to fill in the relevant password. |
|
Identifier |
App Store identifier for the VPN app being configured. The app creator should provide this information. |
|
VPN on Demand |
This setting applies to iOS and macOS devices only. Select to enable VPN On Demand. The On Demand Rules field displays. On Demand rules are associated with an array of dictionaries that define the network match criteria identifying a particular network location. VPN On Demand matches the dictionaries in the On Demand Rules against properties of your current network connection to determine whether domain-based rules should be used in determining whether to connect, then handles the connection as follows:
VPN On Demand rules are applied when the device's primary network interface changes, for example when the device switches to a different Wi-Fi network.
|
|
Per-app VPN |
Select Yes to create a per-app VPN setting. An additional license may be required for this feature. The Provider Type field displays. Per-app VPN is supported on iOS devices version 9.0 through the most recently released version of iOS or supported newer versions. You cannot delete a per-app VPN setting that is being used by an app. Remove the per-app VPN setting from the app before you delete the setting. You can enable per-app VPN for an app when you:
When multiple labels are assigned to associate the selected VPN configurations in the Per-App VPN section, then VPN prioritization will happen in the order of the selected list. See the Ivanti EPMM Apps@Work Guide for information about how to add or edit apps.
|
Continue to Domains.
Continue to Custom Data.
Proxy - Manual
Use the following guidelines to configure a Custom SSL VPN connection with a manual proxy.
|
Item |
Description |
|
Name |
Enter a short phrase that identifies this VPN setting. |
|
Description |
Provide a description that clarifies the purpose of these settings. |
|
Channel |
For macOS only. Select one of the following distribution options:
|
|
Connection Type |
Select Custom SSL (iOS and macOS only). |
|
Server |
Enter the IP address, hostname, or URL for the VPN server. |
|
Proxy |
Select Manual. To configure an Automatic proxy, go to Proxy - Automatic. |
|
Proxy Server URL |
Automatic Proxy Enter the URL for the proxy server. Enter the URL of the location of the proxy auto-configuration file. |
|
Proxy Server |
Enter the name for the proxy server. |
|
Proxy Server Port |
Enter the port number for the proxy server. |
|
Type |
Select Static or Variable for the type of authentication to be used for the proxy server. |
|
Proxy Server User Name |
If the authentication type is Static, enter the username for the proxy server. If the authentication type is Variable, the default variable selected is $USERID$. |
|
Proxy Server Password |
If the authentication type is Static, enter the password for the proxy server. Confirm the password in the field below. If the authentication type is Variable, the default variable selected is $PASSWORD$. |
|
Proxy Domains (iOS only) |
The VPN will only proxy for the domain and domain suffixes specified here (.com and .org are examples of top-level domain suffixes). Domain suffixes can be used to match multiple domains. For example, .com would include all .com domains, and example.com would include all domains ending in example.com, such as pages.example.com and mysite.example.com. Wildcards are not supported. Select Add+ to add a domain. |
|
Username |
Specify the user name to use (required.) The default value is $USERID$. Use this field to specify an alternate format, such as: $USERID$, $EMAIL$, $SAM_ACCOUNT_NAME$, $USER_CUSTOM1$, $USER_CUSTOM2$, $USER_CUSTOM3$, $USER_CUSTOM4$, $CUSTOM_DEVICE_Attributename$, $CUSTOM_USER_Attributename$, $NULL$ You can use combinations such as the following:
Enter $NULL$ if you want the field presented to the user to be blank. Users will need to fill in the relevant username. Some enterprises have a strong preference concerning which identifier is exposed. |
|
User Authentication |
Select the user authentication to use:
|
|
Password |
Specify the password to use (required.) The default value is $PASSWORD$. Include at least one of the following variables: $USERID$, $EMAIL$, $PASSWORD$, $USER_CUSTOM1$, $USER_CUSTOM2$, $USER_CUSTOM3$, $USER_CUSTOM4$, $CUSTOM_DEVICE_Attributename$, $CUSTOM_USER_Attributename$, $NULL$ You can use combinations such as $EMAIL$:$PASSWORD$ Enter $NULL$ if you want the field presented to the user to be blank. Users will need to fill in the relevant password. |
|
Identifier |
App Store identifier for the VPN app being configured. The app creator should provide this information. |
|
VPN on Demand |
This setting applies to iOS and macOS devices only. Select to enable VPN On Demand. The On Demand Rules field displays. On Demand rules are associated with an array of dictionaries that define the network match criteria identifying a particular network location. VPN On Demand matches the dictionaries in the On Demand Rules against properties of your current network connection to determine whether domain-based rules should be used in determining whether to connect, then handles the connection as follows:
VPN On Demand rules are applied when the device's primary network interface changes, for example when the device switches to a different Wi-Fi network.
|
|
Per-app VPN |
Select Yes to create a per-app VPN setting. An additional license may be required for this feature. The Provider Type field displays. Per-app VPN is supported on iOS devices version 9.0 through the most recently released version of iOS or supported newer versions. You cannot delete a per-app VPN setting that is being used by an app. Remove the per-app VPN setting from the app before you delete the setting. You can enable per-app VPN for an app when you:
When multiple labels are assigned to associate the selected VPN configurations in the Per-App VPN section, then VPN prioritization will happen in the order of the selected list. See the Ivanti EPMM Apps@Work Guide for information about how to add or edit apps.
|
Continue to Domains.
Continue to Custom Data.
Proxy - Automatic
Use the following guidelines to configure a Custom SSL VPN connection with an automatic proxy.
|
Item |
Description |
|
Name |
Enter a short phrase that identifies this VPN setting. |
|
Description |
Provide a description that clarifies the purpose of these settings. |
|
Channel |
For macOS only. Select one of the following distribution options:
|
|
Connection Type |
Select Custom SSL (iOS and macOS only). |
|
Server |
Enter the IP address, hostname, or URL for the VPN server. |
|
Proxy |
Select Automatic. To configure a Manual proxy, go to Proxy - Manual. |
|
Proxy Server URL |
Enter the URL for the proxy server. Enter the URL of the location of the proxy auto-configuration file. |
|
Proxy Domains (iOS only) |
The VPN will only proxy for the domain and domain suffixes specified here (.com and .org are examples of top-level domain suffixes). Domain suffixes can be used to match multiple domains. For example, .com would include all .com domains, and example.com would include all domains ending in example.com, such as pages.example.com and mysite.example.com. Wildcards are not supported. Select Add+ to add a domain. |
|
Username |
Specify the user name to use (required.) The default value is $USERID$. Use this field to specify an alternate format, such as: $USERID$, $EMAIL$, $SAM_ACCOUNT_NAME$, $USER_CUSTOM1$, $USER_CUSTOM2$, $USER_CUSTOM3$, $USER_CUSTOM4$, $CUSTOM_DEVICE_Attributename$, $CUSTOM_USER_Attributename$, $NULL$ You can use combinations such as the following:
Enter $NULL$ if you want the field presented to the user to be blank. Users will need to fill in the relevant username. Some enterprises have a strong preference concerning which identifier is exposed. |
|
User Authentication |
Select the user authentication to use:
|
|
Password |
Specify the password to use (required.) The default value is $PASSWORD$. Include at least one of the following variables: $USERID$, $EMAIL$, $PASSWORD$, $USER_CUSTOM1$, $USER_CUSTOM2$, $USER_CUSTOM3$, $USER_CUSTOM4$, $CUSTOM_DEVICE_Attributename$, $CUSTOM_USER_Attributename$, $NULL$ You can use combinations such as $EMAIL$:$PASSWORD$ Enter $NULL$ if you want the field presented to the user to be blank. Users will need to fill in the relevant password. |
|
Identifier |
App Store identifier for the VPN app being configured. The app creator should provide this information. |
|
VPN on Demand |
This setting applies to iOS and macOS devices only. Select to enable VPN On Demand. The On Demand Rules field displays. On Demand rules are associated with an array of dictionaries that define the network match criteria identifying a particular network location. VPN On Demand matches the dictionaries in the On Demand Rules against properties of your current network connection to determine whether domain-based rules should be used in determining whether to connect, then handles the connection as follows:
VPN On Demand rules are applied when the device's primary network interface changes, for example when the device switches to a different Wi-Fi network.
|
|
Per-app VPN |
Select Yes to create a per-app VPN setting. An additional license may be required for this feature. The Provider Type field displays. Per-app VPN is supported on iOS devices version 9.0 through the most recently released version of iOS or supported newer versions. You cannot delete a per-app VPN setting that is being used by an app. Remove the per-app VPN setting from the app before you delete the setting. You can enable per-app VPN for an app when you:
When multiple labels are assigned to associate the selected VPN configurations in the Per-App VPN section, then VPN prioritization will happen in the order of the selected list. See the Ivanti EPMM Apps@Work Guide for information about how to add or edit apps.
|
Continue to Domains.
Continue to Custom Data.
On Demand Rules
Applicable to: iOS 7 and later
Whenever a network change is detected, the VPN On Demand service compares the newly connected network against the match network criteria specified in each set of rules (in order) to determine whether VPN On Demand should be allowed or not on the newly-joined network.
Rule sets are checked sequentially, beginning with the first. A rule set matches the current network only if all of the specified policies in that rule set match.
If a rule set matches the current network, a server probe is sent if a URL is specified in the profile. VPN then acts according to the policy defined in the dictionary (for example, Allow, Ignore, Evaluate Connection, Connect, or Disconnect).
Define sets of evaluation rules for each action that can be taken by VPN On Demand: Allow, Connect, Disconnect, Evaluate Connection, and Ignore. You can define more than one set of rules for each type of action that can be taken. For each set of evaluation rules, the number of rules defined for that set is indicated in the No. of Rules column.
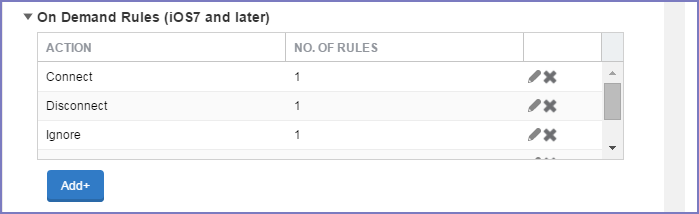
Procedure
-
Select Add+ to add a new set of On Demand evaluation rules.
A rule creation dialog box opens.
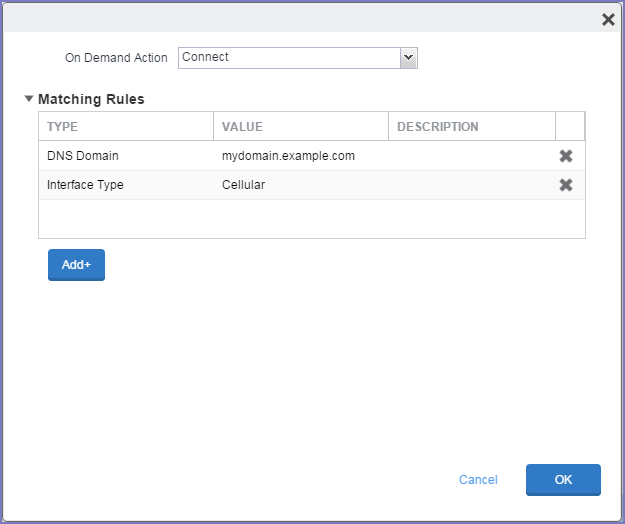
-
From the On Demand Action drop-down list, select the action you want to be taken when the rules you create below are matched.
The following actions are available:
•Allow: (Deprecated by iOS.) Allow VPN On Demand to connect if triggered.
•Connect: Unconditionally initiate a VPN connection on the next network attempt.
•Disconnect: Tear down the VPN connection and do not reconnect on demand as long as this dictionary matches.
•Evaluate Connection: Evaluate the action parameters for each connection attempt.
•Ignore: Leave any existing VPN connection up, but do not reconnect on demand as long as this dictionary matches.
-
Matching Rules - For each rule you create, enter one of the following types:
•DNS domain: This rule matches if any of the domain names in the specified list matches any domain in the device’s search domains list. A wildcard '*' prefix is supported. For example, *.example.com matches against either mydomain.example.com or yourdomain.example.com.
•DNS Server Address: This rule matches if any of the network’s specified DNS servers match any entry in the list. Matching with a single wildcard is supported. For example, 17.* matches any DNS server in the class A 17 subnet.
•SSID: A list of SSIDs to match against the current network. If the network is not a Wi-Fi network, or if the SSID does not appear in this list, the match fails. Omit this rule and the corresponding list to match against any SSID.
•Interface Type: If specified, this rule matches only if the primary network interface hardware matches the specified interface type. Choose Ethernet, Wifi, or Cellular.
•URL String Probe: A URL to probe. If this URL is successfully fetched without redirection (returning a 200 HTTP status code), this rule matches.
- Enter a value for each rule type and an optional description.
- After adding your rules, select OK.
Default Rules
Define a default rule that simply specifies a default VPN On Demand action in case none of the On Demand rules match, or if no On Demand rules have been defined.
Procedure
- From the On Demand Action drop-down list, select the action you want to be taken by default, if none of the rules match or none are defined.
-
Select Add+ to add a default rule.
The following actions are available:
•Allow: (Deprecated by iOS.) Allow VPN On Demand to connect if triggered.
•Connect: Unconditionally initiate a VPN connection on the next network attempt.
•Disconnect: Tear down the VPN connection and do not reconnect on demand as long as this dictionary matches.
•Evaluate Connection: Evaluate the action parameters for each connection attempt.
•Ignore: Leave any existing VPN connection up, but do not reconnect on demand as long as this dictionary matches.
If you select Evaluate Connection, a domain actions table displays:
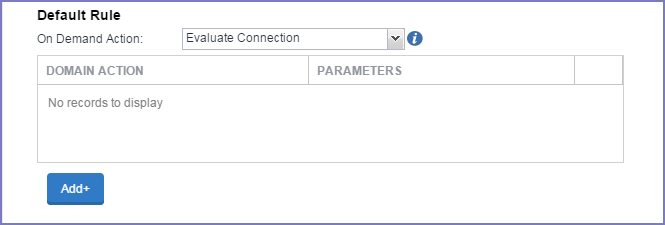
-
Select Add+ to add a domain action.
The Action Parameters dialog box opens.
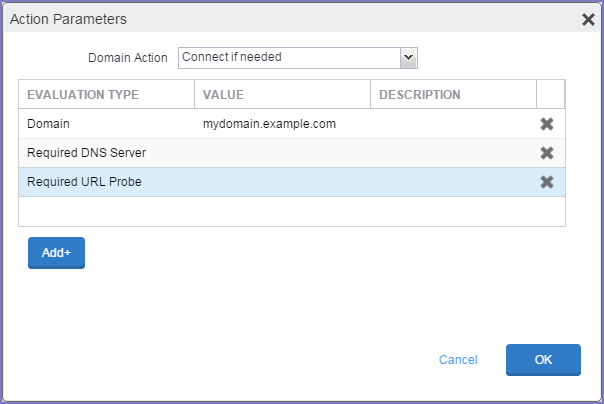
-
From the Domain Action drop-down list, select one of the following actions to be taken for the domains listed in the table:
•Connect if needed: The specified domains should trigger a VPN connection attempt if domain name resolution fails, such as when the DNS server indicates that it cannot resolve the domain, responds with a redirection to a different server, or fails to respond (timeout).
•Never connect: The specified domains should never trigger a VPN connection attempt.
-
Select Add+ to include any of the following evaluation types:
•Domain: The domains for which this evaluation applies.
•Required DNS Server: IP addresses of DNS servers to be used for resolving the specified domains. These servers need not be part of the device’s current network configuration. If these DNS servers are not reachable, a VPN connection is established in response. These DNS servers should be either internal DNS servers or trusted external DNS servers. You can only configure required DNS server evaluation types for the Connect if needed domain action.
•Required URL Probe: An HTTP or HTTPS (preferred) URL to probe, using a GET request. If no HTTP response code is received from the server, a VPN connection is established in response. You can only configure required URL probe evaluation types for the Connect if needed domain action.
- Add a value and optional description for each entry.
- Select OK to save your domain action parameters.
Domains
Safari Domains
Applicable to: Safari Domains (iOS 7 and later; macOS 10.11 and later)
You must update your VPN software to a version that supports Per-app VPN.
If the server ends with one of these domain names, a VPN connection is started automatically.
- Add+ - Click to add a domain.
- Safari Domain - Enter a domain name. Only alphanumeric characters and periods (.) are supported.
- Description - Enter a description for the domain.
Once the configuration has been saved, you can edit the Safari Domain information by clicking the Edit icon.
Calendar Domains
Deprecated in iOS 13.4 and later.
Applicable to: Calendar Domains (iOS 13 and later; macOS 10.15 and later)
If the server ends with one of these domain names, a VPN connection is started automatically.
- Add+ - Click to add a domain.
- Calendar Domain - Enter a domain name. Only alphanumeric characters and periods (.) are supported.
- Description - Enter a description for the domain.
Contact Domains
Deprecated in iOS 13.4 and later.
Applicable to: Contact Domains (iOS 13 and earlier; macOS 10.15 and later)
If the server ends with one of these domain names, a VPN connection is started automatically.
- Add+ - Click to add a domain.
- Contact Domain - Enter a domain name. Only alphanumeric characters and periods (.) are supported.
- Description - Enter a description for the domain.
Mail Domains
Deprecated in iOS 13.4 and later.
Applicable to: Mail Domains (iOS 13 and later; macOS 10.15 and later)
If the server ends with one of these domain names, a VPN connection is started automatically.
- Add+ - Click to add a domain.
- Mail Domain - Enter a domain name. Only alphanumeric characters and periods (.) are supported.
- Description - Enter a description for the domain.
Associated Domains
Applicable to: Associated Domains (iOS 14.3 and later; macOS 11.0 and later). Applicable to MDM devices only.
Connections to servers within one of these domains are associated with the per-app VPN.
- Add+ - Click to add a domain.
- Mail Domain - Enter a domain name. Only alphanumeric characters and periods (.) are supported.
- Description - Enter a description for the domain.
Excluded Domains
Applicable to: Excluded Domains (iOS 14.3 and later; macOS 11.0 and later). Applicable to MDM devices only.
Connections to servers within one of these domains are excluded from the per-app VPN.
- Add+ - Click to add a domain.
- Mail Domain - Enter a domain name. Only alphanumeric characters and periods (.) are supported.
- Description - Enter a description for the domain.
For more information, see Managed domains settings.
Custom Data
- Add+ - Select to add a new key / value pair.
- Key / Value - Enter the Key / value pairs necessary to configure the VPN setting. The app creator should provide the necessary key / value pairs.