What you configure on Core to use derived credentials
The following diagram summarizes the MobileIron Core configuration for using derived credentials, and shows whether you do the configuration on the System Manager or the Admin Portal.
The table following the diagram:
| • | Describes each configuration task. |
| • | Indicates to which derived credential providers and device platform (iOS or Android) the task applies. |
Note The Following:
| • | The task list assumes you use Apps@Work to distribute apps to iOS devices. However, using Apps@Work is not required. Various methods are available for device users to get the app on their iOS devices. Therefore, tasks related to using Apps@Work are optional. |
| • | The task list assumes that you want device users to register Mobile@Work using a registration PIN rather than with a user ID and password, since typically, device users who use smart cards do not have passwords. However, using a registration PIN is a requirement only with Entrust derived credentials. For other derived credential providers, it is not a requirement, and therefore the related tasks are optional. |
Figure 1. Derived credential configuration summary on MobileIron Core
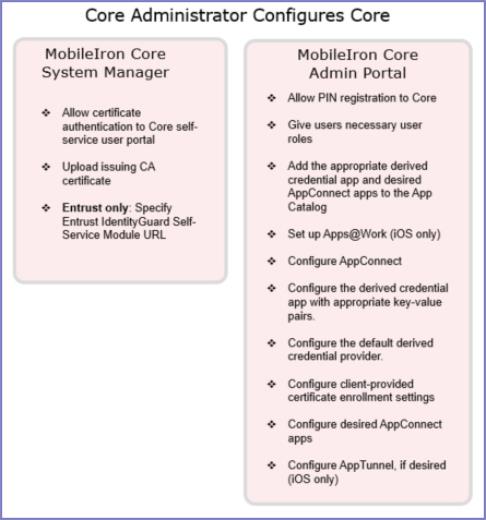
|
Task |
Notes |
||||||||||||||||||
|
Allowing certificate authentication includes uploading to Core a valid issuing (CA) certificate or a valid supporting certificate chain. Entrust This task is required for Entrust derived credentials, because it is a prerequisite for configuring Core to use the Entrust IdentityGuard Self-Service Module (SSM) URL. All other derived credentials providers Although not strictly required for other derived credential providers, device users who use smart cards typically do not have passwords. Therefore, if you want them to be able to access the self-service user portal to, for example, generate a registration PIN, this step is required. |
||||||||||||||||||
|
Entrust Core uses this URL to get derived credentials from Entrust. The device user will use the PIV-D Manager app to activate the derived credential on a device. |
||||||||||||||||||
|
Entrust This task is required for Entrust derived credentials because device users need a registration PIN to request an Entrust derived credential. All other derived credentials providers Although not strictly required for other derived credential providers, device users who use smart cards typically do not have passwords. Therefore, if you want them to be register Mobile@Work using a one-time registration PIN, this step is required. |
||||||||||||||||||
|
All derived credentials providers From the user portal, the device users can:
Additionally, when using Entrust From the user portal, device users get an Entrust derived credential, which includes getting the Entrust activation password to enter later on the device to activate the derived credential. This capability has no corresponding user portal role. |
||||||||||||||||||
|
Entrust on Android Add the PIV-D Manager app for Android to the App Catalog on Core. Entrust and DISA Purebred on iOS Add the PIV-D Manager app for iOS to the App Catalog on Core Other derived credential providers on iOS Add the appropriate third-party derived credential app to the App Catalog on Core. NOTE FOR iOS DEVICES:
|
||||||||||||||||||
|
All derived credentials providers NOTE FOR iOS DEVICES:
|
||||||||||||||||||
|
All derived credentials providers iOS only This task assumes you use Apps@Work for iOS. However, various methods are available for device users to get apps on their devices. |
||||||||||||||||||
|
All derived credentials providers Configuring AppConnect allows device users to use AppConnect apps, including the derived credential app. |
||||||||||||||||||
|
Configure the PIV-D Manager app for iOS as follows: Entrust
DISA Purebred
For both Entrust and DISA Purebred
|
||||||||||||||||||
|
Entrust on Android Configure the PIV-D Manager app for Android to:
|
||||||||||||||||||
|
On iOS, derived credential providers other than Entrust or DISA Purebred You configure a third-party derived credential app to receive app-specific settings from Core, as defined by the app vendor or developer. |
||||||||||||||||||
|
All derived credentials providers iOS only Select which derived credential provider is the default choice. If necessary, add a derived credential provider to the list. |
||||||||||||||||||
|
All derived credentials providers The activated derived credentials are stored in Mobile@Work for iOS or Secure Apps Manager for Android. You configure an AppConnect app to use derived credentials by referencing a client-provided certificate enrollment setting from the app’s AppConnect app configuration (or Web@Work setting or Docs@Work setting). You configure a client-provided certificate enrollment setting for one of these purposes, as needed: authentication, signing, encryption, or decryption.
|
||||||||||||||||||
|
All derived credentials providers This task is necessary only if your device users use Web@Work |
||||||||||||||||||
|
All derived credentials providers This task is necessary only if your device users use Docs@Work. |
||||||||||||||||||
|
All derived credentials providers This task is necessary only if your device users use Email+. |
||||||||||||||||||
|
All derived credentials providers This task is necessary only if your device users use other AppConnect apps that use derived credentials. |
||||||||||||||||||
|
All derived credentials providers iOS only This task is necessary only if you want to use:
Using AppTunnel with HTTP/S tunneling, you authenticate the user to the Standalone Sentry using a derived credential. |
||||||||||||||||||
|
All derived credentials providers iOS only This task is necessary only if you want to use:
Using per-app VPN with MobileIron Tunnel for iOS (AppTunnel with TCP tunneling), AppConnect apps can authenticate to the backend resource with a derived credential. |