Creating compromised devices policy
Creating a compromised devices policy for MTD is optional, however, Ivanti recommends having standard policies in place. You can choose from a wide array of Ivanti Neurons for MDM policy templates, that you can use or modify to create robust compliance policies. As an example, let's set up a policy to restart an iOS device if the jail-breaking policy is violated.
For reference and other information about these options, see Policy > Adding a custom policy in the Ivanti Neurons for MDM Administrator Guide.
Procedure
-
From the Ivanti Neurons for MDM Administrator console, select Policies. The Policies page displays.
-
Select +Add for policy options. The Choose Policy Type page displays.
-
Select Compromised Devices. The Compromised Devices menu displays.
-
Give the policy a useful name in the Name field. Add an optional description, if you desire.
-
From the Choose Actions section, select Monitor to configure tiered compliance actions.
Ivanti Sentry version 9.0.0 or later is required to utilize the tiered compliance actions.
-
In the first Actions field, select an option from the menu:
Figure 1. Tiered compliance action menu
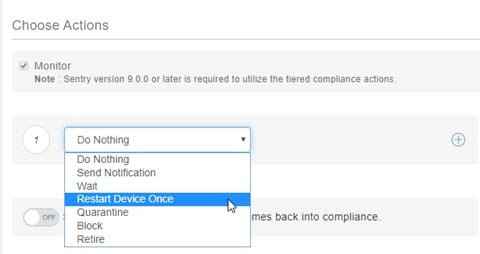
- Do Nothing (the default) – Take no action.
- Send Notification – Follow the prompts to create a warning email.
- Wait – Select the waiting time in minutes, days, or hours.
- Restart Device Once – When a device goes out of compliance, the device is restarted. This will bring some devices back into compliance.
- Quarantine – Configure default and optional quarantine actions.
- Block – Uses Ivanti Sentry to block managed devices from accessing email and AppConnect-enabled applications. Ivanti Sentry version 9.0.0 or later is required to utilize the block action.
- Retire – Retires the device. This action cannot be undone.
-
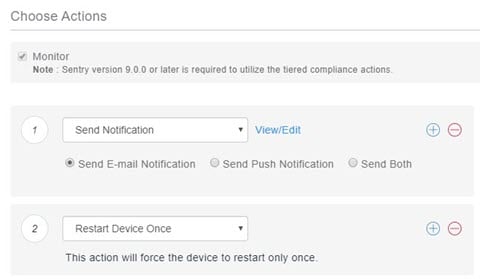
For example, you might want your first action to be an email or text message to the user. So select Send Notification, and configure your message.
-
To add more compliance levels, select the plus (+) icon to the right of the action. To delete any level, select the red minus (–).
-
For the second action, select Restart Device Once. No configuration for this option is needed.
Figure 2. Restart Device Once option to limit notifications
-
Select Yes, I understand... after you read how these policies will affect devices.
-
Select Next. The Distribute page displays.
-
Select a distribution option.
-
Select Done. The policy is pushed to devices at the next check-in.