Configuring Ivanti Neurons for MDM for SSO certificates
Simple Certificate Enrollment Protocol (SCEP) must be configured in Ivanti Neurons for MDM to generate certificates from CAs configured within Ivanti Neurons for MDM. To create the fields in user or device certificates, you must define SCEP. In order to define SCEP, it must obtain information from LDAP source.
LDAP source configuration
For the SCEP to request user certificates from CA, it must obtain the user information from the LDAP source. For example, Active Directory as an LDAP Source. You must configure two important attributes:
•User’s email address obtained from Active Directory. userPrincipalName is the LDAP attribute populated in the email field.
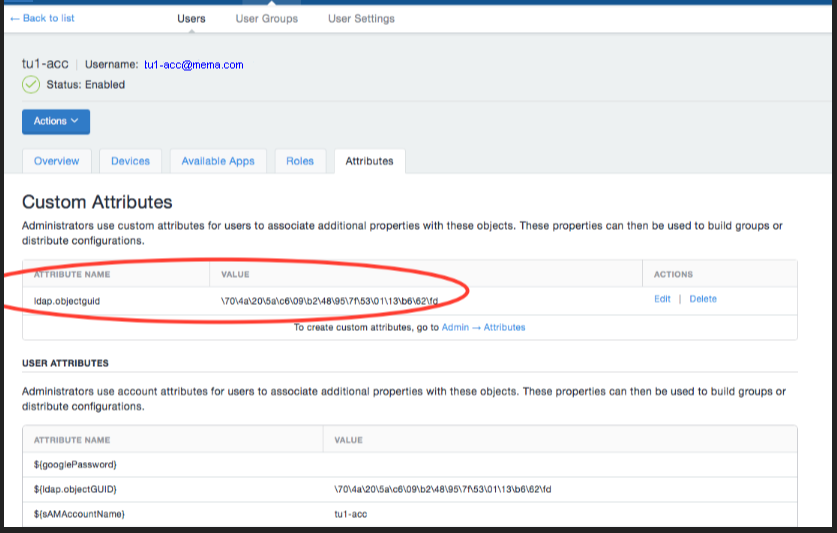
•User’s unique ID in the Active Directory. ObjectGUID is obtained and set as the attribute Custom 1.
After updating LDAP, you must sync LDAP. On the User’s tab, value of the custom attribute objectGUID is as below:
Figure 1. ldap source configuration
SCEP configuration
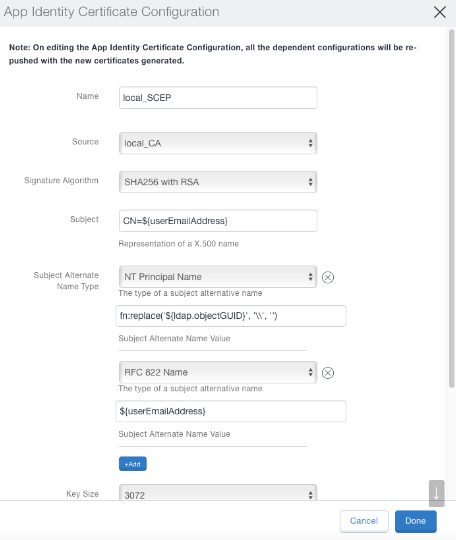
The SCEP configuration must be updated in two locations in Ivanti Neurons for MDM:
•Admin > Certificate Authority
•Configurations > Add > Identity Certificate
After the LDAP configuration, to obtain the fields for certificates, define the SCEP. Add two sub-fields in the Subject Alternative Name field of the certificate.
•The sub-field of type RFC 822 Name holds the email address. As shown in the LDAP configuration, this corresponds to the $EMAIL$ directory attribute.
•The sub-field of type NT Principal Name (required only for Office 365) holds the unique immutable Id. This configuration corresponds to the objectGUID custom attribute.
You must enter "fn:replace('${ldap.objectGUID}', '\\', '')" manually in this field value.
If you are using a local user instead of LDAP, then you can hardcore the value of RFC 822 name to EmailID of the user.
For Office 365, you can get the immutable ID by executing the following command in ADFS Windows server PowerShell.
Get-MsolUser -UserPrincipalName <username> | select ImmutableId
Convert Immutable Id value from Base64 to Hex and then add it in the SCEP profile. Both the Subject Alt Names must be present in the SCEP profile for SSO to work.
Figure 2. identity certificate configuration