About Zero Sign-on with MobileIron Access
Zero Sign-on provides secure passwordless access to enterprise cloud resources.
The following provides additional information about Zero Sign-on with MobileIron Access:
- Required components for Zero Sign-on
- Use cases for Zero Sign-on
- Considerations for Zero Sign-on
- Zero Sign-on authentication flow
Required components for Zero Sign-on
Deploying Zero Sign-on with MobileIron Access requires that the following components are set up:
-
MobileIron Access deployment with a MobileIron unified endpoint management (UEM) platform. The MobileIron UEM platforms are: MobileIron Cloud, MobileIron Core, or MobileIron Connected Cloud.
An Access deployment includes the following:
- MobileIron Tunnel configuration with Access enabled.
- MobileIron Tunnel deployed to devices.
-
iOS, Android, Windows 10, or macOS devices devices managed by MobileIron UEM.
-
MobileIron UEM client. The MobileIron UEM clients are: MobileIron Go for Cloud or Mobile@Work for Core.
See the MobileIron Access Release Notes for supported versions.
Use cases for Zero Sign-on
Zero Sign-on allows users password less access to enterprise cloud services. The following describes the use cases that are enabled when you configure Zero Sign-on:
- Password less access from managed devices: Users accessing an enterprise cloud service provider (SP) from a managed device are automatically authenticated using certificate-based single sign-on. Users do not need to enter their username and password.
- Password less access from unmanaged devices: Users accessing an enterprise cloud service provider (SP) from an unmanaged device are presented with a QR code. Scanning the QR code with their managed device authenticates the user and allows access from the unmanaged device. Users scan the QR code using the MobileIron client and the native camera on the managed device. Users do not need to enter their username and password. Users have the following additional options for subsequent log in:
Enable push notifications. A push notification is sent to the managed device on subsequent log in from the unmanaged device if the "remember me" option is selected.
When a user tries to log in from the desktop browser, a push notification is sent to all the active devices. When the user allows push notification on any one of the appropriate device, access is granted to the user. However, on all other devices, the push notifications become invalid.Alternately, users can use the MobileIron client on their managed device to generate a one-time passcode (OTP). OTP allows users to access cloud services from the unmanaged device even when the MobileIron client does not have access to the Internet.
Considerations for Zero Sign-on
Consider the UEM and client support described in the following table:
|
MobileIron UEM |
MobileIron Client |
Feature supported |
|---|---|---|
|
MobileIron Cloud |
MobileIron Go for iOS |
QR code, push notifications, OTP |
|
MobileIron Go for Android and Android enterprise |
QR code, push notifications, OTP |
|
| MobileIron Core |
Mobile@Work for iOS |
QR code, push notifications, OTP |
|
Mobile@Work for Android and Android enterprise |
QR code, push notifications, OTP |
Zero Sign-on authentication flow
The following describes the authentication flow from an unmanaged device using Zero Sign-on.
Figure 1. Zero Sign-on authentication flow
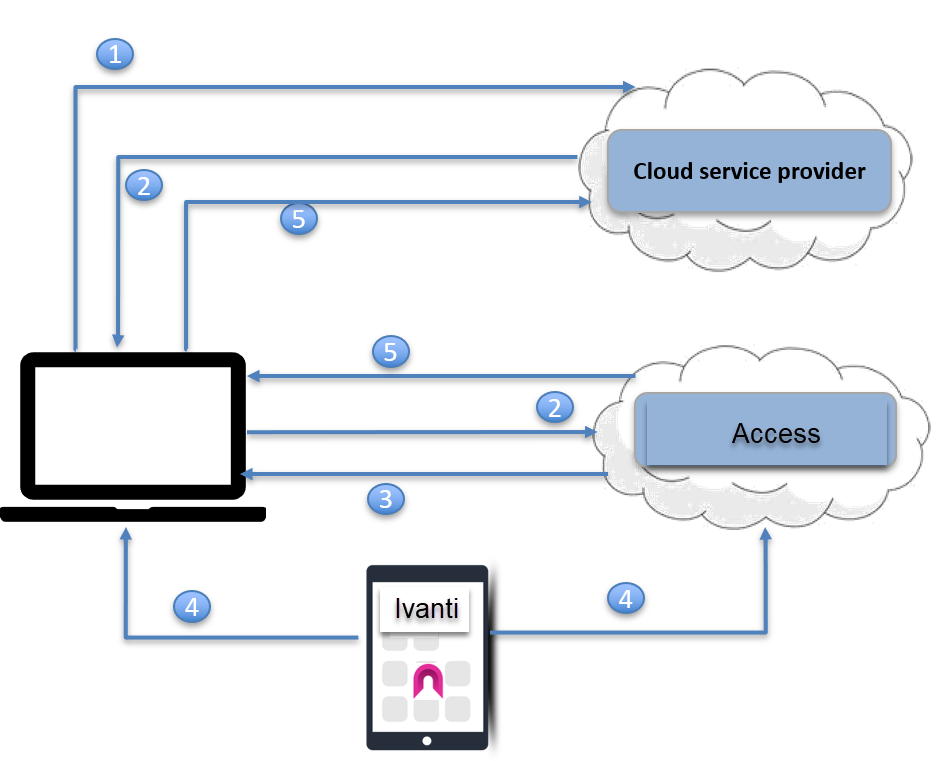
| 1. | User requests access to a cloud service from an unmanaged device, such as a desktop. |
| 2. | The cloud service redirects user to the configured identity provider (IdP)to authenticate. Since Access is the configured IdP, the request is redirected to Access. |
| 3. | Access generates and presents a QR code to the user. |
| 4. | The user scans the QR code with a MobileIron managed mobile device to approve the login. |
| 5. | Access generates a new SAML response to redirect to the original SP. The original SP obtains the user identity from the SAML response and presents the personalized screen to the user. |