|
Name
|
Required. Enter a descriptive name for this policy. This is the text that will be displayed to identify this policy throughout the Admin Portal. This name must be unique within this policy type.
Though using the same name for different policy types is allowed (e.g., Executive), consider keeping the names unique to ensure clearer log entries.
|
Default Security Policy
|
|
Status
|
Select Active to turn on this policy. Select Inactive to turn off this policy.
Use the Status feature to turn a policy on or off across all phones affected by it. The policy definition is preserved in case you want to turn it on again.
|
Active
|
|
Priority
|
Specifies the priority of this custom policy relative to the other custom policies of the same type. This priority determines which policy is applied if more than one policy is associated with a specific device. Select “Higher than” or “Lower than”, then select an existing policy from the drop-down list. For example, to give Policy A a higher priority than Policy B, you would select “Higher than” and “Policy B.”
Because this priority applies only to custom policies, this field is not enabled when you create the first custom policy of a given type.
|
|
|
Description
|
Enter an explanation of the purpose of this policy.
|
Default Security Policy
|
| Password fields
|
|
Password
|
Select Mandatory to specify that the user must enter a password before being able to access the device. Otherwise, select Optional, which allows the user to determine whether the password will be set.
If you intend to use the Lock feature in case the phone is lost or stolen, then a password must be set on the phone. Therefore, specifying a mandatory password is strongly advised.
For iOS
and macOS
devices:
Select Mandatory to specify that the device user must comply with the password policy when resetting the password for the device. This does not force a user to change an existing password.
For iOS devices: If a security policy is edited and the Password field is set to Optional, then the security policy will not be pushed to devices. This results in an inaccurate count in your WatchList on the Policies & Configurations > Policies page. Ivanti recommends you have the Password field set to Mandatory.
|
Optional
|
|
Password Type
|
Specify general restrictions for the password:
Simple: Determines whether a simple password is allowed. A simple password can contain repeated characters, or ascending/descending characters, for example 123 or CBA.
Alphanumeric: Requires passwords to include at least one letter and one number.
For iOS, tvOS
, and macOS
: If you select both Simple and Alphanumeric, then passwords can include repeating and/or ascending/descending characters. If you select Alphanumeric only, then passwords may not include repeating and/or ascending/descending characters.
Don’t Care: Applies the default requirements specified by the device OS. This option is not supported on iOS.
If no check box is selected, the Password Type defaults to Don’t Care.
For Android 12: Android 12 devices in Work Profile mode do not support password type and password length. As a result, they are reported in Ivanti EPMM as "Unsupported."
For Windows Phone 8.1 devices: The Don’t Care option requires that the password is either simple or alphanumeric.
To allow the use of a PIN, but not a simple password such as 1234 or 1111, select the Don’t allow simple password option.
For Windows 10 Mobile devices: This feature is not supported. Use Minimum Number of Complex Characters to make changes to these keyboards.
|
Don’t Care
|
|
Complex PIN (Android only)
|
For Android devices only:
Select On to prohibit the device user from using ordered or repeating digits in a PIN.
This option is enabled only if:
- the password is mandatory
- the password type is simple only
Examples of ordered digits: 1234, 2468, 9876
Example of repeating digits: 4444
This feature requires Android 6.0 and supported newer versions. Devices running earlier versions behave as if this option is set to Off.
|
Off
|
|
Minimum Password Length
|
Enter a number between 1 and 16 to specify the minimum length for the password. Leave this setting blank to specify no minimum.
Note the following:
- For Android devices: When the Don't Care option is set for the Password Type field, the Minimum Password Length field does not apply.
- For Android 12: Android 12 devices in Work Profile mode do not support password type and password length. As a result, they are reported in Ivanti EPMM as "Unsupported."
|
6
|
|
Maximum Inactivity Timeout
|
Select the maximum amount of time to allow as an inactivity timeout. To disable this feature, select Never. The user can then specify up to this value as the interval after which the screen locks.
For macOS: Enter the maximum timeout interval that the device user can set for the device before the screen saver engages.
For iOS and tvOS: The Grace Period for Device Lock option determines whether the user must enter a password to unlock the screen. Also consider the case when the maximum inactivity timeout that you specify is greater than the maximum inactivity timeout that the device supports. In this case, the inactivity timeout that the user can specify is limited by the device’s maximum inactivity timeout.
For Windows Phone 8.1 and Windows 10 Mobile devices: If the Maximum Inactivity Timeout is set to one minute, the device uses the timeout set on the device.
|
30 minutes
|
|
Minimum Number of Complex Characters
|
Specify the minimum number of special characters that must be included in a password.
For Windows Phone 8.1 devices: Specify the minimum level of complexity, 1 to 4, required in a password. The values indicate the minimum number of character types required. The character types are lowercase, uppercase, numbers, and non-alphanumeric.
For Windows 10 Mobile devices: The complexity will determine what type of password and keypad the user sees. 1 - Digits only (the default)2 - Digits and lowercase letters are required3 - Digits, lowercase letters, and uppercase letters are required4 - Digits, lowercase letters, uppercase letters, and special characters are required.
For Windows 10 Desktop devices: This feature is not supported.
|
0
|
|
Maximum Password Age
|
For Windows Phone 8.1 devices: This feature is not supported.
For Windows 10 devices: Specifies when the password expires (in days).
This policy must be wrapped in an Atomic command.
Supported values are listed below:
- An integer X where 0 <= X <= 730.
- 0 (default) - Passwords do not expire.
If all policy values = 0 then 0; otherwise, Min policy value is the most secure value.
For iOS,
macOS,
tvOS, and Android:
Specify the numbers of days after which the password will expire. 0 indicates no limit.
Ivanti Mobile@Work 10.1.0.0 for Android and higher supported releases provides the device user a notification when the password is going to expire within the next 7 days.
For more information, see "Setting an alert that a device's PIN change request was skipped" in Ivanti EPMM Device Management Guide for Android and Android Enterprise devices.
|
0
|
|
Maximum Number of Failed Attempts
|
This feature does not apply to Windows devices.
Specify the maximum number of times the user can enter an incorrect password before the device is wiped. 0 indicates no limit.
For Android and Android Enterprise devices: When set to zero, unlimited passcode failures are allowed. When set to anything greater than zero only the number of consecutive failures specified are allowed.
For iOS and tvOS: When set to a maximum number of 3 or less, the device imposes a time delay before a passcode can be entered again. The time delay increases with each failed attempt, as shown in the following table.
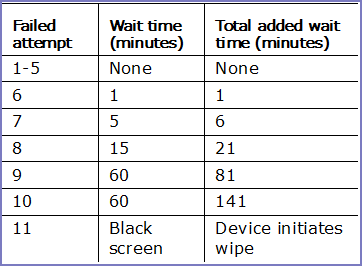
For example, if the device user has failed to enter the correct password for the 7th time, a wait time of 5 minutes is imposed, for a total wait time of 6 minutes, even when the maximum number of failed attempts has been set to 3.
When set to 4 or above, devices that can no longer be disabled by users are wiped when entering the fifth incorrect passcode. There is no wait time in this case.
When set to 3 or less, and enabling the iOS or tvOS setting to erase the device after too many failed passcode attempts (under Settings > Touch ID & Passcode > Erase Data in iOS), the device is wiped when entering the 11th failed passcode.
If there is no passcode set on the device, data protection is disabled by default. This is as per Apple design.
|
0 (no limit)
|
|
Password History
|
For Android, iOS and tvOS devices:
Specify the number of passwords remembered to ensure that users define a different password.
For example, if you want to prevent users from repeating a password for the next four password changes, enter 4.
|
0
|
|
Maximum Number of Failed Attempts
|
If this is set as 1, the user is not prompted to enter the device password.
This feature specifies the number of authentication failures allowed before the device will be wiped. A value of 0 disables device wipe functionality.
This policy must be wrapped in an Atomic command.
Prior to reaching the failed attempts limit, the user is sent to the lock screen and warned that more failed attempts will lock their computer. When the user reaches the limit, the device automatically reboots and shows the BitLocker recovery page. This page prompts the user for the BitLocker recovery key.
The following list shows the supported values:
- An integer X where 4 <= X <= 16 for desktop and 0 <= X <= 999 for mobile devices.
- 0 (default) - The device is never wiped after an incorrect PIN or password is entered.
The most secure value is 0 if all policy values = 0; otherwise, Min policy value is the most secure value.
|
|
|
Maximum Number of Failed Attempts
|
For Windows 10 Mobile devices: When a user reaches the value set by this policy, the device is wiped.
|
|
|
Maximum Number of Failed Attempts
|
For Windows 10 Desktop devices: When a user reaches the value set by this policy, it is not wiped, but put on BitLocker recovery mode, which makes the data inaccessible but recoverable. If BitLocker is not enabled, then the policy cannot be enforced.
|
|
|
Password History
|
For Windows Phone 8.1 devices: This feature is not supported.
For Windows 10 devices: This feature specifies how many passwords can be stored in the history that cannot be used.
This policy must be wrapped in an Atomic command.
Supported values are listed below:
- An integer X where 0 <= X <= 50.
- 0 (default)
The value includes the user's current password. A setting of 1 indicates users cannot reuse their current password when choosing a new password and a setting of 5 indicates users cannot set their new password to their current password or their previous four passwords.
The Max policy value is the most restricted.
|
|
|
Grace Period for Device Lock
|
For macOS only: Specify the maximum amount of time the device can be on the screen saver without prompting for a passcode on wake from the screen saver.
For iOS and tvOS only: Specify the interval after the device locks during which the user can unlock the device without entering a passcode.
|
None
|
|
Data Encryption
These features are not supported on iOS or macOS devices.
|
|
Device Encryption
|
For Android Samsung Knox:
Select On to turn on encryption. Otherwise, select Off.
If Device Encryption is turned on, then the Password option is automatically set to Mandatory.
For Windows:
Setting encryption is supported for Windows Phone 8.1 and Windows 10 Mobile devices. Setting encryption is not supported for Windows 10 Desktop devices, however, encryption can be enabled by setting it manually on the device.
Once encryption has been set, looking up encryption is supported for all Windows devices.
If Device Encryption is turned on, it cannot be turned off. You must reset the device to factory settings to turn off device encryption.
|
Off
|
|
Data Type
|
For Android devices only: Indicates the data type.
|
none selected
|
|
File Types
|
For Android devices only: Indicates the file type.
|
none specified
|
|
SD Card Encryption
|
Android Samsung Knox and LG devices only: Select On to enforce SD card encryption. Otherwise, select Off.
Supported only with Android 7.0 through the most recently released version as supported by Ivanti EPMM.
Supported on LG devices only with Ivanti Mobile@Work 9.7 for Android through the most recently released version as supported by Ivanti EPMM.
Apply to Samsung managed devices
Select to apply SD card encryption to Samsung Work Managed Devices or Managed Device with Work Profile (COPE) mode on Android devices versions 8-10.
|
Off
|
|
Device Log Encryption
|
Select On to turn on device log encryption. Otherwise, select Off.
See “Device log encryption” in the Device Management Guidefor Android Devices.
|
Off
|
|
For details on all Windows 10 Desktop options, see the Bridge chapter in the Ivanti EPMM Device Management Guide for Windows devices.
|
|
Android
(For Android only)
|
|
Require strict TLS for Apps@Work (Android only)
|
For Android devices only:
Select this check box so that Ivanti Mobile@Work will require strict TLS between Apps@Work and other services, for all devices with this Security policy applied.
The device will no longer allow you to use http:// links for override URLs in Apps@Work.
|
Not selected
|
|
Common Criteria Mode (Samsung Knox and LG only)
|
For Android 7.0 devices and supported newer versions:
This feature is not commonly used.
For customers that require this mode, select this check box to put a Samsung Knox or LG device in Common Criteria mode.
For Samsung Knox devices, selecting this option requires a Knox license and the Samsung General policy needs to be enabled.
Apply to Samsung Managed devices
This feature is not commonly used.
For customers that require this mode, select this check box to put a Samsung managed device in Common Criteria mode.
This option is supported only on Android 7.0 and supported newer versions.
|
Not selected
|
|
Block SmartLock (from Android 6.0 only)
|
For Android devices only:
Select this option to prohibit the device user from using the Smart Lock feature on the device. Selecting this option causes the Block Smart Lock Options to display. You must select at least one of the Block Smart Lock Options.
The impact of selecting this option depends on the Android version and Ivanti Mobile@Work version on the device:
- With Android 6.0 and Ivanti Mobile@Work 10.1.0.0 and supported newer versions: Your selections of the individual Block Smart Lock Optionsare applied.
- Selecting Block SmartLock blocks all types of Smart Locks, regardless of your selections of the individual Block Smart Lock Options.
This security policy setting overrides the Lockscreen Widgets setting in the lockdown policy.
|
Not selected
|
|
Block Smart Lock Options (from Android 6.0)
|
These fields appear only if you have selected Block Smart Lock (from Android 6.0 only).You must select at least one of these options.
Support for each of these options vary across device models. Selecting an option has no impact on devices that do not support the option.
|
|
|
Block Bluetooth
|
This field appears only if you have selected Block Smart Lock (from Android 6.0 only)
Select to not allow unlocking a device because it is connected to a trusted device using Bluetooth.
Some device models combine Bluetooth and NFC into trusted devices.
|
Not selected
|
|
Block NFC
|
This field appears only if you have selected Block Smart Lock (from Android 6.0 only)
Select to not allow unlocking a device because it is connected to a trusted device using NFC (near-field communication).
Some device models combine Bluetooth and NFC into trusted devices.
|
Not selected
|
|
Block Places (Location)
|
This field appears only if you have selected Block Smart Lock (from Android 6.0 only)
Select to not allow unlocking a device because of its location, also known as a "trusted place".
|
Not selected
|
|
Block Face
|
This field appears only if you have selected Block Smart Lock (from Android 6.0 only)
Select to not allow unlocking a device because it recognizes the user's face, also known as a "trusted face".
|
Not selected
|
|
Block On-body
|
This field appears only if you have selected Block Smart Lock (from Android 6.0 only)
Select to not allow unlocking a device because the user is carrying it in their hand, pocket, or bag.
|
Not selected
|
|
Block Voice
|
This field appears only if you have selected Block Smart Lock (from Android 6.0 only)Select to not allow unlocking a device because it recognizes the user's voice.
|
Not selected
|
|
Block Fingerprint (from Android 6.0 or Samsung MDM 5.3)
|
For Android devices only:
Select this option to prohibit the device user from using a fingerprint to access the device.
This feature requires the following on the device:
- Android 6.0 and supported newer versions
- On Samsung devices, Samsung MDM 5.3 through the most recently released versions supported by Ivanti EPMM.
- Fingerprint hardware
This setting has no impact on devices that do not meet the listed requirements; fingerprint is allowed, if available.
This security policy setting overrides the LockscreenWidgets setting in the lockdown policy.
|
Not selected
|
|
Block Iris Scan (Samsung and Android 9.0)
|
For Android devices only:
Select this option to prohibit the device user from using iris scanning to unlock the device. This option requires that the device is:
- A Samsung device with the iris scanning feature.
- A Samsung device running Samsung OS 7.0 through the most recently released version as supported by Ivanti EPMM.
- A non-Samsung device running Android 9.0 through the most recently released version as supported by Ivanti EPMM.
- Running Ivanti Mobile@Work 10.1 through the most recently released version as supported by Ivanti EPMM.
This setting has no impact on other devices.
This security policy setting overrides the Lockscreen Widgets setting in the lockdown policy.
|
Not selected
|
|
Block Face Unlock (Samsung and Android 9.0)
|
For Android devices only:
Select this option to prohibit the device user from using face recognition to unlock the device. This option requires that the device is:
- A Samsung device with the face unlock feature
- A Samsung device running Samsung OS 7.0 through the most recently released version as supported by Ivanti EPMM.
- A non-Samsung device running Android 9.0 through the most recently released version as supported by Ivanti EPMM.
- Running Ivanti Mobile@Work 10.1 through the most recently released version as supported by Ivanti EPMM.
This setting has no impact on other devices.
This security policy setting overrides the Lockscreen Widgets setting in the lockdown policy.
|
Not selected
|
|
Require Google SafetyNet Attestation
|
For Android devices only: Select this option to perform SafetyNet attestation on devices. See "Enabling SafetyNet attestation on Android devices" in the Ivanti EPMM Device Management Guide for Android and Android Enterprise devices.
|
Not selected
|
|
Block notifications on lock screen
|
Android Enterprise managed device profile only:
Select this option to prevent notifications from being displayed on the device lock screen. Applies to Managed Device with Work Profile (COPE) mode on Android devices versions 8-10.
|
Not selected
|
|
Allow only redacted notifications on lock screen
|
Android Enterprise work profile only: This option will redact notifications shown on the lock screen hiding the notification contents. Block notifications on lock screen does not affect this. Applies to Managed Device with Work Profile (COPE) mode on Android devices versions 8-10.
|
Not selected
|
|
Windows Phone 8.1
|
(For Windows Phone 8.1 devices only.)
|
|
Firewall
|
This is available on all Windows-supported devices.
|
On
|
|
Anti-Virus
|
This is available on all Windows-supported devices.
|
On
|
|
Auto-Update
|
This is available on all Windows-supported devices.
|
On
|
|
Windows 10
|
(For Windows 10 devices only.)
|
|
Defender Real-time Protection
|
This setting is turned on by default. Once a user turns it off it can only be turned back on by an administrator.
|
On
|
|
DHA On-premises URL
|
Device Health Attestation (DHA) is used to increase device monitoring for those systems (such as government agencies) that need the information. DHA also takes a passive approach to the data, allowing administrators to decide how they want to handle compliance.
Turning on this feature begins the collection of data, which is sent to Microsoft Cloud DHA or on-prem servers. To use an on-premises server, go to the Admin Portal >Policies & Configs > Policies > select a security policy > Edit > Windows 10 > DHA On-premises URL.
Only Microsoft Server 2016 can be used as DHAs.
Once collected and reported back to Ivanti EPMM, the information displays on individual Device Details pages on a per-device basis.
Administrators can use this information to determine if a device should be wiped or looked at for other security reasons.
|
Off
|
| Access Control
|
|
For the following options, select the compliance action you want to apply to devices that trigger access control. For detailed information on the impact that compliance actions have on devices, see “Compliance actions for security policy violations” in the Ivanti EPMM Device Management Guide for your operating system.
|
|
For All Platforms |
|
Apply compliance action when a device has not connected to Ivanti EPMM in x days
|
Select the compliance action you want to apply if a device has not connected to Ivanti EPMM in the specified number of days.
For iOS devices: All compliance actions are supported if MDM is enabled, except for those related to Android devices, When Data Encryption is disabled, and Application Restrictions. Ivanti EPMM only checks whether MDM policies are out of date.
For macOS devices: You can send an alert and quarantine the device.
For Android devices: Only the following compliance actions are supported:
- Sending alert
- Blocking email access if you are using a Standalone Sentry for email access.
-
Blocking app tunnels.
For Windows devices: Only the following compliance actions are supported:
- Sending alert
- Blocking email access if you are using a Standalone Sentry for email access.
-
Supported custom compliance actions.
|
|
|
Apply compliance action when a policy has been out of date for x days
|
Select the compliance action you want to apply if a device has not met policy requirements for the specified number of days.
For iOS devices: All compliance actions are supported.
For macOS devices: You can send an alert and quarantine the device.
For Android devices:
Supports only the following compliance actions:
- Sending alert
- Blocking email access if you are using a Standalone Sentry for email access.
-
Blocking app tunnels.
For Windows devices: Supports only the following compliance actions:
- Sending alert
- Blocking email access if you are using a Standalone Sentry for email access.
-
Supported custom compliance actions.
|
|
|
Apply compliance action when a device violates the following App Control rules
|
Select the compliance action you want to apply when a device violates the specified App Control rules. See the Ivanti EPMM Apps@Work Guide.
|
|
| iOS and tvOS devices |
|
Apply compliance action when iOS version is less than
|
Select the compliance action you want to apply when Ivanti EPMM detects an iOS device having a version number less than the specified version.
|
|
|
Apply compliance action when a compromised iOS device is detected
|
Select the compliance action you want to apply when Ivanti EPMM detects an iOS device that has been modified to circumvent manufacturer restrictions.
In Ivanti Mobile@Work, if the compliance action specifies Enforce compliance actions locally on devices, the following compliance actions, if selected, are enforced on the device without connecting to Ivanti EPMM:
- Alert the device user with a banner or notification.
- Block AppConnect apps.
- The device user becomes unauthorized to use AppConnect apps.
- Retire AppConnect apps.
- The device user becomes unauthorized to use AppConnect apps and the apps’ secure data is deleted.
All other compliance actions require the device to be connected with Ivanti EPMM.
|
|
|
Apply compliance action for the following disallowed devices
|
Select the compliance action you want to apply when Ivanti EPMM detects a specified iOS device, such as AppleTV or iPad 2.
|
|
|
Apply compliance action when device MDM is deactivated (iOS 5 or higher)
|
Select the compliance action you want to apply when Ivanti EPMM detects that the MDM profile has been removed from the device.
|
|
|
Enable Activation Lock (Supervised iOS 7 and later devices only)
|
Select to enable the activation lock feature. See the section “Managing the Activation Lock for iOS devices” in the Ivanti EPMM Device Management Guide for iOS and macOS devices.
|
|
|
Only join Wi-Fi networks installed by profiles (iOS 10.3 and later with supervised devices only)
|
Enabling this option filters the Wi-Fi network choices that devices can join to only include the Wi-Fi networks installed by profiles. Toggling the value of this option causes Ivanti EPMM to push the Wi-Fi configurations to any devices with this security policy.
|
|
| iOS devices |
|
|
|
Apply compliance action when Data Protection is disabled
|
Select the compliance action you want to apply when Ivanti EPMM detects an iOS device that has the Data Protection feature disabled.
Note: If the data protection feature is required for devices in the security policy, or if the password requirements are imposed, tvOS devices will fail to satisfy the policy because Apple does not support password requirements. To impose this requirement on your devices, create a separate policy for tvOS devices.
|
|
| macOS
|
|
Apply compliance action when macOS version is less than
|
Select a compliance action to apply when the macOS version on the device is less than the version you select from the drop-down list.
|
|
|
Apply compliance action when Full Disk Encryption (FileVault) is disabled
|
Select a compliance action to apply when full disk encryption (FileVault) is disabled on the device.
|
|
|
Apply compliance action when device MDM is deactivated
|
Select a compliance action to apply when the MDM (mobile device management) profile is deactivated on the device.
|
|
|
For Android devices only
|
|
Apply compliance action when Android version is less than x
|
Select the compliance action you want to apply when Ivanti EPMM detects an Android device having a version number less than the specified version.
|
|
|
Apply compliance action when a compromised Android device is detected
|
Select the compliance action you want to apply when Ivanti EPMM detects an Android device that has been “rooted,” that is, root access has been given to an app.
|
|
|
Apply compliance action when Data Encryption is disabled
|
Select the compliance action you want to apply when Ivanti EPMM detects an Android device that has the Data Encryption feature disabled.
The quarantine action Remove All Configurations has no impact when data encryption is disabled.
|
|
|
Apply compliance action when Samsung Knox device attestation fails
|
Select the compliance action you want to apply when Ivanti EPMM detects that a Samsung Knox device has failed an attestation check.
|
|
|
Apply compliance action when device administrator is deactivated
|
Select the compliance action you want to apply when Ivanti EPMM detects that the device administrator privilege has been removed from the Ivanti Mobile@Work app.
The quarantine action Remove All Configurations has no impact when the device administrator is deactivated.
|
|
|
Apply compliance action when USB debug is enabled
|
Select the compliance action you want to apply when Ivanti EPMM detects that USB debugging was enabled.
|
|
|
Bypass Factory Reset Protection
|
Applies to Android Enterprise devices in “work managed” mode only.
When enabled, Android’s Factory Reset Protection feature is bypassed, and factory reset devices will be unlocked.
When disabled, Android’s Factory Reset Protection is active. A factory reset device will be locked and will require the owner’s Google Account credentials before the device can be set up again.
No administrative code exists to unlock a factory reset device if bypass is disabled.
|
enabled
|
| For Windows devices only
|
|
Apply compliance action when Windows version is less than x
|
Select the compliance action you want to apply when Ivanti EPMM detects an Windows device having a version number less than the specified version.
|
|
|
Don’t allow simple password
|
Check this box to allow the use of a PIN, but not a simple password such as 1234 or 1111.
|
|
|
Apply compliance action when Data Encryption is disabled
|
Select the compliance action you want to apply when Ivanti EPMM detects a Windows Phone 8.1 device that has the Data Encryption feature disabled.
|
|
|
Application Restrictions
|
For Windows devices, select the check box, then select the restriction from the drop-down list.
|
|
