Using Local Actions
The administrator can configure mitigation actions and compliance rules for managed Ivanti devices using the Ivanti Mobile Threat Defense Local Actions threat defense policy. The actions are applied locally on the device. Local action policies can be applied in parallel with server-initiated policies for best practice coverage.
Mitigation and compliance using Ivanti Mobile Threat Defense Local Actions configuration includes the following sections:
Managing mitigation using the MTD Management Console and Local Action
Detected threats can be mitigated through a combination of local- and server-initiated mitigation and compliance actions. Applied together, they provide the highest level of client threat protection.
The process works this way:
Local mitigation is implemented using Local Actions, the threat is mitigated based on the Local Actions configuration and requires a connection to Ivanti MDM and MTD Management Console.
Server mitigation is implemented using compliance policies based on the device threat level custom attribute. The MTD Management Console instructs Ivanti MDM on the severity of the threat level on the device. The MDM administrator can configure various compliance policies and set mitigation actions based on the device threat level. See Creating MTD compliance policies.
When the threat is remediated on the device, and the device is connected to the Ivanti MDM or MTD Management Console, the client passes this state change to the MTD Management Console. The MTD Management Console tells Ivanti MDM that the that the threat level on the device has changed by changing the device threat level custom attribute. This then removes the policy violation for the device. Ivanti MDM then restores the device back to normal operations.
Configuring MTD Local Actions for Ivanti EPMM
Using the Ivanti Mobile Threat Defense Local Actions policy, you can set specific local actions to be taken on supported iOS and Android devices when the MTD-enabled client detects a threat. Local actions will only be taken on devices that are licensed and activated for MTD.
Procedure
- Log in to Ivanti EPMM
- Go to Policies & Configs -> Policies.
- Click Add New.
-
Select MTD Local Actions.
- In the Add MTD Local Actions policy page, enter a Name for the policy.
-
Select the MTD provider Lookout.
- Enter an optional Description.
-
In the Policy Setup section, scroll to the category containing the threat you want to enable.
- Network Threats
- Device Threats
- App Threats
The number of threats are indicated for each threat category.
-
To select and configure a network, device, or app threat from the MTD Local Actions page, follow these general steps:
-
Select ^ to expand the threat category, displaying all of the threats contained within that category. This selection controls which notifications are enabled on the device and which migration actions are taken locally on the device when a threat is detected.
-
For Local Actions iOS, select Block AppConnect Apps.
-
For Local Actions Android, select any one of the following:
- Wipe the device
- Quarantine: Remove All Configurations
- Quarantine: Do not remove Wi-Fi settings for Wi-Fi-only devices
- Quarantine: Do not remove Wi-Fi settings for all devices
- Quarantine: Remove managed apps, and block new downloads
- Disable Bluetooth
- Disconnect from Wi-Fi
-
For Notifications, select Yes and No to enable or disable notifications, respectively.
-
To choose multiple threat actions, select the check box to the left of the threat. Select the Actions pull-down menu to select multiple actions for the threat.
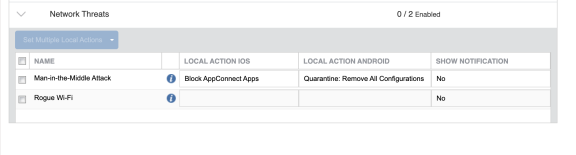
For example, expanding the Network Threats section displays three columns: Local Actions IOS, Local Actions Android, or Show Notification columns. These are used to select an action that applies when a threat is detected on a device. The example below displays Network Threats as expanded, in the Man-in-the-Middle Attack row, the Local Actions iOS is set to Block Connected Apps and the Local Actions Android section is set to Quarantine: Remove All Configurations.
- Select Save.
-
Select the MTD Local Actions policy
-
Select Actions->Apply to label to apply the policy to the desired groups of devices
Editing an MTD local actions configuration
The threat detection list is updated when new threats are identified by the MTD provider or existing threats are removed. Changes to the threat definitions list result in generating a notification to the administrator with the change details. If needed, the administrator can use this information to edit the existing local action configurations.
-
Go to Policies & Configurations > Policies and select the policy that you want to edit.
- Select Edit. The Edit Ivanti Mobile Threat Defense Solution for MDM Local Actions Configuration page is displayed.
- Make the appropriate changes and then select Done.
Local Actions against network, device, and app threats
The following network, device, and app threats and compliance actions are available on MTD-enabled client devices.
Local Actions Device threats
The following Device threats are available in Ivanti Mobile@Work Local Actions:
| Device Threats | Description |
Platform |
| Access Control Violation | The device access control has been altered, due to a possible device compromise. Changes to the access control system can result in the device being rooted and allow attackers to access sensitive data. |
Android |
|
Developer Mode |
A device that has developer mode enabled has an increased attack surface that may make the device more vulnerable to malicious actors. |
Android |
|
No Passcode |
A device with no passcode enabled is highly vulnerable to malicious actors. It’s imperative for end users to set up a passcode to protect sensitive corporate data. |
iOS Android |
|
Out of Date Security Patch Level |
An Android device that is running an outdated security patch may contain security vulnerabilities that may result in corporate data compromise. |
Android |
|
Out of Date Operating System |
A device that is running an outdated OS version may contain security vulnerabilities that may result in corporate data compromise. |
iOS |
| Rooted / Jailbroken Device |
The device has been rooted or jailbroken by the device user. Users that root or jailbreak their devices typically do so to access restricted content or device functionality. |
iOS Android |
|
Unencrypted Device |
A device that does not have storage encryption enabled is at increased risk of personal and corporate data compromise. |
iOS Android |
|
|
An Android device that’s able to install applications from unknown third-party sources is at increased risk of exposure to malicious applications. |
Android |
|
|
An Android device with USB Debugging enabled provides an attacker with physical access to the device a much greater attack surface and more opportunity to compromise corporate data. |
Android |
|
|
This app was installed on the device by an unreputable source. The app may have circumvented the vetting and approval process and may be harmful. Alternatively, the app may be under development and could be a test build. |
Android |
|
|
There is a trusted signing identity on the device that may be used to install and execute 3rd party apps not from the iOS App Store. |
iOS |
Local Actions App threats
The following App threats are available in Ivanti Mobile@Work Local Actions:
|
Threat |
Description |
Platform |
|
|
Adware contains code from an advertising network to collect personal information or engage in intrusive presentations of advertising without providing proper notification. This functionality can include adding shortcuts to the desktop or displaying ads in the notification tray. |
iOS |
|
|
App droppers download applications to devices without user consent. They may suggest that the user install the downloaded application and the downloaded application itself may be malicious. |
iOS Android |
|
|
Backdoors leave a file or program on a device that will allow other programs to access protected areas of the device’s operating system. |
iOS Android |
|
|
Bots place significant device functionality under the remote control of a third party. This functionality may include accessing the network, sending SMS, making phone calls, or downloading applications. |
iOS |
|
|
Chargeware will charge a device’s wireless bill for services without providing adequate information about the charges or giving users an opportunity to accept the charges. |
iOS Android |
|
|
Click fraud applications use devices to defraud pay-per-click or pay-per-download advertising, which may result in data overage charges on a device’s wireless bill. |
iOS Android |
|
Data Leak |
Data leaking applications send information about users and/or their devices to a third party without user knowledge or consent. Forwarded information may include contacts, calls, SMS messages, current or previous location data, and browsing history. The information may or may not be used for malicious purposes. |
iOS Android |
|
|
Denylisted apps are applications that your IT department has deemed inappropriate or unsafe for use on your device. |
iOS Android |
|
|
An application designed to take advantage of a flaw in a operating system, typically for malicious purposes such as installing malware. |
iOS Android |
|
|
Riskware includes code, libraries, or network services that pose a risk to devices due to known vulnerabilities in the code or the low reputation of service providers used by the code. This type of application is not known to be malicious, but may subject devices to more risk than a typical application. |
iOS Android |
|
|
Root enablers give users access to privileged functionality on their devices and are commonly used in phone modification communities to enable full access and control over the device. |
iOS Android |
|
Spam Application |
Spam applications send SMS or make calls from devices to enable spam campaigns, which may result in fraudulent charges on a device’s wireless bill. |
iOS Android |
|
Spyware |
Spyware applications harvest information from many devices. They hide on devices and forward information about device activities to a third party. Information forwarded may include contacts, calls, SMS messages, current or previous locations, and browsing history. Users may install this software themselves, so they may not want to remove it. |
iOS Android |
|
|
Surveillance applications are generally commercial software designed to monitor a specific, targeted device. They hide on devices and record or forward information about user activities to the installer of the software. Forwarded information may include contacts, call history, SMS messages, current or previous locations, and browsing history. |
iOS Android |
|
|
Toll fraud applications send premium SMS or make calls to premium rate numbers that charge a device’s wireless bill, often with little or no indication to the device user. |
iOS Android |
|
|
Trojans perform actions other than those advertised in order to perform malicious actions such as fraudulently charging a device’s wireless bill or stealing information from devices. |
iOS |
|
|
A malicious application that installs itself on your device and can damage it or the uses the contents on the device for malicious purpose. |
iOS Android |
|
|
A device may become unstable or exploited when using this application. |
IOS Android |
|
|
Worms exploit a software flaw to remotely attack devices. They will attempt to replicate themselves from device to device, and may also steal information from devices and cause unpredictable behavior. |
IOS Android |
Local Actions Network threats
The following Network threats are available in Ivanti Mobile@Work Local Actions:
|
Threat |
Description |
Platform |
|
|
A Man-in-the-Middle Attack occurs when a malicious actor inserts itself between the mobile device and the network or service that the user is trying to access. This makes it possible to intercept and modify data communications that the user believes to be private. |
iOS Android |
|
Rogue Wi-Fi |
A rogue Wi-Fi risk detected implies that there is a malicious actor that has connected a wireless access point (such as WiFi Pineapple) and is imitating a legitimate wireless access point. This makes it possible to intercept and modify data communications that the user believes to be private. |
iOS |
Available mitigation actions by device type
Regardless of the threat type, each iOS, Android, or Samsung Knox Android device offers a different limited set of available compliance behaviors. The following tables describe these available compliance behaviors.
| Local Compliance Action | Definition |
|
None |
No action will be taken on the device. |
|
Block Email Access and AppConnect Apps |
|
| Local Compliance Action | Definition |
|
None |
No action will be taken on the device. |
|
Wipe the device |
Retires the device. |
|
Quarantine - Remove all configurations |
Removes configurations that provide access to corporate resources, such as certificates. Configurations that secure the device are not removed. |
|
Quarantine - Do not remove Wi-Fi settings for Wi-Fi only devices |
Removes configurations that provide access to corporate resources, such as certificates, with the exception of the Wi-Fi settings on Wi-Fi only devices. Configurations that secure the device are not removed. |
|
Quarantine - Do not remove Wi-Fi settings for all devices |
Removes configurations that provide access to corporate resources, such as certificates, with the exception of Wi-Fi settings on all devices. Configurations that secure the device are not removed. |
|
Quarantine - Remove managed apps and block new downloads |
Removes access to the company App Catalog and/or work apps. |
|
Disable Bluetooth |
Disables Bluetooth to the company App Catalog and/or work apps. |
|
Disconnect from Wi-Fi |
Disables Wi-Fi to the company App Catalog and/or work apps. |
MTD Local Action should not be configured for server-detected threats, since the device needs to communicate with the Ivanti MTD server in order to remediate the threat.