Security Hardening
Security Enhanced (SELinux, CSP) Support
This feature constraints access to the ICS Linux system (ICS Linux applications) with the minimal set of resources they need.
1.In the serial console, enter 13 to select Security Operations (SElinux, CSP)
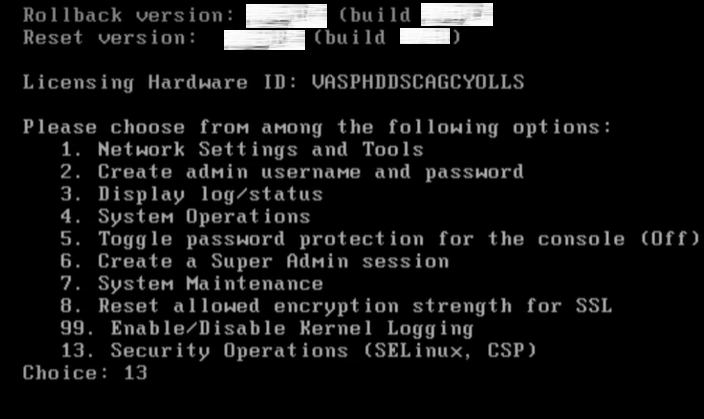
2.Choose the SELinux mode: This feature is enabled by default with system running in enforcing mode. To change the mode enter 1 and choose the following options:
•Permissive: Does not deny any operations but only logs Access Vector Cache (AVC) messages.
• Enforcing: Denies operations based on SELinux policy rules and logs Access Vector Cache (AVC) messages.
SE Linux cannot be disabled.
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross-Site Scripting (XSS) and data injection attacks. These attacks are used for everything from data theft, to site defacement, to malware distribution.
It is strictly recommended to remove any existing CSP header prior to upgrade, from UI System > Configuration > Security > Advanced configuration.
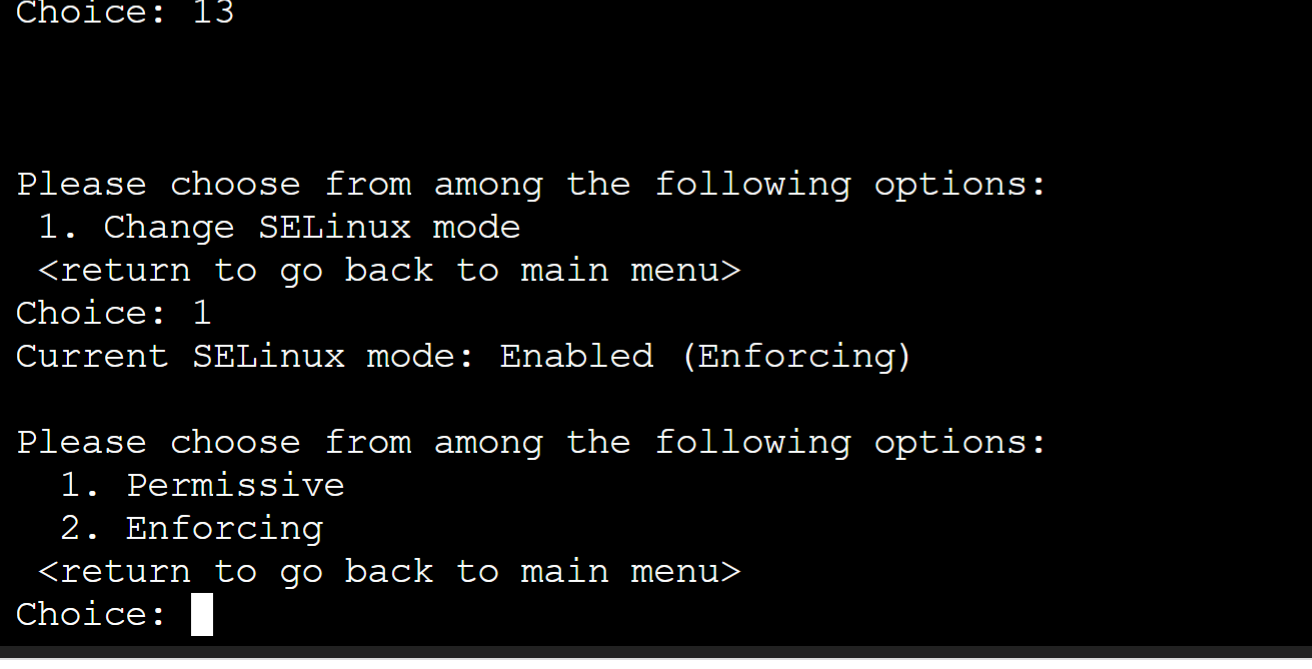
3.Enter 2 to enable/disable Content Security Policy (CSP).
CSP is enabled by default beginning from Release 22.7R2 onwards.
•Disable CSP: Enter 0 to disable CSP.
•Enable CSP: Enter 1 to enable CSP.
CSP Header Sample:
Content-Security-Policy: script-src 'nonce-xxxxxxxxxxxxxxxx' 'strict-dynamic'; object-src 'none'; base-uri 'none';
Radius Configuration
This features change the Queue mechanism of Radius auth server request from LIFO to FIFO.
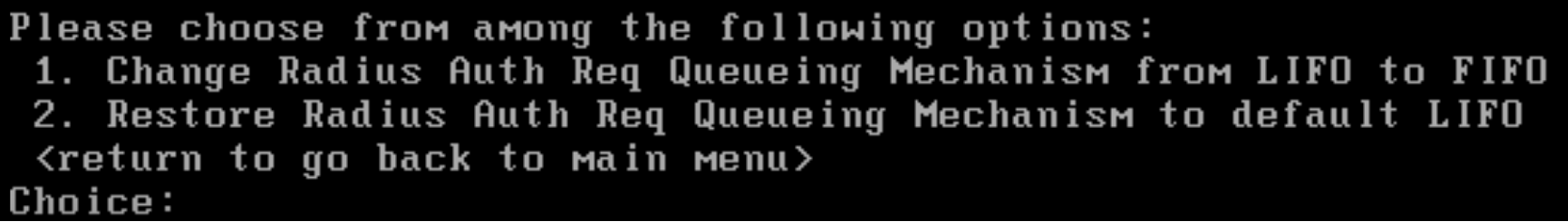
1.In the serial console, enter 14 to select Radius Configurations.

•Enter 1 to change the Radius auth request queue mechanism from LIFO to FIFO.
•To restore back to LIFO enter 2.
Audit Logs
A snapshot of the system state captures details that can help Support Center diagnose system performance problems. The system stores up to ten snapshots, which are packaged into an encrypted "dump" file that you can download and then e-mail to Global Support Center.
To enable Audit Logs:
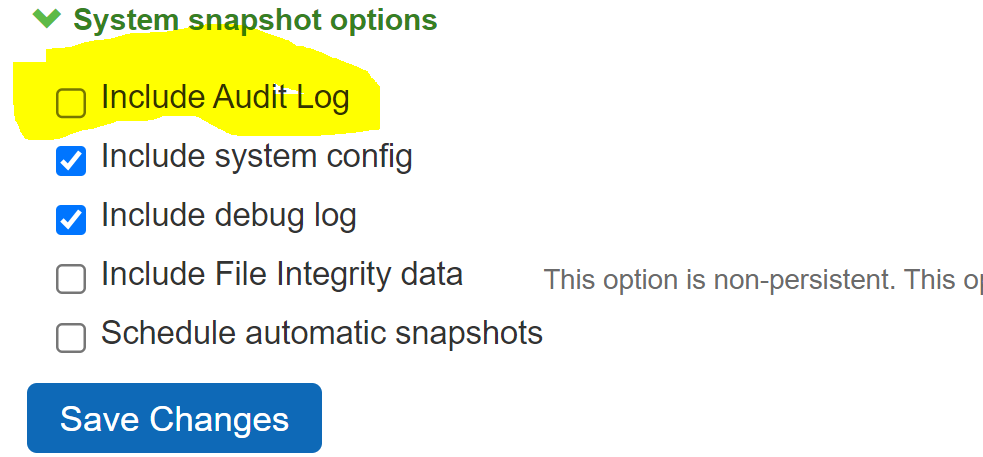
1.Select Maintenance > Troubleshooting > System Snapshot to display the configuration page.
2.Click the checkbox Include Audit Log under System snapshot options.
Enable SELinux Audit Logs
SELinux audit logs can be very useful for finding out security attacks via SELinux denials and also for debugging purpose.
Sample SELinux denial message
type=AVC msg=audit(1223024155.684:49): avc: denied { getattr } for pid=2000 comm="httpd" path="/var/www/html/file1" dev=dm-0 ino=399185 scontext=unconfined_u:system_r:httpd_t:s0 tcontext=system_u:object_r:samba_share_t:s0 tclass=file
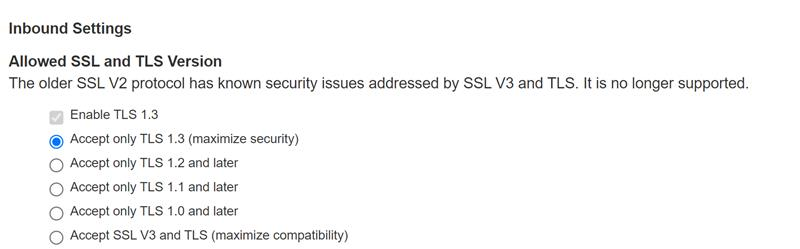
TLS 1.3 Support
To enable TLS 1.3:
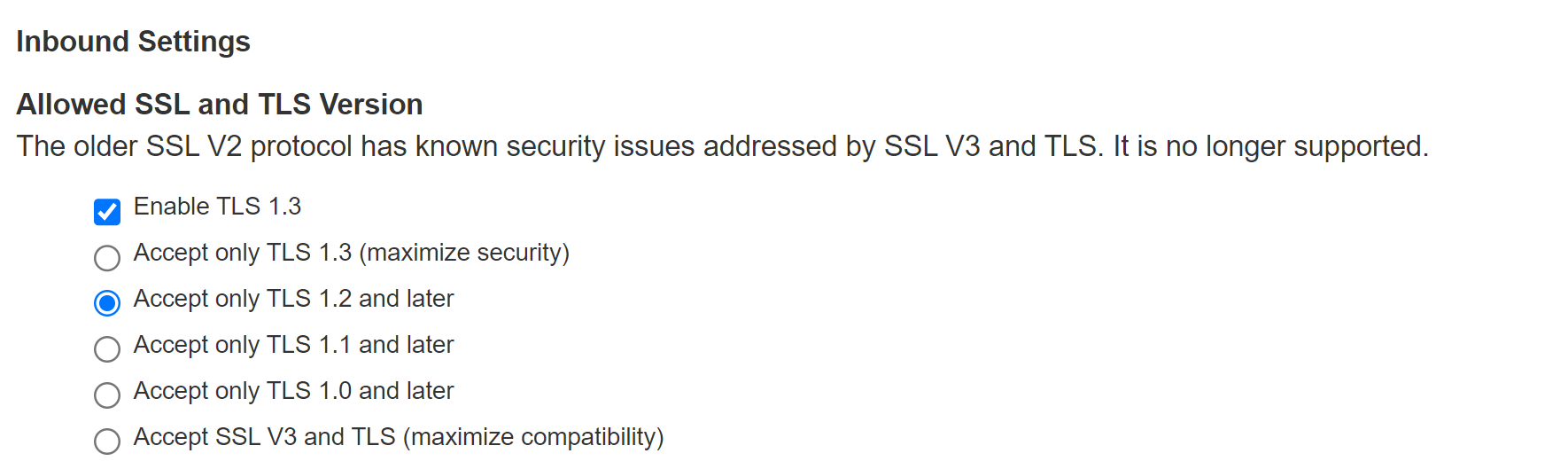
1.Select the checkbox Enable TLS 1.3, under Inbound Settings Allowed SSL and TLS Version
TLS for certAuth would be TLS 1.2 even if TLS 1.3 is selected by admin. Note that connection between server and client still would be TLS 1.3. TLS 1.2 is only used for inner TLS (To send as payload in TLS 1.3 packets).
2.While enforcing TLS 1.3 the following Confirm Cipher Change message is displayed.
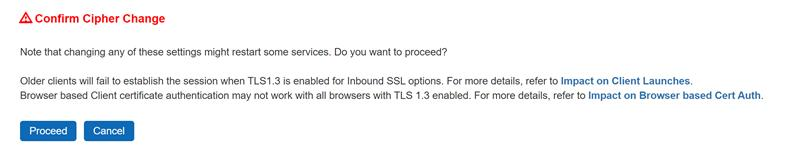
Client certificate authentication may not work on all browsers with TLS 1.3 enabled. For more details, refer to these articles Impact on Client Launchers and Impact on Browser Based Cert Auth.
3.On selecting Accept only TLS 1.3 option, only TLS1.3 version and its related ciphers are enabled while other versions and their related cipher suites are rejected.
Release 22.4R2 and later does not support weak ciphers and the following list of ciphers are removed:
•TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256
•TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256
•TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256
•TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256
•TLS_ECDH_RSA_WITH_AES_128_CBC_SHA
•TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA
•TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384
•TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384
•TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384
•TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384
•TLS_ECDH_RSA_WITH_AES_256_CBC_SHA
•TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA
•TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA
•TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA
•TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA
•SSL_RSA_WITH_3DES_EDE_CBC_SHA
•TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA
•SSL_RSA_WITH_RC4_128_MD5
•SSL_RSA_WITH_RC4_128_SHA
•TLS_ECDH_ECDSA_WITH_RC4_128_SHA
•TLS_ECDHE_ECDSA_WITH_RC4_128_SHA
•TLS_ECDH_RSA_WITH_RC4_128_SHA
•TLS_ECDHE_RSA_WITH_RC4_128_SHA