Introduction
The Secure Boot feature offers protection against unauthorized bootloader and kernel images, malware, and rootkits, and ensures compliance with secure-by-design principle while improving boot time security validation. This feature is supported on ISA6000/ISA8000 Hardware Appliances and VMware for ICS release 22.8R2. For deploying on VMware, refer to Connect Secure VMware and Hyper-V Deployment Guide.
The upgrade process for hardware appliances involves uploading the 22.8R2 package, importing logs and configurations, converting MBR to GPT partitions, and transitioning from Legacy BIOS to UEFI.
|
Note |
|
Abbreviations Used in This Guide
|
Term |
Description |
|---|---|
|
BIOS and UEFI |
Basic input / output system (BIOS) is a program fixed and embedded on a device's microprocessor that helps to initialize hardware operations. Unified Extensible Firmware Interface (UEFI) offers users a faster and sleeker experience. It supports secure booting of the bootloader. BIOS uses 16-bit mode and has a limited user interface, UEFI uses 32-bit or 64-bit mode and offers a more advanced graphical user interface. |
|
MBR and GPT |
Master Boot Record (MBR) is the information in the first sector of a hard disk or a removable drive. GUID Partition Table (GPT) is introduced as part of the Unified Extensible Firmware Interface (UEFI) initiative.
GPT provides a more flexible mechanism for partitioning disks than the older Master Boot Record (MBR) partitioning scheme. |
|
GRUB and GRUB2 |
GRand Unified Bootloader (GRUB or GNU GRUB) is a Multiboot boot loader for Linux and other Unix-based OSes. GRUB2 bootloader is the bootloader on x86 systems that is used to load the linux kernel or any other OS. GRUB2 is allowed to load by UEFI if its signature matches the signature in the UEFI’s whitelist DB. |
|
ICS |
Ivanti Connect Secure (ICS) provides a seamless, cost-effective SSL VPN solution for remote and mobile users from any web-enabled device to corporate resources. |
| ISA | Ivanti Secure Access hardware appliance. |
Benefits of Secure Boot Feature
•Protection from unauthorized bootloader images - Secure Boot prevents booting unauthorized bootloader (GRUB) images via signature verification of the bootloader (GRUB) from UEFI.
•Protection from unauthorized kernel images - Secure Boot prevents booting unauthorized kernel images via signature verification of the kernel from GRUB bootloader.
•Protection against malware and rootkits - Secure Boot prevents loading malware/rootkits via chain of trust from UEFI to GRUB to Kernel using signatures verification.
•Compliance with Security By Design principle for boot protection.
Migrating from Non-Secure Boot to Secure Boot
To upgrade from non-Secure Boot 22.x release to Secure Boot release 22.8R2:
1.Log into the Admin portal.
2.Upload the 22.8R2 package using standard upgrade process. For details, see ICS Administration Guide.
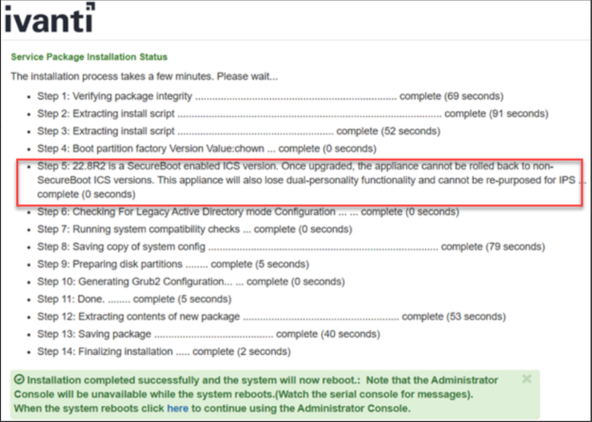
The system performs the following actions, which requires multiple reboots as part of the upgrade.
•All the logs, configs are imported from previous non-Secure Boot to Secure Boot supported 22.8R2 release builds.
•Converts MBR to GPT partitions.
•Legacy BIOS is converted to UEFI
•For ISA6000, 2-stage UEFI upgrade process. Admin can expect at least two additional reboots in this case.
•For ISA8000, single-stage UEFI upgrade process. Admin can expect one additional reboot in this case.
•Factory Reset partition will be upgraded from previous 22.x release build to the Secure Boot 22.8R2 release build.
After the upgrade to the Secure Boot build (detailed above) is complete, the images on an ICS would look like the following:

If you decide NOT to upgrade to the first Secure Boot release, i.e. 22.8R2, but wait till the next available release, then you need to upgrade in the following order:
- First upgrade to 22.8R2 Secure Boot release as described above.
- Next upgrade to the newer version.
Deploying Virtual ICS from OVF
ICS 22.8R2 needs vTPM to be enabled at the ESXi infrastructure. To enable vTPM, you need VMware vSphere and a key provider, such as Native Key Provider. vTPM and Native Key Provider are licensed for use in all vSphere versions. Supported ESXi versions are 7.0.x and 8.0.x.
vTPM is a VMware component, and for the latest documentation please refer to VMware product documentation.
To deploy Virtual ICS (vICS) from OVF:
1.Select Compute > vApps > New, and then select the Add vAPP From OVF option.
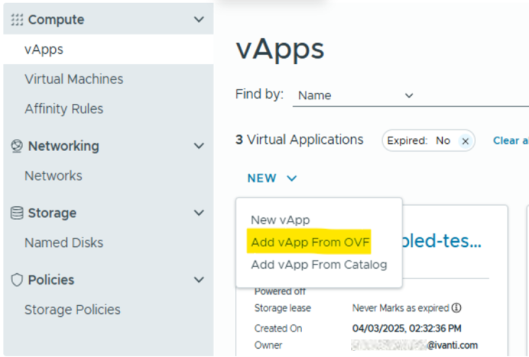
2.Select all three files required for deployment of vICS:
•OVF file - example: ISA-V-VMWARE-ICS-22.8R2-10034.1-VT-ISA8000-V.ovf
•NVRAM file - example: ISA-V-VMWARE-ICS-22.8R2-10034.1-VT-file1.nvram
•VMDK file - example: ISA-V-VMWARE-ICS-22.8R2-10034.1-VT-disk1.vmdk
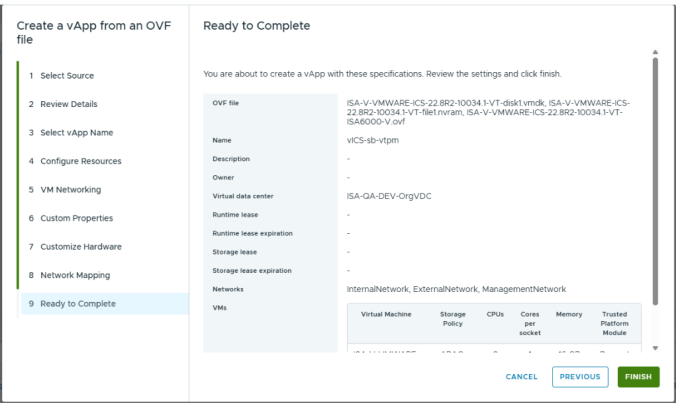
3.Follow the wizard and configure the necessary details as per your requirement. Click Finish.
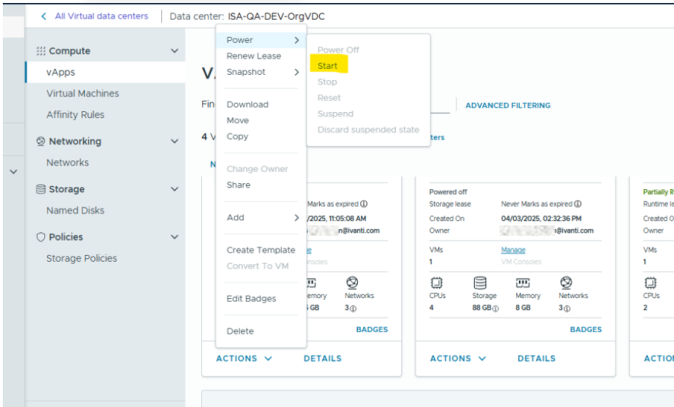
4.Click Start to power on vICS.
vTPM on ESXi 8.0.x
No additional steps are required to add vTPM when the ESXi itself is enabled with vTPM support.
Prerequisites
•vCenter license
•ESXi license
•Key Management Server on vCenter
•vTPM requirements as specified by Broadcom https://techdocs.broadcom.com/us/en/vmware-cis/aria/aria-automation/all/vtpm-overview.html
vTPM on ESXi 7.x
If ESXi 7.2 is used as hypervisor, then vTPM does not get attached automatically on deploying virtual ICS. Attach vTPM by selecting Settings > ADD NEW DEVICE > Trusted Platform Module.
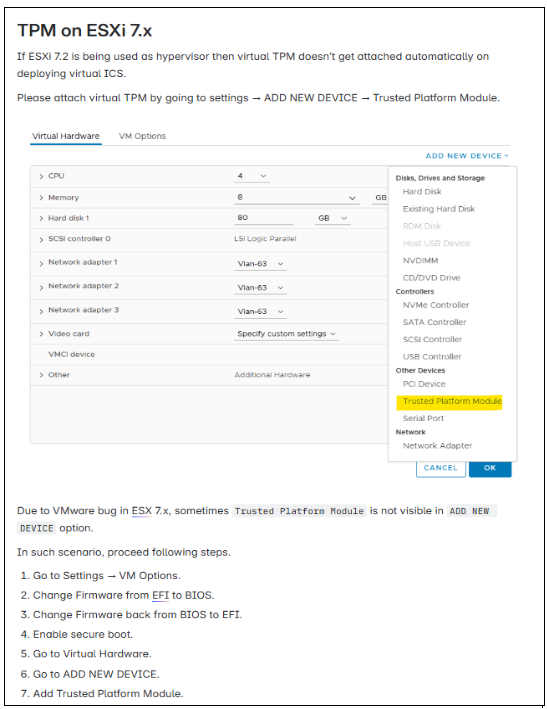
Limitations
•Upgrade from older 22.7R2.x release to rel-22.8R2 release is not supported for virtual ICS on VMware platform.
•Removing vTPM from virtual ICS can make virtual ICS non recoverable.
•Cloning virtual ICS with replace TPM option is not supported.
•Exporting virtual ICS with vTPM to template is not supported by VMware.
Security Best Practices
•Ensure BIOS/UEFI is enabled with Administrative password for every ISA Hardware Appliance. This ensures only authorized Admins can enter BIOS/UEFI settings.
•Ensure Toggle password protection for the console is ON for every appliance console access to prevent unauthorized access to Admin console.
•Ensure Secure Boot/vTPM features are always in Enabled state for BIOS/UEFI and VM settings.