Custom Ivanti Connect Secure Deployment on AWS Portal
Prerequisites and System Requirements on AWS
To deploy the Ivanti Connect Secure Virtual Appliance on AWS, you need the following:
•An AWS account
•Access to the AWS portal (https://console.aws.amazon.com/)*
•Ivanti Connect Secure Virtual Appliance AMI ID
•AWS CloudFormation template
•Ivanti Connect Secure licenses **
•Site-to-Site VPN between AWS and the corporate network (optional)
Note: This is needed only if the Ivanti Connect Secure users need to access corporate resources.
•Ivanti License Server (optional)**
•Located at corporate network, accessible through site-to-site VPN
•Ivanti Connect Secure configuration in XML format (optional)
Ivanti Connect Secure Virtual Appliance can be deployed only through AWS CloudFormation style.
Deploying Ivanti Connect Secure on Amazon Web Services
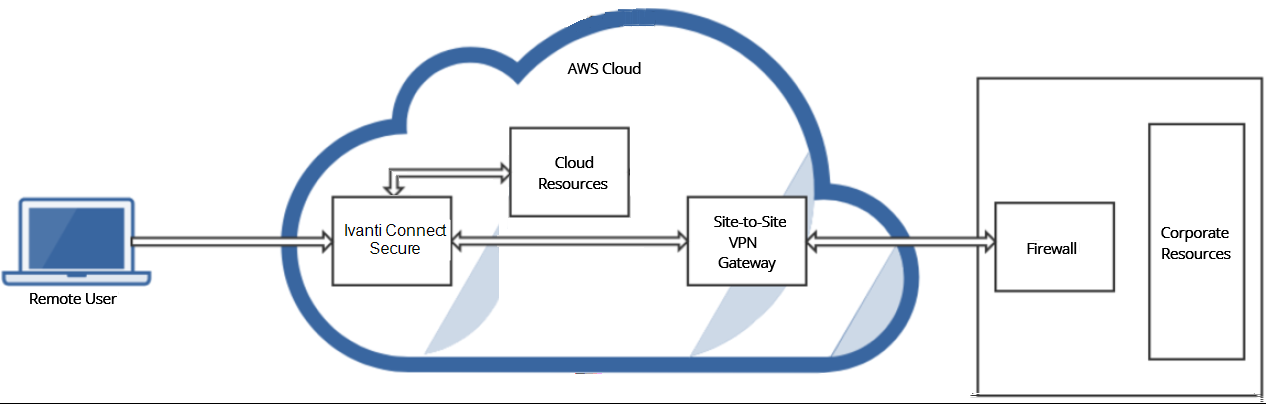
As depicted in the below diagram, a remote user can use Ivanti Connect Secure to securely access cloud resources as well as corporate resources. To access corporate resources, the Ivanti Connect Secure administrator needs to ensure that site-to-site VPN is already established between AWS and the corporate network.
Supported Platform Systems
This section helps you in choosing the instance types that should be deployed with Ivanti Connect Secure for AWS.
•ISA4000-V
•ISA6000-V
•ISA8000-V
|
Model |
vCPU |
RAM |
Disk Space in 22.6R2 and Later |
Disk Space prior to 22.6R2 |
|---|---|---|---|---|
|
ISA4000-V (M5.xlarge - 3 NICs) |
4 |
16 GB |
80 GB |
40 GB |
|
ISA6000-V ( M5.2xlarge - 3 NICs) |
8 |
32 GB |
80 GB |
40 GB |
|
ISA8000-V (M5.4xlarge - 3 NICs) |
16 |
64 GB |
80 GB |
40 GB |
|
ISA4000-V (t3.xlarge - 3 NICs) |
4 |
16 GB |
80 GB |
40 GB |
|
ISA6000-V (t3.2xlarge - 3 NICs) |
8 |
32 GB |
80 GB |
40 GB |
Customs Templates
To deploy 2-NIC or 3-NIC in an existing VPC respectively using the links below:
{
"AWSTemplateFormatVersion" : "2010-09-09",
"Description" : "Deploy ICS with 2 nic into an existing VPC",
"Metadata" : {
"AWS::CloudFormation::Interface" : {
"ParameterGroups" : [
{
"Label" : { "default" : "Existing VPC details" },
"Parameters" : [ "VpcId", "SubnetIntId", "SubnetExtId"]
},
{
"Label" : { "default":"ICS Configuration" },
"Parameters" : [
"InstanceType",
"AdminUsername",
"AdminPassword",
"ICSConfigData",
"ICSImageAMIId",
"KeyName" ]
}
],
"ParameterLabels" : {
"VpcId" : { "default" : "Existing VPC ID" },
"SubnetIntId" : {"default" : "Internal Subnet ID"},
"SubnetExtId" : {"default" : "External Subnet ID"},
"ICSImageAMIId" : {"default" : "ICS AMI ID"},
"InstanceType" : {"default" : "Instance Type"},
"KeyName" : {"default" : "SSH Key Name"},
"AdminUsername": {"default": "Admin User Name"},
"AdminPassword": {"default": "Admin Password"},
"ICSConfigData": {"default": "Config Data"}
}
}
},
"Parameters" : {
"KeyName": {
"Type": "AWS::EC2::KeyPair::KeyName",
"Default": "",
"AllowedPattern" : "[-_ a-zA-Z0-9]*",
"Description": "Name of an existing EC2 KeyPair. Your ICS will launch with this KeyPair.",
"ConstraintDescription": "Must be the name of an existing EC2 KeyPair."
},
"ICSImageAMIId" : {
"Type" : "String",
"Description" : "AMI ID of your existing ICS image"
},
"InstanceType": {
"Description": "Select ICS instance type",
"Type": "String",
"Default": "m5.large",
"AllowedValues": [
"t3.medium",
"t3.large",
"t3.xlarge",
"t3.2xlarge",
"m5.large",
"m5.xlarge",
"m5.2xlarge",
"m5.4xlarge"
],
"ConstraintDescription": "Must be an allowed EC2 instance type."
},
"AdminUsername": {
"Description": "Ivanti Connect Secure admin user.",
"Type": "String",
"MinLength": "1",
"MaxLength": "30",
"AllowedPattern": ".{1,30}"
},
"AdminPassword": {
"Description": "Password for the Ivanti Connect Secure admin user, should be minimum 10 characters",
"Type": "String",
"MinLength": "10",
"MaxLength": "128",
"AllowedPattern": ".{10,128}",
"NoEcho": "true"
},
"ICSConfigData": {
"Type": "String",
"Description": "Ivanti Connect Secure configuration data.",
"Default": "<wins-server>1.1.1.1</wins-server><dns-domain>psecure.net</dns-domain><cert-common-name>va1.psecure.net</cert-common-name><cert-random-text>fdsfpisonvsfnms</cert-random-text><cert-organisation>Psecure Org</cert-organisation><config-download-url></config-download-url><config-data></config-data><auth-code-license></auth-code-license><enable-license-server>n</enable-license-server><accept-license-agreement>y</accept-license-agreement>",
"AllowedPattern": "^<wins-server>(([2][5][0-5]\\.)|([2][0-4][0-9]\\.)|([0-1]?[0-9]?[0-9]\\.)){3}(([2][5][0-5])|([2][0-4][0-9])|([0-1]?[0-9]?[0-9]))</wins-server><dns-domain>.{1,50}</dns-domain><cert-common-name>.{1,50}</cert-common-name><cert-random-text>.{1,50}</cert-random-text><cert-organisation>.{1,80}</cert-organisation><config-download-url>.*</config-download-url><config-data>.*</config-data><auth-code-license>.*</auth-code-license><enable-license-server>[yn]</enable-license-server><accept-license-agreement>[yn]</accept-license-agreement>$",
"ConstraintDescription": "Invalid configuration. Please refer Ivanti Connect Secure AWS deployment guide for configuration elements and allowed values."
},
"VpcId" : {
"Type" : "String",
"Description" : "ID of existing VPC"
},
"SubnetIntId" : {
"Type" : "String",
"Description" : "ID of the subnet where ICS internal interface connects"
},
"SubnetExtId" : {
"Type" : "String",
"Description" : "ID of the subnet where ICS External interface connects"
}
},
"Resources" : {
"EIP0" : {
"Type" : "AWS::EC2::EIP",
"Properties" : {
"Domain" : "vpc"
}
},
"EIPAssoc0" : {
"Type" : "AWS::EC2::EIPAssociation",
"Properties" : {
"NetworkInterfaceId" : { "Ref" : "Eth0" },
"AllocationId" : { "Fn::GetAtt" : ["EIP0", "AllocationId"] },
"PrivateIpAddress" : { "Fn::GetAtt" : ["Eth0", "PrimaryPrivateIpAddress" ] }
}
},
"EIP1" : {
"Type" : "AWS::EC2::EIP",
"Properties" : {
"Domain" : "vpc"
}
},
"EIPAssoc1" : {
"Type" : "AWS::EC2::EIPAssociation",
"Properties" : {
"NetworkInterfaceId" : { "Ref" : "Eth1" },
"AllocationId" : { "Fn::GetAtt" : ["EIP1", "AllocationId"] },
"PrivateIpAddress" : { "Fn::GetAtt" : ["Eth1", "PrimaryPrivateIpAddress" ] }
}
},
"ICSvExternalSecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Access Rules for ICS external port",
"VpcId": {
"Ref": "VpcId"
},
"SecurityGroupIngress": [
{
"IpProtocol": "icmp",
"FromPort": "-1",
"ToPort": "-1",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "80",
"ToPort": "80",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "443",
"ToPort": "443",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "udp",
"FromPort": "4500",
"ToPort": "4500",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "11000",
"ToPort": "11099",
"CidrIp": "0.0.0.0/0"
}
],
"SecurityGroupEgress": [
{
"CidrIp": "127.0.0.1/32",
"IpProtocol": "-1"
}],
"Tags": [
{
"Key": "Name",
"Value": { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvExtSG" ] ] }
}
]
}
},
"ICSvInternalSecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Access Rules for ICS internal port",
"VpcId": {
"Ref": "VpcId"
},
"SecurityGroupIngress": [
{
"IpProtocol": "icmp",
"FromPort": "-1",
"ToPort": "-1",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "80",
"ToPort": "80",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "443",
"ToPort": "443",
"CidrIp": "0.0.0.0/0"
}
],
"Tags": [
{
"Key": "Name",
"Value": { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvIntSG" ] ] }
}
]
}
},
"EC2Instance" : {
"Type" : "AWS::EC2::Instance",
"DependsOn" : ["EIPAssoc0", "EIPAssoc1"],
"Properties" : {
"ImageId" : {"Ref" : "ICSImageAMIId"},
"KeyName" : { "Ref" : "KeyName" },
"InstanceType" : { "Ref" : "InstanceType" },
"NetworkInterfaces" : [
{ "NetworkInterfaceId" : {"Ref" : "Eth0" }, "DeviceIndex" : "0" },
{ "NetworkInterfaceId" : {"Ref" : "Eth1" }, "DeviceIndex" : "1" }
],
"Tags" : [
{"Key" : "Name",
"Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvAWS" ] ] }
}
],
"UserData": {
"Fn::Base64": {
"Fn::Join": [
"",
[
"<pulse-config>",
"<admin-password>",
{
"Ref": "AdminPassword"
},
"</admin-password>",
"<admin-username>",
{
"Ref": "AdminUsername"
},
"</admin-username>",
{
"Ref": "ICSConfigData"
},
"</pulse-config>"
]
]
}
}
}
},
"Eth0" : {
"Type" : "AWS::EC2::NetworkInterface",
"Properties" : {
"Description" : "eth0",
"GroupSet" : [ { "Ref" : "ICSvInternalSecurityGroup" } ],
"SourceDestCheck" : "false",
"SubnetId" : { "Ref" : "SubnetIntId" },
"Tags" : [ {"Key" : "Name", "Value" : "Interface 0"}, {"Key" : "Interface", "Value" : "eth0"} ]
}
},
"Eth1" : {
"Type" : "AWS::EC2::NetworkInterface",
"Properties" : {
"Description" : "eth1",
"GroupSet" : [ { "Ref" : "ICSvExternalSecurityGroup" } ],
"SourceDestCheck" : "false",
"SubnetId" : { "Ref" : "SubnetExtId" },
"Tags" : [ {"Key" : "Name", "Value" : "Interface 1"}, {"Key" : "Interface", "Value" : "eth1"} ]
}
}
},
"Outputs" : {
"InstanceId" : {
"Value" : { "Ref" : "EC2Instance" },
"Description" : "Instance Id of newly created instance"
},
"ExternalAddress" : {
"Value" : { "Fn::Join" : [" ", [ "Public IP address:", { "Ref" : "EIP1" }, "Private IP address:", { "Fn::GetAtt" : ["Eth1", "PrimaryPrivateIpAddress"] }]]},
"Description" : "ICS Extenal Interface details"
},
"InternalAddress" : {
"Value" : { "Fn::Join" : [" ", [ "Public IP address:", { "Ref" : "EIP0" }, "Private IP address:", { "Fn::GetAtt" : ["Eth0", "PrimaryPrivateIpAddress"] }]]},
"Description" : "ICS Internal Interface details"
}
}
}
{
"AWSTemplateFormatVersion" : "2010-09-09",
"Description" : "Deploy ICS with 3 nic into an existing VPC",
"Metadata" : {
"AWS::CloudFormation::Interface" : {
"ParameterGroups" : [
{
"Label" : { "default" : "Existing VPC details" },
"Parameters" : [ "VpcId", "SubnetIntId", "SubnetExtId", "SubnetMgmtId" ]
},
{
"Label" : { "default":"ICS Configuration" },
"Parameters" : [
"ICSImageAMIId",
"InstanceType",
"AdminUsername",
"AdminPassword",
"ICSConfigData",
"KeyName" ]
}
],
"ParameterLabels" : {
"VpcId" : { "default" : "Existing VPC ID" },
"SubnetIntId" : {"default" : "Internal Subnet ID"},
"SubnetExtId" : {"default" : "External Subnet ID"},
"SubnetMgmtId" : {"default" : "Management Subnet ID"},
"ICSImageAMIId" : {"default" : "ICS AMI ID"},
"InstanceType" : {"default" : "Instance Type"},
"KeyName" : {"default" : "SSH Key Name"},
"AdminUsername": {"default": "Admin User Name"},
"AdminPassword": {"default": "Admin Password"},
"ICSConfigData": {"default": "Config Data"}
}
}
},
"Parameters" : {
"KeyName": {
"Type": "AWS::EC2::KeyPair::KeyName",
"AllowedPattern" : "[-_ a-zA-Z0-9]*",
"Description": "Name of an existing EC2 KeyPair. Your ICS will launch with this KeyPair.",
"ConstraintDescription": "Must be the name of an existing EC2 KeyPair."
},
"ICSImageAMIId" : {
"Type" : "String",
"Description" : "AMI ID of your existing ICS image"
},
"InstanceType": {
"Description": "Select ICS instance type",
"Type": "String",
"Default": "m5.large",
"AllowedValues": [
"t3.medium",
"t3.large",
"t3.xlarge",
"m5.large",
"m5.xlarge",
"m5.2xlarge",
"m5.4xlarge"
],
"ConstraintDescription": "Must be an allowed EC2 instance type."
},
"AdminUsername": {
"Description": "Ivanti Connect Secure admin user.",
"Type": "String",
"MinLength": "1",
"MaxLength": "30",
"AllowedPattern": ".{1,30}"
},
"AdminPassword": {
"Description": "Password for the Ivanti Connect Secure admin user, should be minimum 10 characters",
"Type": "String",
"MinLength": "10",
"MaxLength": "128",
"AllowedPattern": ".{10,128}",
"NoEcho": "true"
},
"ICSConfigData": {
"Type": "String",
"Description": "Ivanti Connect Secure configuration data.",
"Default": "<wins-server>1.1.1.1</wins-server><dns-domain>psecure.net</dns-domain><cert-common-name>va1.psecure.net</cert-common-name><cert-random-text>fdsfpisonvsfnms</cert-random-text><cert-organisation>Psecure Org</cert-organisation><config-download-url></config-download-url><config-data></config-data><auth-code-license></auth-code-license><enable-license-server>n</enable-license-server><accept-license-agreement>y</accept-license-agreement>",
"AllowedPattern": "^<wins-server>(([2][5][0-5]\\.)|([2][0-4][0-9]\\.)|([0-1]?[0-9]?[0-9]\\.)){3}(([2][5][0-5])|([2][0-4][0-9])|([0-1]?[0-9]?[0-9]))</wins-server><dns-domain>.{1,50}</dns-domain><cert-common-name>.{1,50}</cert-common-name><cert-random-text>.{1,50}</cert-random-text><cert-organisation>.{1,80}</cert-organisation><config-download-url>.*</config-download-url><config-data>.*</config-data><auth-code-license>.*</auth-code-license><enable-license-server>[yn]</enable-license-server><accept-license-agreement>[yn]</accept-license-agreement>$",
"ConstraintDescription": "Invalid configuration. Please refer Ivanti Connect Secure AWS deployment guide for configuration elements and allowed values."
},
"VpcId" : {
"Type" : "String",
"Description" : "ID of existing VPC"
},
"SubnetIntId" : {
"Type" : "String",
"Description" : "ID of the subnet where ICS internal interface connects"
},
"SubnetExtId" : {
"Type" : "String",
"Description" : "ID of the subnet where ICS External interface connects"
},
"SubnetMgmtId" : {
"Type" : "String",
"Description" : "ID of the subnet where ICS Management interface connects"
}
},
"Resources" : {
"EIP0" : {
"Type" : "AWS::EC2::EIP",
"Properties" : {
"Domain" : "vpc"
}
},
"EIPAssoc0" : {
"Type" : "AWS::EC2::EIPAssociation",
"Properties" : {
"NetworkInterfaceId" : { "Ref" : "Eth0" },
"AllocationId" : { "Fn::GetAtt" : ["EIP0", "AllocationId"] },
"PrivateIpAddress" : { "Fn::GetAtt" : ["Eth0", "PrimaryPrivateIpAddress" ] }
}
},
"EIP1" : {
"Type" : "AWS::EC2::EIP",
"Properties" : {
"Domain" : "vpc"
}
},
"EIPAssoc1" : {
"Type" : "AWS::EC2::EIPAssociation",
"Properties" : {
"NetworkInterfaceId" : { "Ref" : "Eth1" },
"AllocationId" : { "Fn::GetAtt" : ["EIP1", "AllocationId"] },
"PrivateIpAddress" : { "Fn::GetAtt" : ["Eth1", "PrimaryPrivateIpAddress" ] }
}
},
"EIP2" : {
"Type" : "AWS::EC2::EIP",
"Properties" : {
"Domain" : "vpc"
}
},
"EIPAssoc2" : {
"Type" : "AWS::EC2::EIPAssociation",
"Properties" : {
"NetworkInterfaceId" : { "Ref" : "Eth2" },
"AllocationId" : { "Fn::GetAtt" : ["EIP2", "AllocationId"] },
"PrivateIpAddress" : { "Fn::GetAtt" : ["Eth2", "PrimaryPrivateIpAddress" ] }
}
},
"ICSvExternalSecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Access Rules for ICS external port",
"VpcId": {
"Ref": "VpcId"
},
"SecurityGroupIngress": [
{
"IpProtocol": "icmp",
"FromPort": "-1",
"ToPort": "-1",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "80",
"ToPort": "80",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "443",
"ToPort": "443",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "udp",
"FromPort": "4500",
"ToPort": "4500",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "11000",
"ToPort": "11099",
"CidrIp": "0.0.0.0/0"
}
],
"SecurityGroupEgress": [
{
"CidrIp": "127.0.0.1/32",
"IpProtocol": "-1"
}],
"Tags": [
{
"Key": "Name",
"Value": { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvExtSG" ] ] }
}
]
}
},
"ICSvInternalSecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Access Rules for ICS internal port",
"VpcId": {
"Ref": "VpcId"
},
"SecurityGroupIngress": [
{
"IpProtocol": "icmp",
"FromPort": "-1",
"ToPort": "-1",
"CidrIp": "0.0.0.0/0"
}
],
"Tags": [
{
"Key": "Name",
"Value": { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvIntSG" ] ] }
}
]
}
},
"ICSvManagementSecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Access Rules for ICS Management port",
"VpcId": {
"Ref": "VpcId"
},
"SecurityGroupIngress": [
{
"IpProtocol": "icmp",
"FromPort": "-1",
"ToPort": "-1",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "80",
"ToPort": "80",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "443",
"ToPort": "443",
"CidrIp": "0.0.0.0/0"
}
],
"SecurityGroupEgress": [
{
"CidrIp": "127.0.0.1/32",
"IpProtocol": "-1"
}],
"Tags": [
{
"Key": "Name",
"Value": { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvMgmtSG" ] ] }
}
]
}
},
"EC2Instance" : {
"Type" : "AWS::EC2::Instance",
"DependsOn" : ["EIPAssoc0", "EIPAssoc1", "EIPAssoc2"],
"Properties" : {
"ImageId" : {"Ref" : "ICSImageAMIId"},
"KeyName" : { "Ref" : "KeyName" },
"InstanceType" : { "Ref" : "InstanceType" },
"NetworkInterfaces" : [
{ "NetworkInterfaceId" : {"Ref" : "Eth0" }, "DeviceIndex" : "0" },
{ "NetworkInterfaceId" : {"Ref" : "Eth1" }, "DeviceIndex" : "1" },
{ "NetworkInterfaceId" : {"Ref" : "Eth2" }, "DeviceIndex" : "2" }
],
"Tags" : [
{"Key" : "Name",
"Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvAWS" ] ] }
}
],
"UserData": {
"Fn::Base64": {
"Fn::Join": [
"",
[
"<pulse-config>",
"<admin-password>",
{
"Ref": "AdminPassword"
},
"</admin-password>",
"<admin-username>",
{
"Ref": "AdminUsername"
},
"</admin-username>",
{
"Ref": "ICSConfigData"
},
"</pulse-config>"
]
]
}
}
}
},
"Eth0" : {
"Type" : "AWS::EC2::NetworkInterface",
"Properties" : {
"Description" : "eth0",
"GroupSet" : [ { "Ref" : "ICSvInternalSecurityGroup" } ],
"SourceDestCheck" : "false",
"SubnetId" : { "Ref" : "SubnetIntId" },
"Tags" : [ {"Key" : "Name", "Value" : "Interface 0"}, {"Key" : "Interface", "Value" : "eth0"} ]
}
},
"Eth1" : {
"Type" : "AWS::EC2::NetworkInterface",
"Properties" : {
"Description" : "eth1",
"GroupSet" : [ { "Ref" : "ICSvExternalSecurityGroup" } ],
"SourceDestCheck" : "false",
"SubnetId" : { "Ref" : "SubnetExtId" },
"Tags" : [ {"Key" : "Name", "Value" : "Interface 1"}, {"Key" : "Interface", "Value" : "eth1"} ]
}
},
"Eth2" : {
"Type" : "AWS::EC2::NetworkInterface",
"Properties" : {
"Description" : "eth2",
"GroupSet" : [ { "Ref" : "ICSvManagementSecurityGroup" } ],
"SourceDestCheck" : "false",
"SubnetId" : { "Ref" : "SubnetMgmtId" },
"Tags" : [ {"Key" : "Name", "Value" : "Interface 2"}, {"Key" : "Interface", "Value" : "eth2"} ]
}
}
},
"Outputs" : {
"InstanceId" : {
"Value" : { "Ref" : "EC2Instance" },
"Description" : "Instance Id of newly created instance"
},
"ManagementAddress" : {
"Value" : { "Fn::Join" : [" ", [ "Public IP address:", { "Ref" : "EIP2" }, "Private IP address:", { "Fn::GetAtt" : ["Eth2", "PrimaryPrivateIpAddress"] }]]},
"Description" : "ICS Management Interface details"
},
"ExternalAddress" : {
"Value" : { "Fn::Join" : [" ", [ "Public IP address:", { "Ref" : "EIP1" }, "Private IP address:", { "Fn::GetAtt" : ["Eth1", "PrimaryPrivateIpAddress"] }]]},
"Description" : "ICS External Interface details"
},
"InternalAddress" : {
"Value" : { "Fn::Join" : [" ", [ "Public IP address:", { "Ref" : "EIP0" }, "Private IP address:", { "Fn::GetAtt" : ["Eth0", "PrimaryPrivateIpAddress"] }]]},
"Description" : "ICS Internal Interface details"
}
}
}
To deploy 2-NIC or 3-NIC in a new VPC respectively using the links below:
{
"AWSTemplateFormatVersion" : "2010-09-09",
"Description" : "Deploy ICS with 2 nic into a new VPC",
"Metadata" : {
"AWS::CloudFormation::Interface" : {
"ParameterGroups" : [
{
"Label" : { "default" : "New VPC Configuration" },
"Parameters" : [ "VPCCIDR", "InternalSubnetCIDR", "ExternalSubnetCIDR", "TunnelSubnetCIDR" ]
},
{
"Label" : { "default":"ICS Configuration" },
"Parameters" : [
"InstanceType",
"AdminUsername",
"AdminPassword",
"ICSConfigData",
"ICSImageAMIId",
"KeyName"
]
}
],
"ParameterLabels" : {
"VPCCIDR" : { "default" : "New VPC address space" },
"InternalSubnetCIDR" : {"default" : "Internal Subnet address space"},
"ExternalSubnetCIDR" : {"default" : "External Subnet address space"},
"TunnelSubnetCIDR" : {"default" : "Tunnel Subnet address space"},
"ICSImageAMIId" : {"default" : "ICS AMI ID"},
"InstanceType" : {"default" : "Instance Type"},
"KeyName" : {"default" : "SSH Key Name"},
"AdminUsername": {"default": "Admin User Name"},
"AdminPassword": {"default": "Admin Password"},
"ICSConfigData": {"default": "Config Data"}
}
}
},
"Parameters" : {
"KeyName": {
"Type": "AWS::EC2::KeyPair::KeyName",
"Default": "",
"AllowedPattern" : "[-_ a-zA-Z0-9]*",
"Description": "Name of an existing EC2 KeyPair. Your ICS will launch with this KeyPair.",
"ConstraintDescription": "Must be the name of an existing EC2 KeyPair."
},
"ICSImageAMIId" : {
"Type" : "String",
"Description" : "AMI ID of your existing ICS image"
},
"InstanceType": {
"Description": "Select ICS instance type",
"Type": "String",
"Default": "m5.large",
"AllowedValues": [
"t3.medium",
"t3.large",
"t3.xlarge",
"m5.large",
"m5.xlarge",
"m5.2xlarge",
"m5.4xlarge"
],
"ConstraintDescription": "Must be an allowed EC2 instance type."
},
"AdminUsername": {
"Description": "Ivanti Connect Secure admin user.",
"Type": "String",
"MinLength": "1",
"MaxLength": "30",
"AllowedPattern": ".{1,30}"
},
"AdminPassword": {
"Description": "Password for the Ivanti Connect Secure admin user, should be minimum 10 characters",
"Type": "String",
"MinLength": "10",
"MaxLength": "128",
"AllowedPattern": ".{10,128}",
"NoEcho": "true"
},
"ICSConfigData": {
"Type": "String",
"Description": "Ivanti Connect Secure configuration data.",
"Default": "<wins-server>1.1.1.1</wins-server><dns-domain>psecure.net</dns-domain><cert-common-name>va1.psecure.net</cert-common-name><cert-random-text>fdsfpisonvsfnms</cert-random-text><cert-organisation>Psecure Org</cert-organisation><config-download-url></config-download-url><config-data></config-data><auth-code-license></auth-code-license><enable-license-server>n</enable-license-server><accept-license-agreement>y</accept-license-agreement>",
"AllowedPattern": "^<wins-server>(([2][5][0-5]\\.)|([2][0-4][0-9]\\.)|([0-1]?[0-9]?[0-9]\\.)){3}(([2][5][0-5])|([2][0-4][0-9])|([0-1]?[0-9]?[0-9]))</wins-server><dns-domain>.{1,50}</dns-domain><cert-common-name>.{1,50}</cert-common-name><cert-random-text>.{1,50}</cert-random-text><cert-organisation>.{1,80}</cert-organisation><config-download-url>.*</config-download-url><config-data>.*</config-data><auth-code-license>.*</auth-code-license><enable-license-server>[yn]</enable-license-server><accept-license-agreement>[yn]</accept-license-agreement>$",
"ConstraintDescription": "Invalid configuration. Please refer Ivanti Connect Secure AWS deployment guide for configuration elements and allowed values."
},
"VPCCIDR": {
"Description": "CIDR block for entire VPC.",
"Type": "String",
"Default": "10.20.0.0/16",
"AllowedPattern": "^(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])(\\/([0-9]|[1-2][0-9]|3[0-2]))$",
"ConstraintDescription": "Must be a valid CIDR range of the form x.x.x.x/x."
},
"InternalSubnetCIDR": {
"Description": "ICS internal interface connects to this subnet",
"Type": "String",
"Default": "10.20.1.0/24",
"AllowedPattern": "^(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])(\\/([0-9]|[1-2][0-9]|3[0-2]))$",
"ConstraintDescription": "CIDR block parameter must be in the form x.x.x.x/x"
},
"ExternalSubnetCIDR": {
"Description": "ICS external interface connects to this subnet",
"Type": "String",
"Default": "10.20.2.0/24",
"AllowedPattern": "^(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])(\\/([0-9]|[1-2][0-9]|3[0-2]))$",
"ConstraintDescription": "CIDR block parameter must be in the form x.x.x.x/x"
},
"TunnelSubnetCIDR": {
"Description": "For L3 VPN connections ICS hands over IP to the clients from this subnet",
"Type": "String",
"Default": "10.20.3.0/24",
"AllowedPattern": "^(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])(\\/([0-9]|[1-2][0-9]|3[0-2]))$",
"ConstraintDescription": "CIDR block parameter must be in the form x.x.x.x/x"
}
},
"Resources" : {
"VPC" : {
"Type" : "AWS::EC2::VPC",
"Properties" : {
"CidrBlock" : {"Ref": "VPCCIDR"},
"EnableDnsHostnames": "true",
"EnableDnsSupport": "true",
"Tags" : [ {"Key" : "Application", "Value" : { "Ref" : "AWS::StackId"} },
{"Key" : "Name", "Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSVPC" ] ] } }
]
}
},
"IntSubnet" : {
"Type" : "AWS::EC2::Subnet",
"Properties" : {
"VpcId" : { "Ref" : "VPC" },
"CidrBlock" : {"Ref" : "InternalSubnetCIDR"},
"AvailabilityZone" : {
"Fn::Select" : [ "0", { "Fn::GetAZs" : "" } ]
},
"Tags" : [ {"Key" : "Application", "Value" : { "Ref" : "AWS::StackId"} },
{"Key" : "Name", "Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSVPCIntSubnet" ] ] } }
]
}
},
"ExtSubnet" : {
"Type" : "AWS::EC2::Subnet",
"Properties" : {
"VpcId" : { "Ref" : "VPC" },
"CidrBlock" : {"Ref" : "ExternalSubnetCIDR"},
"AvailabilityZone" : {
"Fn::Select" : [ "0", { "Fn::GetAZs" : "" } ]
},
"Tags" : [ {"Key" : "Application", "Value" : { "Ref" : "AWS::StackId"} },
{"Key" : "Name", "Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSVPCExtSubnet" ] ] } }
]
}
},
"TunnelSubnet" : {
"Type" : "AWS::EC2::Subnet",
"Properties" : {
"VpcId" : { "Ref" : "VPC" },
"CidrBlock" : {"Ref" : "TunnelSubnetCIDR"},
"AvailabilityZone" : {
"Fn::Select" : [ "0", { "Fn::GetAZs" : "" } ]
},
"Tags" : [ {"Key" : "Application", "Value" : { "Ref" : "AWS::StackId"} },
{"Key" : "Name", "Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSVPCTunnelSubnet" ] ] } }
]
}
},
"InternetGateway" : {
"Type" : "AWS::EC2::InternetGateway",
"Properties" : {
"Tags" : [ {"Key" : "Application", "Value" : { "Ref" : "AWS::StackId"} },
{"Key" : "Name", "Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSVPC" ] ] } }
]
}
},
"AttachGateway" : {
"Type" : "AWS::EC2::VPCGatewayAttachment",
"Properties" : {
"VpcId" : { "Ref" : "VPC" },
"InternetGatewayId" : { "Ref" : "InternetGateway" }
}
},
"PublicSubnetRouteTable" : {
"Type" : "AWS::EC2::RouteTable",
"Properties" : {
"VpcId" : {"Ref" : "VPC"},
"Tags" : [ {"Key" : "Application", "Value" : { "Ref" : "AWS::StackId"} },
{"Key" : "Name", "Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSVPC" ] ] } }
]
}
},
"PublicSubnetRoute" : {
"Type" : "AWS::EC2::Route",
"DependsOn" : "AttachGateway",
"Properties" : {
"RouteTableId" : { "Ref" : "PublicSubnetRouteTable" },
"DestinationCidrBlock" : "0.0.0.0/0",
"GatewayId" : { "Ref" : "InternetGateway" }
}
},
"ExtSubnetRouteTableAssociation" : {
"Type" : "AWS::EC2::SubnetRouteTableAssociation",
"Properties" : {
"SubnetId" : { "Ref" : "ExtSubnet" },
"RouteTableId" : { "Ref" : "PublicSubnetRouteTable" }
}
},
"IntSubnetRouteTableAssociation" : {
"Type" : "AWS::EC2::SubnetRouteTableAssociation",
"Properties" : {
"SubnetId" : { "Ref" : "IntSubnet" },
"RouteTableId" : { "Ref" : "PublicSubnetRouteTable" }
}
},
"EIP0" : {
"Type" : "AWS::EC2::EIP",
"Properties" : {
"Domain" : "vpc"
}
},
"EIPAssoc0" : {
"Type" : "AWS::EC2::EIPAssociation",
"Properties" : {
"NetworkInterfaceId" : { "Ref" : "Eth0" },
"AllocationId" : { "Fn::GetAtt" : ["EIP0", "AllocationId"] },
"PrivateIpAddress" : { "Fn::GetAtt" : ["Eth0", "PrimaryPrivateIpAddress" ] }
}
},
"EIP1" : {
"Type" : "AWS::EC2::EIP",
"Properties" : {
"Domain" : "vpc"
}
},
"EIPAssoc1" : {
"Type" : "AWS::EC2::EIPAssociation",
"Properties" : {
"NetworkInterfaceId" : { "Ref" : "Eth1" },
"AllocationId" : { "Fn::GetAtt" : ["EIP1", "AllocationId"] },
"PrivateIpAddress" : { "Fn::GetAtt" : ["Eth1", "PrimaryPrivateIpAddress" ] }
}
},
"ICSvExternalSecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Access Rules for ICS external port",
"VpcId": {
"Ref": "VPC"
},
"SecurityGroupIngress": [
{
"IpProtocol": "icmp",
"FromPort": "-1",
"ToPort": "-1",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "80",
"ToPort": "80",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "443",
"ToPort": "443",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "udp",
"FromPort": "4500",
"ToPort": "4500",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "11000",
"ToPort": "11099",
"CidrIp": "0.0.0.0/0"
}
],
"SecurityGroupEgress": [
{
"CidrIp": "127.0.0.1/32",
"IpProtocol": "-1"
}],
"Tags": [
{
"Key": "Name",
"Value": { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvExtSG" ] ] }
}
]
}
},
"ICSvInternalSecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Access Rules for ICS internal port",
"VpcId": {
"Ref": "VPC"
},
"SecurityGroupIngress": [
{
"IpProtocol": "icmp",
"FromPort": "-1",
"ToPort": "-1",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "443",
"ToPort": "443",
"CidrIp": "0.0.0.0/0"
}
],
"Tags": [
{
"Key": "Name",
"Value": { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvIntSG" ] ] }
}
]
}
},
"EC2Instance" : {
"Type" : "AWS::EC2::Instance",
"DependsOn" : ["EIPAssoc0", "EIPAssoc1"],
"Properties" : {
"ImageId" : {"Ref" : "ICSImageAMIId"},
"KeyName" : { "Ref" : "KeyName" },
"InstanceType" : { "Ref" : "InstanceType" },
"NetworkInterfaces" : [
{ "NetworkInterfaceId" : {"Ref" : "Eth0" }, "DeviceIndex" : "0" },
{ "NetworkInterfaceId" : {"Ref" : "Eth1" }, "DeviceIndex" : "1" }
],
"Tags" : [
{"Key" : "Name",
"Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvAWS" ] ] }
}
],
"UserData": {
"Fn::Base64": {
"Fn::Join": [
"",
[
"<pulse-config>",
"<admin-password>",
{
"Ref": "AdminPassword"
},
"</admin-password>",
"<admin-username>",
{
"Ref": "AdminUsername"
},
"</admin-username>",
{
"Ref": "ICSConfigData"
},
"</pulse-config>"
]
]
}
}
}
},
"Eth0" : {
"Type" : "AWS::EC2::NetworkInterface",
"Properties" : {
"Description" : "eth0",
"GroupSet" : [ { "Ref" : "ICSvInternalSecurityGroup" } ],
"SourceDestCheck" : "false",
"SubnetId" : { "Ref" : "IntSubnet" },
"Tags" : [ {"Key" : "Name", "Value" : "Interface 0"}, {"Key" : "Interface", "Value" : "eth0"} ]
}
},
"Eth1" : {
"Type" : "AWS::EC2::NetworkInterface",
"Properties" : {
"Description" : "eth1",
"GroupSet" : [ { "Ref" : "ICSvExternalSecurityGroup" } ],
"SourceDestCheck" : "false",
"SubnetId" : { "Ref" : "ExtSubnet" },
"Tags" : [ {"Key" : "Name", "Value" : "Interface 1"}, {"Key" : "Interface", "Value" : "eth1"} ]
}
}
},
"Outputs" : {
"InstanceId" : {
"Value" : { "Ref" : "EC2Instance" },
"Description" : "Instance Id of newly created instance"
},
"ExternalAddress" : {
"Value" : { "Fn::Join" : [" ", [ "Public IP address:", { "Ref" : "EIP1" }, "Private IP address:", { "Fn::GetAtt" : ["Eth1", "PrimaryPrivateIpAddress"] }]]},
"Description" : "ICS Extenal Interface details"
},
"InternalAddress" : {
"Value" : { "Fn::Join" : [" ", [ "Public IP address:", { "Ref" : "EIP0" }, "Private IP address:", { "Fn::GetAtt" : ["Eth0", "PrimaryPrivateIpAddress"] }]]},
"Description" : "ICS Internal Interface details"
}
}
}
{
"AWSTemplateFormatVersion" : "2010-09-09",
"Description" : "Deploy ICS with 3 nic into a new VPC",
"Metadata" : {
"AWS::CloudFormation::Interface" : {
"ParameterGroups" : [
{
"Label" : { "default" : "New VPC Configuration" },
"Parameters" : [ "VPCCIDR", "InternalSubnetCIDR", "ExternalSubnetCIDR", "ManagementSubnetCIDR", "TunnelSubnetCIDR" ]
},
{
"Label" : { "default":"ICS Configuration" },
"Parameters" : [
"ICSImageAMIId",
"InstanceType",
"AdminUsername",
"AdminPassword",
"ICSConfigData",
"KeyName"
]
}
],
"ParameterLabels" : {
"VPCCIDR" : { "default" : "New VPC address space" },
"InternalSubnetCIDR" : {"default" : "Internal Subnet address space"},
"ExternalSubnetCIDR" : {"default" : "External Subnet address space"},
"ManagementSubnetCIDR" : {"default" : "Management Subnet address space"},
"TunnelSubnetCIDR" : {"default" : "Tunnel Subnet address space"},
"ICSImageAMIId" : {"default" : "ICS AMI ID"},
"InstanceType" : {"default" : "Instance Type"},
"KeyName" : {"default" : "SSH Key Name"},
"AdminUsername": {"default": "Admin User Name"},
"AdminPassword": {"default": "Admin Password"},
"ICSConfigData": {"default": "Config Data"}
}
}
},
"Parameters" : {
"KeyName": {
"Type": "AWS::EC2::KeyPair::KeyName",
"Default": "",
"AllowedPattern" : "[-_ a-zA-Z0-9]*",
"Description": "Name of an existing EC2 KeyPair. Your ICS will launch with this KeyPair.",
"ConstraintDescription": "Must be the name of an existing EC2 KeyPair."
},
"ICSImageAMIId" : {
"Type" : "String",
"Description" : "AMI ID of your existing ICS image"
},
"InstanceType": {
"Description": "Select ICS instance type",
"Type": "String",
"Default": "m5.large",
"AllowedValues": [
"t3.medium",
"t3.large",
"t3.xlarge",
"m5.large",
"m5.xlarge",
"m5.2xlarge",
"m5.4xlarge"
],
"ConstraintDescription": "Must be an allowed EC2 instance type."
},
"AdminUsername": {
"Description": "Ivanti Connect Secure admin user.",
"Type": "String",
"MinLength": "1",
"MaxLength": "30",
"AllowedPattern": ".{1,30}"
},
"AdminPassword": {
"Description": "Password for the Ivanti Connect Secure admin user, should be minimum 10 characters",
"Type": "String",
"MinLength": "10",
"MaxLength": "128",
"AllowedPattern": ".{10,128}",
"NoEcho": "true"
},
"ICSConfigData": {
"Type": "String",
"Description": "Ivanti Connect Secure configuration data.",
"Default": "<wins-server>1.1.1.1</wins-server><dns-domain>psecure.net</dns-domain><cert-common-name>va1.psecure.net</cert-common-name><cert-random-text>fdsfpisonvsfnms</cert-random-text><cert-organisation>Psecure Org</cert-organisation><config-download-url></config-download-url><config-data></config-data><auth-code-license></auth-code-license><enable-license-server>n</enable-license-server><accept-license-agreement>y</accept-license-agreement>",
"AllowedPattern": "^<wins-server>(([2][5][0-5]\\.)|([2][0-4][0-9]\\.)|([0-1]?[0-9]?[0-9]\\.)){3}(([2][5][0-5])|([2][0-4][0-9])|([0-1]?[0-9]?[0-9]))</wins-server><dns-domain>.{1,50}</dns-domain><cert-common-name>.{1,50}</cert-common-name><cert-random-text>.{1,50}</cert-random-text><cert-organisation>.{1,80}</cert-organisation><config-download-url>.*</config-download-url><config-data>.*</config-data><auth-code-license>.*</auth-code-license><enable-license-server>[yn]</enable-license-server><accept-license-agreement>[yn]</accept-license-agreement>$",
"ConstraintDescription": "Invalid configuration. Please refer Ivanti Connect Secure AWS deployment guide for configuration elements and allowed values."
},
"VPCCIDR": {
"Description": "CIDR block for entire VPC.",
"Type": "String",
"Default": "10.20.0.0/16",
"AllowedPattern": "^(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])(\\/([0-9]|[1-2][0-9]|3[0-2]))$",
"ConstraintDescription": "Must be a valid CIDR range of the form x.x.x.x/x."
},
"InternalSubnetCIDR": {
"Description": "ICS internal interface connects to this subnet",
"Type": "String",
"Default": "10.20.1.0/24",
"AllowedPattern": "^(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])(\\/([0-9]|[1-2][0-9]|3[0-2]))$",
"ConstraintDescription": "CIDR block parameter must be in the form x.x.x.x/x"
},
"ExternalSubnetCIDR": {
"Description": "ICS external interface connects to this subnet",
"Type": "String",
"Default": "10.20.2.0/24",
"AllowedPattern": "^(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])(\\/([0-9]|[1-2][0-9]|3[0-2]))$",
"ConstraintDescription": "CIDR block parameter must be in the form x.x.x.x/x"
},
"ManagementSubnetCIDR": {
"Description": "ICS management interface connects to this subnet",
"Type": "String",
"Default": "10.20.3.0/24",
"AllowedPattern": "^(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])(\\/([0-9]|[1-2][0-9]|3[0-2]))$",
"ConstraintDescription": "CIDR block parameter must be in the form x.x.x.x/x"
},
"TunnelSubnetCIDR": {
"Description": "For L3 VPN connections ICS hands over IP to the clients from this subnet",
"Type": "String",
"Default": "10.20.4.0/24",
"AllowedPattern": "^(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])(\\/([0-9]|[1-2][0-9]|3[0-2]))$",
"ConstraintDescription": "CIDR block parameter must be in the form x.x.x.x/x"
}
},
"Resources" : {
"VPC" : {
"Type" : "AWS::EC2::VPC",
"Properties" : {
"CidrBlock" : {"Ref": "VPCCIDR"},
"EnableDnsHostnames": "true",
"EnableDnsSupport": "true",
"Tags" : [ {"Key" : "Application", "Value" : { "Ref" : "AWS::StackId"} },
{"Key" : "Name", "Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSVPC" ] ] } }
]
}
},
"IntSubnet" : {
"Type" : "AWS::EC2::Subnet",
"Properties" : {
"VpcId" : { "Ref" : "VPC" },
"CidrBlock" : {"Ref" : "InternalSubnetCIDR"},
"AvailabilityZone" : {
"Fn::Select" : [ "0", { "Fn::GetAZs" : "" } ]
},
"Tags" : [ {"Key" : "Application", "Value" : { "Ref" : "AWS::StackId"} },
{"Key" : "Name", "Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSVPCIntSubnet" ] ] } }
]
}
},
"ExtSubnet" : {
"Type" : "AWS::EC2::Subnet",
"Properties" : {
"VpcId" : { "Ref" : "VPC" },
"CidrBlock" : {"Ref" : "ExternalSubnetCIDR"},
"AvailabilityZone" : {
"Fn::Select" : [ "0", { "Fn::GetAZs" : "" } ]
},
"Tags" : [ {"Key" : "Application", "Value" : { "Ref" : "AWS::StackId"} },
{"Key" : "Name", "Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSVPCExtSubnet" ] ] } }
]
}
},
"MgmtSubnet" : {
"Type" : "AWS::EC2::Subnet",
"Properties" : {
"VpcId" : { "Ref" : "VPC" },
"CidrBlock" : {"Ref" : "ManagementSubnetCIDR"},
"AvailabilityZone" : {
"Fn::Select" : [ "0", { "Fn::GetAZs" : "" } ]
},
"Tags" : [ {"Key" : "Application", "Value" : { "Ref" : "AWS::StackId"} },
{"Key" : "Name", "Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSVPCMgmtSubnet" ] ] } }
]
}
},
"TunnelSubnet" : {
"Type" : "AWS::EC2::Subnet",
"Properties" : {
"VpcId" : { "Ref" : "VPC" },
"CidrBlock" : {"Ref" : "TunnelSubnetCIDR"},
"AvailabilityZone" : {
"Fn::Select" : [ "0", { "Fn::GetAZs" : "" } ]
},
"Tags" : [ {"Key" : "Application", "Value" : { "Ref" : "AWS::StackId"} },
{"Key" : "Name", "Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSVPCTunnelSubnet" ] ] } }
]
}
},
"InternetGateway" : {
"Type" : "AWS::EC2::InternetGateway",
"Properties" : {
"Tags" : [ {"Key" : "Application", "Value" : { "Ref" : "AWS::StackId"} },
{"Key" : "Name", "Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSVPC" ] ] } }
]
}
},
"AttachGateway" : {
"Type" : "AWS::EC2::VPCGatewayAttachment",
"Properties" : {
"VpcId" : { "Ref" : "VPC" },
"InternetGatewayId" : { "Ref" : "InternetGateway" }
}
},
"PublicSubnetRouteTable" : {
"Type" : "AWS::EC2::RouteTable",
"Properties" : {
"VpcId" : {"Ref" : "VPC"},
"Tags" : [ {"Key" : "Application", "Value" : { "Ref" : "AWS::StackId"} },
{"Key" : "Name", "Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSVPC" ] ] } }
]
}
},
"PublicSubnetRoute" : {
"Type" : "AWS::EC2::Route",
"DependsOn" : "AttachGateway",
"Properties" : {
"RouteTableId" : { "Ref" : "PublicSubnetRouteTable" },
"DestinationCidrBlock" : "0.0.0.0/0",
"GatewayId" : { "Ref" : "InternetGateway" }
}
},
"ExtSubnetRouteTableAssociation" : {
"Type" : "AWS::EC2::SubnetRouteTableAssociation",
"Properties" : {
"SubnetId" : { "Ref" : "ExtSubnet" },
"RouteTableId" : { "Ref" : "PublicSubnetRouteTable" }
}
},
"MgmtSubnetRouteTableAssociation" : {
"Type" : "AWS::EC2::SubnetRouteTableAssociation",
"Properties" : {
"SubnetId" : { "Ref" : "MgmtSubnet" },
"RouteTableId" : { "Ref" : "PublicSubnetRouteTable" }
}
},
"IntSubnetRouteTableAssociation" : {
"Type" : "AWS::EC2::SubnetRouteTableAssociation",
"Properties" : {
"SubnetId" : { "Ref" : "IntSubnet" },
"RouteTableId" : { "Ref" : "PublicSubnetRouteTable" }
}
},
"EIP0" : {
"Type" : "AWS::EC2::EIP",
"Properties" : {
"Domain" : "vpc"
}
},
"EIPAssoc0" : {
"Type" : "AWS::EC2::EIPAssociation",
"Properties" : {
"NetworkInterfaceId" : { "Ref" : "Eth0" },
"AllocationId" : { "Fn::GetAtt" : ["EIP0", "AllocationId"] },
"PrivateIpAddress" : { "Fn::GetAtt" : ["Eth0", "PrimaryPrivateIpAddress" ] }
}
},
"EIP1" : {
"Type" : "AWS::EC2::EIP",
"Properties" : {
"Domain" : "vpc"
}
},
"EIPAssoc1" : {
"Type" : "AWS::EC2::EIPAssociation",
"Properties" : {
"NetworkInterfaceId" : { "Ref" : "Eth1" },
"AllocationId" : { "Fn::GetAtt" : ["EIP1", "AllocationId"] },
"PrivateIpAddress" : { "Fn::GetAtt" : ["Eth1", "PrimaryPrivateIpAddress" ] }
}
},
"EIP2" : {
"Type" : "AWS::EC2::EIP",
"Properties" : {
"Domain" : "vpc"
}
},
"EIPAssoc2" : {
"Type" : "AWS::EC2::EIPAssociation",
"Properties" : {
"NetworkInterfaceId" : { "Ref" : "Eth2" },
"AllocationId" : { "Fn::GetAtt" : ["EIP2", "AllocationId"] },
"PrivateIpAddress" : { "Fn::GetAtt" : ["Eth2", "PrimaryPrivateIpAddress" ] }
}
},
"ICSvExternalSecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Access Rules for ICS external port",
"VpcId": {
"Ref": "VPC"
},
"SecurityGroupIngress": [
{
"IpProtocol": "icmp",
"FromPort": "-1",
"ToPort": "-1",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "80",
"ToPort": "80",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "443",
"ToPort": "443",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "udp",
"FromPort": "4500",
"ToPort": "4500",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "11000",
"ToPort": "11099",
"CidrIp": "0.0.0.0/0"
}
],
"SecurityGroupEgress": [
{
"CidrIp": "127.0.0.1/32",
"IpProtocol": "-1"
}],
"Tags": [
{
"Key": "Name",
"Value": { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvExtSG" ] ] }
}
]
}
},
"ICSvInternalSecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Access Rules for ICS internal port",
"VpcId": {
"Ref": "VPC"
},
"SecurityGroupIngress": [
{
"IpProtocol": "icmp",
"FromPort": "-1",
"ToPort": "-1",
"CidrIp": "0.0.0.0/0"
}
],
"Tags": [
{
"Key": "Name",
"Value": { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvIntSG" ] ] }
}
]
}
},
"ICSvManagementSecurityGroup": {
"Type": "AWS::EC2::SecurityGroup",
"Properties": {
"GroupDescription": "Access Rules for ICS Management port",
"VpcId": {
"Ref": "VPC"
},
"SecurityGroupIngress": [
{
"IpProtocol": "icmp",
"FromPort": "-1",
"ToPort": "-1",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "80",
"ToPort": "80",
"CidrIp": "0.0.0.0/0"
},
{
"IpProtocol": "tcp",
"FromPort": "443",
"ToPort": "443",
"CidrIp": "0.0.0.0/0"
}
],
"SecurityGroupEgress": [
{
"CidrIp": "127.0.0.1/32",
"IpProtocol": "-1"
}],
"Tags": [
{
"Key": "Name",
"Value": { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvMgmtSG" ] ] }
}
]
}
},
"EC2Instance" : {
"Type" : "AWS::EC2::Instance",
"DependsOn" : ["EIPAssoc0", "EIPAssoc1", "EIPAssoc2"],
"Properties" : {
"ImageId" : {"Ref" : "ICSImageAMIId"},
"KeyName" : { "Ref" : "KeyName" },
"InstanceType" : { "Ref" : "InstanceType" },
"NetworkInterfaces" : [
{ "NetworkInterfaceId" : {"Ref" : "Eth0" }, "DeviceIndex" : "0" },
{ "NetworkInterfaceId" : {"Ref" : "Eth1" }, "DeviceIndex" : "1" },
{ "NetworkInterfaceId" : {"Ref" : "Eth2" }, "DeviceIndex" : "2" }
],
"Tags" : [
{"Key" : "Name",
"Value" : { "Fn::Join": [ "-", [ { "Ref": "AWS::StackName" }, "ICSvAWS" ] ] }
}
],
"UserData": {
"Fn::Base64": {
"Fn::Join": [
"",
[
"<pulse-config>",
"<admin-password>",
{
"Ref": "AdminPassword"
},
"</admin-password>",
"<admin-username>",
{
"Ref": "AdminUsername"
},
"</admin-username>",
{
"Ref": "ICSConfigData"
},
"</pulse-config>"
]
]
}
}
}
},
"Eth0" : {
"Type" : "AWS::EC2::NetworkInterface",
"Properties" : {
"Description" : "eth0",
"GroupSet" : [ { "Ref" : "ICSvInternalSecurityGroup" } ],
"SourceDestCheck" : "false",
"SubnetId" : { "Ref" : "IntSubnet" },
"Tags" : [ {"Key" : "Name", "Value" : "Interface 0"}, {"Key" : "Interface", "Value" : "eth0"} ]
}
},
"Eth1" : {
"Type" : "AWS::EC2::NetworkInterface",
"Properties" : {
"Description" : "eth1",
"GroupSet" : [ { "Ref" : "ICSvExternalSecurityGroup" } ],
"SourceDestCheck" : "false",
"SubnetId" : { "Ref" : "ExtSubnet" },
"Tags" : [ {"Key" : "Name", "Value" : "Interface 1"}, {"Key" : "Interface", "Value" : "eth1"} ]
}
},
"Eth2" : {
"Type" : "AWS::EC2::NetworkInterface",
"Properties" : {
"Description" : "eth2",
"GroupSet" : [ { "Ref" : "ICSvManagementSecurityGroup" } ],
"SourceDestCheck" : "false",
"SubnetId" : { "Ref" : "MgmtSubnet" },
"Tags" : [ {"Key" : "Name", "Value" : "Interface 2"}, {"Key" : "Interface", "Value" : "eth2"} ]
}
}
},
"Outputs" : {
"InstanceId" : {
"Value" : { "Ref" : "EC2Instance" },
"Description" : "Instance Id of newly created instance"
},
"ManagementAddress" : {
"Value" : { "Fn::Join" : [" ", [ "Public IP address:", { "Ref" : "EIP2" }, "Private IP address:", { "Fn::GetAtt" : ["Eth2", "PrimaryPrivateIpAddress"] }]]},
"Description" : "ICS Management Interface details"
},
"ExternalAddress" : {
"Value" : { "Fn::Join" : [" ", [ "Public IP address:", { "Ref" : "EIP1" }, "Private IP address:", { "Fn::GetAtt" : ["Eth1", "PrimaryPrivateIpAddress"] }]]},
"Description" : "ICS Extenal Interface details"
},
"InternalAddress" : {
"Value" : { "Fn::Join" : [" ", [ "Public IP address:", { "Ref" : "EIP0" }, "Private IP address:", { "Fn::GetAtt" : ["Eth0", "PrimaryPrivateIpAddress"] }]]},
"Description" : "ICS Internal Interface details"
}
}
}
Registering the AMI
This section describes the steps to register the AMI. This is the one-time activity to be followed to deploy Ivanti Connect Secure on AWS.
To register AMI, do the following:
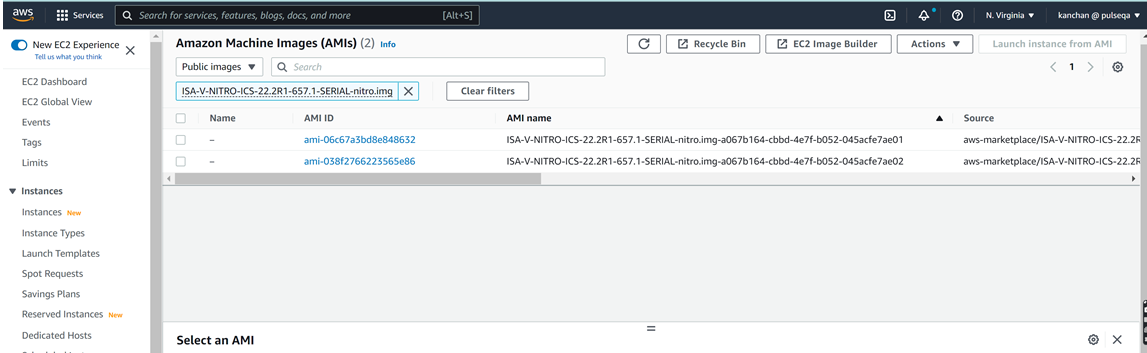
1.Login to AWS Portal.
2.Search for the AMI name in the Public images: ISA-V-NITRO-ICS-22.2R1-657.1-SERIAL-nitro.img. Images can be searched under public AMI section and copy AMI ID for custom deployment using custom templates. To determine AMI for 2 NIC and 3 NIC based on the AMI name or AMI ID, refer to the KB article.
To deploy 2-NIC or 3-NIC in an existing VPC and new VPC respectively using the links above.
ICS gateway AMIs are available in all AWS regions (except China).