NDcPP Mode
Overview
If NDcPP Mode is enabled, then the following changes are applied to ICS/IPS:
•When NDcPP option is enabled, only NDcPP allowed crypto algorithms are allowed.
•Device/Client Auth certificate 3072 bit key length support.
•Not allowing Import of Device/Client Auth Certificate if Respective CAs are not in Trusted Stores.
•Not allowing Importing of Device Certificate without Server Authentication EKU (Extended Key Usage).
•Device/Client Auth/CA certificate revocation check during Certificate Import
•Syslog certificate revocation check during TLS connection establishment.
•Not Allowing 1024 bit Public Key Length Server Certificate from Syslog during TLS connection.
Steps to Setup the ICS/IPS for NDcPP
Prerequisites for ICS/IPS Configurations
•External DNS Server should be able to resolve the hostnames used in the testing
•External Syslog server is up and running.
•External CRL is up and running.
Password Minimum Length Configuration
On Administrator Web Console, follow below instruction to set administrator minimum password length to be 15.
-
Set in Admin Realm:
-
Set in local auth server configuration:
-
Review all previously configured administrator passwords, update to ensure all are at least 15 characters.
1.Navigate to Administrators > Admin Realms
2.Click on Admin Users.
3.Click on the Authentication Policy tab.
4.Click on Password tab
5.Click on Only allow users that have passwords of a minimum length.
6.Enter 15 as Minimum Length.
1.Navigate to Authentication > Auth. Servers.
2.Click on Administrators.
3.On the Settings tab, click on Password Options section.
4.Configure 15 characters as Minimum length.
5.Configure Maximum Length greater than or equal to 15 characters set as Minimum Length
Serial Console Access Control Configuration
Configure administrator access control for the local serial console is a two-step process.
-
Enable allow console access for the administrator, In Administrator Web Console.
-
Enable password protection for the console.
1.Go to Authentication > Auth. Servers
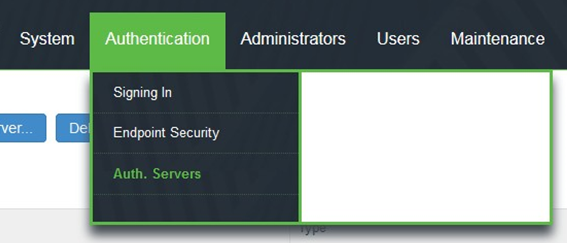
2.This screen is shown.
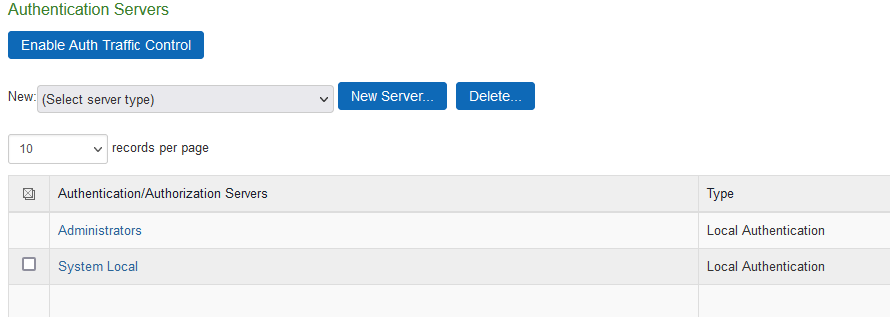
3.Select Administrators.
4. Click on Users tab.
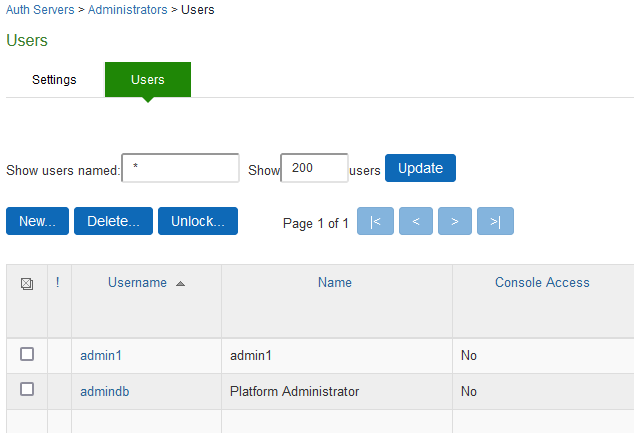
5.Click on administrator name configured in Initial Setup
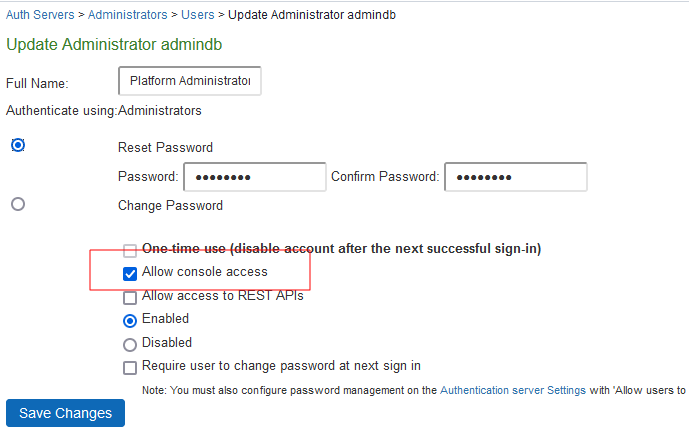
6.Click on the Allow console access checkbox
7.Click on Save Changes.
1.Connect to the local serial console, the serial console menu is shown as below.
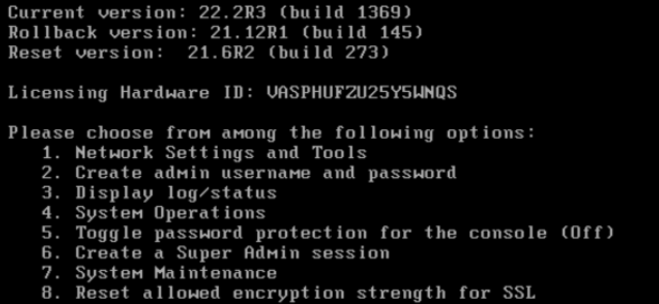
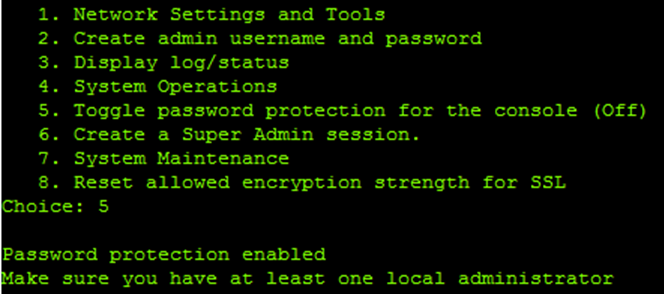
2.Choose option 5 on the local serial console. You should see a confirmation: “Password protection enabled, make sure you have at least one local administrator”.
Terminating a Local Console Session
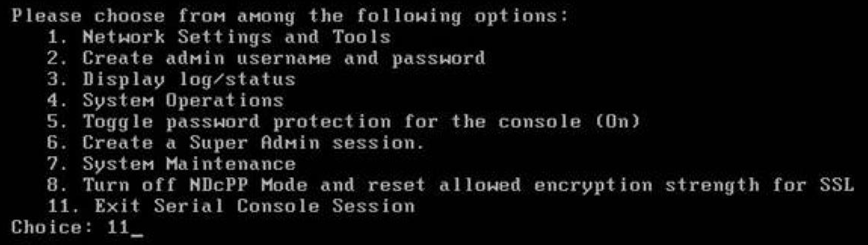
To exit a console session, choose option 11 on the local serial console.
Administrative Banner Configuration
Configuring administrator banner for the Administrator Web Console and the local serial console is a two-step process.
-
Create a Sign-in notification. On Administrator Web Console :
-
Associate the notification with an admin URL. On Administrator Web Console,
1.Navigate to Authentication > Signing In > Sign-in Notifications
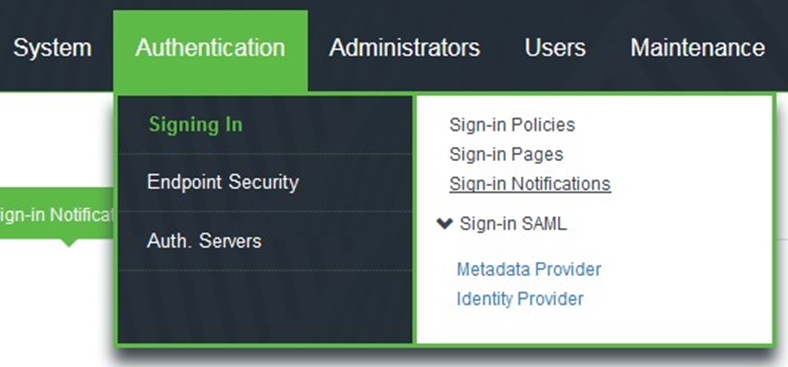
2.This screen is shown
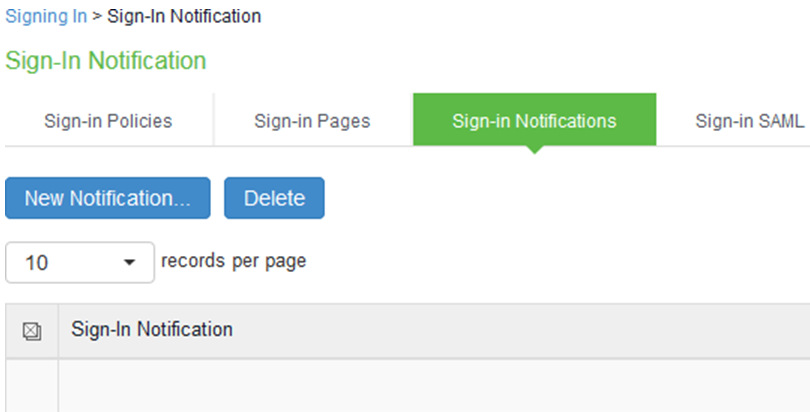
3.Click on New Notification
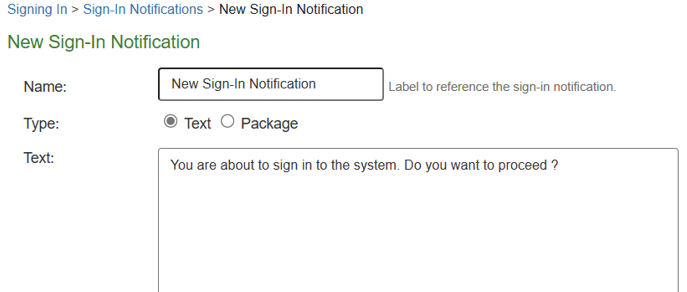
4.Enter a name for the new notification in the Name:
5.In Type:, select Text
6.Enter banner message in the Text:
7.Click on Save Changes
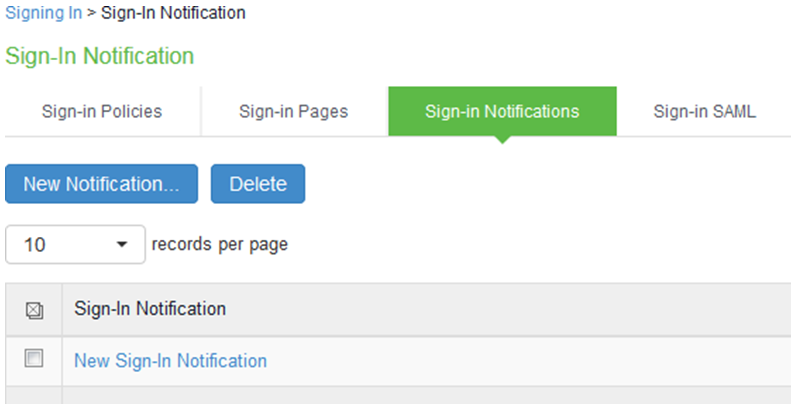
1.Navigate to Authentication > Signing In > Sign-In Policies
2.Click on admin URL */admin/
3.In the Configure SignIn Notifications section, select the check box Pre-Auth Sign-in Notification.
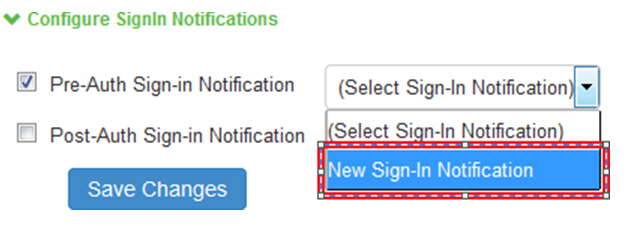
4.A drop down box appears next to Pre-Auth Sign-in Notification once it is selected, in the drop down box, select the notification you created in Step 1 above.
5.Click on Save Changes
Configure GUI Inactivity Timeout Period
1.Navigate to Administrators > Admin Roles > <Role Name> > Session Options
2.Under the Session lifetime section, enter the Idle timeout in minutes.
Terminating a GUI Session
To log out of the web administrative session, on any screen click on the “Sign Out” link at the top right of the screen.
Import Trusted Client CA
Trusted Client CA is required to validate the client certificate that is used by the ICS/IPS to authenticate to syslog server.
On Administrator Web Console,
1. Navigate to System > Configuration > Certificates > Trusted Client CAs
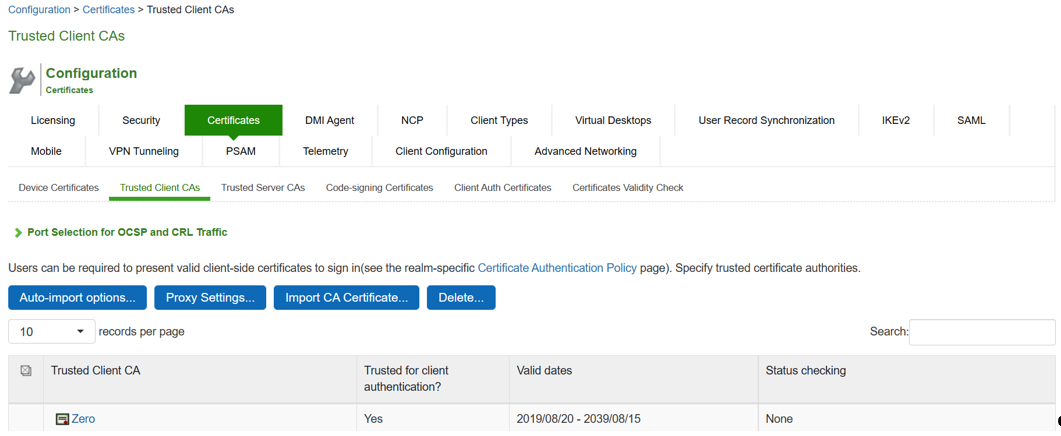
2.Click Import CA Certificates… button to import CA or Chain of CAs one by one as explained below in different Screenshots.
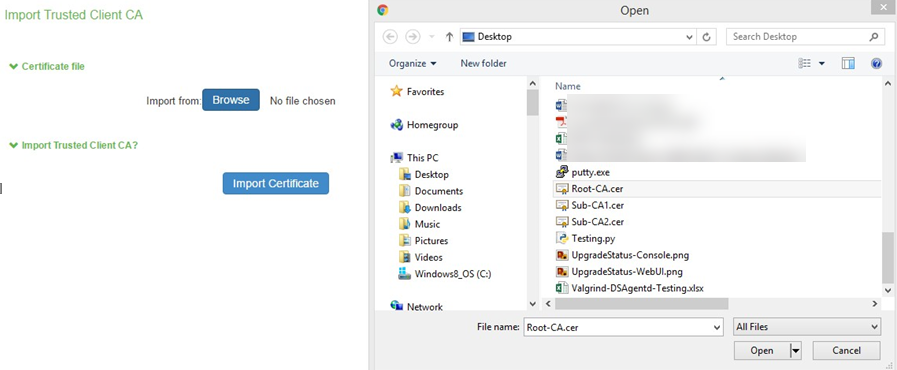
3.Click on Import Certificate.
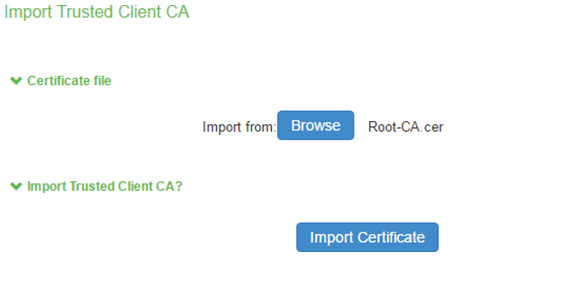
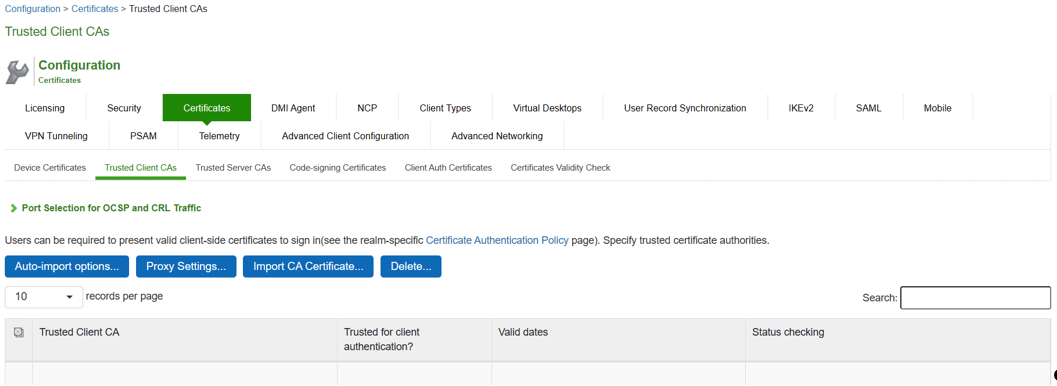
4.The imported trusted client CA is shown in the Trusted Client CAs table
Import Trusted Server CA
Trusted Server CA is used in two situations:
•To validate the device certificate that is generated for TLS handshake when a TLS client is connecting to the ICS/IPS.
•To validate the server certificate received in TLS handshake when the ICS/IPS connects to syslog server and Pulse One.
1.On Administrator Web Console, navigate to System > Configuration > Certificates > Trusted Server CAs.
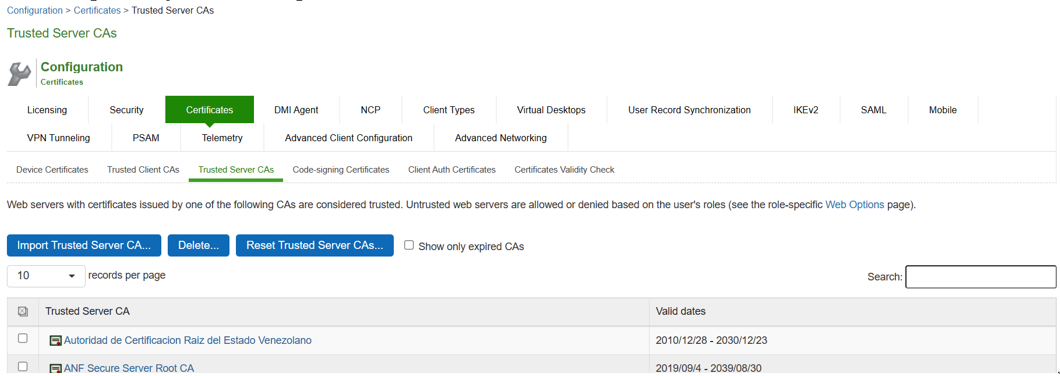
2.Click on Import Trusted Server CA…
3.On the Import Trusted Server CA screen, click on Browser, import the root CA certificate file.

To import CA Chain, all Sub CAs must be imported one by one.
4.Once CA or CA Chain is Imported, click Done
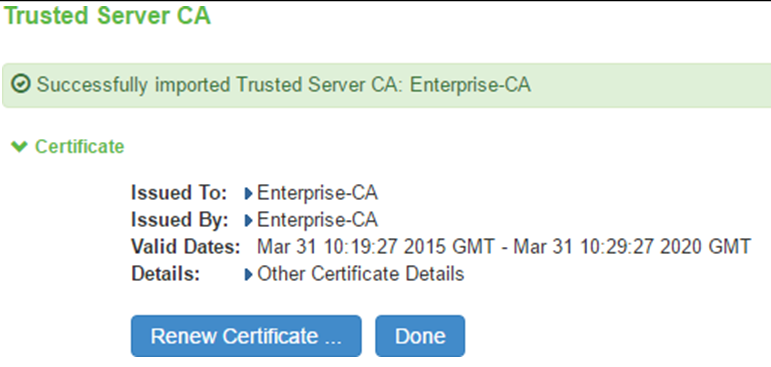
5.The CA Common Name of the imported trusted server CA should be shown in the Trusted Server CA table on screen System > Configuration > Certificates > Trusted Server CAs.

The CRL configured in the certificate is used, thus no additional configuration is required to configure CRL for trusted server certificate.
Software Updates
If a new NDcPP compliant software package is available, follow instructions in this section to update the software package on the ICS/IPS. The verification of the authenticity of the software package is performed by digital signature verification.
1.Download the ICS/IPS software package from Pulse Secure Licensing and Download Center onto a trusted computer system.
2.On Administrator Web Console, navigate to Maintenance > System > Upgrade/Downgrade.
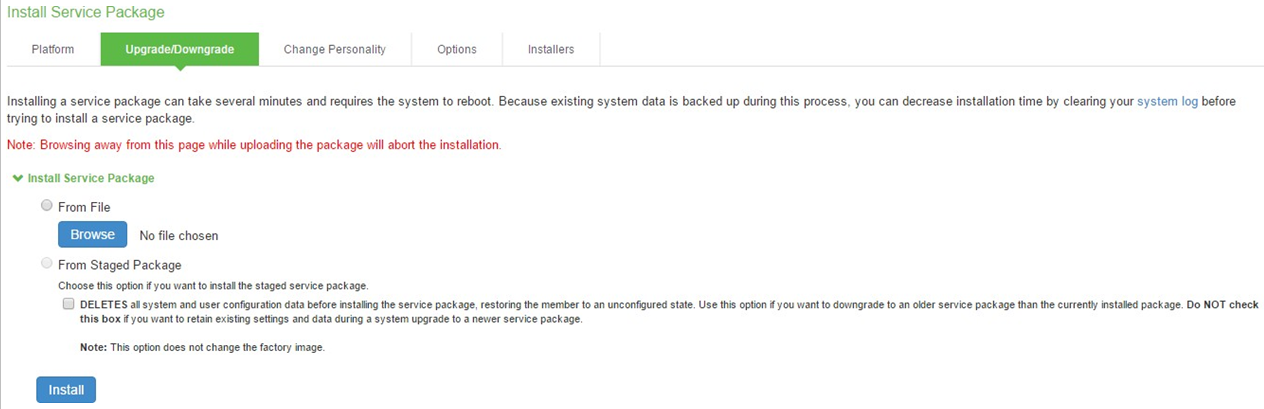
3.In the expanded Install Server Package section, click on From File option, then click on Browse to select the server package downloaded earlier.
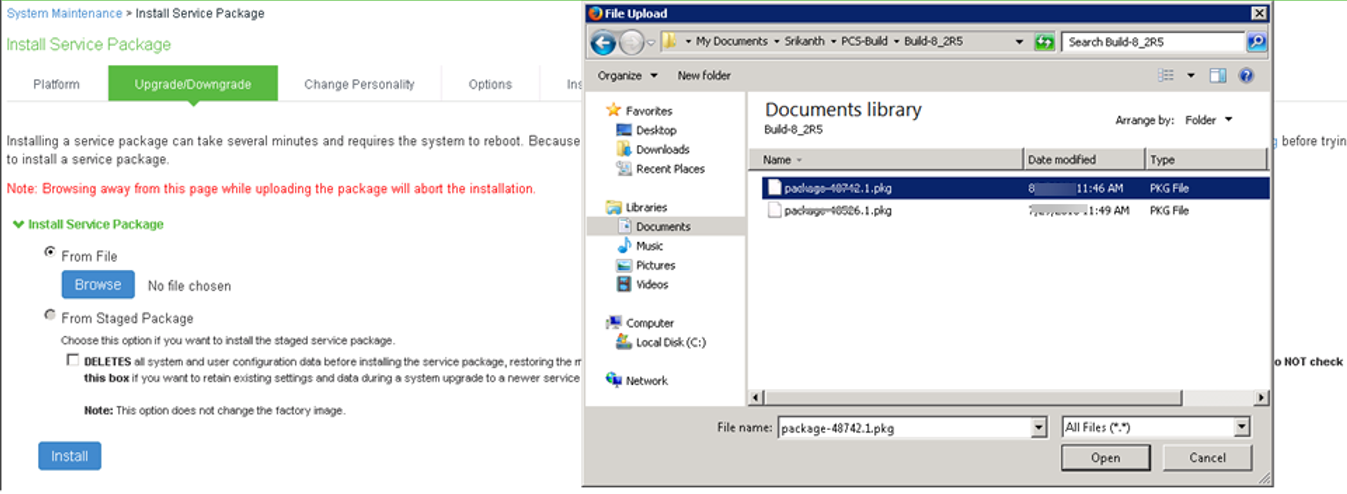
4.Click Install to start the installation process.
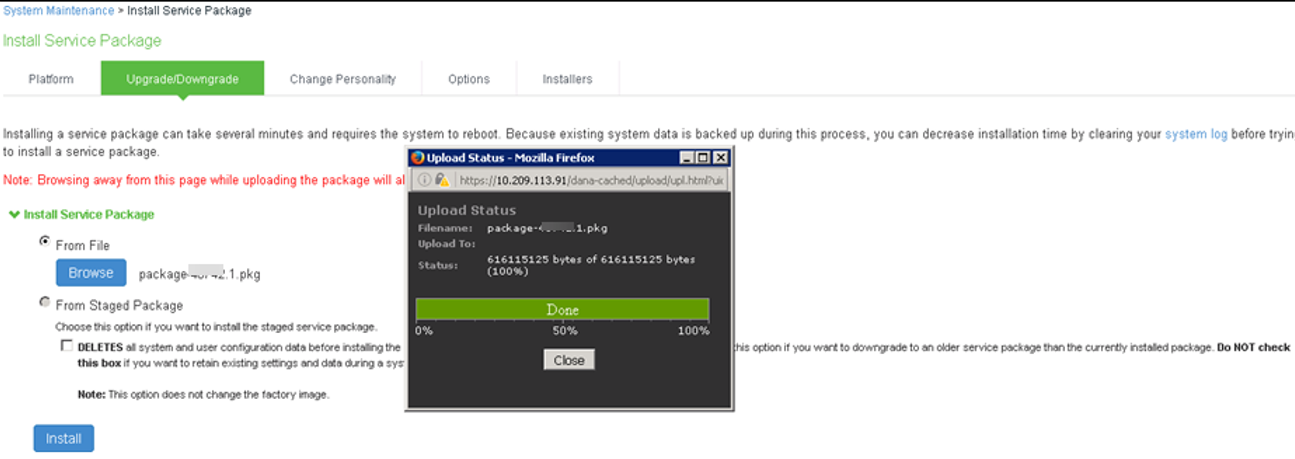
5.Below information is shown during installation.
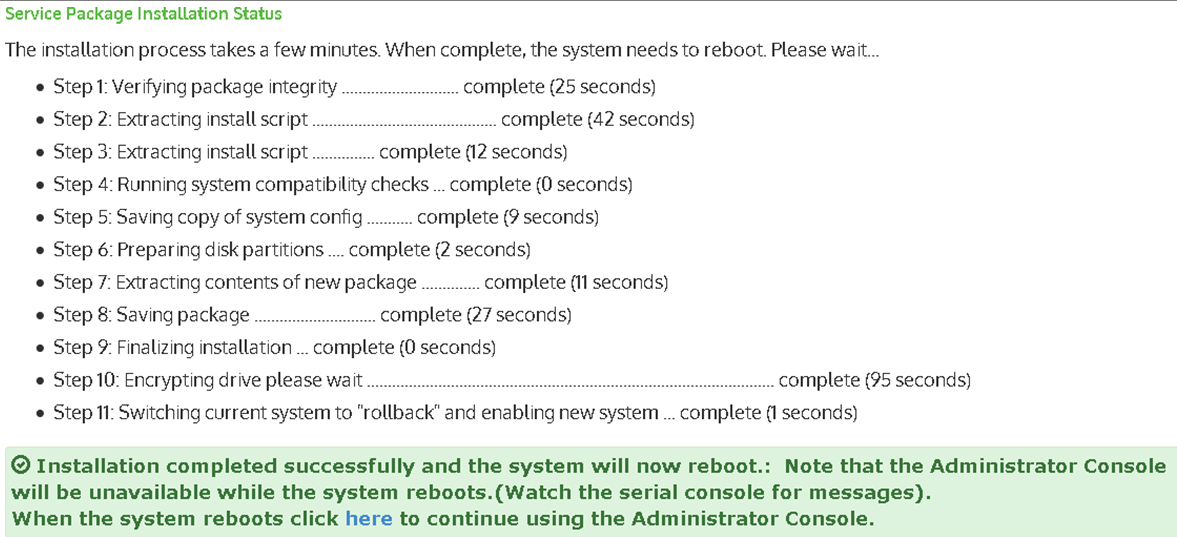
6.Confirm current software version
After system boot up, go to System Maintenance > Platform screen, verify Current version: displays the correct software version.
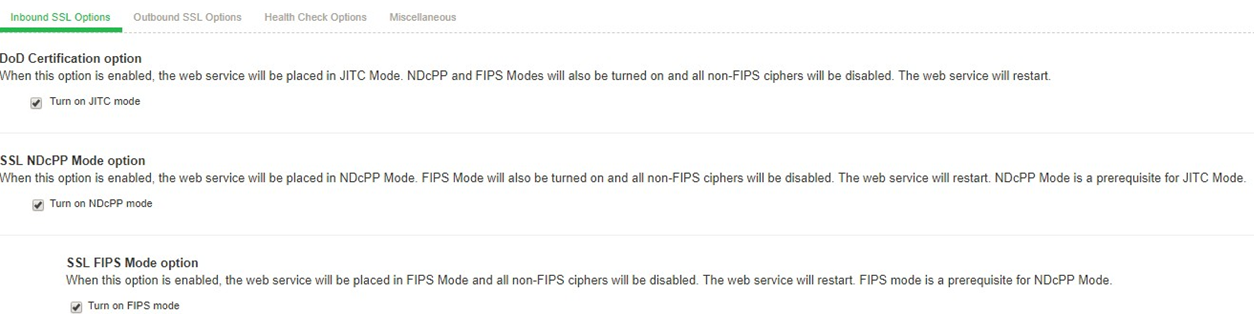
Enabling NDcPP Mode
On Administrator Web Console,
-
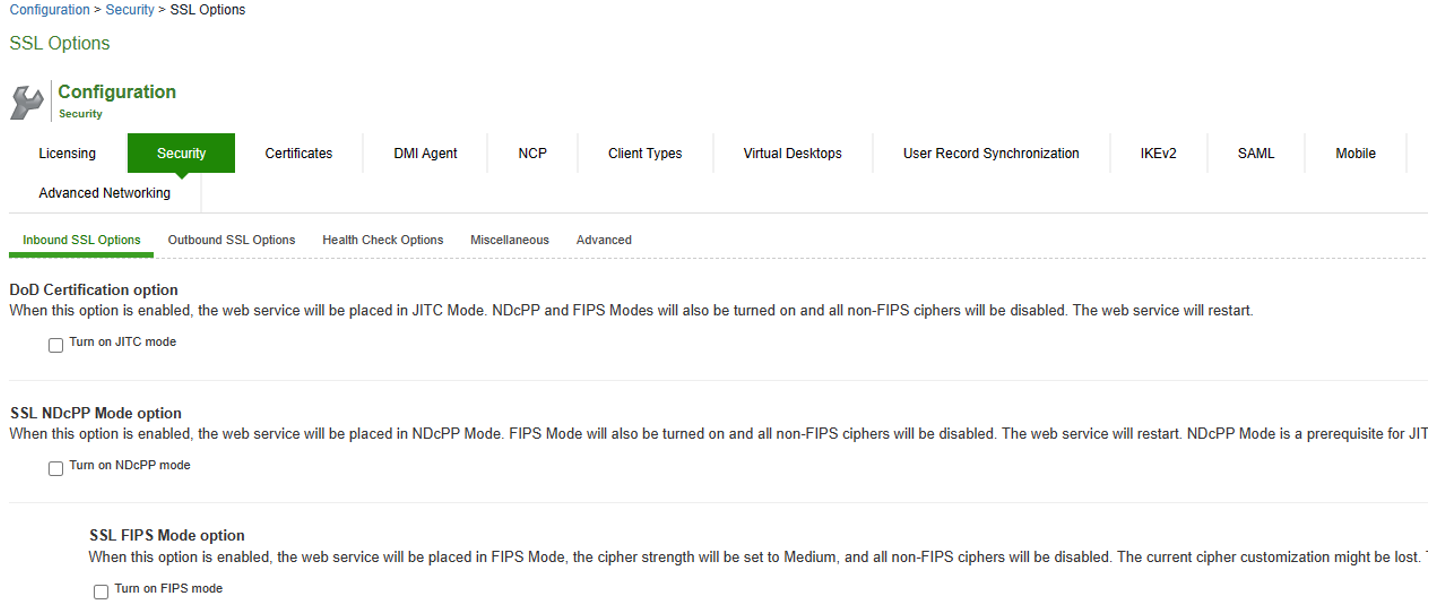
Navigate to System > Configuration > Security > Inbound SSL Options.
-
Click on the Turn on NDcPP mode checkbox highlighted to make the ICS/IPS common criteria compliant
-
Once Turn on NDcPP mode is enabled, Turn on FIPS mode is also automatically enabled.
-
Enable the Use 2048 bit Diffie-Hellman key exchange checkbox.
-
Uncheck SSL Legacy Renegotiation Support option.
-
Click on Save Changes.
-
At this point, the Turn on NDcPP mode is enabled for both Inbound SSL Options and Outbound SSL Options and the following is shown:
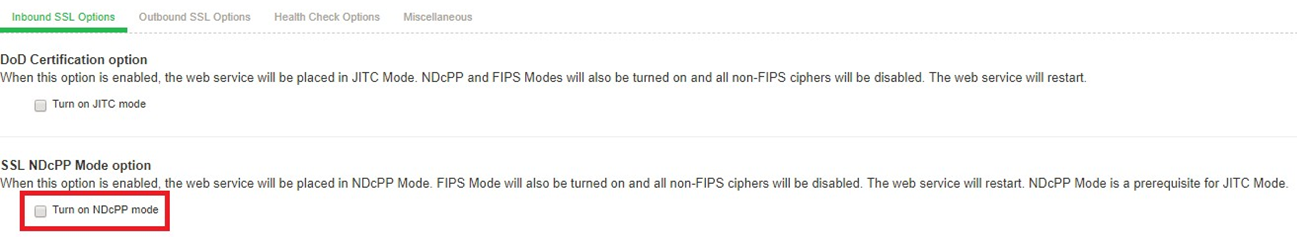


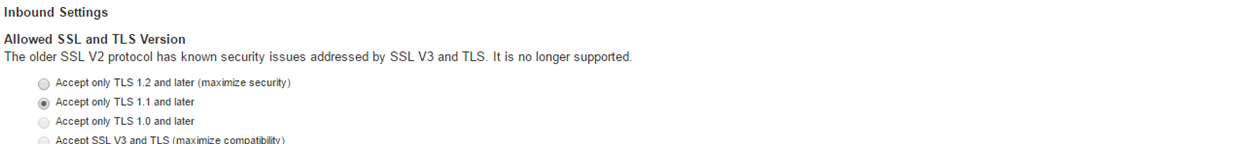
1.Accept only TLS1.0 and later and Accept SSL V3 and TLS (maximize compatibility) are disabled in the NDcPP mode. Accept only TLS 1.1 and later is selected by default.
2.Custom SSL Cipher Selection Allowed Encryption Strength are automatically selected. Click on Show Selected Ciphers displays below 16 Ciphers in the right panel labelled Selected Cipher.
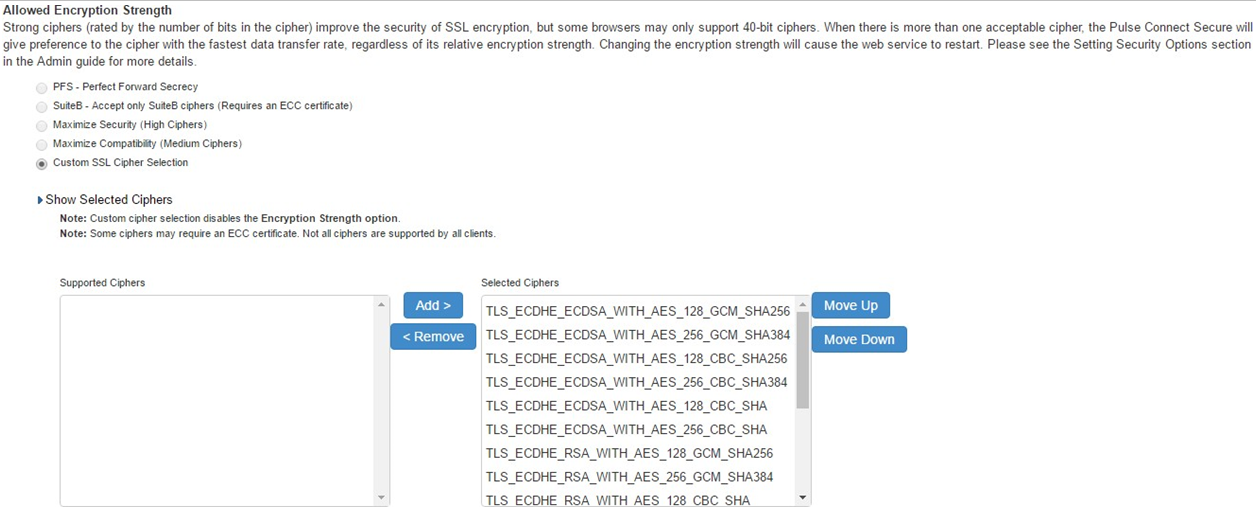
3.Select TLS_DHE_RSA_WITH_AES_128_CBC_SHA and TLS_DHE_RSA_WITH_AES_256_CBC_SHA on the right panel, and click “Remove” button to remove it from the “Selected Ciphers”.
4.Navigate to System > Configuration > Security > outbound SSL Options
5.Custom SSL Cipher Selection Allowed Encryption Strength are automatically selected. Click on Show Selected Ciphers displays below 16 Ciphers in the right panel labelled Selected Cipher.
6.Select TLS_DHE_RSA_WITH_AES_128_CBC_SHA and TLS_DHE_RSA_WITH_AES_256_CBC_SHA on the right panel, and click “Remove” button to remove it from the “Selected Ciphers”.
8. Optionally, you may check below log to confirm NDcPP mode is enabled:
Navigate to System > Log/Monitoring > Admin Access > Logs and Check for the Logs mentioned in the section NDcPP Mode Enable Configuration Admin Logs
9. Optionally, you may check below log to confirm that DHE2048 Key Exchange Option is enabled:
Navigate to System > Log/Monitoring > Admin Access > Logs and Check for the Logs mentioned in the section DH2048 Key Exchange Enable Configuration Admin Logs.
Audit Logs for NDcPP Mode
NDcPP Mode Enable Configuration Admin Logs
Configuration change to enable NDcPP mode on the ICS/IPS
|
Info |
ADM23434 |
<current timestamp> <node name> <IP Address> <user id> <Realm> <Role> – Allowed SSL and TLS changed from ‘TLSv1 and above’ to ‘TLS1.1 and above’. |
|
Info |
ADM31354 |
<current timestamp> <node name> <IP Address> <user id> <Realm> <Role> – Changed Allowed Encryption Strength from <ciphersuite> to <ciphersuite>. |
|
Info |
ADM30965 |
<current timestamp> <node name> <IP Address> <user id> <Realm> <Role> – FIPS mode is now turned on. The web server will restart. |
|
Info |
ADM31273 |
<current timestamp> <node name> <IP Address> <user id> <Realm> <Role> – NDcPP mode is now turned on. The web server will restart. |
NDcPP Mode Disable Configuration Admin Logs
Configuration change to disable NDcPP mode on the ICS/IPS.
|
Info |
ADM31273 |
<current timestamp> <node name> <IP Address> <user id> <Realm> <Role> – NDcPP mode is now turned off. The web server will restart. |
DH2048 Key Exchange Enable Configuration Admin Logs
Configuration change to enable DH2048 Key Exchange Option on the ICS/IPS.
|
Info |
ADM31287 |
<current timestamp> <node name> <IP Address> <user id> <Realm> <Role> – DHE2048 option is now enabled |