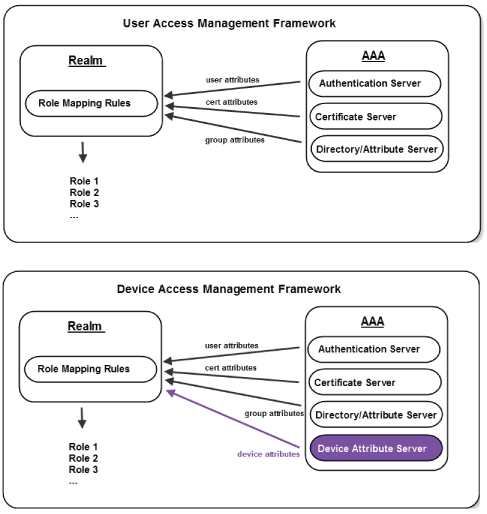
Understanding the Device Access Management Framework
In this framework, the MDM is a device authorization server, and MDM record attributes are the basis for granular access policy determinations. For example, you can implement policies that allow devices that have a clean MDM posture assessment and are compliant with MDM policies to access the network, but deny access to servers when you want to prevent downloads to employee-owned devices or to a particular platform that might be vulnerable. To do this, you use the device attributes and status maintained by the MDM in Ivanti Secure Access Client role-mapping rules, and specify the device-attribute-based roles in familiar Ivanti Secure Access Client policies.
The framework simply extends the user access management framework realm configuration to include use of device attributes as a factor in role mapping rules. The following figure illustrates the similarities.
The following table summarizes vendor support for this release.
|
Product |
Vendor |
|
Pulse Workspace (PWS) AirWatch MDM MobileIron MDM Microsoft Intune |
|
Table summarizes supported methods for determining the device identifiers.
|
Product |
Policies |
|
Device certificate (required) |
The following table summarizes policy reevaluation features.
|
Product |
Policy Reevaluation |
|
The MDM is query and policies evaluated only during sign-in. If desired, you can use the user role session timeout setting to force users to sign in periodically. If you use a certificate server for user authentication, the users are not prompted to sign in again; however, if you have enabled user role notifications, users do receive a notification each time sign-in occurs. |
The dynamic policy evaluation feature is not used in the device access management framework.
The following table summarizes the policies in which you can specify device-attribute-based roles.
|
Product |
Policies |
|
Resource policies or resource profiles |
Solution Overview
In the past, to ensure security and manageability of the corporate network, enterprise information technology (IT) departments had restricted network access to company-issued equipment. For mobile phones, the classic example was the company-issued BlackBerry handset. As powerful mobile smart phones and tablets have become commonly held personal possessions, the trend in enterprise IT has been to stop issuing mobile equipment and instead allow employees to use their personal smart phones and tablets to conduct business activities. This has lowered equipment costs, but BYOD environments pose capacity planning and security challenges: how can an enterprise track network access by non-company-issued devices? Can an enterprise implement policies that can restrict the mobile devices that can access the network and protected resources in the same way that SSL VPN solutions restrict user access?
MDM vendors have emerged to address the first issue. MDMs such as AirWatch, MobileIron, Microsoft Intune provide enrollment and posture assessment services that prompt employees to enter data about their mobile devices. The MDM data records include device attributes and posture assessment status that can be used in the access management framework to enforce security policies.
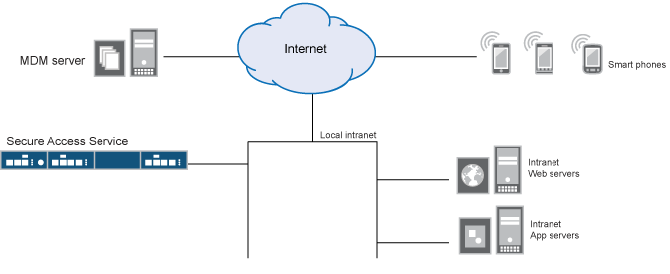
The following figure shows a deployment with Ivanti Connect Secure and the MDM cloud service.
The solution shown in this example leverages the Ivanti access management framework to support attribute-based network access control for mobile devices. In the device access management framework, the MDM is a device authorization server and MDM record attributes are the basis for access policy determinations. For example, suppose your enterprise wants to enforce a policy that allows access only to mobile devices that have enrolled with the MDM or are compliant with the MDM posture assessment policies. You can use the attributes and status maintained by the MDM in role-mapping rules to implement the policy.
In this framework, a native supplicant is used to authenticate the user of the device. The device itself is identified using a client certificate that contains device identity. The client certificate can be used to identify the device against the MDM records and authenticate the user against a certificate server.
The Ivanti solution supports granular, attribute-based resource access policies. For example, you can implement policies that allow devices that have a clean MDM posture assessment and are compliant with MDM policies to access the network, but deny access to servers when you want to prevent downloads to employee-owned devices or to a particular platform that might be vulnerable.