Encryption
Using older unauthorized versions or incorrectly configuring protocol negotiation makes the gateway vulnerable to known and unknown attacks that exploit vulnerabilities in this protocol.
The implementation of TLS 1.3 is highly recommended due to its speed and security benefits when compared to the previous versions as it does not support vulnerable ciphers.
•Benefits of TLS 1.3, include faster connection setup and the absence of support for vulnerable ciphers, making it a secure choice for modern applications.
•Disabling Older Protocols: It is recommended to disable older TLS protocols in favor of TLS 1.3 to leverage its security enhancements and performance improvements.
•Server Name Indication: Extension of SNI in TLS 1.3, which conceals the domain connected to, enhancing privacy and security, especially behind networks like Cloudflare.
The ICS must be configured to use TLS 1.2, at a minimum.
1.In the ICS Web UI, navigate to System > Configuration > Inbound SSL Options.
2.Under Allowed SSL and TLS Version, check the box for Accept only TLS 1.2 (maximize security).
3.Click Save Changes.
4.Click Proceed for acceptance of Cipher Change.
5.Under Allowed Encryption Strength, select maximize security.
Navigate to System > Configuration > Outbound SSL Options.
1.Under Allowed SSL and TLS Version, check the box for Use TLS 1.2 and later (maximize security).
2.Click Save Changes.
3.Click Proceed for acceptance of Cipher Change.
4.Under Allowed Encryption Strength, select maximize security.
Enable TLS1.3
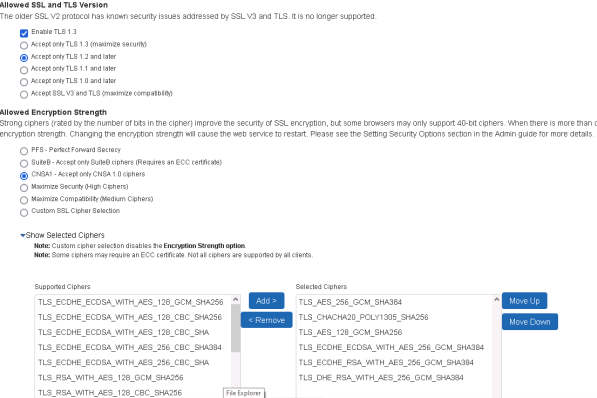
Re-order (top down) the preferred ciphers in the list so that the most required cipher is at the top of the selected list.