Deployment Scenarios
Cloud Secure uses Security Assertion Markup Language (SAML) for exchange of authentication information between client device (Mobile, Desktops, and other devices), Service Provider (Cloud applications such as O365, salesforce and so on) and Identity Provider (Ivanti Connect Secure) to provide SSO.
Single Sign-On, using SAML is classified into IdP initiated and SP Initiated scenarios:
•SP initiated scenario - The user tries to access the application, the cloud service triggers SAML authentication requests and redirects them to IdP for authentication.
•IdP initiated scenario - The user first authenticates with Identity provider before accessing the cloud service.
This section describes the following deployment scenarios:
•Deployment using Web Browser SSO Profile
•Deployment using Enhanced Client or Proxy (ECP) Profile
•Deployment using Third-Party IdP
•Deployment for On-Premise Users
Deployment using Web Browser SSO Profile
In SAML Web Browser SSO Profile, an endpoint web browser is used to exchange SAML messages between endpoint, Service Provider (SP), and Identity Provider (IdP). The web browser requests for a service from the SP. As part of the authentication flow, Service Provider requests and receives an identity assertion from the Identity Provider through the web browser. Before providing identity assertion to SP, the IDP requests the user to enter the user credentials for authentication.
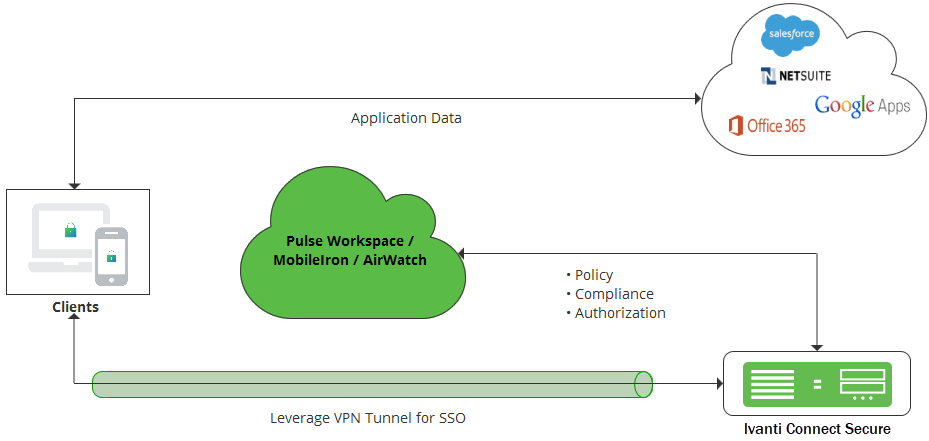
For web browser SSO, Ivanti Secure Access Client on mobile or desktop is used to deliver strong authentication and device compliance check. On mobile devices, cloud applications can be configured with per-app VPN client which is launched automatically when cloud application tries to access cloud service. On desktop, Ivanti Secure Access Client may be connected manually by an end user. On mobile devices, users authenticate using certificates to eliminate the need to enter password. For mobile device compliance check, Pulse Workspace or Third-Party MDM servers such as MobileIron or AirWatch is used. Ivanti Secure Access Client host checker is used for desktop device’s compliance check. Once authentication and compliance check are completed successfully, application data flows directly between the endpoint and the Service Provider.
Deployment using Enhanced Client or Proxy (ECP) Profile
The Enhanced Client or Proxy (ECP) is similar to web browser SSO, but it is designed for applications other than web browsers. The SP and IdP communicate directly instead of exchanging SAML messages over user’s web browser.
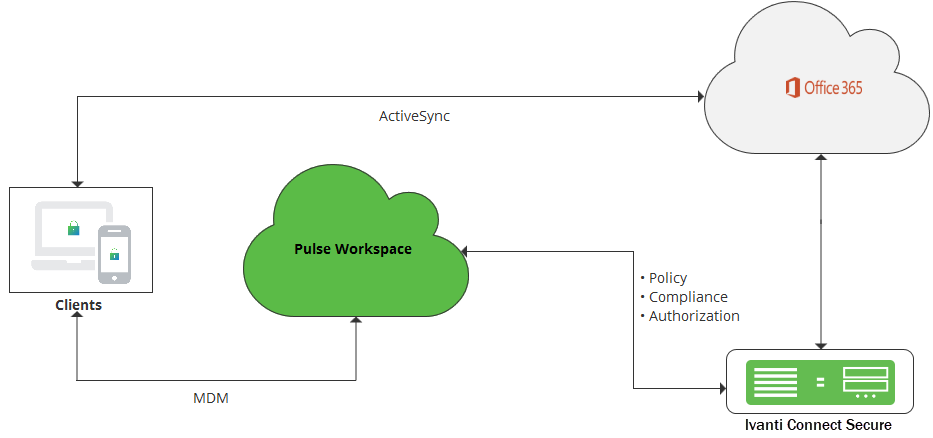
The native outlook applications on mobile devices use ECP profile (unlike web browser SSO profile) for authentication. For ECP profile, Cloud Secure solution uses the unique token generated by Pulse Workspace for authentication and to retrieve device compliance details. As part of the mobile device registration, Pulse Workspace generates and provisions unique token to mobile device. Once mobile device gets registered, the native outlook application is automatically provisioned to connect to Office 365 using the username and unique token. This generates a login request to Office 365. Upon receiving a login request, Office 365 delegates the authentication responsibility to Ivanti Connect Secure by providing user name and unique token through ECP. Ivanti Connect Secure verifies the user and checks the device compliance through PWS using this unique token. Once authentication and compliance check are successful, Ivanti Connect Secure provides an assertion to Office 365, which provides an email access to native outlook application.
Deployment using Third-Party IdP
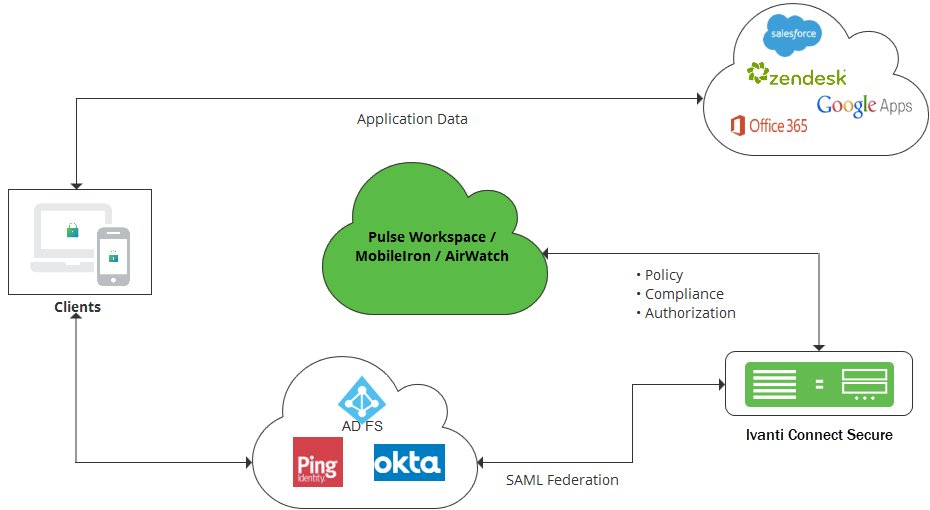
Cloud Secure also provides Secure Single Sign-On for cloud services by integrating with Third-Party Identity Providers. Cloud Secure supports integration with Third-Party IdPs such as Ping One, Okta and Microsoft AD FS.
For Cloud Secure Solution, the Third-Party IdPs act as both IdP (for cloud services) and SP (for Ivanti Connect Secure acting as IdP). Third-Party IdPs allow Ivanti Connect Secure to be configured as external SAML Identity Provider to authenticate users and enable secure Single Sign-On to cloud applications.
Deployment for On-Premise Users
Cloud Secure provides Single Sign-On access to cloud services for On-Premise users authenticated to Ivanti Policy Secure after compliance posture assessment. On premise users are authenticated by Ivanti Policy Secure when they are connected to enterprise network. Ivanti Policy Secure exports this session to Federation server through IF-MAP federation capability. Ivanti Connect Secure acts as Federation client and imports session information from Federation Server and uses this imported session information to generate SAML assertions to provide access to On-Premise users. This eliminates users providing credentials again with every application access.
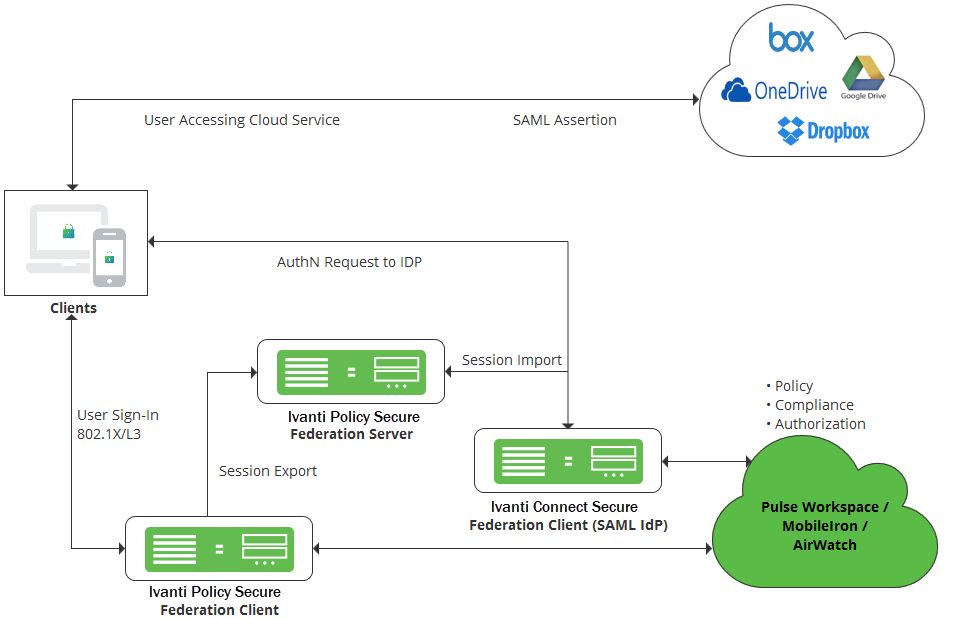
IF-MAP Federation is used for session sharing between Ivanti Policy Secure and Ivanti Connect Secure.
On-Premise user SSO Flow
1.User Sign-In: On-Premise users authenticate to Ivanti Policy Secure (Federation Client) via Ivanti Secure Access Client or native supplicant. As part of this 802.1x authentication, compliance check will be performed before granting access to the user.
In case of mobiles, user connects to SSID (SSID settings will be pushed from Pulse Workspace) and authenticates with Ivanti Policy Secure using certificate authentication. Ivanti Policy Secure uses Pulse Workspace return attributes for mobile compliance checks before granting access.
2.Session Export: Since Ivanti Policy Secure is configured as Federation Client, IF-MAP session information will be exported to Federation Server
3.Access Cloud Service: User accesses cloud service enabled with Single Sign-On
4.AuthN Request: Ivanti Connect Secure acting as SAML IdP and Federation Client will receive the SAML Authentication Request
5.Session Import: On receiving SAML AuthnRequest, since Ivanti Connect Secure is configured to use existing VPN session and existing IF-MAP imported session, it will initially check for a local VPN session. If not found, Ivanti Connect Secure will import the IF-MAP session from Federation Server.
SAML Assertion: Ivanti Connect Secure will use this imported session information to generate SAML response/assertion and sends it to cloud service thus providing SSO access to On-Premise users.