Appendix A: Network Security Group (NSG)
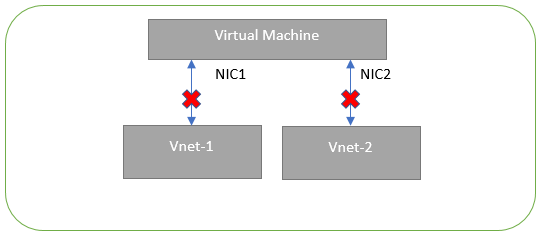
Microsoft Azure has a limitation where virtual machine with multiple network interfaces cannot connect to different Virtual Networks (VNETs). For example, a VM with two NIC cards, NIC1 and NIC2, will not be able to connect to Vnet1 and Vnet2 respectively.
Virtual Machine with two NIC cards Connecting to VNet1 and Vnet2
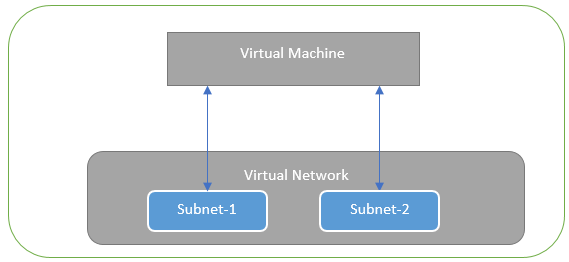
Microsoft Azure supports a virtual machine with multiple NICs to connect to different Subnets under a same Virtual Network. For example, a VM with two NICs, NIC1 and NIC2, can connect to ‘Subnet1’ and ‘Subnet2’ where these subnets exist under a same Virtual Network respectively.
Virtual Machine with two NICs Connecting to Subnet1 and Subnet2
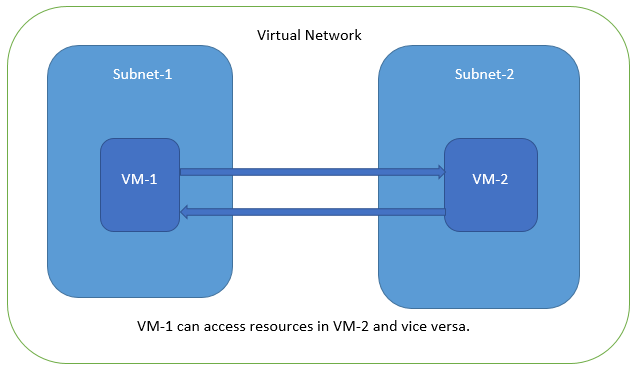
Azure provides isolation between different Vnets. But it does not provide the same kind of isolation when it comes to subnets in the same Vnet. For example, consider a Vnet has two subnets, Subnet1 and Subnet2. And consider two VMs, VM-1 and VM-2, which are connected to Subnet1 and Subnet2 respectively. In this scenario VM-1 can access the resources from VM-2 and vice versa.
Virtual Machine VM-1 can Access Resources in VM-2 and Vice Versa
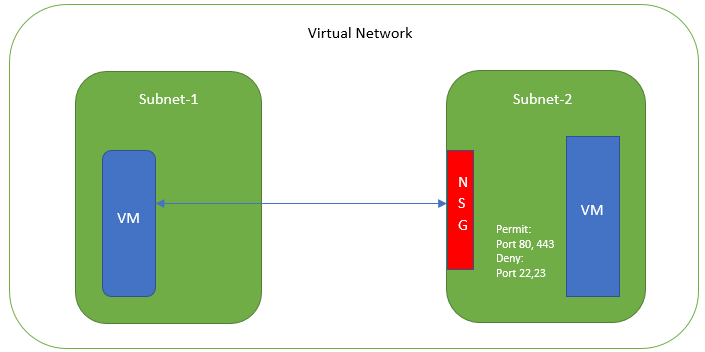
Application isolation is an important concern in enterprise environments, as enterprise customers seek to protect various environments from unauthorized or unwanted access. To achieve the traffic isolation between subnets, go for an option of filtering traffic using “Network Security Group” provided by Azure.
Traffic Filtering by MS Azure Network Support Group
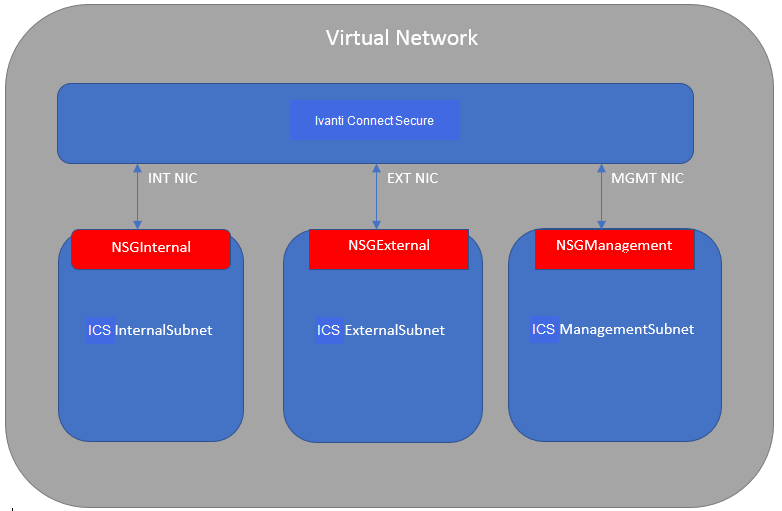
Ivanti Connect Secure, when provisioned through the ARM template provided by Ivanti , creates four subnets under a virtual network named “ICSVirtualNetwork”. The four Subnets are:
1.ICSInternalSubnet
2.ICSExternalSubnet
3.ICSManagementSubnet
4.ICSTunnelVPNPoolSubnet
Along with above mentioned subnets, create the following three Network Security Groups (NSG) policies:
1.NSGExternalSubnet
2.NSGInternalSubnet
3.NSGManagementSubnet
NSG External, Internal and Management Subnets
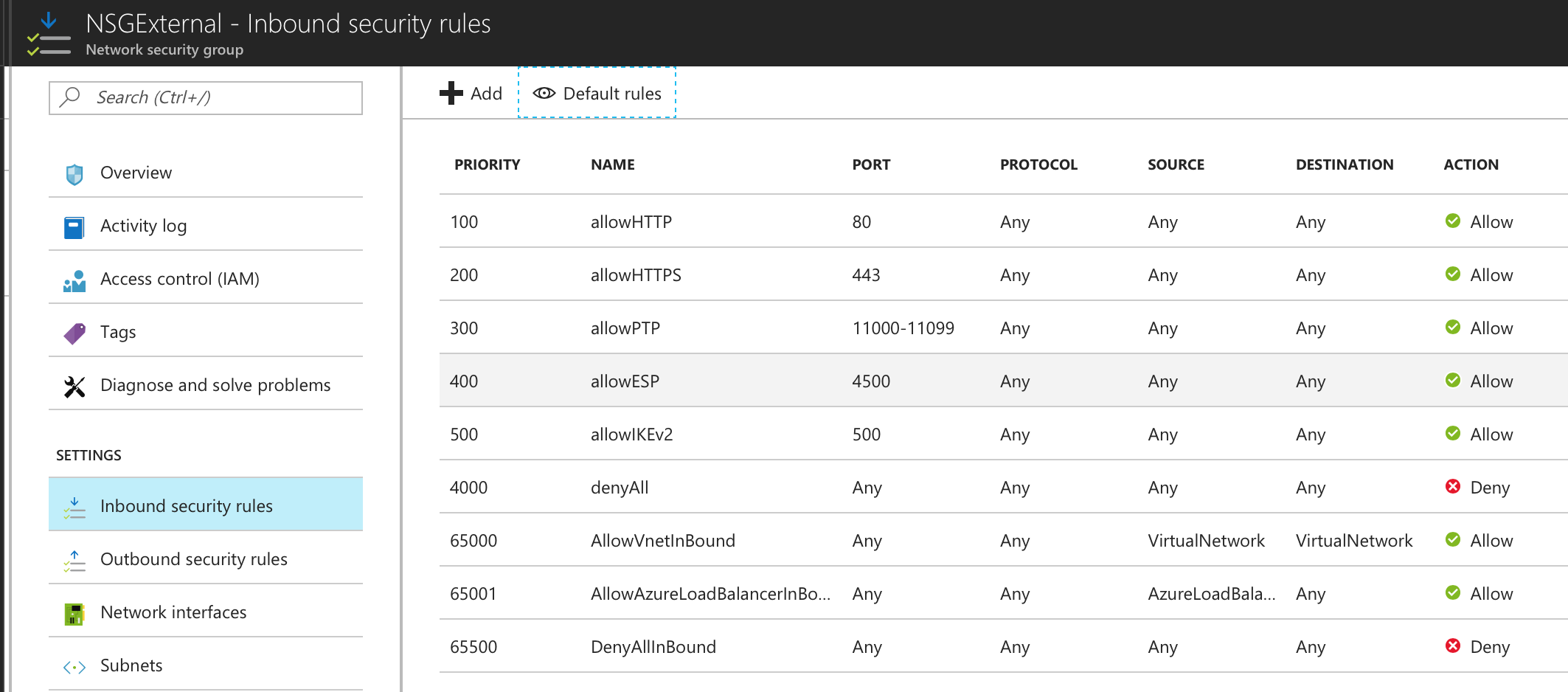
In Network Security Group (NSG) we need to create policies for Inbound and outbound traffic.
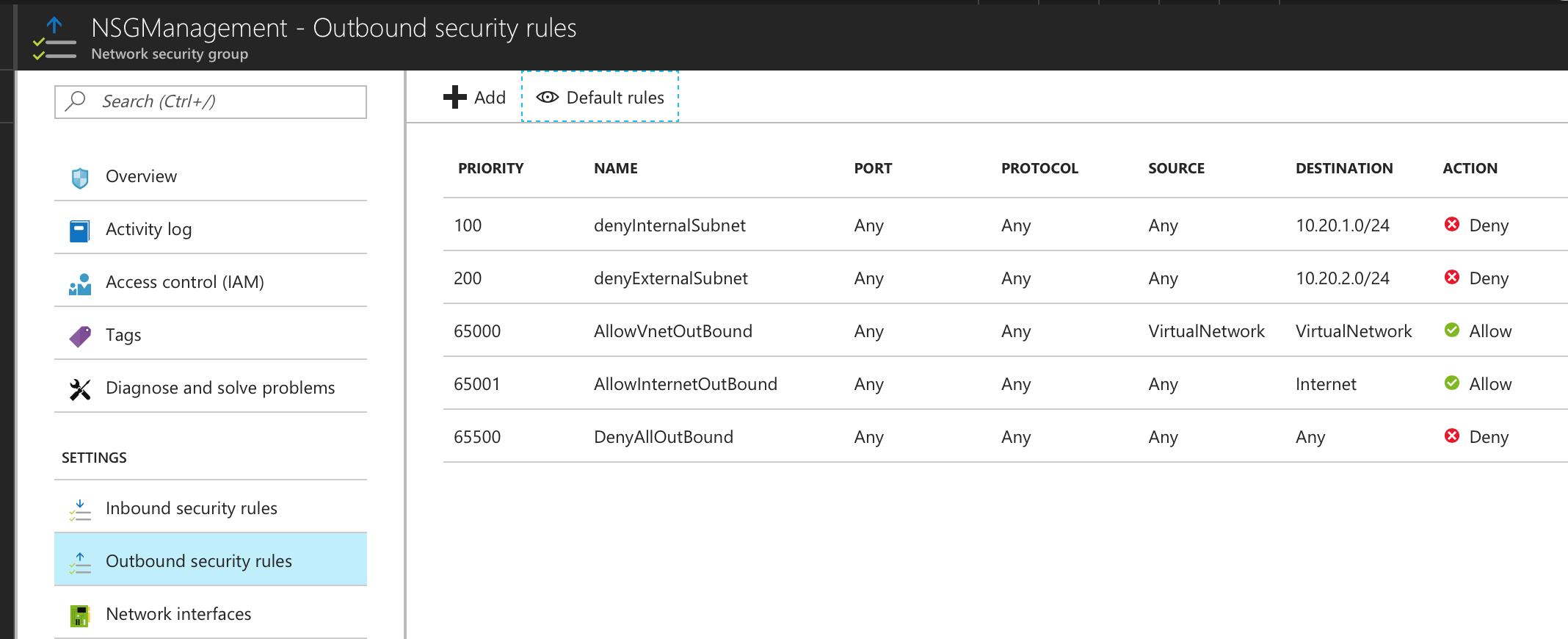
The list of NSG Inbound/Outbound rules created “NSGExternalSubnet” are:
•NSG External - Inbound Rules
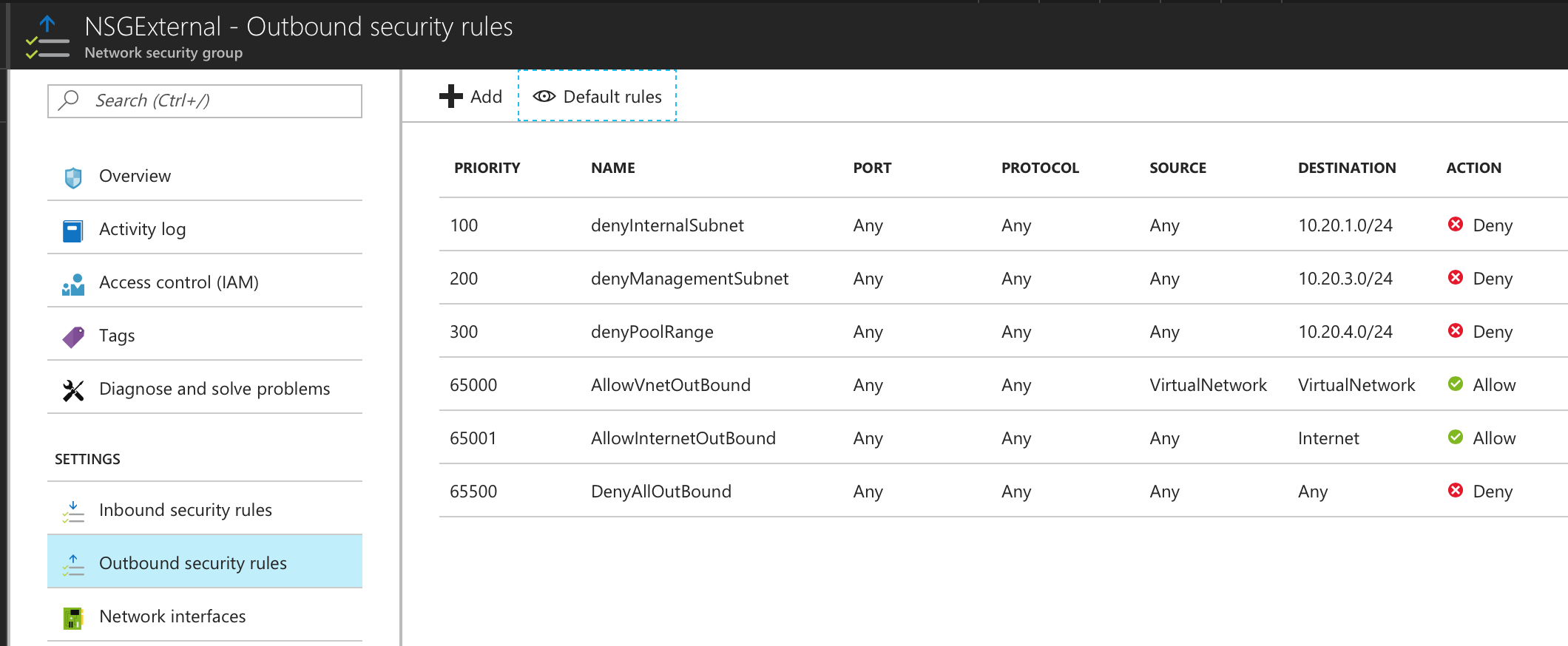
•NSG External - Outbound Rules
The list of NSG Inbound/Outbound rules created “NSGInternalSubnet” are:
•NSG Internal - Inbound Rules
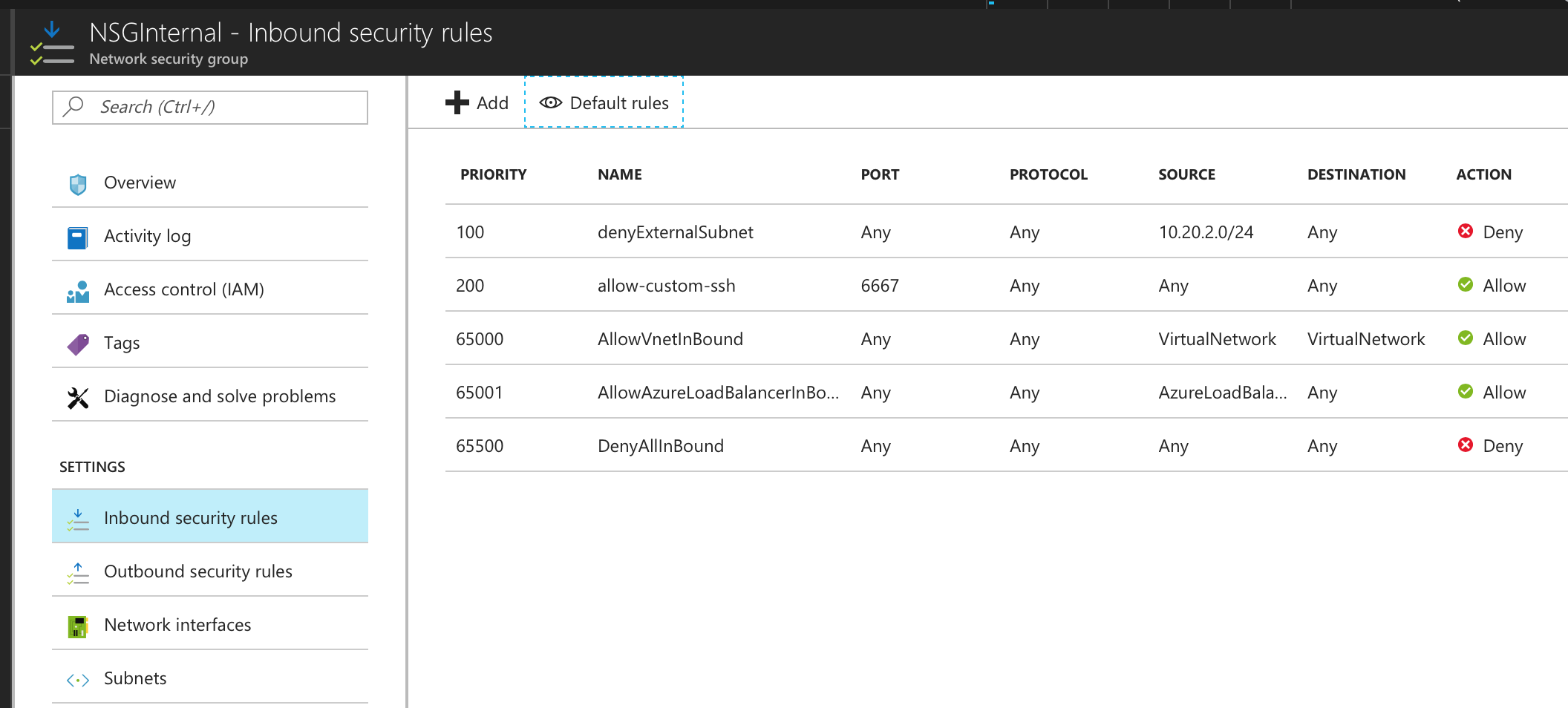
• NSG Internal - Outbound Rules
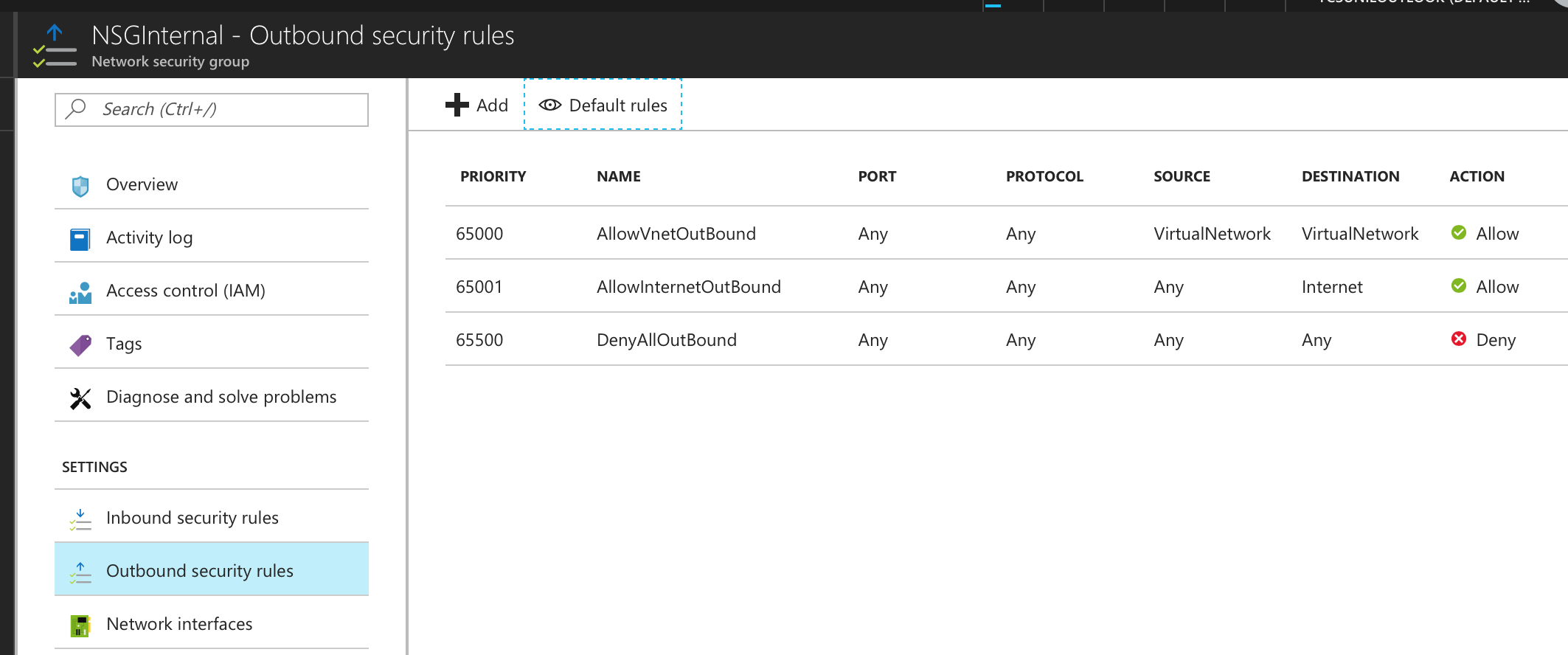
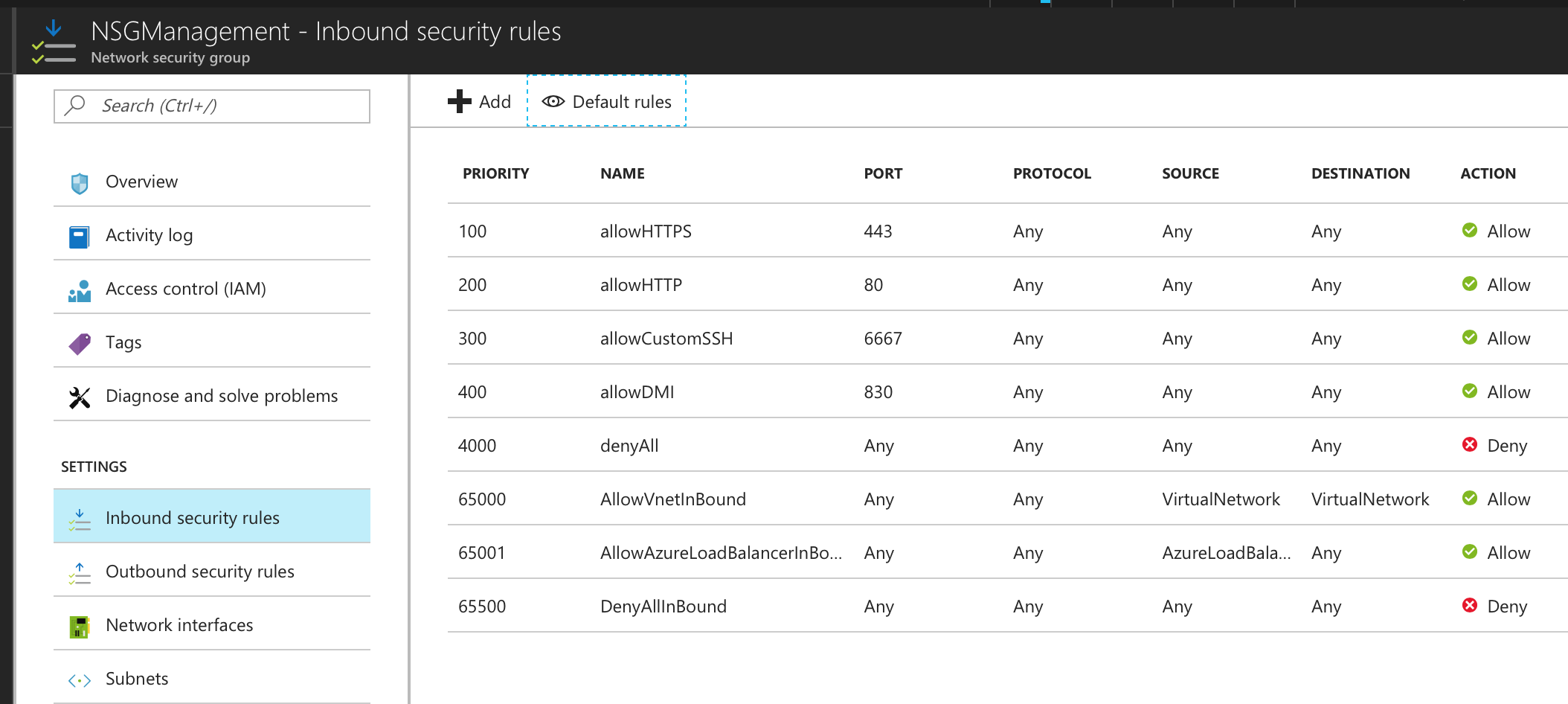
The list of NSG Inbound/Outbound rules created “NSGManagementSubnet” are:
•NSG Management - Inbound Rules
•NSG Management - Outbound Rules