FAQ1: I am unable to connect to my backend resources through L3 VPN
Solution: The solution describes the configuration required in the Azure Virtual Network and ICS to connect to the On-premise network through the L3 VPN connection.
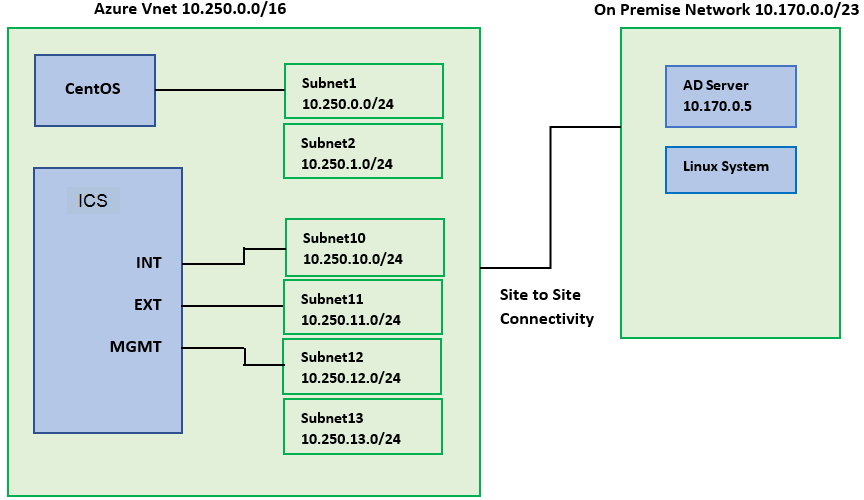
The following network topology shows two networks, Azure Virtual Network and On-premise network, with Site-to-Site connectivity between them.
Ivanti Connect Secure on Microsoft Azure
Before proceeding with the configuration, prepare a configuration checklist that will be handy during the configuration.
|
Azure Virtual Network |
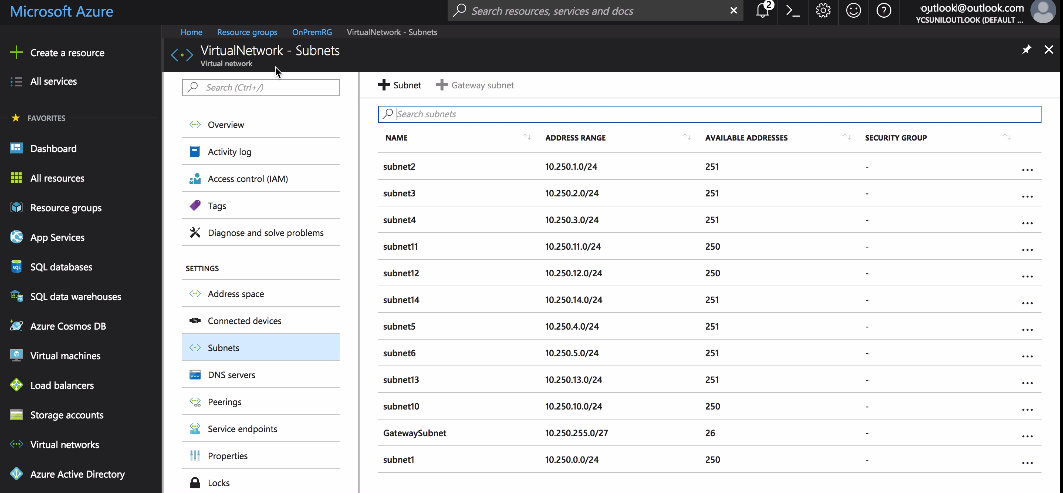
Resource group name: OnPremRG Virtual Network name: VirtualNetwork Virtual Network address space: 10.250.0.0/16 Subnets: Subnet1: 10.250.0.0/24 Subnet2: 10.250.1.0/24 Subnet3: 10.250.2.0/24 Subnet4: 10.250.3.0/24 . . . . Subnet10: 10.250.10.0/24 Subnet11: 10.250.11.0/24 Subnet12: 10.250.12.0/24 Subnet13: 10.250.13.0/24
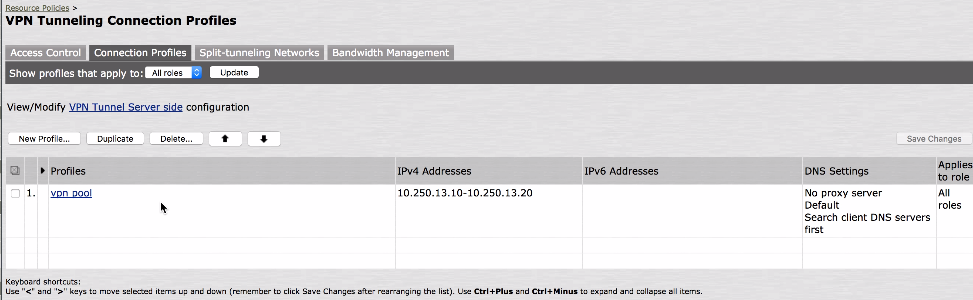
ICS Internal interface connected to Subnet10 (10.250.10.0/24) ICS External interface connected to Subnet11 (10.250.11.0/24) ICS Management interface connected to Subnet12 (10.250.12.0/24) ICS VPN pool connected to Subnet13 (10.250.13.0/24)
CentOS system IP address: 10.250.0.4 connected to Subnet1 (10.250.0.0) Public IP address: 104.211.245.193 VPN Pool address space: 10.250.13.0/24 |
|
On-premise network |
On-premise Network address space: 10.170.0.0/23 AD Server IP address: 10.170.0.5 |
The Azure Vnet with address space 10.250.0.0/16 has four subnets - Subnet10 to Subnet12 - connected to ICS’s Internal, External and Management interfaces respectively, and Subnet13 connected to ICS VPN pool.
The CentOS system is connected to Subnet1.
Virtual Network in a Resource Group (OnPremRG)
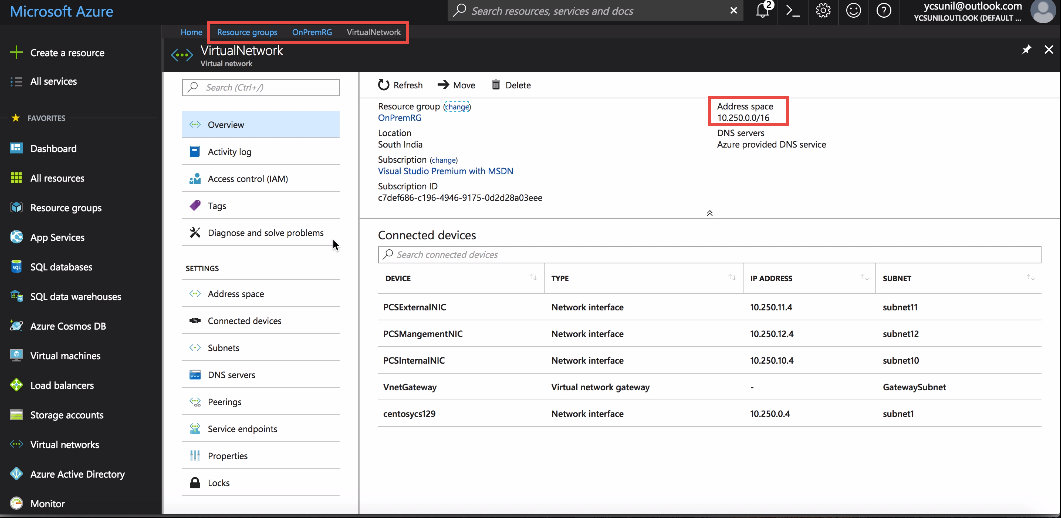
Subnets in the Virtual Network
Log in to ICS admin console and configure the VPN tunneling connection profile. The VPN pool has the range 10.250.13.10 to 10.250.13.20 in subnet13.
VPN Tunneling Connection Profile
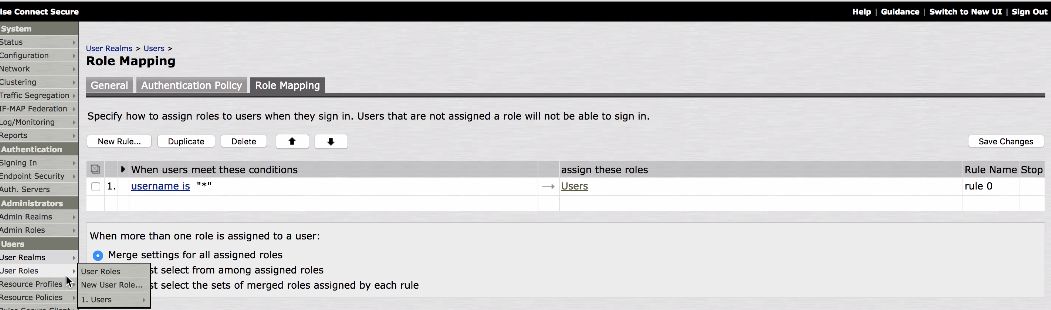
Create a user for this VPN tunnel policy and define the role mapping rule.
Use Role Mapping
Testing the Connection to CentOS System
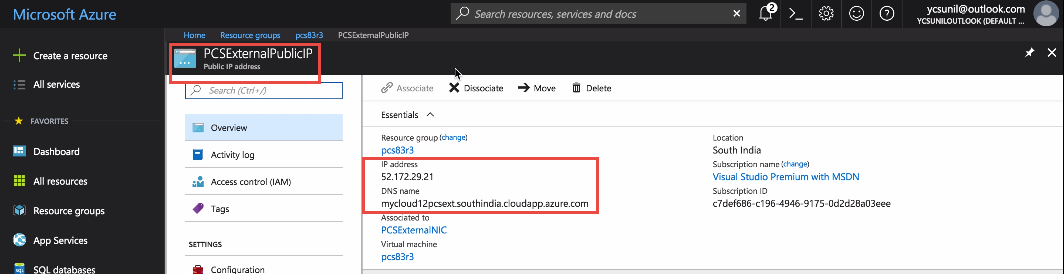
1.Note down the public IP address / FQDN of ICS’s External interface.
Public IP of ICS External Interface
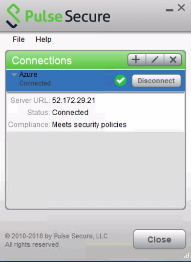
2.From client, connect to ICS.
Client Connection
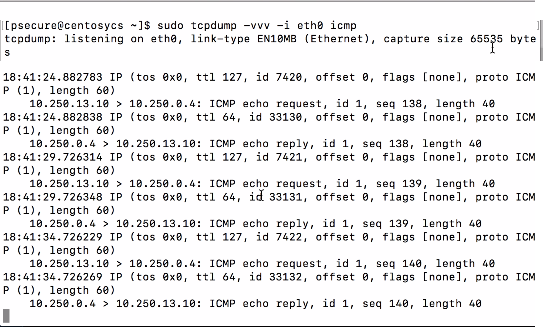
3.Once connected, on the CentOS system run tcpdump to capture the icmp traffic. And from the client system, ping to CentOS system.
tcpdump and ping responses
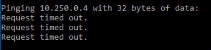
The following is observed:
•The CentOS system shows echo request and echo reply messages.
•The ICMP request is from 10.250.13.10, which is the tunnel IP.
•The client system shows the “Request timed out” messages.
•The packet is sent out from the CentOS system, but it is not forwarded to the ICS Internal interface.
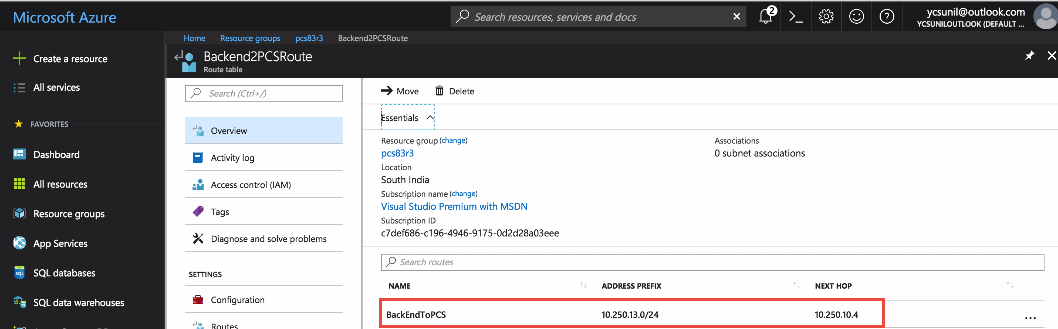
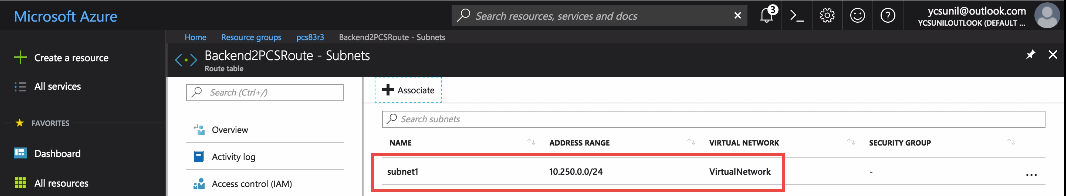
The solution is to add a route that forwards any packet in the tunnel IP address range 10.150.13.0/24 to ICS Internal interface. And associate the route to subnet (Subnet1) connected to the CentOS system.
Route Table
Subnet Association
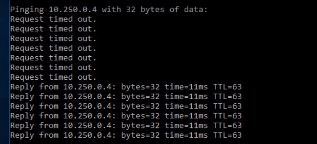
Wait for some time and observe that the packets are transmitted successfully.
Successful Packets Transmission
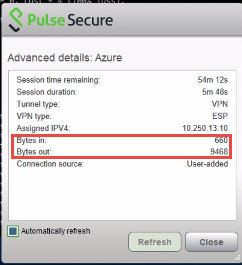
Testing the Connection to On-premise Resource
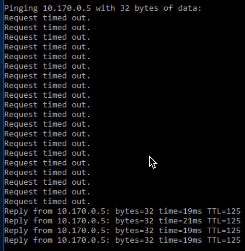
4.From the client system, ping the on-premise resource, AD server whose IP address is 10.170.0.5.
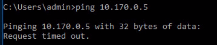
The output shows “Request timed out” messages. The packet in the return traffic stops at the Azure gateway subnet.
The solution is to add a route that forwards any packet at the gateway subnet to tunnel IP address range 10.150.13.0/24, and associate the route to gateway subnet.
Route Table

Subnet Association
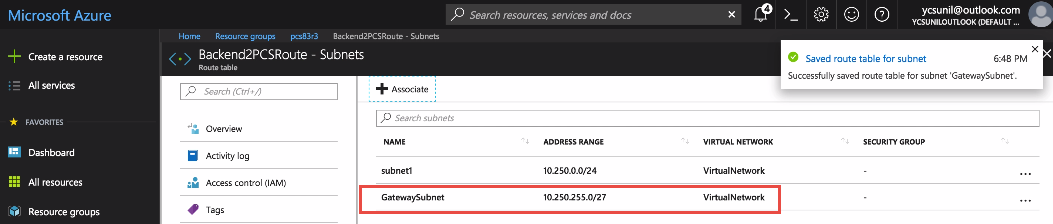
Wait for some time and observe that the packets are transmitted successfully.
Successful Packets Transmission