Defining Host Checker Pre-Authentication Access Tunnels
If your policies require Host Checker rules or third-party J.E.D.I. DLLs to access a policy server (or other resource) to check compliance before users are authenticated, you can use one of the following methods to make the resource available to the Host Checker Windows clients:
•Deploy the policy server in a DMZ where Host Checker rules or third-party J.E.D.I. DLLs can access the server directly instead of going through Ivanti Connect Secure-This deployment is the simplest solution because you do not have to define a Host Checker pre-authentication access tunnel through Ivanti Connect Secure between clients and the policy server.
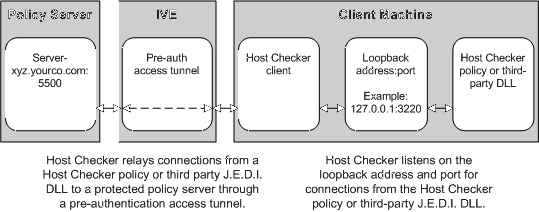
•Deploy the policy server in a protected zone behind Ivanti Connect Secure (Windows only)-This deployment requires you to define a pre-authentication access tunnel. A pre-authentication access tunnel enables Host Checker rules or third-party J.E.D.I. DLLs to access the protected policy server or resource before the system authenticates users. To define a pre-authentication access tunnel, you associate a loopback address (or hostname) and port on the client with an IP address and port on the policy server. You add one or more tunnel definitions to a MANIFEST.HCIF file, which you then upload to Ivanti Connect Secure. You can upload multiple MANIFEST.HCIF files to Ivanti Connect Secure. For all third-party policies enabled on a realm, Host Checker creates tunnels for all of the tunnel definitions in all of the MANIFEST.HCIF files, assuming the definitions are unique.While running on a Windows client, Host Checker listens for a connection on each loopback address and port you specify in the tunnel definitions. The connections can originate from the integrated Host Checker rules and from client-side or server-side J.E.D.I. DLLs. Host Checker uses the pre-authentication access tunnel(s) to forward the connections through Ivanti Connect Secure to the policy server(s) or other resource.
Host Checker pre-authentication access tunnels are supported on Windows only.
Specifying Host Checker Pre-Authentication Access Tunnel Definitions
For Windows clients, you can define a pre-authentication access tunnel that enables Host Checker methods or third-party J.E.D.I. DLLs to access a protected policy server (or other resource) before users are authenticated.
A definition for a Host Checker pre-authentication access tunnel configures access to one policy server or other resource. Each tunnel definition consists of a pair of IP addresses and ports: one loopback IP address and port on the client, and one IP address and port on the policy server.
You specify one or more tunnel definition(s) in a Host Checker policy package definition file. The package definition file, which must be named MANIFEST.HCIF, defines the name of an interface DLL, the Host Checker policies defined in the DLL, and the pre-authentication access tunnel definitions. Note that if you do not include policies in your package, Host Checker simply enforces that the package has run on the client. If you do declare policies through this file, they become available through the admin console where you can implement them at the realm, role, and resource policy levels.
Within the MANIFEST.HCIF file, you must include one definition per line, with a blank line between each definition, using the following format:
HCIF-Main: <DLLName>
HCIF-Policy: <PolicyName>
HCIF-IVE-Tunnel: <client-loopback>:port <policy-server>:port
where:
<DLLName> is the name of the interface DLL, such as myPestPatrol.dll. Even if you are not using an interface DLL, you must include a dummy DLL as a placeholder file that has this exact name.
<PolicyName> is the name of a policy defined in the DLL, such as myFileCheck. You can define multiple policies by using the HCIF-Policy statement for each policy. If you are not using an interface DLL, you can use any policy name as a placeholder.
The syntax of a Host Checker tunnel definition is:
HCIF-IVE-Tunnel: <client-loopback>:port <policy-server>:port
where:
<client-loopback> is a loopback address that begins with 127. and takes any of the following forms:
•An IP address and port that takes the form of 127.*.*.*:port. To avoid conflicts with JSAM, do not use 127.0.0.1 with port 80, but you can use 127.0.0.1 with other ports. For example: 127.0.0.1:3220
•A hostname that resolves to a loopback address that begins with 127. You can use a local hosts file on each client computer or a DNS server to resolve the loopback address.
•A hostname that does not resolve to a loopback address, or resolves to a non-loopback address. In these cases, Host Checker allocates a loopback address and updates the local hosts file on the client with the mapping. Note that the user must have administrator privileges in order for Host Checker to modify the local hosts file. If the user does not have administrator privileges, Host Checker cannot update the hosts file and cannot open the pre-authentication access tunnel. In that case, Host Checker logs an error.
<policy-server> is the IP address or hostname of the back-end policy server. Ivanti Connect Secure resolves the hostname you specify.
For example, in the following tunnel definition, 127.0.0.1:3220 is the client loopback address and port, and mysygate.company.com:5500 is the policy server hostname and port:
HCIF-IVE-Tunnel: 127.0.0.1:3220 mysygate.company.com:5500
Or you can use a hostname for the client, as in this example:
HCIF-IVE-Tunnel: mysygate.company.com:3220 mysygate.company.com:5500
Keep the following in mind when specifying tunnel definitions:
•You must add a blank line between each line in the MANIFEST.HCIF file, and you can use a semi-colon at the beginning of a line to indicate a comment. For example:
HCIF-Main: myPestPatrol.dll
HCIF-Policy: myFileCheck
HCIF-Policy: myPortCheck
; Tunnel definitions
HCIF-IVE-Tunnel: 127.0.0.1:3220 mysygate.company.com:5500
HCIF-IVE-Tunnel: 127.1.1.1:3220 mysygate2.company.com:5500
HCIF-IVE-Tunnel: mysygate.company.com:3220 mysygate3.company.com:5500
•Host Checker pre-authentication access tunnels are supported on Windows only.
•If <client-loopback> is a non-loopback address, then Host Checker cannot open the pre-authentication access tunnel and logs an error instead.