Using Endpoint Security Assessment Plug-In
The Endpoint Security Assessment Plug-in (ESAP) on Ivanti Connect Secure checks third-party applications on endpoints for compliance with the predefined rules you configure in a Host Checker policy. This plug-in is included in the system software package.
Ivanti frequently adds enhancements, bug fixes, and support for new third-party applications to the plug-in. New plug-in releases are available independently and more frequently than new releases of the system software package. If necessary, you can upgrade the plug-in independently of upgrading the system software package.
You can upload up to four versions of the plug-in to your system, but it uses only one version at a time (called the active version). If necessary, you can roll back to a previously active version of the plug-in.
Upgrading the Endpoint Security Assessment Plug-In
To upgrade the Endpoint Security Assessment Plug-in:
1.Download the Endpoint Security Assessment Plug-in from the Support Center to your computer:
•Open the following page:
https://forums.ivanti.com/s/article/How-to-Contact-Ivanti-Support
•Click the Software tab.
•Navigate to the ESAP release you want and click the link to download the package file to your computer.
2.Select Authentication > Endpoint Security > Host Checker.
3.At the bottom of the Host Checker page under Manage Endpoint Security Assessment Plug-In Versions:
4.If you have previously uploaded four versions of the component software, you must delete one of the versions before you can upload another one. Select the version you want to delete and click Delete.
5.If you want the system to actively begin using the new component software immediately after you upload it, select the Set as active after upload option.
6.Click Browse, select the plug-in file you want to upload to the system, and click OK.
7.Click Upload. While the system uploads and decrypts the plugin .zip file, the message “Loading” appears in the plug-in list under Manage Endpoint Security Assessment Plug-In Versions. If the device is a member of a cluster, it displays the message “Loading...” while the plug-in is transferred to the other cluster nodes. After the plug-in is installed, the date and time of the plug-in installation appears in the plug-in list.
8.If you did not select the Set as active after upload option, activate the plug-in you want to use by selecting the version in the plug-in list and clicking Activate.
- If you attempt to activate a version of the plug-in that does not support all of the predefined rules already configured in all Host Checker policies, the system does not allow activation of that plug-in version. For example, if a Host Checker policy is configured to use a predefined rule to check for a version of antivirus software, and you attempt to activate a plug-in version that does not support that particular version of the antivirus software, the system does not allow you to activate that plug-in version. To view the list of supported products for a plug-in version, click the plug-in's version number under Manage Endpoint Security Assessment Plug-In Versions.
- You can roll back to an older plug-in version after upgrading to a later version by selecting the older version as the active version. But, if you modified any Host Checker policies after upgrading to the later version, the rollback may not succeed. Rollback is guaranteed to succeed only if the policies did not change.
- If you upgrade the system software to a newer version, or you import a user configuration file, the currently active plug-in version does not change. If you want to use a different plug-in version after upgrading or importing a user configuration file, you must manually activate that plug-in version.
- If the system already has four versions of the plug-in installed when you upgrade the system software to a newer version, it automatically deletes the oldest plug-in version and installs, but does not activate, the plug-in included with the new system software.
Activating the OPSWAT SDK Version
Beginning with Release 8.2R5, Ivanti Policy Secure supports both v3 and v4 SDKs provided by OPSWAT. The default SDK version used is v3, but it can be reconfigured based on your requirement. The product/vendor names used by v3 and v4 SDK might differ. Due to the product/vendor names mismatch, there is a possibility that the rules become empty while creating Host Checker rule with v3 SDK activated and upon enabling v4 SDK. To avoid this, a migration page is added to help the administrators in migrating the policies from v3 to v4 SDK. To use v3 or v4 SDK:
1.Select Authentication > Endpoint Security > Host Checker.
2.Select the Activate Older SDK in ESAP for Host Checker policy evaluation check box for v3 SDK.
3.Clear the Activate Older SDK in ESAP for Host Checker policy evaluation check box for v4 SDK.
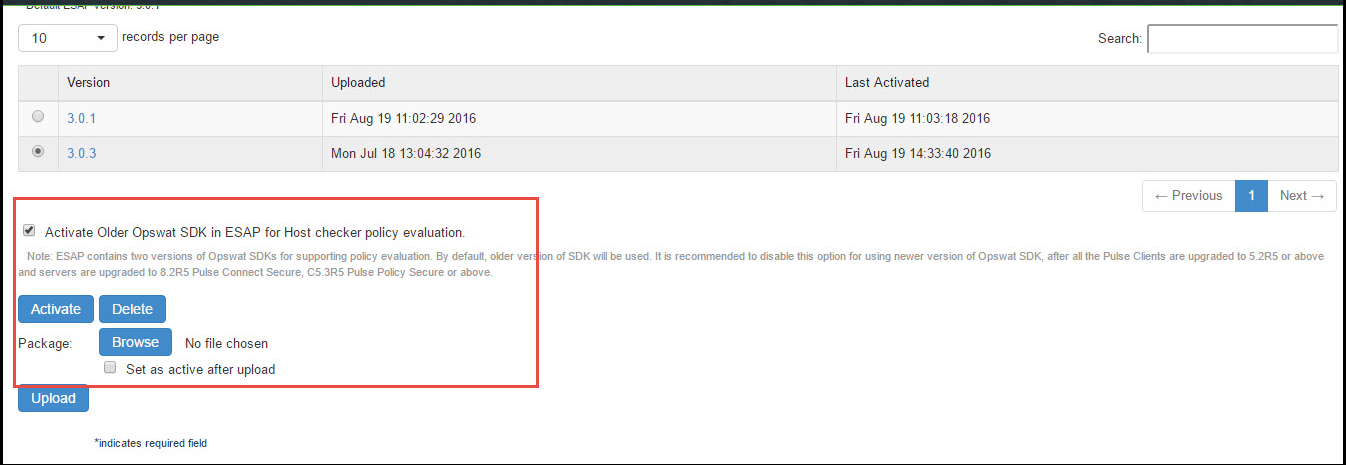
It is recommended to disable this option for using newer version of OPSWAT SDK, after all the Ivanti Secure Access Clients are upgraded to 5.2R5 or above and servers are upgraded to Ivanti Connect Secure 8.2R5 or above.
4.Click Activate. A confirm Activation page appears which lists the products and/or vendors, which are no longer supported in that particular ESAP SDK version. From the drop-down list, admin can select one or many new products/vendors instead of the existing product/vendor.
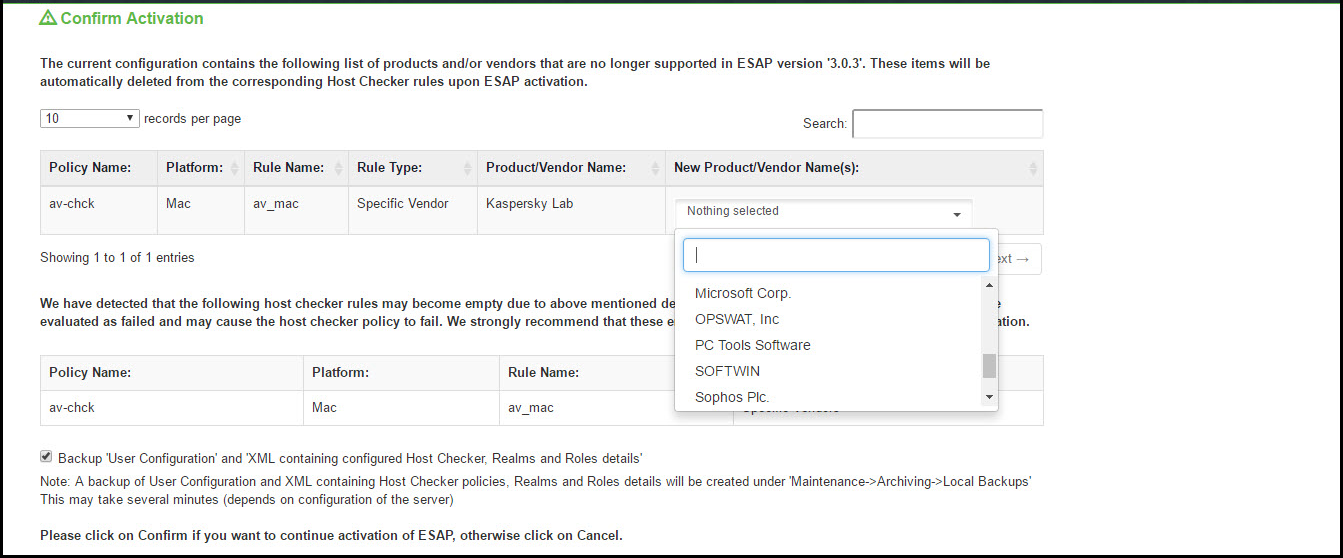
Only the products/vendors, which gets changed are listed. If some rules have some products/vendors whose names are not changed, it will be automatically migrated and will not be listed.
5.Select Backup 'User Configuration' and 'XML containing configured Host Checker, Realms and Roles details to create a local backup of user configurations under Maintenance > Archiving > Local Backups.
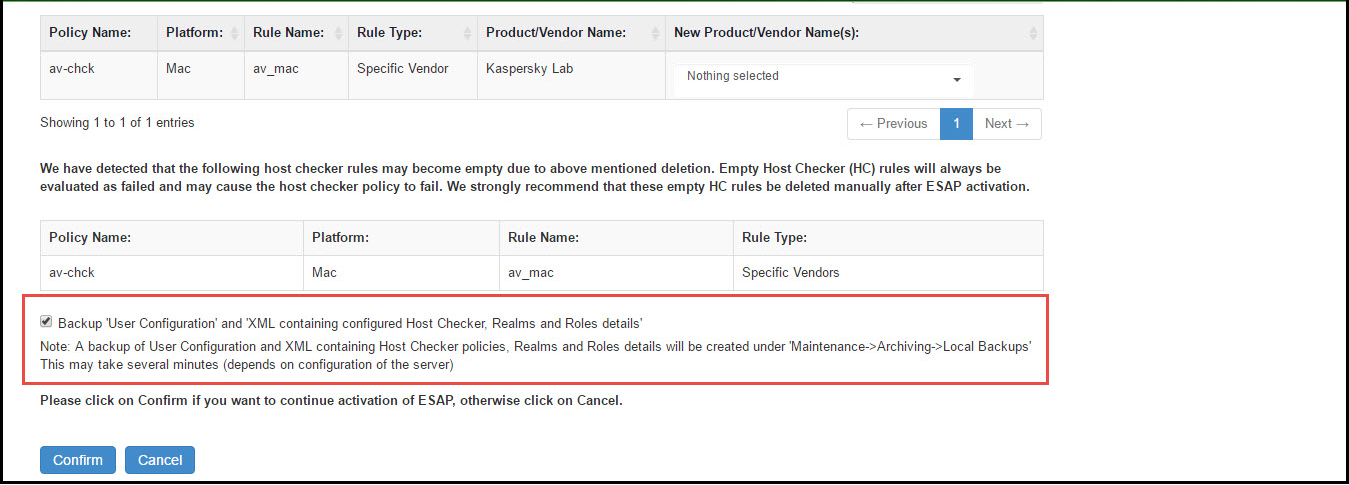
Server maintains a maximum of 5 backups. To capture a new backup, older one will be automatically deleted.
Server Notification: Server already contains allowed maximum number of user configuration backups. Existing backup configuration 'xxxxx' will be deleted for storing the new backup.
6.Click Confirm.
OPSWAT SDK V3 to V4 Migration
Ivanti supports OPSWAT version 3 and version 4 for endpoint compliance evaluation. The migration option helps the administrators to migrate their servers and clients with OPSWAT v4 to take advantage of latest updates.
Software Support
Beginning 9.1R2 release, the following OS are supported:
•Windows 7 and later releases
•macOS 10.12 and later releases
As a prerequisite, a minimum ESAP version 3.4.2 is required for supporting migration of OPSWAT SDK from v3 to v4 version. A warning message is displayed if the minimum version is not present.
To migrate from v3 to v4 version:
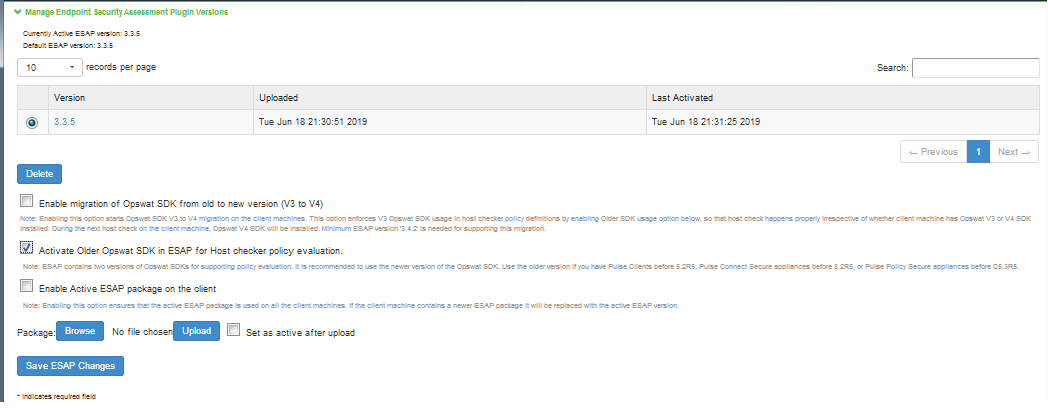
1.Navigate to "Manage Endpoint Security Assessment PlugIn Versions" section on the Authentication > Endpoint Security > Host Checker page.
2.Select the Enable migration of Opswat SDK from old to new version (V3 to V4) option.
On enabling this option, the clients start downloading the V4 SDK and migrate to newer SDK.
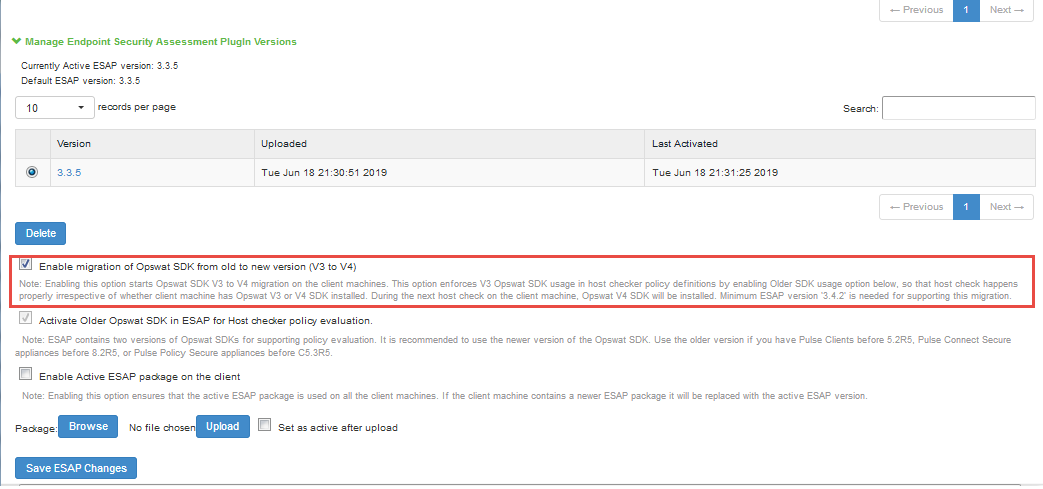
3.Clear the Enable migration of Opswat SDK from old to new version (V3 to V4) option once the migration is complete.
4.Verify the migration status. In the confirmation message box, click Confirm.
Post migration, an administrator can remap the configured products in the policies to map to the newer SDK using the Post Migration window. For example, in the below screenshot, the Product /Vendor Name for the policy has been changed from Microsoft Corp. to Microsoft Corporation for successful migration.
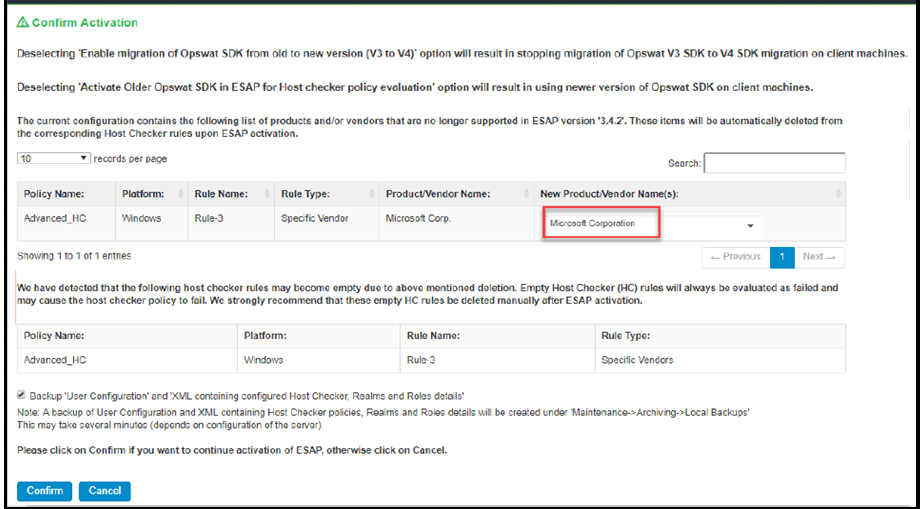
5.Enable Backup User Configuration and XML containing Host Checker, Realms and Role details for performing configuration backup. This option helps to revert to the previous version of Ivanti Connect Secure/Ivanti Policy Secure configuration, if required.
6.Click Confirm.
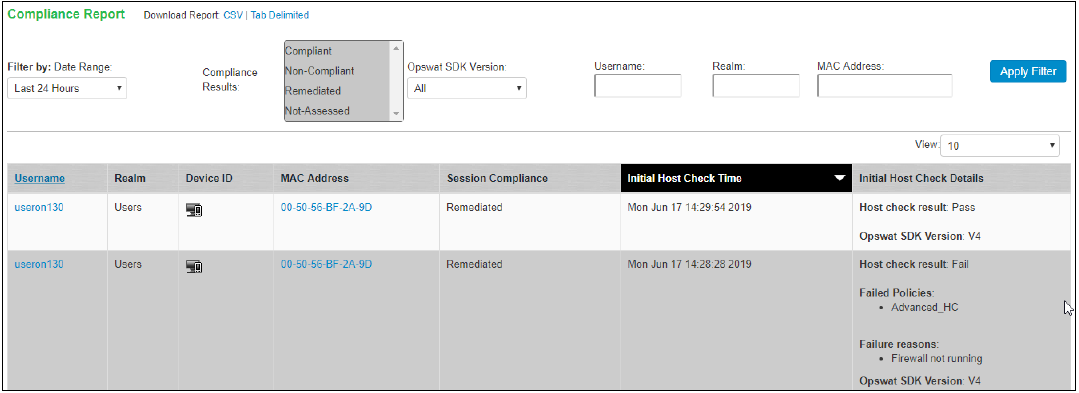
Compliance Report
The Compliance Report displays the compliance details of the users connected to the server. The report also includes the OPSWAT SDK version used for these connections. OPSWAT SDK version is used to filter the users using a specific OPSWAT SDK version.
The compliance report page displays the OPSWAT SDK version details only when the "Enable migration of OPSWAT SDK from old to new version (V3 to V4)" option is enabled.
To check the SDK version for each connection, view the report under System > Reports > Compliance Report.
Roll Back Procedure
To roll back to previous version of OPSWAT SDK:
1.Navigate to "Manage Endpoint Security Assessment PlugIn Versions" section on Authentication > Endpoint Security > Host Checker page.
2.Clear the Enable migration of Opswat SDK from old to new version (V3 to V4) check box.
3.Enable Activate Older Opswat SDK in ESAP for Host Checker policy evaluation.
4.Click Save ESAP Changes.
End User Flow
User logging in from browser or User logging in from Ivanti Secure Access Client for L3 connection:
•Client machine has OPSWAT V3 SDK installed.
•Host Check starts on the client machine as part of connection establishment.
•Server sends the required information to client for upgrading V3 to V4 SDK.
•Client downloads V4 SDK and collects the installed security products details using newly installed V4 SDK and sends the detected product details to server.
•Server evaluates configured OPSWAT based rules by consuming the details received from client machine.
•Host Checker continues to use the installed V4 SDK on client machine for subsequent host checks and connections.
User logging in from Ivanti Secure Access Client for L2 connections:
•Client machine has OPSWAT V3 SDK installed.
•Host Check starts on the client machine as part of connection establishment.
•Server sends the required information to client for upgrading V3 to V4 SDK.
•During L2 connection, client fails to download V4 SDK.
•Host Checker collects the installed security products details using existing V3 SDK and sends the detected product details to server.
•Server evaluates configured OPSWAT based rules by consuming the details received from client machine.
•L2 connection is established followed by an L3 connection.
•Server detects L2 followed by L3 connection attempt and remembers that ESAP upgrade is needed on the client machine.
•Host Check is triggered again on client machine during L3 connection.
•Server sends the required information to client for upgrading V3 to V4 SDK.
•Client downloads V4 SDK (because L2 connection is complete already) and collects the installed security products details using newly installed V4 SDK and sends the detected product details to server.
•Server evaluates configured OPSWAT based rules by consuming the details received from client machine.
•Host Checker continues to use the installed V4 SDK on client machine for subsequent host checks and connections.
Changing the Active ESAP Package
Administrator can activate any of the already uploaded ESAP packages by selecting the corresponding radio button under "Manage Endpoint Security Assessment Plugin Versions" table and then clicking on "Activate" button.
To change the active ESAP packages:
1.Select Authentication > Endpoint Security > Host Checker.
2.Under Manage Endpoint Security Assessment Plugin Versions, select the required ESAP version.
3.Click Activate.
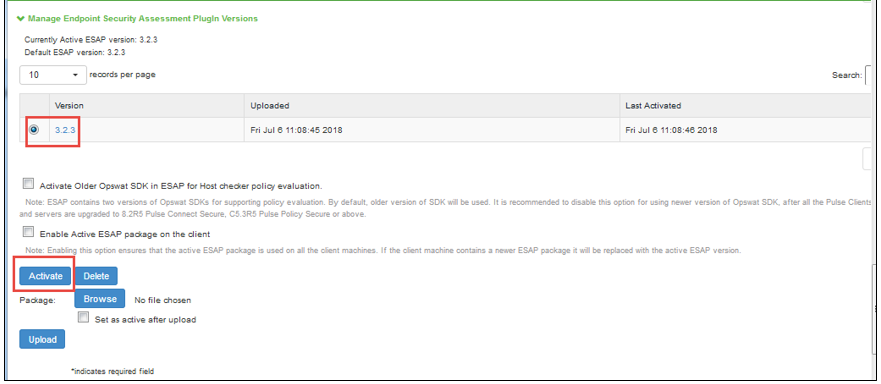
If the client machine has newer ESAP package and if it has to be replaced, then select "Enable the Active ESAP package". For detailed procedure, see Enabling the Active ESAP Package.
Enabling the Active ESAP Package
Administrator can enable "Enable Active ESAP package on the client" checkbox to ensure that client machine always uses the active ESAP package, even if the active ESAP package is older than the version installed on the client system. In case client machine has newer ESAP package installed, it will be replaced with the older Active ESAP version with this option enabled.
To enable the active ESAP package:
1.Select Authentication > Endpoint Security > Host Checker.
2.Under Manage Endpoint Security Assessment Plugin Versions, select the Enable Active ESAP package on the client check box.
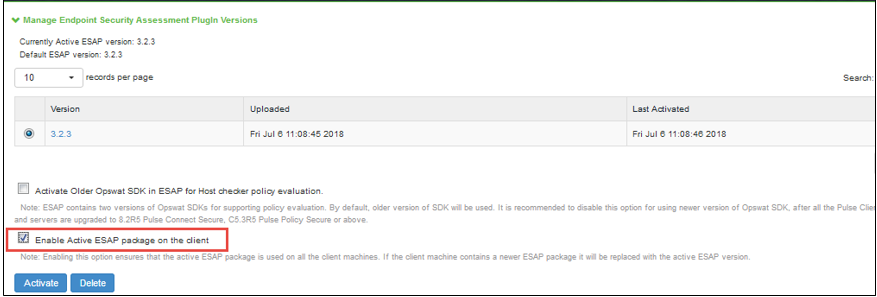
3.Click Activate.