Access Control with SAML Server
In a SAML deployment, a SAML service provider is configured to request authentication from a SAML identity provider. The SAML identity provider responds with assertions regarding the identity, attributes, and entitlements (according to your configuration). The exchange enforces security and enables the SSO user experience.
IPS as a SAML Service Provider
If you are working with a partner that has implemented a SAML identity provider, you can deploy the IPS as a SAML service provider to inter-operate with it, thereby enabling SSO for users who should have access to protected resources. In this model, the user is authenticated by the SAML identity provider. The system uses the SAML response containing the assertion to make an authentication decision.
The choices the identity provider makes to implement SAML determine the deployment choices, for example whether to use SAML 2.0 or SAML 1.1, whether to reference a published metadata configuration file, and whether to use a POST or artifact profile. When you deploy the system as a SAML service provider, you create a SAML authentication server configuration that references the partner SAML identity provider, and a set of access management framework objects (realm, role mapping rules, and sign-in policy) that reference the SAML authentication server.
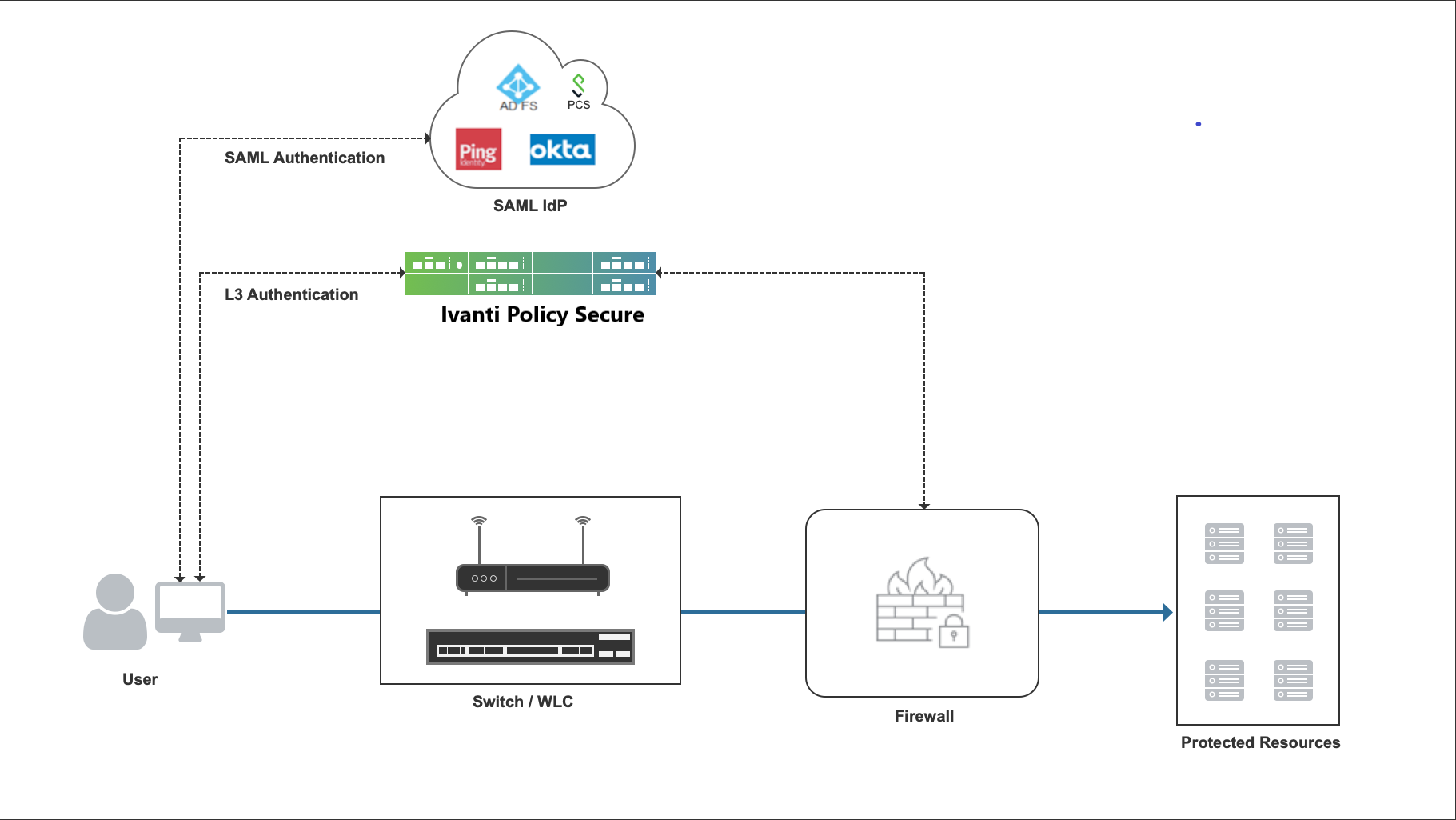
Layer 3 Authentication and Enforcement using SAML Server
Figure shows how to access firewall protected resources using SAML server on IPS.
-
End user using an user agent (either a browser or a Ivanti Secure Access Client) authenticates to IPS
-
Ivanti Policy Secure(IPS) acting as a SAML Service Provider (SP), issues a SAML authentication (SAML AuthN) request to SAML IdP through the user agent. If SAML authentication request is valid, IdP authenticates the end user and generates SAML assertion and sends it to IPS (SAML SP) through user agent.
-
Ivanti Policy Secure(IPS) validates the SAML assertion and if it's valid, authentication is successful.
-
The user is first authenticated with SAML IdP. Once end user is authenticated appropriate role is assigned and the user ID is pushed to firewall. The end user can access the protected resource.
Ivanti Secure Access Client uses embedded browser for SAML authentication. It should be enabled on the Ivanti Secure Access Client connection settings in IPS.
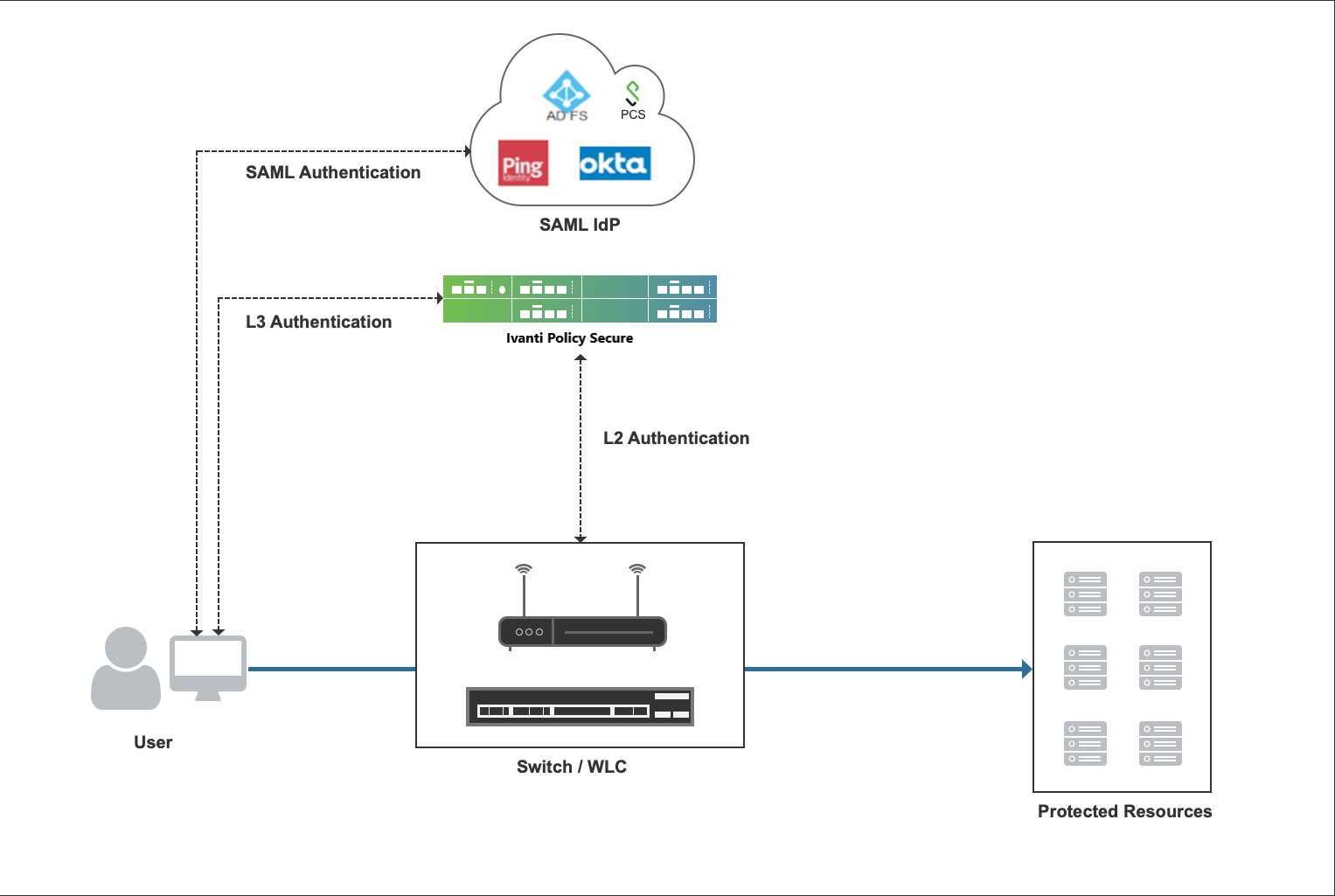
Layer 2 Authentication and Enforcement using SAML Server
Figure shows how to access switch protected resources using SAML server on IPS.
For Layer 2 access control using SAML server on IPS, below mechanism is used:
-
MAC address authentication is performed using either RADIUS or SNMP for Layer 2 authentication. The session is created on IPS after successful MAC authentication and the user is provided with a limited access role since the Host Checker is not performed.
-
The user must be able to access both IPS and SAML IdP after L2 authentication. For policy enforcement using MAC address authentication, see here.
-
Ivanti Secure Access Client or web browser is used to perform Layer 3 authentication using SAML server.
-
After successful Layer 3 authentication on IPS via SAML IdP, both Layer 2 (MAC authentication) and Layer 3 (SAML authentication) connections are bridged using MAC address.
-
Host Checker is performed and if the SAML authentication is successful the user is provided with Full Access Role.
-
The user can access protected resources.
Layer 2 session is updated with the RADIUS attributes of the Layer 3 connection. The bridged session is used to perform Layer 2 access control. For more information on session bridging, see here.