Configuring IPS for enabling Behavioral Analytics
For the fresh Installation of IPS, UEBA package will not be available by default for anomaly detection. Admin must add the UEBA package. In case of upgrade of IPS (R7 or earlier to R8 or later), the previous UEBA package is retained. You may download latest UEBA package from Ivanti Support Site (https://my.pulsesecure.net).
UEBA Package
- Log in to Ivanti Support Site, https://my.pulsesecure.net.
- Select Ivanti Policy Secure as product and navigate to the "Ivanti Behavioral Analytics Database" section. Download the package, "ps-ics-ips-behavioral-analytics-v1.0.x.pkg".
- From the Admin Console, select System > Behavioral Analytics.
- Navigate to Browse and select the UEBA package.
- Click Upload & Activate.
- Click Save Changes.
Configuring IPS for Adaptive Authentication
To enable adaptive authentication:
- Select System > Behavioral Analytics > Configuration.
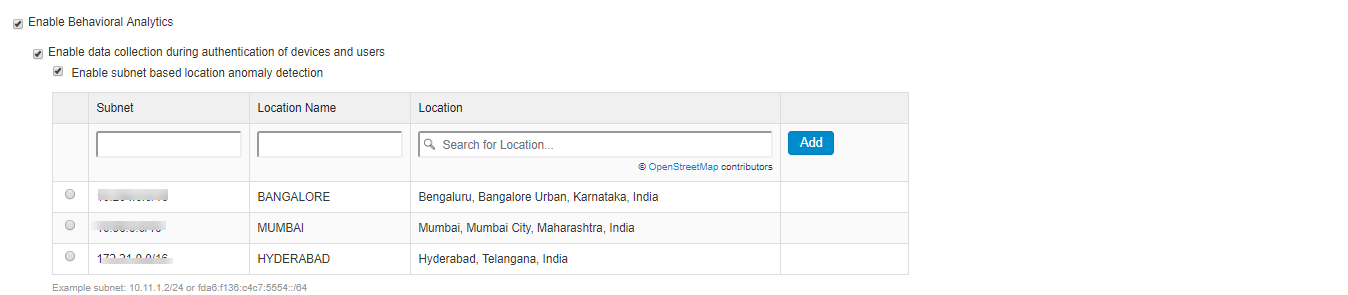
- Under Configurations, select Enable Behavioral Analytics.
- For enabling Adaptive Authentication, select Enable data collection during authentication of devices and users.
- For location-based anomaly detection, select Enable subnet based location anomaly detection.
- Enter the Subnet details. For example, 10.11.1.2/24.
- Enter the location name.
- Type the location to search and press Enter.
- Click Add to add the location.
- Select User > User Realms > General.
- Under Additional Authentication Server, Enable Additional Authentication Server.
- Select Enable Adaptive authentication.
- Under Authentication #2, select the desired secondary authentication server from the drop-down list.
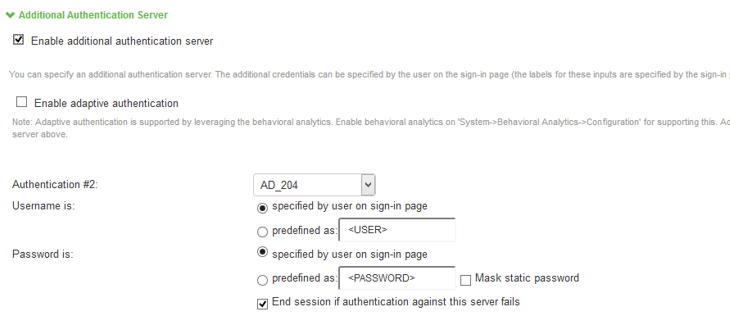
- Click Save Changes.
Configuring IPS to detect Anomaly Traffic from IoT devices
As a pre-requisite Profiler should have been configured for detecting the anomaly traffic from IoT devices. For more information, see Profiler Deployment Guide.
To determine anomaly traffic from IoT devices:
- Select System > Behavioral Analytics > Configuration.
- Under Configurations, select Enable Behavioral Analytics.
- Select Enable Network Traffic from switches.
- Configure the list of switches in the network from where the required data can be received/forwarded to analytics engine on IPS.
- Add the switches manually by adding (Switch IP address/mac address) or add the existing switches under Add Switch from list table. Select Dynamically add switches from RADIUS and SNMP clients to automatically add switches from RADIUS and SNMP clients.
- Select Enable Data Collection through SPAN from switch to enable SPAN configuration for determining unknown domain anomaly for unmanaged devices.
- Select the network interface (External port/Internal port).
- (Optional) Enter the IP address of the DNS server and click Add. DNS requests from these servers will not be considered for anomaly detection.
- Enter the learning duration in days (7-30 days). Learning duration is learning period for unmanaged devices to build the device profile.
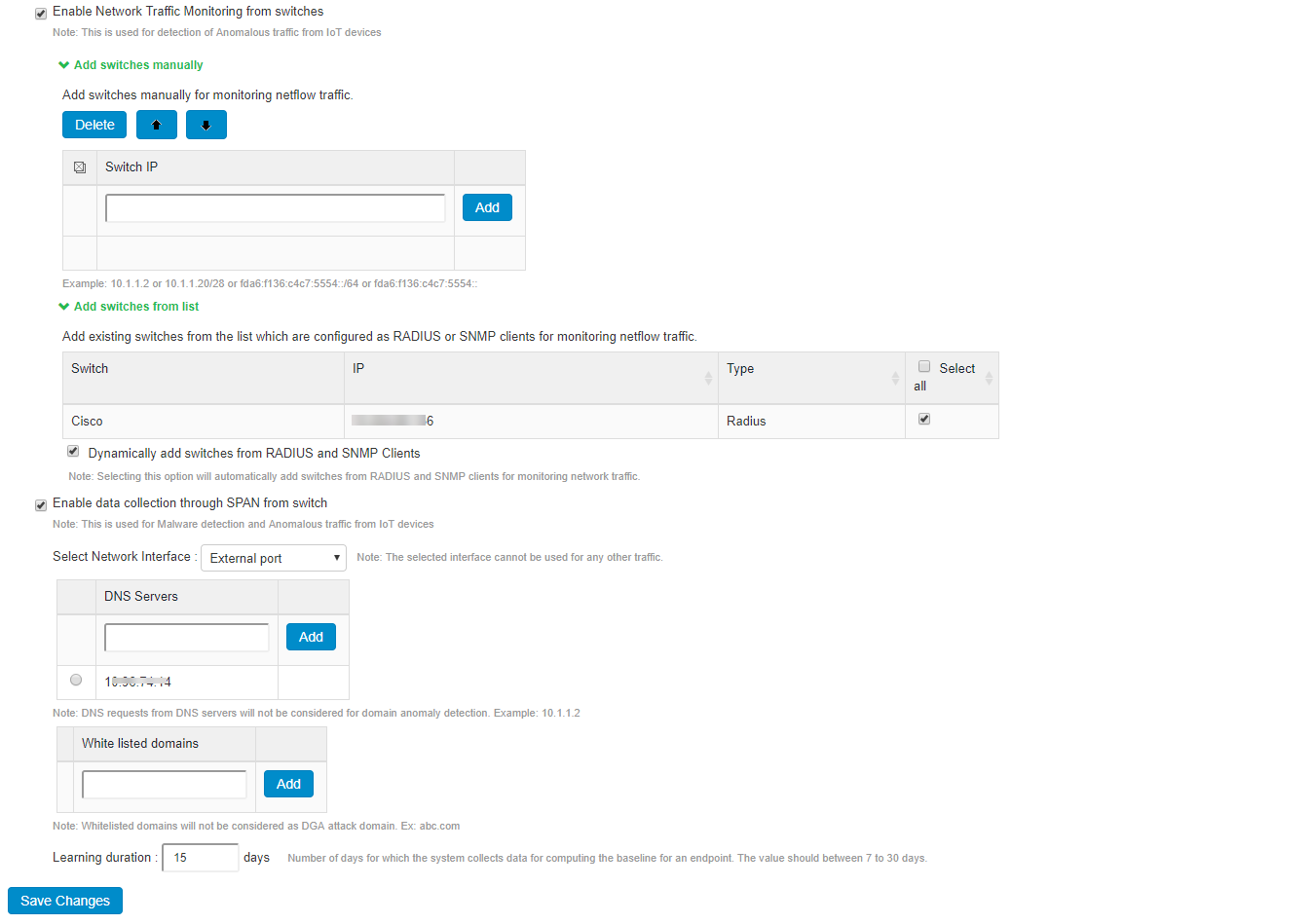
- Click Save Changes.
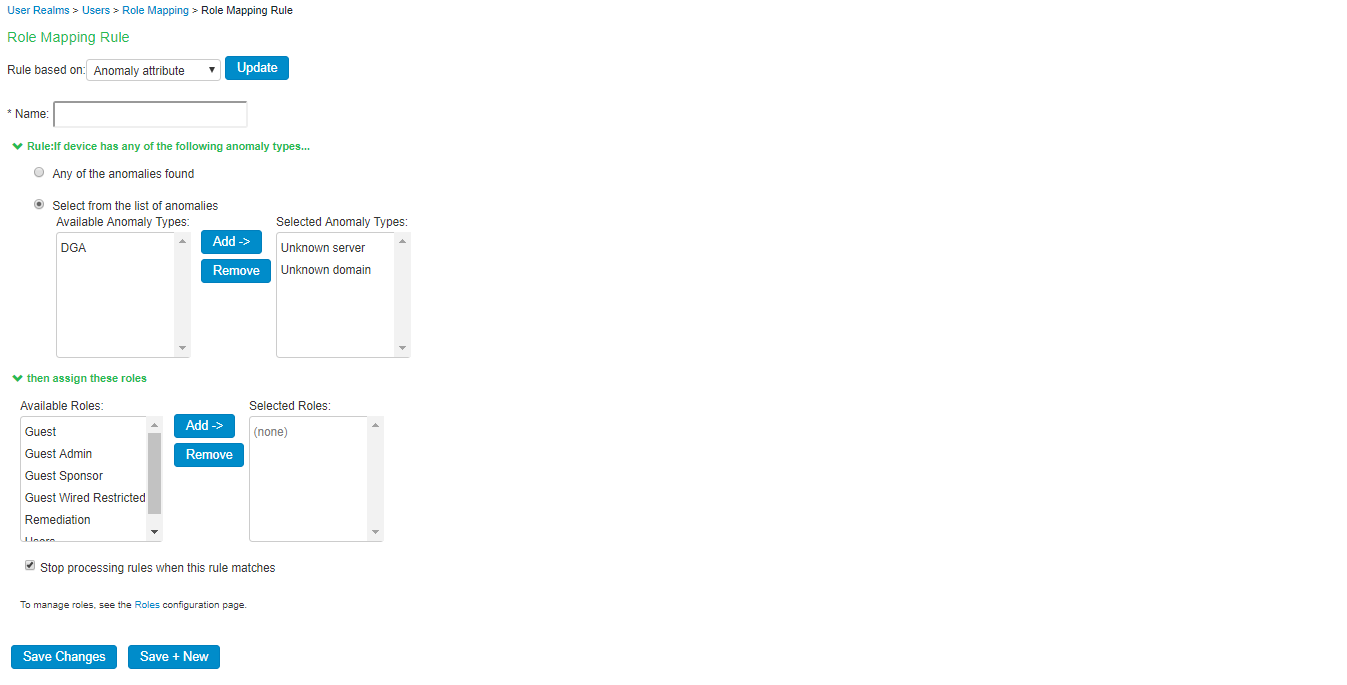
- Configure the role mapping rules for user realm and/or MAC authentication realm.
- Create new role mapping rule, select Anomaly attribute under Rule based on and click Update.
- Enter the rule name.
- Under Rule: If device has any of the following anomaly types:
- Any of the anomalies found- Select this option to detect the device with any anomaly type.
- Select from list of anomalies- Select this option to configure the specific anomaly type from the available list. To detect anomaly traffic from IoT devices configure Unknown server/Unknown domain as anomaly from the list of Available Anomaly Types.
- Select Stop processing more rules option to stop evaluating role mapping rules if the user meets the conditions specified for this rule. Ensure that the rule is at the top of the list.
- Configure the required roles and click Save Changes.
Configuring IPS to detect Potential Malware
IPS relies on DNS traffic collected through SPAN to determine the potential malware on the endpoint.
To configure IPS for detecting potential malware:
- Select System > Behavioral Analytics > Configuration.
- Under Configurations, select Enable Behavioral Analytics.
-
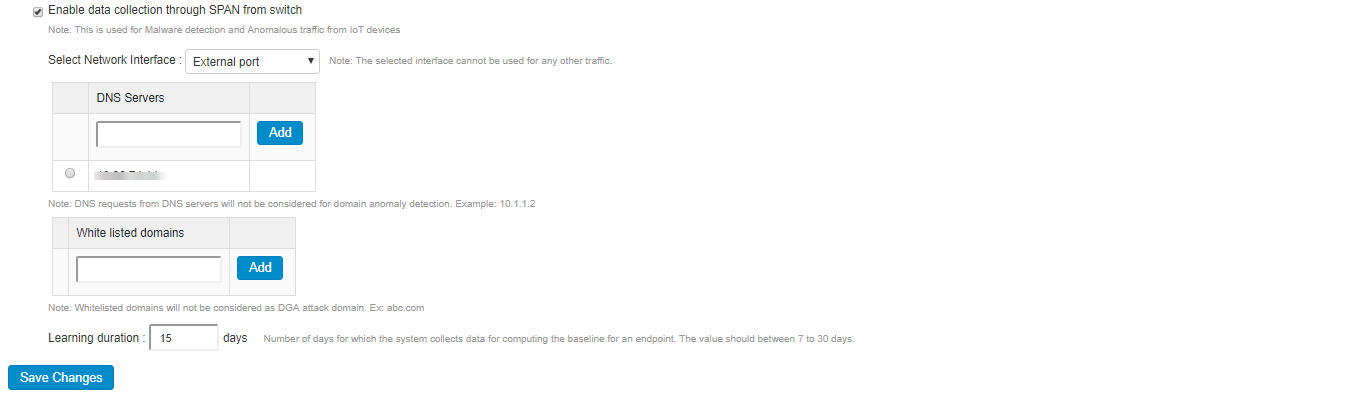
Select Enable Data Collection through SPAN from switch to enable SPAN configuration for determining DGA based potential malware attacks. This anomaly detection mechanism is supported for both managed and unmanged/IoT devices.
- Select the network interface (External port/Internal port).
- (Optional) Enter the IP address of the DNS server and click Add. DNS requests from these servers will not be considered for anomaly detection.
- (Optional) Enter the white listed domains to exempt the domains from anomaly detection.
-
Configure the role mapping rules for user realm and/or MAC authentication realm.
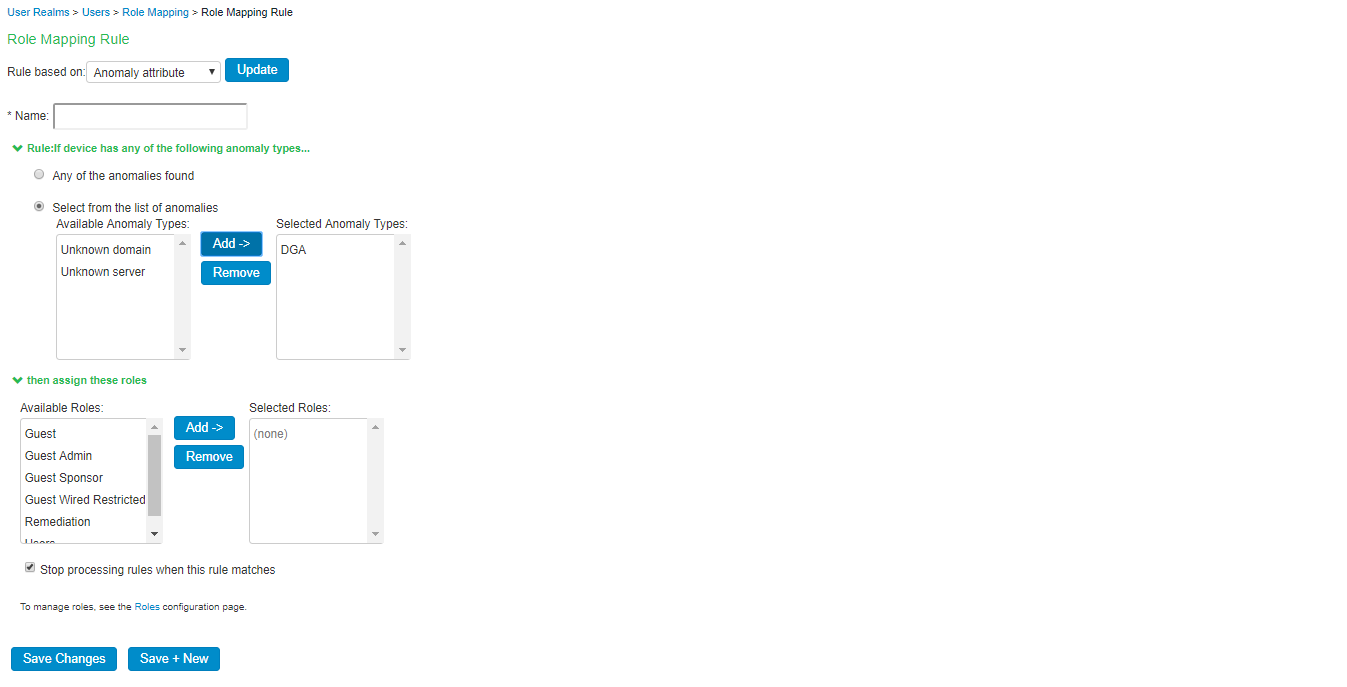
- Create new role mapping rule, select Anomaly attribute under Rule based on and click Update.
- Enter the rule name.
- Under Rule: If device has any of the following anomaly types:
- Any of the anomalies found- Select this option to detect the device with any anomaly type.
- Select from list of anomalies- Select this option to configure the specific anomaly type from the available list. To detect potential malware from IoT devices configure DGA as anomaly from the list of Available Anomaly Types.
- Select Stop processing more rules option to stop evaluating role mapping rules if the user meets the conditions specified for this rule. Ensure that the rule is at the top of the list.
The Administrator can also create Anomaly rules based on Custom Expressions.
- Click Save Changes.