Deployment of IPS/ICS using PAN/Check Point/ FortiGate Next Generation Firewall
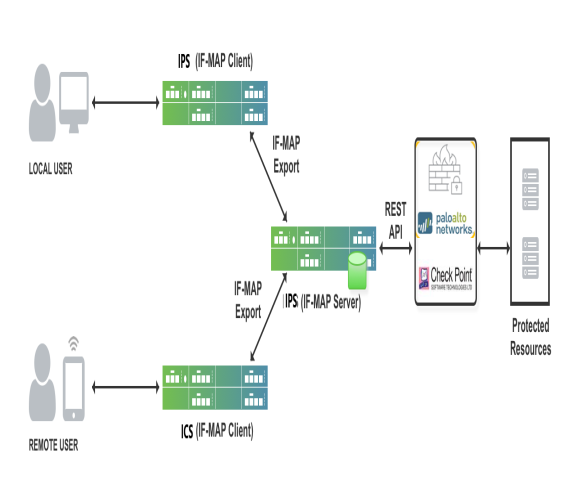
In a federated enterprise, a user can log in to a IPS or ICS device (remote access) for authentication and access the resource protected by the PAN/Check Point/ FortiGate Firewall. The session information is shared across IPS or ICS device using IF-MAP protocol through IF-MAP server.
The PAN/Check Point/ FortiGate Firewall controls the IPS and ICS user's access to protected resources based on the policy settings. The IF-MAP server receives the session information of multiple IPS and ICS and provisions user identity information to Firewall. The federation requires provisioning of user’s information on the PAN/Check Point/ FortiGate Firewall and allows access to the protected resource based on the resource access policies that are configured on IPS.
The authentication process is described below:
- The remote user establishes VPN tunnel using Ivanti Secure Access Client and the role is granted to the user based on policy configured on ICS.
- ICS session is exported to IF-MAP server.
- IF-MAP server provisions user identity details to PAN/Check Point/ FortiGate Firewall.
- The remote user tries to access PAN firewall protected resource. PAN/Check Point/ FortiGate Firewall allows access to protected resource if the user is authorized.
- User's role changes while logged in (for example, when Host Check compliance change causes role(s) to change). In this case, user's new role(s) are sent to PAN/Check Point/ FortiGate Firewall.
- User logs out of ICS. In this case, all information associated with the user from that endpoint is removed from the Firewall. User is denied access to protected resources by Firewall.
The same workflow applies to local users connecting through IPS.