Deployment of IPS using PAN Firewall
This section describes the integration of IPS with Palo Alto Networks next-generation firewall. The IPS and PAN firewall integration allows users to enforce role based access to network resources and web applications and ensures endpoint compliance. The integrated solution provides policy enforcement for end to end protection of sensitive corporate data from unauthenticated access and attacks.
IPS combines user identity and device security state information with network location to create a unique, session specific access control policy for each user. The Palo Alto Networks firewall provides a feature called User Identification (User-ID) that creates policies and performs reporting based on users and groups rather than individual IP addresses. IPS uses the User-ID XML API to send the IP address to user and IP address to Group (Role) mapping information to the Palo Alto Networks firewall. PAN firewall enables the flexibility to apply different rules to the same server based on tags. A tag is a metadata element, which defines its role on the network, the operating system, or the different kinds of traffic it processes.
The Palo Alto Networks firewall compares the user information against the tag that is associated to a security rule. If the User Role name matches the tag, then traffic is either allowed or denied based on the configuration. When a user logs in, Ivanti Policy Secure provisions their user ID, IP address of the endpoint, and role information to the Palo Alto Networks firewall; that enables firewall policies based on any of these attributes to be enforced.
Similarly, when a user logs out, the user ID, IP address of the endpoint, and role information is removed from the firewall. More importantly, when a user's role changes, the role change information is dynamically updated on the firewall, so that access based on the updated roles is automatically changed based on the policy matched by the new information.
With Palo Alto Networks firewall integration, all users' role changes, which includes compliance check failure or unauthorized behavior are dynamically updated on the firewall. The access is based on user roles and not merely on source IP addresses.
IPS is the policy decision point that determines which users and endpoints can access protected resources. Palo Alto Networks Next Gen firewalls serve as the policy enforcement points to provide the ultimate protection to ensure that network assets are secured.
Palo Alto Networks integration with Ivanti Policy Secure leverages dynamic role information provisioned to the firewall upon user session establishment and for the duration of the session. Ivanti Policy Secure also communicates user information to the Palo Alto Networks firewall when users log in or log out from their device.
Deploying IPS with a PAN firewall for a Small Enterprise
IPS and PAN integration can be used for role based layer 3 access control. For small scale enterprise deployment, you can use a single IPS and PAN firewall as it involves less number of users. For example, employees, contractors, and guest users. A single IPS device provisioning to a PAN firewall can handle up to 30,000 user sessions. The following is a sample deployment with a IPS device along with a PAN firewall.
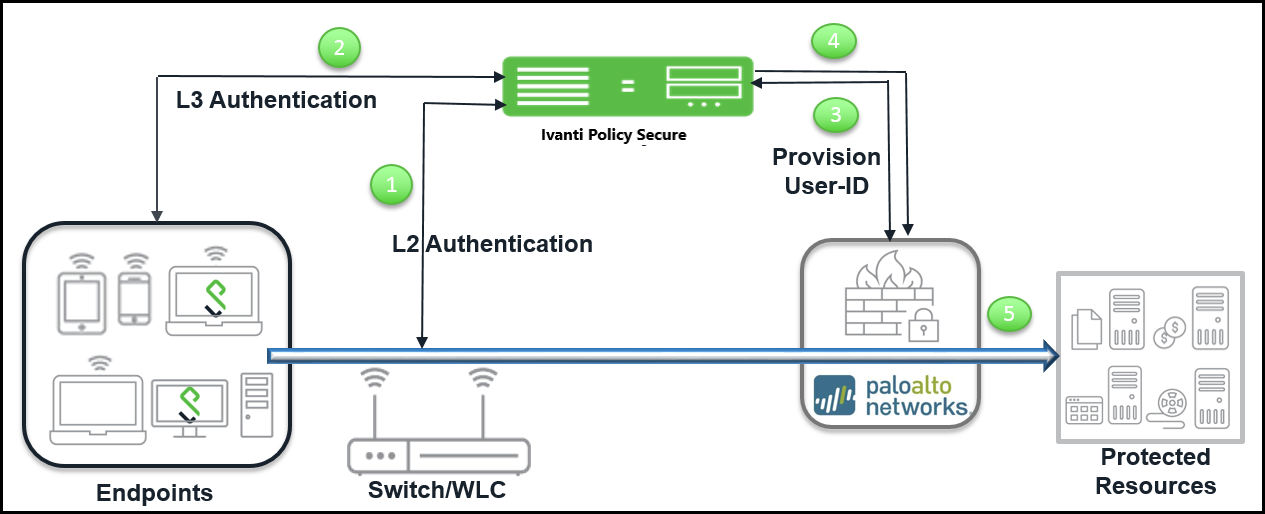
The authentication process is described below:
- The endpoints connect to switch/WLAN and performs the layer 2 authentication with IPS.
- IPS performs the layer 3 authentication and performs compliance check on the endpoint and detects for any unauthorized behavior.
- IPS provisions the auth table entries on the PAN firewall.
- IPS provisions the auth table with changes in role information if any on PAN firewall. The user role changes, which includes any unauthorized behavior are dynamically updated on the firewall. The access is based on roles, rather than only on source IP addresses.
- The PAN firewall applies policies to allow or block user access to protected resources.
Deploying multiple IPS with PAN firewall
The deployment example describes an enterprise environment with multiple IPS servers where different users are authenticated using different IPS servers. For such deployments, multiple IPS servers can be configured to communicate with a single PAN firewall. The multiple IPS servers sends user-ID entries to a single PAN firewall.

Deploying IPS with PAN firewall for a Large Enterprise
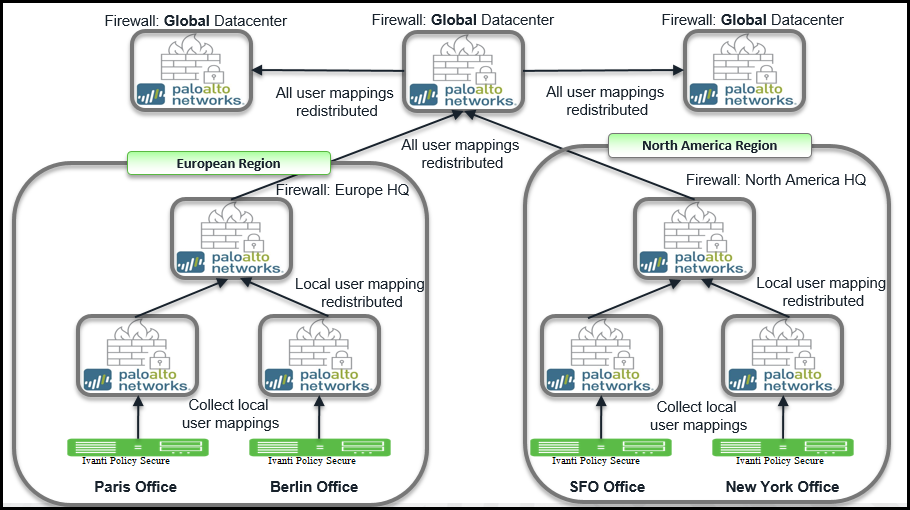
A large-scale enterprise network uses multiple firewalls to enforce policies. You can reduce the resources that the firewalls and information sources use in the querying process by configuring some firewalls to acquire mapping information. You can enable the firewall to enforce user based policies when users rely on local sources for authentication (for example, regional directory services) but need access to remote resources (for example, global data center applications).
The deployment example describes how a global datacenter resources is distributed across the branches and shared across the local offices. It also shows how you can organize the redistribution sequence in layers, where each layer has one or more firewalls. In this example, bottom-layer firewalls in local offices rely on IPS for authentication and then redistribute the mapping information to middle-layer firewalls in regional offices, which redistribute to one top-layer firewall in a global data center. The data center firewall redistributes the mapping information to other data center firewalls so that they can enforce global policies for all users.